How To Create AWS IAM Roles Using Terraform?
Last Updated :
26 Feb, 2024
Terraform is an IAAC tool which is used provision infrastructure . Here in this guide i will first discuss what is terraform . Then i will discuss what is IAM Role and in which scenarios we should use IAM Role . Then i will walk you through the different steps to create an IAM Role for an EC2 service having CloudWatch and SNS full access policy .
What is Terraform ?
Terraform is a Infrastructure As Code tool which uses declarative configurational language that is Hashicorp Configurational Language (HCL) to define and provision infrastructure . Terraform has the ability to provision and manage infrastructure across multiple cloud such as AWS , Azure ,GCP , etc . This ability helps the organizations to adopt multi cloud strategy and avoid depending on only one type of cloud platform . When users create infrastructure manually by using the AWS console or Azure console or other cloud provider console , there is a chance that they may face manual error . Fixing these error may take too much time . But if the same task is done using terraform it can entirely eliminate the manual error occurrence . This makes terraform more reliable to provision infrastructure . Overall terraform ‘s simplicity , cross platform compatibility and automation capabilities makes it an essential tool to maintain control, reliability and scalability .
What is IAM Role ?
An IAM Role is an AWS Identity and Access Management resource which defines a set of policies to ensure AWS services access other necessary AWS resources or services . IAM roles can be attached various AWS services such as EC2 , Lambda , S3 and many more . This allows the AWS services to have temporary permissions to do specific tasks . IAM Role has a ability to establish trust relationships, defining which AWS accounts, IAM users or AWS services are allowed to assume the role .
IAM Role is mainly used in these scenarios :
- To grant permissions to AWS services such as EC2 , Lambda , etc .
- To enable cross account access for sharing resources .
- Temporary permissions for applications and services running on AWS infrastructure .
Hence we can say IAM Role plays an important role in ensuring the security and integrity of AWS cloud platform by minimizing the exposure of long term passwords .
Pre-requisites
Before moving to next section make sure that you have installed terraform on your system , if you have not installed terraform , then follow this detailed geeksforgeeks article Setup Terraform On Linux and Windows Machine to install terraform on your system .
Steps To Create IAM Role Using Terraform
Step 1 : Mention the provider and region in which you want to create the AWS resources .
provider.tf
provider "aws" {
region = "us-east-1"
}

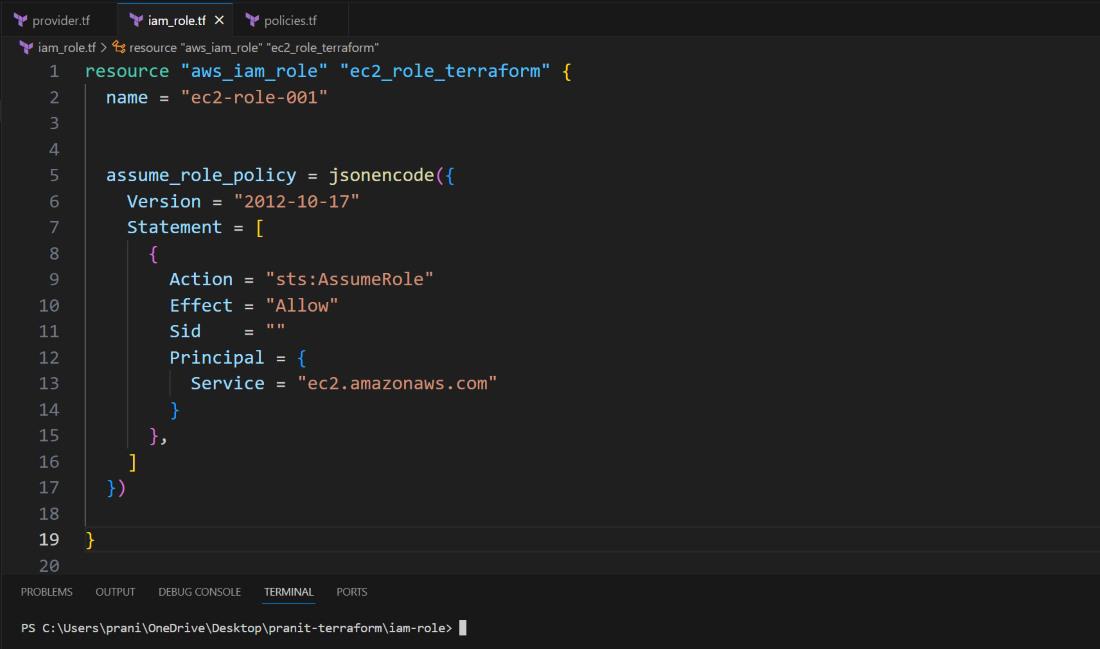
Step 2 : Then create an IAM Role for particular AWS service . Here i have created IAM Role for EC2 service .
iam-role.tf
resource "aws_iam_role" "ec2_role_terraform" {
name = "ec2-role-001"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = "sts:AssumeRole"
Effect = "Allow"
Sid = ""
Principal = {
Service = "ec2.amazonaws.com"
}
},
]
})
}
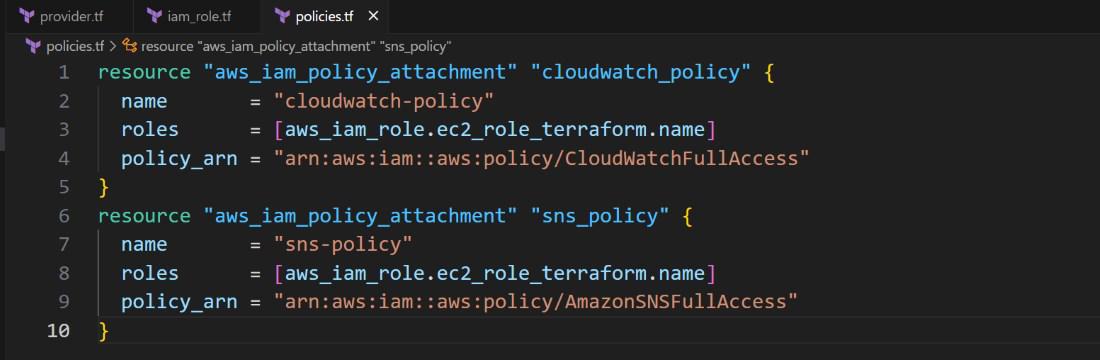
Step 3 : Attach policies to the IAM Role . Here i have attached the cloudwatch and sns full access policy to the IAM Role .
policies.tf
resource "aws_iam_policy_attachment" "cloudwatch_policy" {
name = "cloudwatch-policy"
roles = [aws_iam_role.ec2_role_terraform.name]
policy_arn = "arn:aws:iam::aws:policy/CloudWatchFullAccess"
}
resource "aws_iam_policy_attachment" "sns_policy" {
name = "sns-policy"
roles = [aws_iam_role.ec2_role_terraform.name]
policy_arn = "arn:aws:iam::aws:policy/AmazonSNSFullAccess"
}
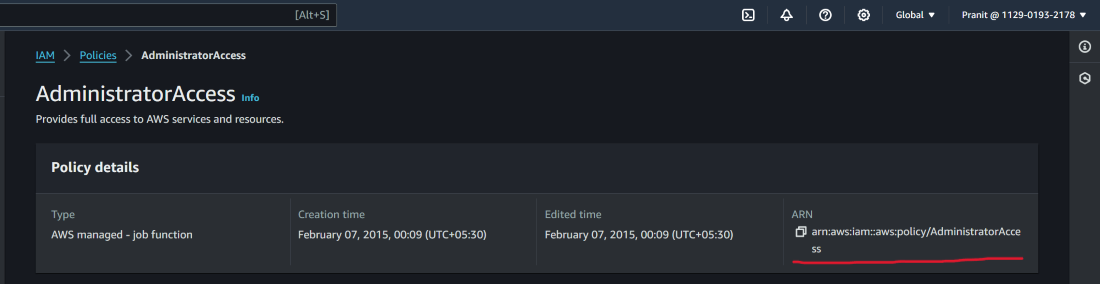
If you want to add any other policy then you just have to copy the policy_arn of that policy . To do this you have to go the AWS IAM dashboard . Here in policies you will see a list of policy . Select your preferred policy and then copy the ARN .
Step 4 : Now execute the terraform file using the below commands one by one .
terraform init
terraform plan
terraform apply

Step 5 : Now verify the IAM Role is created on AWS Console or not .

Conclusion
Here in this article we have first learned about terraform and then learned about what is AWS IAM Role . Then we have followed the steps to create a IAM Role for an EC2 service with AmazonSNSFullAccess and CloudWatchFullAccess policy . Finally we have verified that whether the IAM Role for EC2 is created or not on AWS console .
AWS IAM Roles Using Terraform-FAQ’s
What is trust policy in AWS IAM ?
Trust policy specify the trusted services that needed to assume the IAM Role .
How to create multiple IAM Roles in a single terraform file ?
You can create multiple IAM Roles by using multiple ‘aws_iam_role‘ resource in a single terraform file .
When to create IAM Roles ?
By default AWS does not allow its resource to access other AWS resources . Here IAM Roles are used to grant permissions to these AWS services to access other AWS resources .
How to create IAM Role for specific AWS service like EC2 or Lambda ?
You can specify the service name in the ‘Principal‘ section of ‘assume_role_policy‘ .
How to grant temporary permissions to IAM Roles using terraform ?
Temporary permissions can be granted to IAM Roles by specifying the session duration in the ‘DurationSeconds‘ fields in ‘assume_role_policy‘ .
Share your thoughts in the comments
Please Login to comment...