What is Network Forensics?
Last Updated :
15 Mar, 2022
The word “forensics” means the use of science and technology to investigate and establish facts in criminal or civil courts of law. Forensics is the procedure of applying scientific knowledge for the purpose of analyzing the evidence and presenting them in court.
Network forensics is a subcategory of digital forensics that essentially deals with the examination of the network and its traffic going across a network that is suspected to be involved in malicious activities, and its investigation for example a network that is spreading malware for stealing credentials or for the purpose analyzing the cyber-attacks. As the internet grew cybercrimes also grew along with it and so did the significance of network forensics, with the development and acceptance of network-based services such as the World Wide Web, e-mails, and others.
With the help of network forensics, the entire data can be retrieved including messages, file transfers, e-mails, and, web browsing history, and reconstructed to expose the original transaction. It is also possible that the payload in the uppermost layer packet might wind up on the disc, but the envelopes used for delivering it are only captured in network traffic. Hence, the network protocol data that enclose each dialog is often very valuable.
For identifying the attacks investigators must understand the network protocols and applications such as web protocols, Email protocols, Network protocols, file transfer protocols, etc.
Investigators use network forensics to examine network traffic data gathered from the networks that are involved or suspected of being involved in cyber-crime or any type of cyber-attack. After that, the experts will look for data that points in the direction of any file manipulation, human communication, etc. With the help of network forensics, generally, investigators and cybercrime experts can track down all the communications and establish timelines based on network events logs logged by the NCS.
Processes Involved in Network Forensics:
Some processes involved in network forensics are given below:
- Identification: In this process, investigators identify and evaluate the incident based on the network pointers.
- Safeguarding: In this process, the investigators preserve and secure the data so that the tempering can be prevented.
- Accumulation: In this step, a detailed report of the crime scene is documented and all the collected digital shreds of evidence are duplicated.
- Observation: In this process, all the visible data is tracked along with the metadata.
- Investigation: In this process, a final conclusion is drawn from the collected shreds of evidence.
- Documentation: In this process, all the shreds of evidence, reports, conclusions are documented and presented in court.
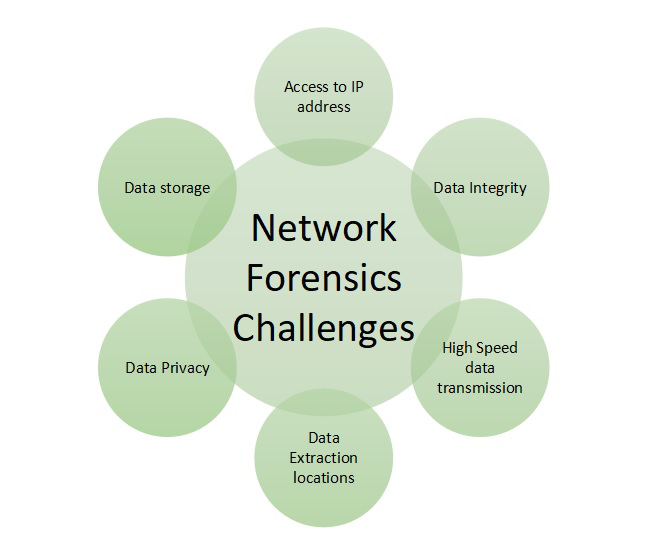
Challenges in Network Forensics:
- The biggest challenge is to manage the data generated during the process.
- Intrinsic anonymity of the IP.
- Address Spoofing.
Advantages:
- Network forensics helps in identifying security threats and vulnerabilities.
- It analyzes and monitors network performance demands.
- Network forensics helps in reducing downtime.
- Network resources can be used in a better way by reporting and better planning.
- It helps in a detailed network search for any trace of evidence left on the network.
Disadvantage:
- The only disadvantage of network forensics is that It is difficult to implement.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...