You just downloaded the latest version of your favorite distribution’s disk image and you are all ready to flash it to your USB and experience the latest and greatest, sounds great right? yeah, but before you press the install button there is an important verification step that helps to check the integrity of your file – Verifying Checksum.
What is Checksum?
Checksum, in simple terms, is a string of numbers derived from a file (which could be any software, movies, images, or documents) using a checksum algorithm. This should always produce the same string of numbers for the same file across devices and if there is even the smallest change within the file then the checksum of that particular file will be different. Two different files “ideally” can’t have the same checksum as two people can’t have the same fingerprint.
These strings of numbers are used to check the “integrity“ of a file to make sure that it has not been corrupted or tampered with in any way. To sum it up, a file produces a unique string of numbers, which is like its fingerprint. If you know the checksum of the original file then you could compare your file with the original one to verify if it has been corrupted, either unintentionally or intentionally by some malicious actor, in any manner.
Example:
A text file containing “apple” and “aapple” would have completely distinct checksums even though there is only a one-word difference.
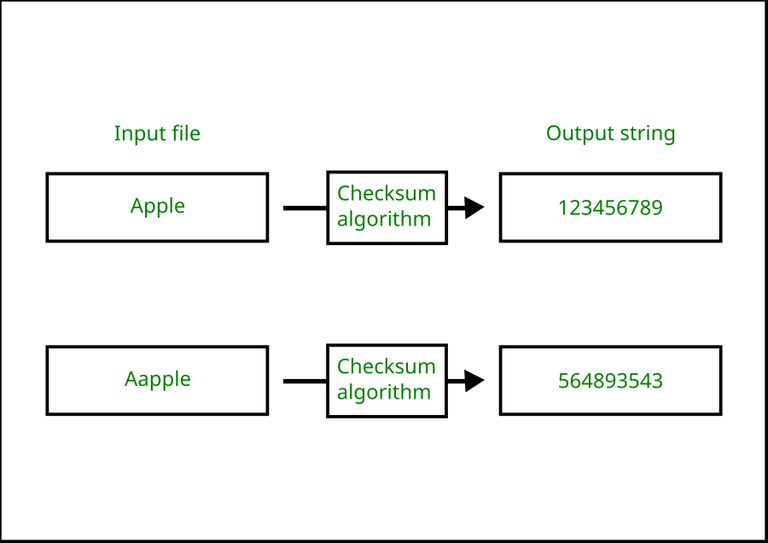
An Illustration showing different files yielding different checksums
Different types of algorithms
There are many types of algorithms to verify hashes but mainly there are Secured Hash Algorithms or SHA algorithms which include SHA1 and SHA 256 algorithms etc, and Message Digest 5 Algorithm or MD5. Currently, MD5 and SHA1 algorithms are not widely used for verification since researchers have found “collisions” in these algorithms, i.e. two different files with the same checksum were discovered; even though the probability of that happening is low, a well-funded organization with malicious intent might be able to reproduce the results.
Therefore, wherever possible, SHA256 should be the preferred algorithm for verification.
When to verify checksum?
Ideally, you should verify it whenever available; i.e. while downloading programs, movies, books, or anything; if the developer/creator has made checksum available – verify it.
What is integrity?
Integrity is to verify if the downloaded file is the same as the original file or not, if the file is exactly the same then the integrity of the file is not compromised. It is a subset of authenticity.
What is authenticity?
Authenticity includes checking the integrity of the file along with verifying the source of the information, if both integrity of the file and source is verified, then we can say that the file is authentic.
Does Checksums look for integrity or authenticity?
Checksums check the integrity of a file but are not a reliable way to check for authenticity. To check the authenticity GPG verification is recommended along with checksum verification.
Example: Let’s say a popular software website was hacked and the hacker swapped the program hosted on the site with their bad program and along with that they also swapped the checksum of the file to match the malicious one; in this case, the checksum of the file will be matching with the source -thus being integral- since the hacker also swapped the checksum of the original program which was hosted on the website but the program you downloaded will not be considered authentic as it’s not from the source that you expect.
Therefore, If you want to check the authenticity of a program you should take extra steps like GPG verification.
How to Install GTK Hash in Linux?
Method 1: Graphical method
Step 1: Download and install the “GTK hash“. For that, first search for the app store and open it.

Opening App Store
Step 2: Search for GTK hash in the search bar of the app store. It should appear now in the results.

Searching GTKHash
Step 3: Install GTK hash by clicking on the install button shown within the app store.
Install GTK hash
Method 2: Using Terminal
To install GtkHash using the terminal use the following command, and that’s it.
flatpak install org.gtkhash.gtkhash

Installing GtkHash via the command line
How to verify checksums in Linux?
Method 1: Using GtkHash Application
Step 1: Open the GtkHash app that you just downloaded, you should now see the home screen of GtkHash.

GTK Hash
Step 2: Open the app and go to edit>preferences and select all the algorithms you want to check for, the default layout should serve you well for general purposes, but if you want to customize a bit, you can select all the algorithms that you wish to check against.
Selecting Preferences
Step 3: Browse the file of which you want to verify the checksum by clicking against the “File” box and browsing for it.

Browse the file
Step 4: Copy and Paste the original checksum value from the website or file to the “Check” box.

Pasting the checksum from the website or file to GTK Hash
Step 5: Click on “hash”. Now it will compute the hash of the file. in our case, it will compute SHA256, SHA1, MD5 and CRC32, as we set the default values in the preferences.

Click on hash
Step 6: If any one of the file’s hash matches the value you copy-pasted, then it will show a checkmark next to it as you can see in the image below.

Check mark showing against the matched
Method 2: Terminal method
To verify checksums in Linux using the terminal you should follow the following steps:
Step 1: Open the folder where you have the program or file stored in the terminal.
Step 2: Now verify the hash
As an example, we will be verifying Linux mint XFCE’s disk image using different algorithms
1. Verifying SHA256 checksum:
Sha 256 is the most popular checksum for verification purposes, so it is very likely that you may find it on the website of the file that you just downloaded. To verify the Sha256 checksum enter the following command into the terminal.
sha256sum "filename"
For our example it would be:
sha256sum linuxmint-21.1-xfce-64bit.iso
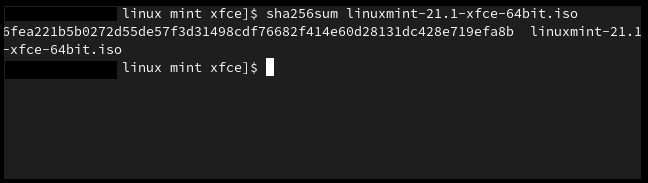
Verifying SHA256
2. Verifying SHA1 checksum:
As discussed earlier researchers have found collision in this algorithm and you may not find it on the website of the software, but if for some reason, you only have SHA1 to verify, then here is the command.
sha1sum "filename"
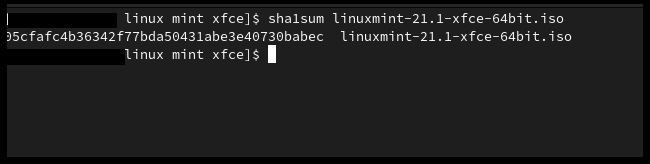
Verifying SHA1
3. Verifying MD5 checksum
Like SHA1, finding MD5 on a website is rare but if you only have that then enter this command into the terminal.
md5sum "filename"
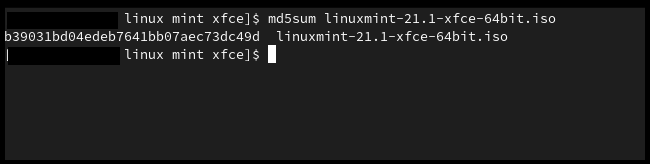
Verifying MD5
Step 3: Now, compare the output you got in the terminal with the checksum given in the website or file. If both are the same then the integrity of the file is verified.
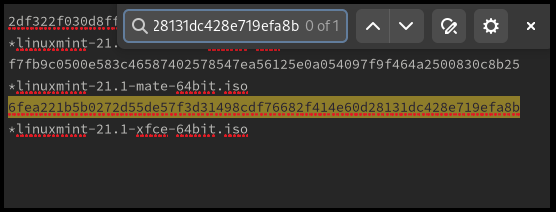
Comparing the output with the checksum in the text file
Share your thoughts in the comments
Please Login to comment...