How To Create Azure Container Registry Using Terraform ?
Last Updated :
26 Mar, 2024
The challenges of managing containers in a larger environment affect not only the efficiency and effectiveness but also the scalability and resilience of the applications. They give an independent and continuous environment for the applications to execute the same and deployed everywhere effortlessly. Microsoft Azure Container Registry or ACR is Microsoft’s fully managed, private Docker container registry service ensuring safety and easy access to images saved.
As we embark on this journey, I will demonstrate how to leverage Azure Terraform template provider to build an Azure Container Registry instance. In this lecture, we will walk through the essential configuration process starting with the authentication towards Azure, creating the ACR resource and finally applying the needed configuration marks in order to create the registry. After following this handbook to the end, you’ll see how to use Terraform effectively to both create and manage your Azure Container Registry which will be used for your extremely important application deployments without much difficulties.
What Is Azure Container Registry?
Azure Container Registry (ACR) is a duplexed by Microsoft Docker container registry service that runs on Azure. It is made to saves, administer and songs private containers images and provides a secure platform to run the same app deployed to diverse environments.
Key Features And Capabilities Of Azure Container Registry
- Private Container Registry: Using ACR, you can save private Docker container repositories into any Azure subscription which enables you to protect your images in a safe place. First off, it allows for applying precise privileges and authentication mechanisms, which ultimately results in only valid users and systems accessing your containers.
- Geo-replication: ACR provides you geo-replication facility due to which you can create version of container registry in more than one Azure cities. This lets you have more places from which you can deploy the images, or to improve efficiency, get the images near the targets of deployment.
- Webhooks: ACR encloses webhooks feature alongside with the registry so that they can analyse if certain events happen like image pushes or removals, notification or actions can be sent. This element takes the integration of the service with the system which can be used for automation.
- Vulnerability Scanning: The Azure container registry integration with the Azure Security Center allows you to perform vulnerability scanning on your container images submission. This feature helps to identify the security vulnerabilities of your container pictures and allows for you to solve the problems before the start of the deployment.
- Azure Active Directory Integration: ACR can acknowledge with Azure Active Directory (Azure AD) for authentication and access management. Thus, Azure Container Registry is basically using your current Azure Active Directory credentials and role-based access controls to permit access management.
What Is Terraform?
Terraform is HashiCorp’s IaC tool based on the open source that helps lay the base for the infrastructure. It lets you specify the sizes, allocations of resources, and Roles in the cloud infrastructure describing only what you need to create and control everything. As the provider for a number of the cloud providers including Azure, AWS, Google Cloud and many others, Terraform makes the provisioning and management of these infrastructures an easy task.
Key Features And Benefits Of Terraform
- Infrastructure as Code: Terraform enforces you to describe the totality of your infrastructure (e.g. virtual machines, networks, databases, containers) utilizing a human-readable constructor language called HashiCorp Configuration Language (HCL). In today’s cloud-native computing environment, infrastructure is not required as code, so the code is versioned controlled, worked on collaboratively, and deployed consistently from one environment to another.
- Cloud-Agnostic: With Terraform, it is possible to configure a lot of cloud providers and job choices, for example, Azure, AWS, Google Cloud, DigitalOcean, and so on. This is convenient especially when managing multiple clouds or hybrid cloud environments, as the same workflows and tooling can be used for administration.
- State Management: Terraform monitors the status of your infrastructure resource and keeps a state file that saves the actual state and reflects the desired state of your resources. The state file here is for the terraform to markedly realize dependable and smooth update, only the necessary changes being observed on the infrastructure in question.
- Dependency Management: Terraform predetermines all dependencies and changes the order of these resources that are to be created, updated, or removed based on interdependencies.
- Plan and Apply: The Terraform employs a workflow of plan and apply, where an execution plan is generated prior to changes to your infrastructure which lists the changes Terraform will make. You can create, update, or delete resources as needed only if you approve and reject the necessary steps after reviewing the plan.
Create Azure Container Registry Using Terraform: A Practical Step-by-Step Guide
Step 1: Install Terraform
- First, you need to have Terraform installed on your local machine or the environment where you’ll be working. You can download the appropriate package for your operating system from the official Terraform website
Step 2. Set Up Azure Credentials
Terraform needs to authenticate with Azure to manage resources. You can set up authentication in one of the following ways:
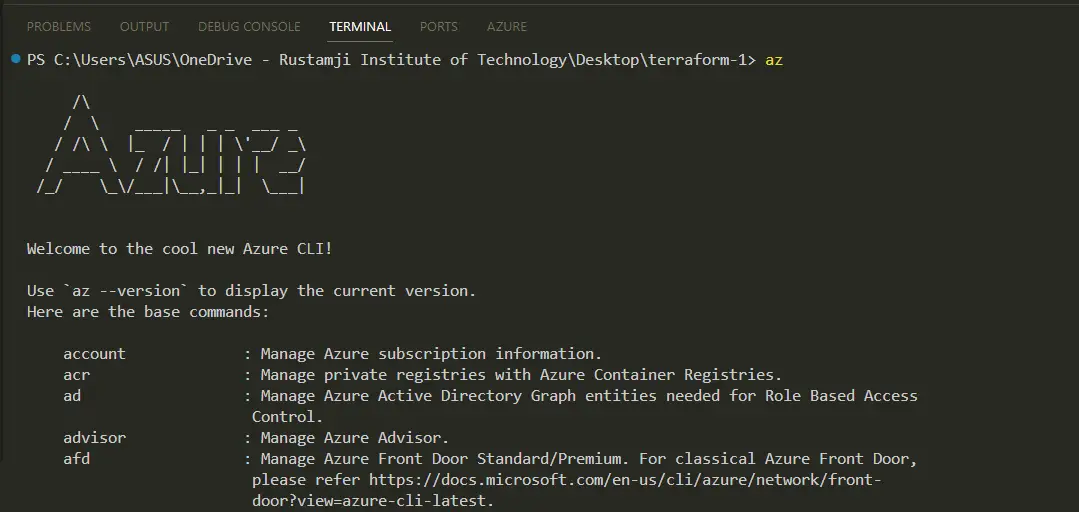
- Service Principal: Create an Azure Service Principal and set the required environment variables (ARM_SUBSCRIPTION_ID, ARM_CLIENT_ID, ARM_CLIENT_SECRET, and ARM_TENANT_ID).
az ad sp create-for-rbac --name "ServicePrincipalName" --role contributor --scopes /subscriptions/<SUBSCRIPTION_ID>
$env:ARM_SUBSCRIPTION_ID="<SUBSCRIPTION_ID>"
$env:ARM_CLIENT_ID="<APP_ID>"
$env:ARM_CLIENT_SECRET="<PASSWORD>"
$env:ARM_TENANT_ID="<TENANT_ID>"
- Managed Identity: If you’re running Terraform from an Azure resource (e.g., a Virtual Machine), you can use a Managed Identity.
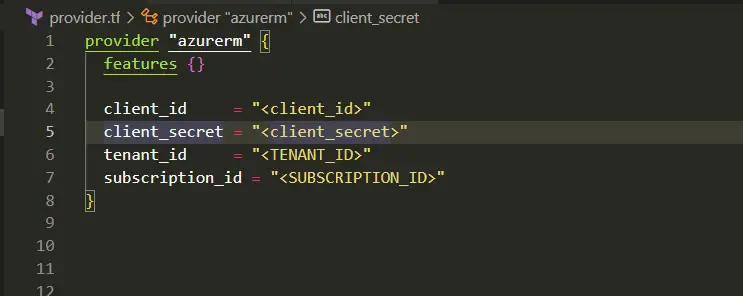
Step 3: Configure Terraform
- In your Terraform configuration file (provider.tf), add the following provider block:
provider "azurerm" {
subscription_id = "<SUBSCRIPTION_ID>"
client_id = "<APP_ID>"
client_secret = "<PASSWORD>"
tenant_id = "<TENANT_ID>"
features {}
}
Step 4: Create Terraform Configuration File
- Create a new file (e.g., main.tf) in your directory and define the Azure Resource Group using the azurerm_resource_group resource:
# Create a resource group
resource "azurerm_resource_group" "rg" {
name = "myResourceGroup"
location = "westus"
}
# Create an Azure Container Registry
resource "azurerm_container_registry" "acr" {
name = "myFintricityRegistry"
resource_group_name = azurerm_resource_group.rg.name
location = azurerm_resource_group.rg.location
sku = "Premium"
admin_enabled = false
}
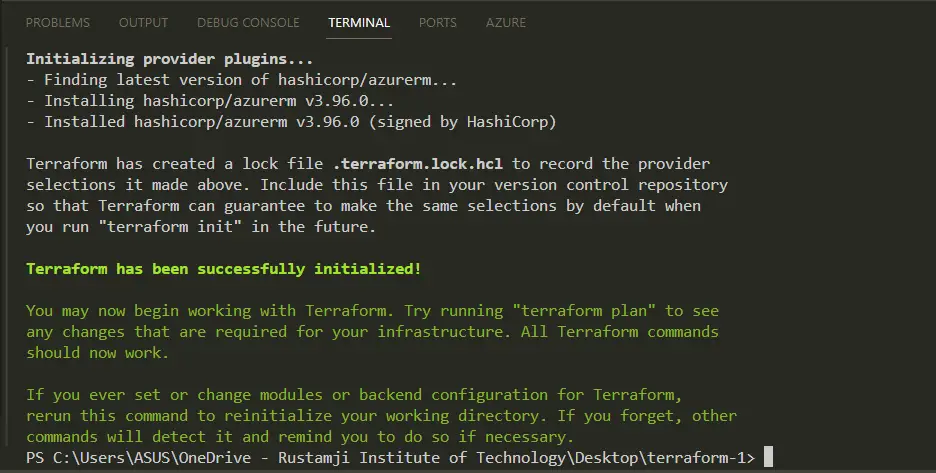
Step 5: Initialize Terraform
- Initialize Terraform by running the following command:
terraform init
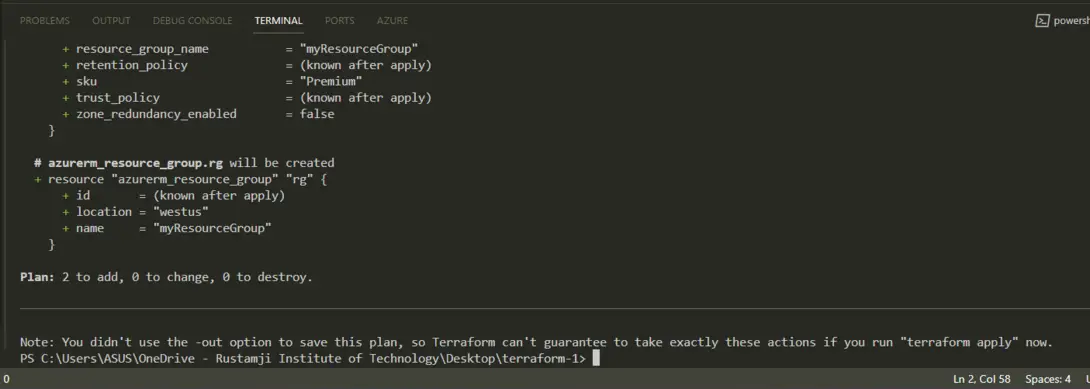
Step 6: Plan Terraform Changes
- Before applying the changes, you can preview the planned actions by running:
terraform plan
- This command shows you the resources that will be created, updated, or deleted based on your configuration.
Step 7: Apply Terraform Changes
- If you’re satisfied with the planned changes, you can apply them by running:
terraform apply
- Terraform will prompt you to confirm the changes before proceeding. Type yes to confirm and create the Azure Resource Group.
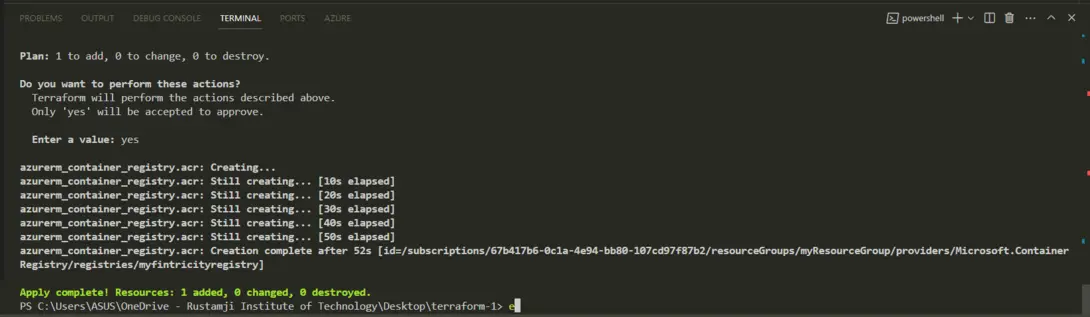
Step 7: Verifying The Changes
- Open the azure portal and look for the newly made azure container registry with terraform:
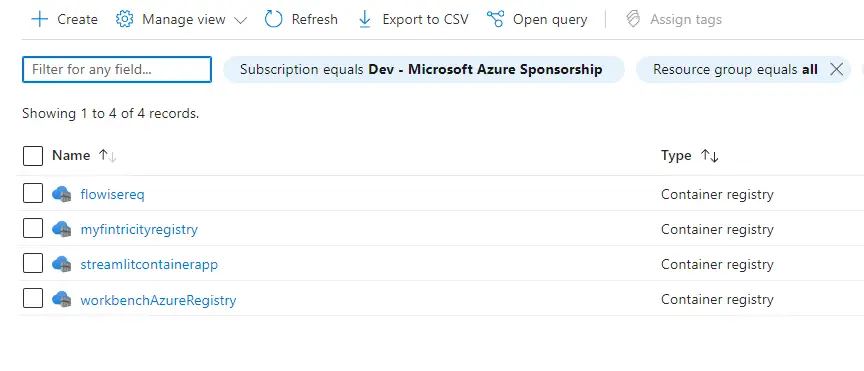
Step 8: Deleting The Resource Group
- It is very important to delete the resource group or anything made via terraform when they are not in use. It can be deleted using the following command:
terraform destroy

Advantages To Create Azure Container Registry With Terraform
Creating an Azure Container Registry (ACR) using Terraform offers several advantages the following are a few:
- Infrastructure as Code: It is with the help of this resource that you not only designate all the necessary infrastructure but also make it into a declarative configuration file. This allows a trusted choice, a uniform, continuous, and automated change in infrastructure.
- Version Control: Keeps record of terraform configurations in a version control system like Git will help you track remote changes, team up with other devs and, if needed, roll back to previous version.
- Dependency Management: Terraform handles the resource dependencies in a predictable way with zero errors, as the data is depended on other resources being provisioned before any changes happen.
- Parallel Execution: When quickly building or improving structures infrastructures Terraform form can automate the build processes by acting on multiple resources at the same time rather than doing things one after another like scripted methods.
- State Management: Terraform doc website keeps a state file that shows which world resources it manages. It is a state file which Terraform uses to figure the correct state and make necessary changes while tracking every modification. That means no surprise in deployment.
Disadvantages To create azure container registry with terraform:
While using Terraform to create an Azure Container Registry (ACR) offers several advantages, there are also some potential disadvantages to consider:While using Terraform to create an Azure Container Registry (ACR) offers several advantages, there are also some potential disadvantages to consider:
- Learning Curve: Metaform, on the other hand, has its own domain-specific language (DSL) as well as syntax which at times are a bit of a challenge for a newbie such as those with no infrastructure as code (IaC) or declarative configuration knowledge.
- State File Management: It uses a state file that keeps information about resources it monitors as terrforming. If the backup file of a state becomes corrupt, lost, or changed via a means other than Terraform, then the result will be things going wrong and inconsistencies. Backup and recovery stating is very important in regard to file management.
- Terraform Provider Updates: Terraform providers’ providers are updated to keep pace with new resource types and features which are incorporated in Azure provider as well. As Terraform is being further developed, including new provider types and plug-ins, it can be challenging to make sure that you are using up to date versions, and that they are compatible with your existing infrastructure.
- Drift Management: Drift detection is one of the Terraform particularly strong capabilities, but drift mediation and management will be of more complexity especially in environments with many resources and different teams in development.
- Limited Visibility and Debugging: Solving the obstacles that are Terraform configurations and resource deployment problems require a lot of knowledge from the painter’s aspect and the strict debugging capabilities.
Conclusion
In the conclusion, make Terraform a powerful tool for creating and administering the Azure Container Registry (ACR) systems, it becomes a vital choice for organizations that plan to adapt to IaC practices, and they can enjoy the benefits of declarative infrastructure provisioning.
With the Terraform code you’ll be able to reliably choose ACR Configuration as well as version control your infrastructure, efficient collaboration with members of the same team, and consistent repeatable deployments in different environments. The Terraform state mgmt and dependency control features streamline the process of creating and arranging ACRs with their dependencies to the way they are supposed to be in the correct order without recurring to manual intervention.
Also, there is a degree of compatibility offered by Terraform through cross-platform and cloud-agnostic approach. Consequently, it is possible to treat your ACR together with other AZ resources or even resources from other cloud providers using a unified workflow. According to the modular configuration technique writing stand-alone modules helps a lot with code reusability and maintainability. Moreover documentation generators provide automated documentation generation feature that simplifies understanding and support of your infrastructure.
Azure Container Registry Using Terraform – FAQ’s
How Do I Authenticate Terraform To Create An ACR In Azure?
You can use a service principal with the appropriate permissions or authenticate with the Azure CLI. Terraform will then use the authenticated credentials to provision resources in your Azure subscription.
Can I Use Terraform To Manage ACR Tasks, Webhooks, Or Repositories?
Yes, Terraform supports managing various ACR resources beyond the registry itself, such as tasks, webhooks, and repositories, using the azurerm_container_registry_* resource types.
How Can I Version Control My Terraform Configurations For ACR?
You can store your Terraform configurations in a version control system like Git. This allows you to track changes, collaborate with team members, and roll back to previous versions if needed.
What Is The Recommended Way To Handle Sensitive Data Like ACR Admin Credentials In Terraform?
It’s best to use a secure storage solution like Azure Key Vault or HashiCorp Vault to store sensitive data and retrieve it during Terraform runs, rather than hardcoding values in your configurations.
Can I Use Terraform To Manage Acr In Multiple Azure Subscriptions Or Environments?
Yes, Terraform supports managing resources across multiple Azure subscriptions or environments by using separate state files or workspaces. You can also use modules or configuration files to promote code reusability across different environments.
Share your thoughts in the comments
Please Login to comment...