Identity and Access Management
Last Updated :
17 Nov, 2023
In a recent study by Verizon, 63% of the confirmed data breaches are due to either weak, stolen, or default passwords used. There is a saying in the cybersecurity world that goes like this “No matter how good your chain is it’s only as strong as your weakest link.” and exactly hackers use the weakest links in the organization to infiltrate. They usually use phishing attacks to infiltrate an organization and if they get at least one person to fall for it, it’s a serious turn of events from thereon. They use the stolen credentials to plant back doors, install malware or exfiltrate confidential data, all of which will cause serious losses for an organization.
How Identity and Access Management Works?
AWS(Amazon Web Services) will allows you to maintain the fine-grained permissions to the AWS account and the services provided Amazon cloud. You can manage the permissions to the individual users or you can manage the permissions to certain users as group and roles will helps you to manage the permissions to the resources.
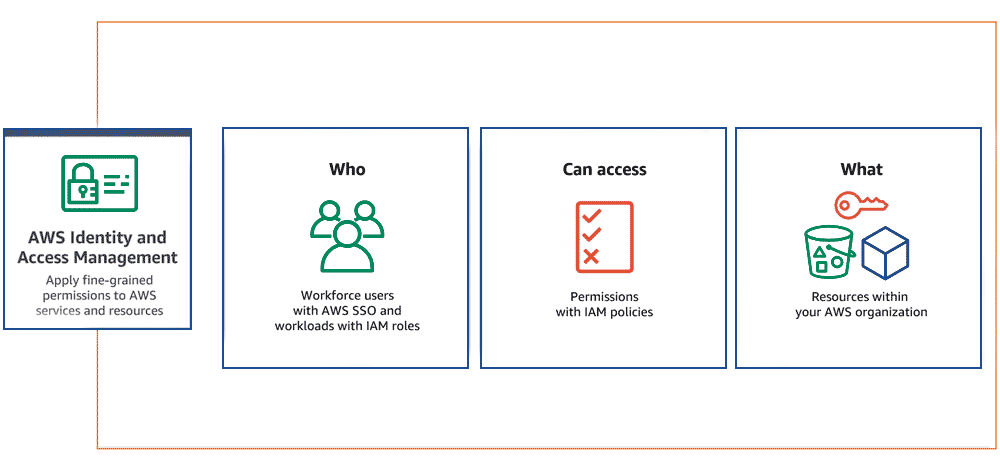
What Is Identity and Access Management(IAM)?
Identity and Access Management (IAM) is a combination of policies and technologies that allows organizations to identify users and provide the right form of access as and when required. There has been a burst in the market with new applications, and the requirement for an organization to use these applications has increased drastically. The services and resources you want to access can be specified in IAM. IAM doesn’t provide any replica or backup. IAM can be used for many purposes such as, if one want’s to control access of individual and group access for your AWS resources. With IAM policies, managing permissions to your workforce and systems to ensure least-privilege permissions becomes easier. The AWS IAM is a global service.
Components of Identity and Access Management (IAM)
Users
- Roles
- Groups
- Policies
With these new applications being created over the cloud, mobile and on-premise can hold sensitive and regulated information. It’s no longer acceptable and feasible to just create an Identity server and provide access based on the requests. In current times an organization should be able to track the flow of information and provide least privileged access as and when required, obviously with a large workforce and new applications being added every day it becomes quite difficult to do the same. So organizations specifically concentrate on managing identity and its access with the help of a few IAM tools. It’s quite obvious that it is very difficult for a single tool to manage everything but there are multiple IAM tools in the market that help the organizations with any of the few services given below.
IAM Identities Classified As
- IAM Users
- IAM Groups
- IAM Roles
Root user
The root user will automatically be created and granted unrestricted rights. We can create an admin user with fewer powers to control the entire Amazon account.
IAM Users
We can utilize IAM users to access the AWS Console and their administrative permissions differ from those of the Root user and if we can keep track of their login information.
Example
With the aid of IAM users, we can accomplish our goal of giving a specific person access to every service available in the Amazon dashboard with only a limited set of permissions, such as read-only access. Let’s say user-1 is a user that I want to have read-only access to the EC2 instance and no additional permissions, such as create, delete, or update. By creating an IAM user and attaching user-1 to that IAM user, we may allow the user access to the EC2 instance with the required permissions.
IAM Groups
A group is a collection of users, and a single person can be a member of several groups. With the aid of groups, we can manage permissions for many users quickly and efficiently.
Example
Consider two users named user-1 and user-2. If we want to grant user-1 specific permissions, such as the ability to delete, create, and update the auto-calling group only, and if we want to grant user-2 all the necessary permissions to maintain the auto-scaling group as well as the ability to maintain EC2,S3 we can create groups and add this user to them. If a new user is added, we can add that user to the required group with the necessary permissions.
IAM Roles
While policies cannot be directly given to any of the services accessible through the Amazon dashboard, IAM roles are similar to IAM users in that they may be assumed by anybody who requires them. By using roles, we can provide AWS Services access rights to other AWS Services.
Example
Consider Amazon EKS. In order to maintain an autoscaling group, AWS eks needs access to EC2 instances. Since we can’t attach policies directly to the eks in this situation, we must build a role and then attach the necessary policies to that specific role and attach that particular role to EKS.
IAM Policies
IAM Policies can manage access for AWS by attaching them to the IAM Identities or resources IAM policies defines permissions of AWS identities and AWS resources when a user or any resource makes a request to AWS will validate these policies and confirms whether the request to be allowed or to be denied. AWS policies are stored in the form of Jason format the number of policies to be attached to particular IAM identities depends upon no.of permissions required for one IAM identity. IAM identity can have multiple policies attached to them.
Access management for AWS resourcesIdentity management
- Access management
- Federation
- RBAC/EM
- Multi-Factor authentication
- Access governance
- Customer IAM
- API Security
- IDaaS – Identity as a service
- Granular permissions
- Privileged Identity management – PIM (PAM or PIM is the same)
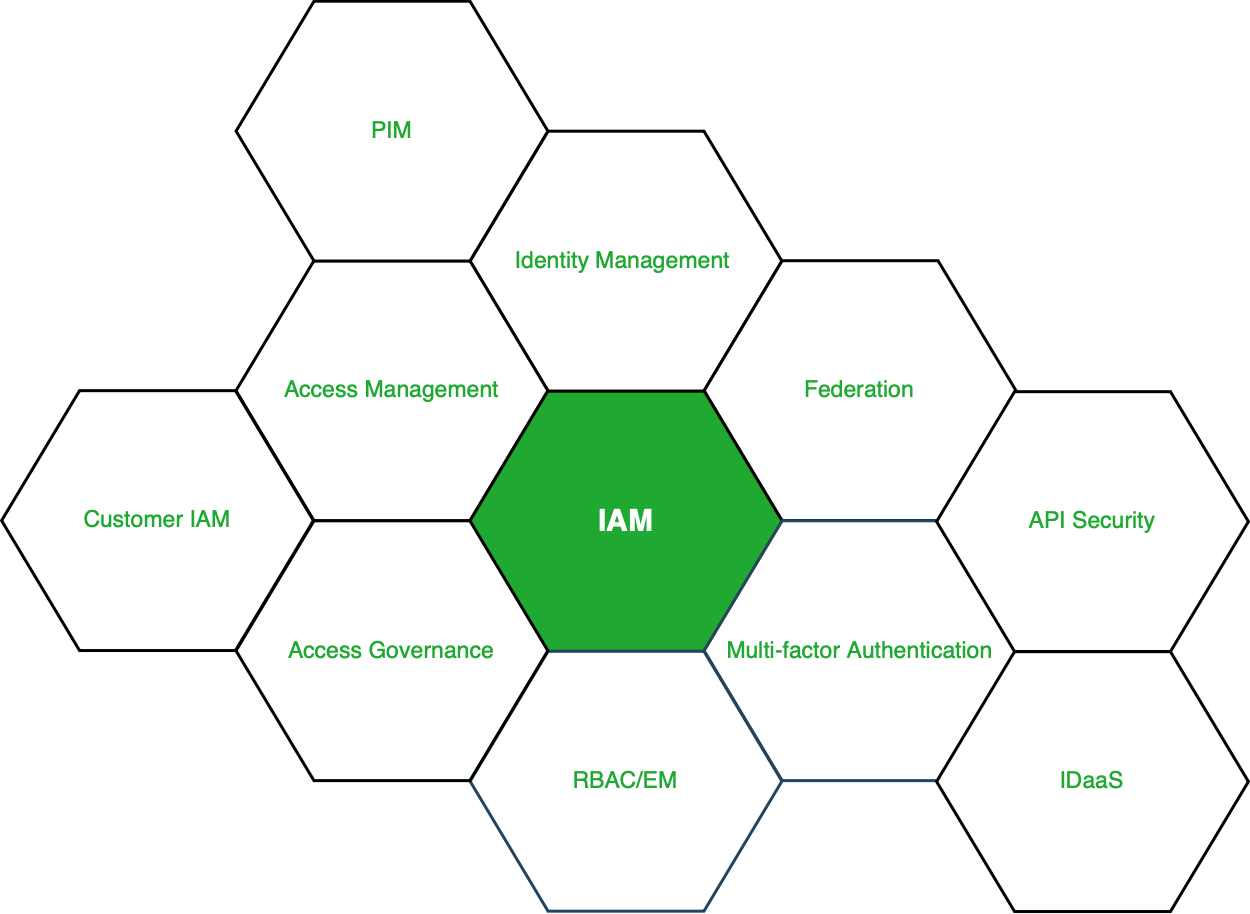 Figure – Services under IAM
Figure – Services under IAM
More About the Services: Looking into the services on brief, Identity management is purely responsible for managing the identity lifecycle. Access management is responsible for the access to the resources, access governance is responsible for access request grant and audits. PIM or PAM is responsible for managing all the privileged access to the resources. The remaining services either help these services or help in increasing the productivity of these services.
Market for IAM: Current situation of the market, there are three market leaders (Okta, SailPoint and Cyberark) who master one of the three domains (Identity Management, Identity Governance and Privilege access management), according to Gartner and Forrester reports. These companies have developed solutions and are still developing new solutions that allow an organization to manage identity and its access securely without any hindrances in the workflow. There are other IAM tools, Beyond Trust, Ping, One login, Centrify, Azure Active Directory, Oracle Identity Cloud Services and many more.
Use cases Identity and Access Management(IAM)
- Resource Access Control: Identity and access management (IAM) will allows you to manage the permissions to the resources in the AWS cloud like users who can access particular serivce to which extent and also instead of mantaing the permissions individually you can manage the permissions to group of users at a time.
- Managing permissions: For example you want to assign an permission to the user that he/her can only perform restart the instance task on AWS EC2 instance then you can do using AWS IAM.
- Implemneting role-based access control(RBAC): Identity and Access Management(IAM) will helps you to manage the permissions based on roles Roles will helps to assign the the permissions to the resourcesw in the AWS like which resources can access the another resource according to the requirement.
- Enabling single sign-on (SSO): Identity and Access Management will helps you to maintain the same password and user name which will reduce the effort of remembering the different password.
IAM Features
Shared Access to your Account: A team working on a project can easily share resources with the help of the shared access feature.
- Free of cost: IAM feature of the AWS account is free to use & charges are added only when you access other Amazon web services using IAM users.
- Have Centralized control over your AWS account: Any new creation of users, groups, or any form of cancellation that takes place in the AWS account is controlled by you, and you have control over what & how data can be accessed by the user.
- Grant permission to the user: As the root account holds administrative rights, the user will be granted permission to access certain services by IAM.
- Multifactor Authentication: Additional layer of security is implemented on your account by a third party, a six-digit number that you have to put along with your password when you log into your accounts.
Accessing IAM
- AWS Console: Access the AWS IAM through the GUI. It is an web application provided by the AWS(Amazon Web Application) it is an console where users can access the aws console
- AWS Command Line Tools: Instead of accessing the console you can access y the command line interface (CLI) to access the AWS web application. You can autiomate the process by using the Scripts.
- IAM Query API: Programmatic access to IAM and AWS by allowing you to send HTTPS requests directly to the service.
FAQ’s On Identity and Access Maagement
1. What Are The 4 Components Of Identity Access Management?
The 4 four major components of dentity Access Management are
- Identity
- Authentication
- Authorization
- Auditing
2. What Is The Role Of Identity Access Management?
Identity and access management (IAM) is a security discipline that enables organizations to manage digital identities and control user access to critical information and systems.
Share your thoughts in the comments
Please Login to comment...