How To Delete & Create VPC Network In The GCP
Last Updated :
01 Mar, 2024
Google Cloud Platform (GCP) provides a hearty systems administration foundation that permits clients to make and manage virtual organizations, known as virtual private clouds (VPCs). VPCs empower clients to safely interface with their cloud assets while keeping up with command-over network arrangements. Understanding VPC organization is fundamental for planning and conveying applications on GCP.
Virtual Private Cloud (VPC)
VPCs are a crucial part of the distributed computing foundation, offering associations the adaptability, security, and versatility expected to convey and deal with their applications and administrations in the cloud. Significant cloud suppliers, for example, Amazon Web Administrations (AWS), Microsoft Sky Blue, and Google Cloud Stage (GCP), offer VPC administrations as a component of their contributions.
- Subnet: A subnet, short for subnetwork, is a legitimate development of an IP organization. It permits a larger organization to be isolated into more modest, reasonable parts for different purposes like security, execution streamlining, or hierarchical design. Subnetting includes partitioning a larger organization into more modest, more productive subnetworks.
- Firewall Rules: Determines the rules that control traffic to and from assets inside a VPC. Clients can characterize firewall rules given IP locations, conventions, and ports.
- Route: A set of rules defining how network traffic should be directed within a VPC. Routes specify the next hop for traffic based on its destination IP address.
- Cloud Router: A Google Cloud administration that gives dynamic direction between VPC organizations and on-premises organizations or other Google Cloud organizations.
Serverless VPC
A serverless VPC is an idea where serverless registration administrations, like AWS Lambda or AWS API Gateway, are incorporated with a VPC. By coordinating serverless administration with a VPC, you can get to assets inside your VPC safely. This incorporation permits serverless capabilities to communicate with different assets, like databases or other services within your VPC, without exposing them to the public internet.
This is accomplished by utilizing a component called VPC endpoints, which permits serverless capabilities to interface with AWS benefits secretly through the AWS network instead of over the web.
Shared VPC
A common VPC (virtual private cloud) on the Google Cloud Platform (GCP) is a system administration tool that permits various undertakings to share a typical VPC organization. This empowers assets from various tasks to communicate with one another safely and effectively inside a similar network space.
IP Addresses
- An IP address (Web Convention Address) is a mathematical name numerical label assigned to each device with a PC network that involves the Web Convention for correspondence.
- IP addresses to fill two principal needs: network interface ID and area location.
- There are two renditions of IP addresses generally utilized: IPv4 and IPv6. IPv4 addresses are 32-digit mathematical addresses communicated as four decimal numbers isolated by periods (e.g., 192.0.2.1), while IPv6 addresses are 128-bit hexadecimal addresses isolated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
- IP addresses are dispensed progressively, with various reaches assigned for different purposes like confidential organizations (e.g., inside a VPC), public web use, and multicast tending.
- IP addresses are fundamental for directing information parcels across networks, empowering correspondence among gadgets and administrations on the web or inside confidential organizations like VPCs.
Creating a VPC network in GCP is a key stage in setting up your cloud framework
The following are more subtleties on each step referenced:
Navigate to VPC Networks:
- Sign in to your Google Cloud Control Console.
- Select the ideal task assuming that you have numerous ventures.
- Explore the “Networking” menu, normally tracked down in the left-hand sidebar.
- Click on “VPC network” to view existing VPC networks or create a new one.
Create a VPC Network:
- When you’re in the VPC networks segment, click on the “Create VPC network” button.
- Give a name to your VPC organization. This name ought to be expressive and special inside your task to distinguish it without any problem.
- Choose the region where you want to deploy this VPC network. This decides the geological place where your organization assets will be hosted.
- Configure the subnet settings: 1)Specify the name for the subnet. 2)Define the IP address range for the subnet. This range should be a subset of the IP range of the VPC network. 3) Choose the region and optionally, the availability zone where you want to deploy the subnet. You may configure additional options like enabling Private Google Access, Flow logs, and so on.
Optional Configurations:
- Define subnets: You can make various subnets inside your VPC network to isolate various pieces of your framework infrastructure. Each subnet can be related to an alternate region and availability zone.
- Firewall rules: Set up firewall rules to control the inbound and outbound traffic to and from your occasions inside the VPC network. You can determine conventions, ports, and IP reach to permit or deny traffic.
Create the VPC:
- Review the arrangements you’ve made for the VPC organization, subnets, and firewall rules.
- Click on “Create” to conclude the formation of the VPC network.
- Google Cloud platform will then, at that point, arrangement the important assets to set up your VPC network as per the specified configurations.
In the wake of making the VPC network, you can begin conveying your virtual machine instances, Kubernetes cluters, or other GCP administrations inside this organization. The VPC gives disconnection and command over your cloud assets, permitting you to connect and manage with your applications and administrations safely.
How to Delete VPC on GCP
Step 1: When you select VPC and click “Delete,” the entire VPC as well as the respecitev subnets are deleted.

Steps to deploy VPC on GCP
Step 1: Login to google cloud console and go to VPC networks. click on VPC networks page.
 Step 2: Click on ‘create VPC network’ .
Step 2: Click on ‘create VPC network’ .
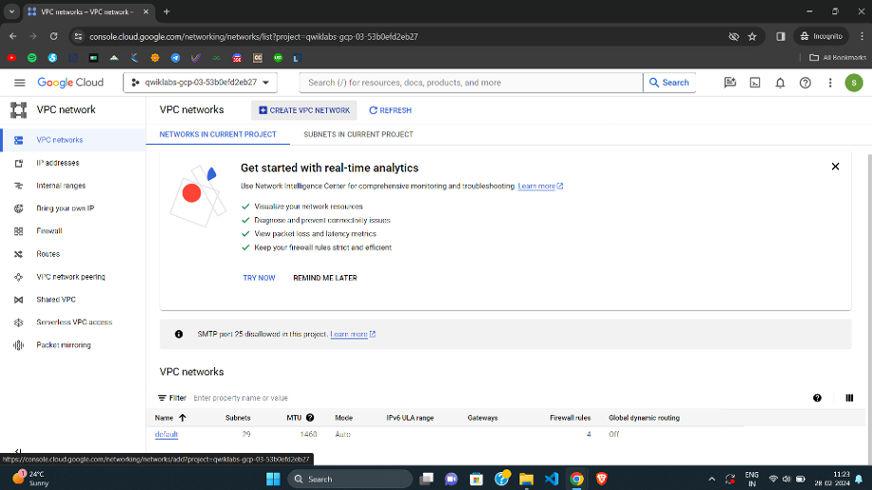
Step 3: We will get the following page, specify the following details.
- VPC name: vpc
- Description (optional): virtual private cloud.
- Subnet create mode: custom(if you choose automatic, it will create subnet in all regions automatically)
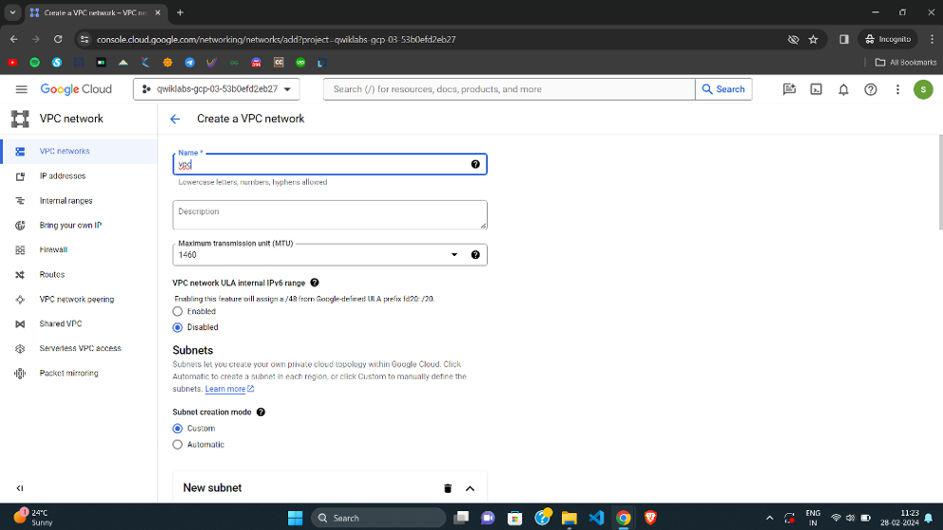
Step 4: Create subnet
- Subnet Name: subnet1
- Region: us-west1.
- IP address range: 10.0.0.0/16 (Specify the CIDR range as per requirement)
- Private Google Access: Off (If you keep this option as ‘ON’ then it will allow this subnet to make API calls to GCP services privately)
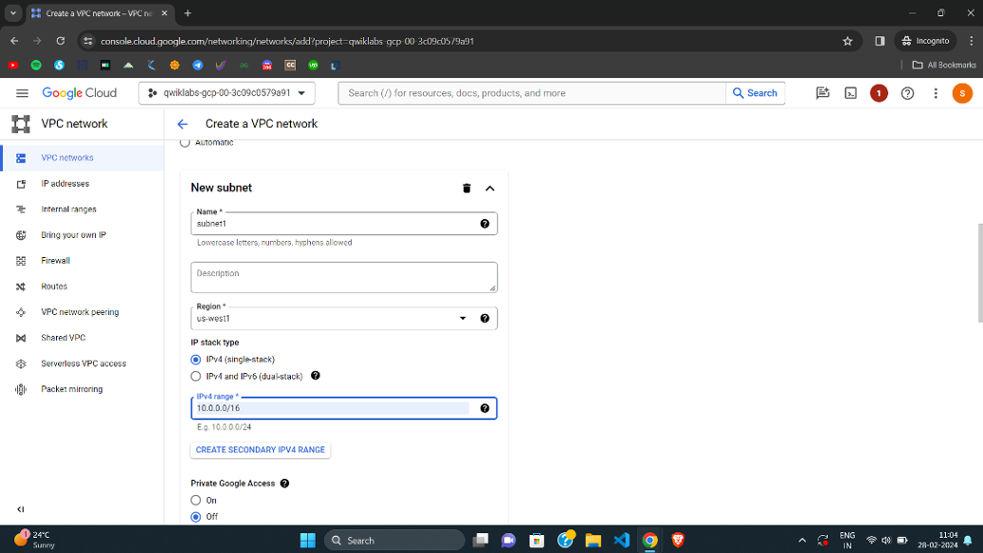
- Flow Logs: off
- and click on done.
- Firewall Rules: Allow Ingress ICMP, RDP and SSH protocols/ ports. ( You can define your own custom rules) .
- Dynamic Routing Mode: Regional
- and hit on create button.

Step 5: Verify VPC Network and Subnet, After the creation of VPC network, we will get following on VPC networks page, verify the VPC and subnet.

.webp)
Delete & Create VPC Network in the GCP – FAQ’s
What is the difference between a VPC and a subnet?
A VPC is a virtual network isolated from other networks in GCP, while a subnet is a segmented portion of the VPC’s IP address range.
Can I connect multiple VPC networks?
Yes, you can establish connectivity between VPC networks using VPC Peering or Cloud VPN/Interconnect.
How do firewall rules work in a VPC?
Firewall rules control inbound and outbound traffic to resources within a VPC based on specified criteria such as IP addresses, protocols, and ports.
Can I change the IP range of an existing subnet?
No, the IP range of a subnet cannot be changed after creation. You would need to create a new subnet with the desired IP range and migrate resources accordingly.
Is it possible to route traffic between on-premises networks and GCP VPCs?
Yes, you can use Cloud VPN or Cloud Interconnect to establish secure connections between on-premises networks and VPC networks in GCP.
Share your thoughts in the comments
Please Login to comment...