1. Explain the range of TCP/IP classes?

2. What are Pvt. IP address?
The private IP address of a system is the IP address that is used to communicate within the same network. Using private IP data, information can be sent or received within the same network. For more details please refer difference between private and public IP addresses.
3. Explain does IP protects data on the network?
IP itself doesn’t guarantee delivering data correctly. It leaves all data protection to the transport protocol. Both TCP and UDP have mechanisms that guarantee that the data they deliver to an application is correct.
Using the IP layer, the correct destination of the packet is identified & delivered. The Transport layer protocols(TCP/UDP) check if the data delivered is correct using the Checksum mechanism. However, if the destination IP is not alive, the packet is hopped by decreasing the TTL (Time to leave) field and when it becomes zero, the packet is lost and undelivered. If the transport layer is UDP, the source doesn’t know of the failure in the delivery of the packet. For more details please refer IP address
4.Tell the name of the data Unit of the Transport layer?
The protocol data unit of the transport layer is a segment or datagram.
5. Tell the name of the data unit to send by the Internet layer?
The protocol data unit of the internet layer is a packet.
6.The difference between TCP and UDP protocols?
| Transmission control protocol (TCP) | User datagram protocol (UDP) |
|---|
| TCP is a connection-oriented protocol. Connection-orientation means that the communicating devices should establish a connection before transmitting data and should close the connection after transmitting the data. | UDP is the datagram oriented protocol. This is because there is no overhead for opening a connection, maintaining a connection, and terminating a connection. UDP is efficient for broadcast and multicast types in order of network transmission. |
| TCP is reliable as it guarantees the delivery of data to the destination router. | The delivery of data to the destination cannot be guaranteed in UDP. |
| TCP provides extensive error checking mechanisms. It is because it provides flow control and acknowledgement of data. | UDP has only the basic error checking mechanism using checksums. |
| Sequencing of data is a feature of Transmission Control Protocol (TCP). This means that packets arrive in-order at the receiver. | There is no sequencing of data in UDP. If the order is required, it has to be managed by the application layer. |
| TCP is comparatively slower than UDP. | UDP is faster, simpler, and more efficient than TCP. |
| Retransmission of lost packets is possible in TCP, but not in UDP. | There is no retransmission of lost packets in the User Datagram Protocol (UDP). |
| TCP has a (20-60) bytes variable length header. | UDP has an 8 bytes fixed-length header. |
| TCP is heavy-weight. | UDP is lightweight. |
| TCP doesn’t support Broadcasting. | UDP supports Broadcasting. |
| TCP is used by HTTP, HTTPs, FTP, SMTP and Telnet. | UDP is used by DNS, DHCP, TFTP, SNMP, RIP, and VoIP. |
For more details please refer difference between TCP and UDP article.
7.How TCP protocol provides reliability?
TCP is reliable as it uses checksum for error detection, attempts to recover lost or corrupted packets by re-transmission, acknowledgment policy, and timers. It uses features like byte numbers and sequence numbers and acknowledgment numbers so as to ensure reliability.
8.Write down the name of services provided by TCP?
- Process to process communication
- Stream orientation
- Full duplex service
- Multiplexing
- Reliability
For more details please refer TCP/IP in the computer networking article.
9.Explain TCP protocol header format?

For more details, please read TCP/IP model article.
10.Write the name of all TCP “Flag”?
A TCP Flag field contains 6 different flags, namely:
- URG: Urgent pointer is valid
- ACK: Acknowledgement number is valid( used in case of cumulative acknowledgment)
- PSH: Request for push
- RST: Reset the connection
- SYN: Synchronize sequence numbers
- FIN: Terminate the connection
For more details, please read TCP/IP model article.
11. What is the role of the TCP checksum field?
One of the important fields of TCP protocol format. It is 16 bits long. This field holds the checksum for error control. It is mandatory in TCP as opposed to UDP. For more details, please read TCP/IP model article.
12.What is PORT?
A port is basically a physical docking point that is basically used to connect the external devices to the computer, or we can say that a port acts as an interface between the computer and the external devices, e.g., we can connect hard drives and printers to the computer with the help of ports. For more details please refer to various TCP and UDP ports article.
13.Write the name of the Well-Known Port used by TCP?
| PORT | Service | Description | Transport Protocol |
|---|
| 7 | Echo | Port just echoes whatever is sent to it. This feature can be used in many attacks, such as Smurf/Fraggle. | TCP and UDP |
| 9 | Discard | Discard any datagram that is received. | |
| 20 /21 | File Transfer Protocol (FTP) | Port used by FTP protocol to send data to a client. | TCP |
| 23 | Telnet | Port used by Telnet to remotely connect to a workstation or server(unsecured) | TCP |
| 25 | Simple Mail Transfer Protocol (SMTP) | Used to send E-Mail over the Internet | TCP |
| 53 | Domain Name System (DNS) | Port for DNS requests, network routing, and zone transfers | TCP |
| 67 | BOOTP | Bootstrap protocol | TCP |
| 80 | Hyper Text Transfer Protocol (HTTP) | Used for browsing web-pages on a browser | TCP |
| 110 | Post Office Protocol (POP3) | Port used to retrieve complete contents of a server mailbox | TCP |
For more details please refer to various TCP and UDP ports article.
14.Define the term Endpoint in TCP?
TcpEndpoint allows you to easily establish and communicate over TCP/IP network connections between client and server processes, possibly residing on different hosts. The TcpEndpoint class follows a telephone-like model of networking: clients “call” servers and servers “answer” clients. Once a network connection is established between a client and a server, the two can “talk” to each other by reading from and writing to the connection.
15.Explain the error control mechanism in TCP?
TCP protocol has methods for finding out corrupted segments, missing segments, out-of-order segments, and duplicated segments.
Error control in TCP is mainly done through the use of three simple techniques :
- Checksum
- Acknowledgment
- Retransmission
16.Explain congestion?
A state occurring in the network layer when the message traffic is so heavy that it slows down network response time is known as congestion. For more details please read TCP congestion control article.
17.What is the difference between stop-and-wait protocol & sliding window protocol?
| S.NO | Stop-and-Wait Protocol | Sliding Window Protocol |
|---|
| 1. | In Stop-and-Wait Protocol, sender sends one frame and wait for acknowledgment from receiver side. | In sliding window protocol, sender sends more than one frame to the receiver side and re-transmits the frame(s) which is/are damaged or suspected. |
|---|
| 2. | Efficiency of Stop-and-Wait Protocol is worse. | Efficiency of sliding window protocol is better. |
|---|
| 3. | Sender window size of Stop-and-Wait Protocol is 1. | Sender window size of sliding window protocol is N. |
|---|
| 4. | Receiver window size of Stop-and-Wait Protocol is 1. | Receiver window size of sliding window protocol may be 1 or N. |
|---|
| 5. | In Stop-and-Wait Protocol, sorting is not necessary. | In sliding window protocol, sorting may be or may not be necessary. |
|---|
| 6. |
Efficiency of Stop-and-Wait Protocol is
1/(1+2*a) |
Efficiency of sliding window protocol is
N/(1+2*a) |
|---|
| 7. | Stop-and-Wait Protocol is half duplex. | Sliding window protocol is full duplex |
|---|
18.What is round trip time?
The length of time taken by a data packet to be sent to a destination includes the time it takes for an acknowledgment of that packet to be received back at the original place. For more details please refer to What is RTT article.
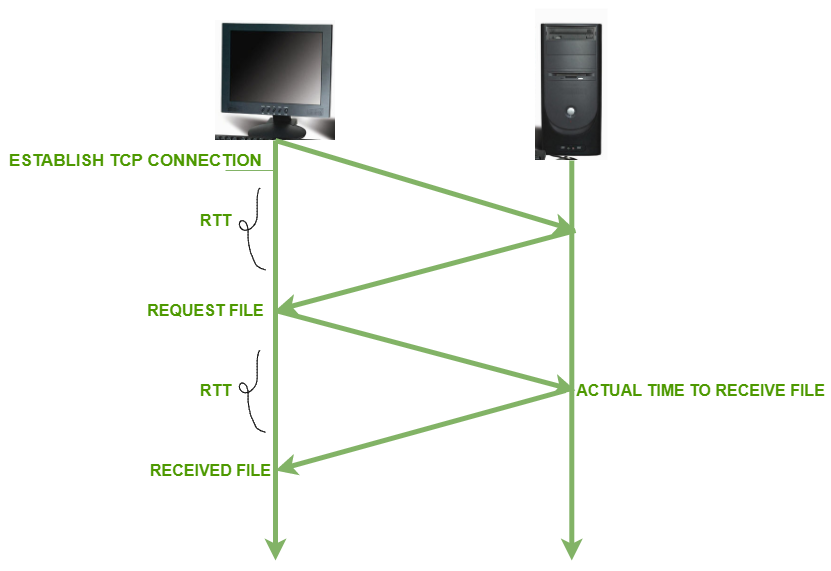
19.What is the significance of TCP acknowledgments?
TCP acknowledgments are used to acknowledge packets that are successfully received by the host. The flag is set if the acknowledgment number field contains a valid acknowledgment number.For more details, please read TCP/IP model article.
20.What is retransmission?
The TCP retransmission means resending the packets over the network that have been either lost or damaged. Here, retransmission is a mechanism used by protocols such as TCP to provide reliable communication. Here, reliable communication means that the protocol guarantees the packet’s delivery even if the data packet has been lost or damaged. The networks are unreliable and do not guarantee the delay or the retransmission of the lost or damaged packets. The network, which uses a combination of acknowledgment and retransmission of damaged or lost packets, offers reliability. For more details please read TCP congestion control article.
21.If TCP round trip time, RTT is currently 30m sec and the following acknowledgment comes in after 26, 32 and 24 m sec respectively what is the new RTT estimate?(Use α = 0.9)
The formula for estimate new RTT
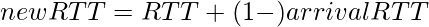
new RTT = 0.9*30+(1-0.9)*26
new RTT = 29.6
For more detail please refer what is RTT article.
22. Write down features of TCP?
- Connection-oriented: An application requests a “connection” to the destination and uses the connection to transfer data
- Stream Data transfer: It is the duty of TCP to pack this byte stream into packets, known as TCP segments, which are passed to the IP layer for transmission to the destination device.
- Reliable: It recovers data from the network layer if data is damaged, duplicated, or corrupted.
- Point to Point: TCP connection provides end-to-end delivery.
- Interoperability: It eliminates cross-platform boundaries.
- Error and flow control: Error-checking, flow-control, and acknowledgment functions.
- Name resolution: It helps in solving human-readable names into IP addresses.
- Routability: TCP/IP is a routable protocol,
- It helps in resolving logical addresses.
- Full Duplex: It provides connection in both directions.
For more details, please read TCP/IP model article.
23.What is SCTP protocol?
SCTP stands for Stream Control Transmission Protocol. It is a connection-oriented protocol on computer networks that provides a full-duplex association, i.e., transmitting multiple streams of data between two endpoints at the same time that have established a connection in the network. It is sometimes referred to as next-generation TCP or TCPng. SCTP makes it easier to support telephonic conversation on the Internet. A telephonic conversation requires the transmitting of the voice along with other data at the same time on both ends. The SCTP protocol makes it easier to establish a reliable connection.SCTP is also intended to make it easier to establish connections over the wireless networks and managing the transmission of multimedia data. SCTP is a standard protocol (RFC 2960) and is developed by the Internet Engineering Task Force (IETF). For more details please read the SCTP full form article.
24.Explain the process of three-way handshaking protocol?
Process of three-way handshaking protocol
- Step 1 (SYN): In the first step, the client wants to establish a connection with the server, so it sends a segment with SYN(Synchronize Sequence Number) which informs the server that the client is likely to start communication and with what sequence number it starts segments.
- Step 2 (SYN + ACK): Server responds to the client request with the SYN-ACK signal bits set. Acknowledgment (ACK) signifies the response of the segment it received and SYN signifies with what sequence number it is likely to start the segment.
- Step 3 (ACK): In the final part, the client acknowledges the response of the server and they both establish a reliable connection with which they will start the actual data transfer.
Steps 1, 2 establish the connection parameter (sequence number) for one direction and it is acknowledged. Steps 2, 3 establish the connection parameter (sequence number) for the other direction and it is acknowledged. With these, full-duplex communication is established.
For more details please read TCP-3 way handshake process.
25.Difference between Leaky bucket and Token bucket algorithm?
| Leaky Bucket | Token Bucket |
|---|
| When the host has to send a packet, the packet is thrown in a bucket. | This leaky bucket holds tokens generated at regular intervals of time. |
| Bucket leaks at a constant rate | The bucket has a maximum capacity. |
| Bursty traffic is converted into uniform traffic by leaky buckets. | Bucket there is a ready packet, a token is removed from the bucket and the packet is sent. |
| In practice, a bucket is a finite queue output at a finite rate. | If there is no token in the bucket, the packet can not be sent. |
For more detail please read Congestion control in the computer network article.
26.Write advantages of the token bucket over the Leaky bucket algorithm?
- If a bucket is full in tokens, tokens are discarded, not packets. While in a leaky bucket, packets are discarded.
- Token Bucket can send large bursts at a faster rate, while buckets always send packets at a constant rate.
For more detail please read Congestion control in the computer network article.
27.What is the difference between connection-oriented service and connection-less?
| S.NO | Connection-oriented Service | Connection-less Service |
|---|
| 1. | Connection-oriented service is related to the telephone system. | Connection-less service is related to the postal system. |
|---|
| 2. | Connection-oriented service is preferred by long and steady communication. | Connection-less Service is preferred by bursty communication. |
|---|
| 3. | Connection-oriented Service is necessary. | Connection-less Service is not compulsory. |
|---|
| 4. | Connection-oriented Service is feasible. | Connection-less Service is not feasible. |
|---|
| 5. | In connection-oriented Service, Congestion is not possible. | In connection-less Service, Congestion is possible. |
|---|
| 6. | Connection-oriented Service gives the guarantee of reliability. | Connection-less Service does not give the guarantee of reliability. |
|---|
| 7. | In connection-oriented Service, Packets follow the same route. | In connection-less Service, Packets do not follow the same route. |
|---|
| 8. | Connection-oriented services require a bandwidth of a high range. | Connection-less Service requires a bandwidth of low range |
|---|
28.What are the TCP connections phases?
In TCP, connection-oriented transmission requires three phases:
- Connection establishment
- Data Transfer
- Connection termination
For more detail read TCP connection establishment article.
29.Write features of TCP sliding window?
Features of the TCP sliding window:
- It uses variable-size windows to provide flow control as well as reliable transfer.
- TCP connections are full-duplex, two transfers proceed simultaneously over each connection, one in each direction.
- It support machine of various speed and size communicate through a network and also routers of various speeds.
30.What is the maximum size of the TCP header? What is the minimum size of TCP header?
- Maximum size of the TCP header = 60 bytes
- Minimum size of the TCP header = 20 bytes
31.Do port addresses need to be unique? Why or why not? Why are port addresses shorter than IP addresses?
Port addressing is done by the transport layer, which is the 4th layer of the OSI (Open System Interconnection) Model. Port addresses are short because they have to perform the end-to-end delivery of the message and the protocols are less in number than computer systems, therefore, port addresses are less than IP addresses. The IP address refers to the computer/device connected to the network and the port address refers to a particular protocol to communicate with the server as per client request. For more details read TCP/IP ports and its application article.
32.Are both UDP and IP unreliable to the same degree? Why or Why not?
No, UDP is unreliable and connectionless. While IP unreliability lies in the upper layer protocols. The IP packet becomes reliable if the upper layer protocol is TCP. In terms of data integrity, UDP is more reliable than IP. The checksum in the IP header only applies to the header itself, not to the whole packet. The UDP checksum applies to the whole user segment.
33.Define the term Datagram?
It is a logical unit to transfer information over the network. This data is transmitted from source to destination. It does not guarantee that data will be delivered or lost on the way. It has two section headers and a data payload. It travels in-network without establishing a prior virtual network between source and destination., ie. unlike, it has no prior information about the path between source and destination. This data is frequently divided into smaller parts and transmitted to the defined route.
34.What are the Registered port and Dynamic port?
Registered port: The ports ranging from 1024 to 49151 are not assigned and controlled by an IANA. They can only be registered with IANA to prevent duplication.
Dynamic port: This port ranging from 49152 to 65535 is neither controlled nor registered. They can be used in any process.
35.Write the importance of TTL field?
The lifespan or lifetime of data that is being sent. Once, after that specified time is over or elapsed, the data will be discarded or it can also be stated as a number of hops that packet is set to exist in the network, after which that packet is discarded. The purpose of the TTL field is to avoid a situation in which an undeliverable datagram keeps circulating in the network.
36.An IPv4 packet has arrived with the first 8 bits as shown: 01000010 The receiver discards the packet. Why?
An IPv4 packet has arrived with the first 8 bits being 01000010 The receiver discards the packet because the first 4 bits represent version IPV4.
and another 4 bits represent header length (/ 4) which should range between 20 to 60 bytes. Here 0010 represents header length, is equal to 2 * 4 = 8. So, the receiver will reject the packet.
37.In an IPv4 packet, the value of HLEN is 1000 in binary. How many bytes of options are being carried by this packet?
If an IPv4 packet, the value of HLEN is 1000 in binary, then 32 bytes of options are carried by this packet.
HLEN = 1000 = 8
8*4 = 32
38.What are open loop congestion control and closed-loop congestion control techniques?
Open-loop congestion control policies are applied to prevent congestion before it happens. The congestion control is handled either by the source or the destination.
Closed-loop congestion control technique is used to treat or alleviate congestion after it happens.
39.Which fields of the IPv4 header change from router to router?
Total length field and header checksum of IPv4 header change from router to router.
40.The value of HLEN in an IPv4 datagram is 7.How many option bytes are present?
If the value of the HLEN field is 7, then there are 28 (since 7 × 4 = 28) bytes included in the header.
41.Can the value of the header length in an IPv4 packet be less than 5?
The value of the header length field of an IP packet can never be less than 5 because every IP datagram must have at least a base header that has a fixed size of 20 bytes.
42.A host is sending 100 datagrams to another host. If the identification number of the first datagram is 1024, what is the identification number of the last(in IPv4)?
if a source is sending 100 datagrams and for the first datagram identification no is 1024 then for the last datagram identification number will be 1024 + 99 = 1123.
43.Explain the reason for the elimination of the checksum in the IPv6 header?
The checksum is eliminated in IPv6 because it is provided by upper-layer protocols; it is therefore not needed at this level.
44.Write down the name of three strategies used to handle the transmission from IPv4 to IPv6?
- Dual-stack
- Tunneling
- Header translation
45.What is tunneling?
A technique of internetworking called Tunneling is used when the source and destination networks of the same type are to be connected through a network of a different type.
46.An IP packet has arrived with the first 8 bits as 01000010. What is the version?
The first 4-bits show version i.e. 0100 which belongs to IP version 4.
47.What is fragmentation?
Fragmentation is an important function of the network layer. It is a technique in which gateways break up or divide larger packets into smaller ones called fragments. Each fragment is then sent as a separate internal packet. Each fragment has its own separate header and trailer. Sometimes, a fragmented datagram also gets fragmented when it encounters a network that handles smaller fragments. Thus, a datagram can be fragmented several times before it reaches its final destination. The reverse process of fragmentation is difficult. Reassembly of fragments is usually done by the destination host because each fragment has become an independent datagram.
48.Suppose the round trip propagation delay for a 10 Mbps Ethernet having a 48-bit jamming signal is 46.4 ms. What is the minimum frame size?
Transmission Speed = 10Mbps.
Round trip propagation delay = 46.4 ms
The minimum frame size = (Round Trip Propagation Delay) * (Transmission Speed) = 10*(10^6)*46.4*(10^-3) = 464 * 10^3 = 464 Kbit
49.In the slow start phase of the TCP congestion control algorithm, what is the size of the congestion window?
In the slow start phase of the TCP congestion control algorithm, the size of the congestion window increases exponentially.
50.What is the maximum window size for data transmission using Selective Reject protocol with n-bit frame sequence number?
The maximum window size for data transmission using the Selective Reject protocol with the n-bit frame sequence number is 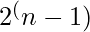 .
.
Share your thoughts in the comments
Please Login to comment...