What Are Azure Data Security Features?
Last Updated :
10 May, 2022
Data security is a huge topic and it’s one of the most important types of security in space today. Lots of hackers and world governments are trying to break into databases because Data has got a lot of financial and other value.
Azure has a multi-layer view of security that you can’t just have one single fence around your data. You need to have multiple layers of security that each one of those has to be violated effectively in order to get to the customer data sitting at the center.
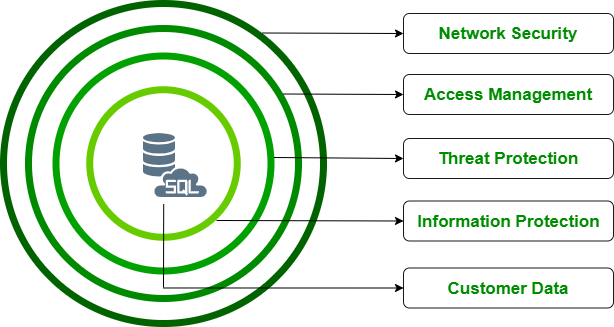
1. Network Security: The topmost layer is Network security.
- Block by default: Azure SQL database has a firewall off by default. So you cannot connect to it unless the IP is white listed. You have to explicitly allow other Azure services even to connect to it. And it’s not just open to the world even if you had credentials like your username and password. You need to have the firewall enabled.
- Protect the whole server or protect individual databases: Once you white list an IP, the database DV 1 and the data warehouse also will be able to be accessed. But we can actually go into the database and put server level firewalls as well. So there are SQL commands effectively that allow you to create firewalls to allow and block. So if you have multiple databases but you only want them to access one, you can allow the IP address through the server but block that IP on many of the databases.
You can allow or restrict other Azure Services and you can even add an endpoint into a virtual network that allows you to control traffic through the network security group through typical virtual network security protections
2. Access management: It deals with identity management and authentication effectively. There are two ways to achieve this:
- SQL authentication (username and password)
- Azure Active Directory (Azure AD)
All servers have a root username and password to the main user that we create during setup. But then we can enable the Azure Active Directory. We have to enable a root ID for that, and then we can create Azure Active Directory users that can then be granted access as well. So once you’ve set up the admin user then you’re opening the door for other users to authenticate through Azure Active Directory and not SQL Server authentication. It allows you to manage your security centralized location instead of having SQL Server has its own authentication database.
Once you are logged in with the user ID and password. You have certain levels of access:
- Principle of The Least Privilege: Microsoft recommends the principle of the least privilege which goes on to state that you should not give people excessive permissions. i.e Everyone should not be admin, Admin account should not be used to do your day-to-day work and Your applications should not be running in DB owner permissions. Creating the right levels, right users, and roles for the permissions can save you if there is a compromise that account doesn’t have excessive privileges.
- Role-Based Access Control (RBAC): Azure Role-Based Access Control (Azure RBAC) helps you manage who has access to Azure ‘s resources, what they can do with those resources, and the areas they have access to. RBAC is another way that protects people from getting access to things they are not supposed to have access to.
- Row Level Security: SQL server itself has security in things such as Row-level security where you can allow users to access specific regions. It’s in the same database and it’s just a column filter that’s going to determine whether you have access to it or not. So you can do all the way down to the data level types of authorization which is fine-grained.
3. Threat Protection: Azure Monitor is the centralized source for alerts, log files, monitoring, and things like that.
- Advanced-Data Security: If you sign up for advanced data security, there’s a free trial for that and then it costs around $20-$30 a month per server. After that, you get these three cool features in terms of threat protection.
- Data Discovery and Classification: Data discovery and classification is pretty cool. It will actually go and examine your data to an audit effectively and determine which of your data fields are potentially and personally identifiable information subject to deep GDP restrictions subject at API. You might want to implement some security rules around personally identifiable information. So you can actually tag these columns as potentially sensitive information and again implement certain rules based on the tags on the columns.
- Vulnerability Assessment: If people can read people’s names and addresses without a certain level of authorization, vulnerability assessment will look at your server and determine if you’ve got too many IP addresses enabled. If you’re set to based on your firewall settings, your server if you’ve got roles in users that are of excessive privileges or don’t have any use and it’s going to tell you important security things about your setup.
- Advanced Threat Protection: Advanced threat protection is more like protecting against SQL injection attacks and some of those common things where we’ve got hackers actively trying to hack into your server guessing the password multiple times.
4. Information Security
- Data Security – At Rest: Data is encrypted by default in Azure- Transparent Data Encryption(TDE). Azure Controls the keys, and often the encryption is transparent to you. You can control the keys using the Azure Key Vault. If someone breaks into an Azure Data Center, they can’t read your data. But if they pass network, identify, and authorization checks, then they can.
- Data Security – In Transit: This is an important one because the Internet is a series of connected nodes. Anyone sitting in between one server and another can read the data so it is important to encrypt it using SSL/TLS(i.e. HTTPS). All data traveling outside of Azure should travel encrypted
- Always Encrypted: Some Azure Database services support an “always encrypted” mode. The data is encrypted at the client and is stored in the encrypted state. Nothing can read it without the key, and only the client has the key. If the client is hacked, they can read the data.
- Data Masking – Anonymizing: Sometimes, you don’t need access to sensitive data fields all the time. i.e You might need to know the order dollar amounts, order id, order date, the product ordered, etc. You have the ability to restrict access to customer personally identifiable information to only some accounts. Data masking returns ***** for certain fields that are needed by a query.
- Store Data Encrypted: You can always choose to have the application do the encryption. If you are storing passwords, hash them using a good hashing algorithm and a salt. Instead of having your password being sent across in plain text and encrypted at the server side you can do the hashing and use salts in the proper algorithm.
5. Customer Data: SQL Database and SQL Managed Instance secure customer data by means of Transport Layer Security (TLS) encryption in motion.
Share your thoughts in the comments
Please Login to comment...