Digital Signature Standard (DSS)
Last Updated :
09 Apr, 2024
As we have studied, signature is a way of authenticating the data coming from a trusted individual. Similarly, digital signature is a way of authenticating a digital data coming from a trusted source. Digital Signature Standard (DSS) is a Federal Information Processing Standard(FIPS) which defines algorithms that are used to generate digital signatures with the help of Secure Hash Algorithm(SHA) for the authentication of electronic documents. DSS only provides us with the digital signature function and not with any encryption or key exchanging strategies. 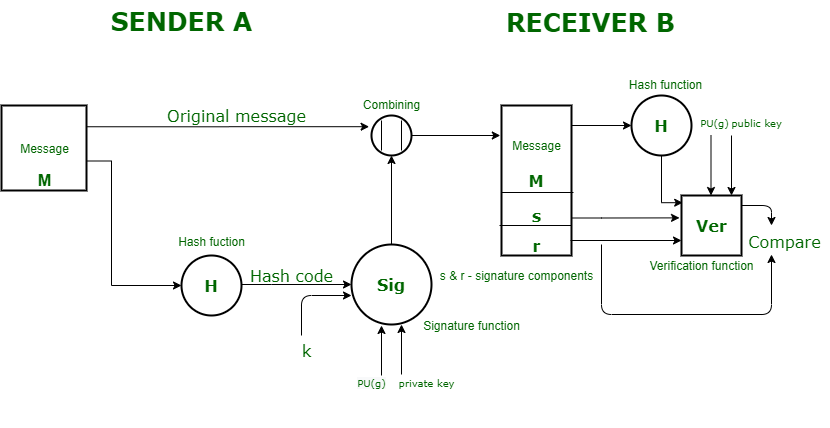
Sign any document online efficiently and organize your workflow with the user-friendly and highly secure e-signature platform SignNow. With this, you can easily share any electronic documents for signature, keep track of them, and even sign the documents on any device.
Sender Side: In DSS Approach, a hash code is generated out of the message and following inputs are given to the signature function –
- The hash code.
- The random number ‘k’ generated for that particular signature.
- The private key of the sender i.e., PR(a).
- A global public key(which is a set of parameters for the communicating principles) i.e., PU(g).
These input to the function will provide us with the output signature containing two components – ‘s’ and ‘r’. Therefore, the original message concatenated with the signature is sent to the receiver. Receiver Side : At the receiver end, verification of the sender is done. The hash code of the sent message is generated. There is a verification function which takes the following inputs –
- The hash code generated by the receiver.
- Signature components ‘s’ and ‘r’.
- Public key of the sender.
- Global public key.
The output of the verification function is compared with the signature component ‘r’. Both the values will match if the sent signature is valid because only the sender with the help of it private key can generate a valid signature.
Benefits of advanced signature:
1.A computerized signature gives better security in the exchange. Any unapproved individual can’t do fakeness in exchanges.
2.You can undoubtedly follow the situation with the archives on which the computerized mark is applied.
3.High velocity up record conveyance.
4.It is 100 percent lawful it is given by the public authority approved ensuring authority.
5.In the event that you have marked a report carefully, you can’t deny it.
6.In this mark, When a record is get marked, date and time are consequently stepped on it.
7.It is preposterous to expect to duplicate or change the report marked carefully.
8.ID of the individual that signs.
9.Disposal of the chance of committing misrepresentation by a sham.
Burdens of computerized signature:
1.You really want to investigate all the similarity issues. In there are a great deal of similarity settings like a refreshed rendition of driver and programming.
2.Programming is one of the main pressing concerns while utilizing a computerized signature testament.
3.On the off chance that you are having a place with the corporate world and running a commodity import association, you want to create a computerized signature for E-tagging.
4.In this signature, Lost or burglary of keys and the utilization of weak storage spaces.
5.There is a more grounded need for a norm through which these various strategies can cooperate.
In this period of quick mechanical headway, a considerable lot of these tech items have a short timeframe of realistic usability.
6.To successfully utilize a computerized signature, the two shippers and beneficiaries might need to purchase computerized endorsements.
7.To work with computerized endorsements, the shipper and beneficiaries need to purchase check programming at an expense.
8.A computerized signature includes the essential road for any business is cash.
Share your thoughts in the comments
Please Login to comment...