Digital Forensics in Information Security
Last Updated :
16 Jun, 2022
Digital Forensics is a branch of forensic science which includes the identification, collection, analysis and reporting any valuable digital information in the digital devices related to the computer crimes, as a part of the investigation. In simple words, Digital Forensics is the process of identifying, preserving, analyzing and presenting digital evidences. The first computer crimes were recognized in the 1978 Florida computers act and after this, the field of digital forensics grew pretty fast in the late 1980-90’s. It includes the area of analysis like storage media, hardware, operating system, network and applications. It consists of 5 steps at high level: 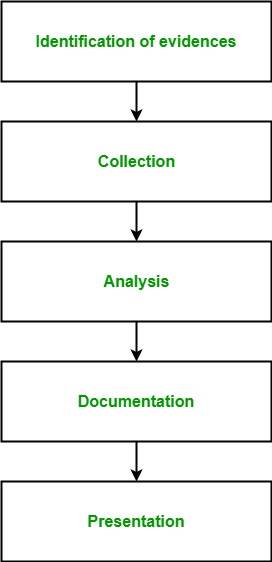
- Identification of evidence: It includes of identifying evidences related to the digital crime in storage media, hardware, operating system, network and/or applications. It is the most important and basic step.
- Collection: It includes preserving the digital evidences identified in the first step so that they doesn’t degrade to vanish with time. Preserving the digital evidences is very important and crucial.
- Analysis: It includes analyzing the collected digital evidences of the committed computer crime in order to trace the criminal and possible path used to breach into the system.
- Documentation: It includes the proper documentation of the whole digital investigation, digital evidences, loop holes of the attacked system etc. so that the case can be studied and analysed in future also and can be presented in the court in a proper format.
- Presentation: It includes the presentation of all the digital evidences and documentation in the court in order to prove the digital crime committed and identify the criminal.
Branches of Digital Forensics:
- Media forensics: It is the branch of digital forensics which includes identification, collection, analysis and presentation of audio, video and image evidences during the investigation process.
- Cyber forensics: It is the branch of digital forensics which includes identification, collection, analysis and presentation of digital evidences during the investigation of a cyber crime.
- Mobile forensics: It is the branch of digital forensics which includes identification, collection, analysis and presentation of digital evidences during the investigation of a crime committed through a mobile device like mobile phones, GPS device, tablet, laptop.
- Software forensics: It is the branch of digital forensics which includes identification, collection, analysis and presentation of digital evidences during the investigation of a crime related to softwares only.
Share your thoughts in the comments
Please Login to comment...