Securing AWS Lambda Functions With IAM Roles And Policies
Last Updated :
27 Feb, 2024
AWS Lambda is a serverless computing service that helps in executing code without any management of servers while AWS IAM is an essential security component that allows authorized individuals or services to have access of other AWS resources. These two AWS services are very important on the AWS cloud platform. Here in this guide, I have first discussed what is AWS Lambda service. Then discuss about AWS IAM service and why it is required to secure your Lambda function using IAM roles and policies. After this, I walked you through the different steps to create an IAM role and attach it to the Lambda function for secure access to other AWS services.
What is AWS Lambda?
AWS Lambda is a serverless computing service that runs the code without any management of servers. The code is written in various programming languages like Python, Node.Js, Java, Golang, .NET, Ruby, and many more. AWS Lambda function can automatically triggered by any specific event configured or at any scheduled time. For example, suppose an organization is using an EC2 instance for its application deployment. Some of the EC2 instances are not used for a long period. So by using the Lambda function organizations can automate the deletion of such unused EC2 instances after it exceeds a threshold time limit. Using AWS Lambda organizations can create better cost-effective infrastructure on the AWS cloud platform. Apart from this, AWS Lambda can also automatically scale up and scale down on the number of requests it receives. Also while executing a Lambda function users do not manage the servers which incur less cost. In summary, we can say AWS Lambda simplifies the development of serverless applications and provides a flexible, scalable, and cost-effective platform for running code without any server management.
What is AWS IAM?
AWS Identity and Access Management (IAM) is a web service that allows organizations to access other AWS services or resources more securely on the AWS cloud platform. IAM service can be integrated with other AWS services like EC2, Lambda, SNS, and many more. IAM manages users, groups, and roles on the AWS cloud environment ensuring that only authorized individuals or services have access to the AWS resources.
Some of the key features of AWS IAM service are :
- IAM allows to creation of different AWS users with each having unique security credentials.
- Permissions can be attached to various AWS users by grouping them together. This ensures access management for multiple users with similar needs.
- IAM also provides multi-factor authentication (MFA). This MFA provides an additional layer of security beyond the username and password.
In summary, we can say AWS IAM is a fundamental security AWS component that helps organizations maintain security, compliance, and governance on the AWS cloud platform.
Why secure Lambda Functions using IAM Roles and Policies?
Securing the Lambda function using IAM roles and policies is a crucial task on the AWS cloud platform. This is so because for the following reasons :
- IAM attaches permissions to Lambda functions to ensure that only the intended services and resources should be accessed by AWS Lambda. By attaching the roles and permissions to the Lambda function, users can minimize the unauthorized access or misuse of AWS resources.
- IAM roles can be attached temporarily to the AWS Lambda function which minimizes the exposure of any long-term security credentials.
- If any unauthorized person tries to access the Lambda function, these IAM roles can restrict the actions that a Lambda function can perform on the cloud environment.
- IAM roles grant secure access to other AWS account’s Lambda functions.
In summary, we can say securing the Lambda function using IAM roles and policies is an essential task to maintain integrity and confidentiality on the AWS cloud platform.
Steps To Secure Lambda Function With IAM Roles and Policies
Step 1: Go to the IAM dashboard and select Roles on the left side of the dashboard.
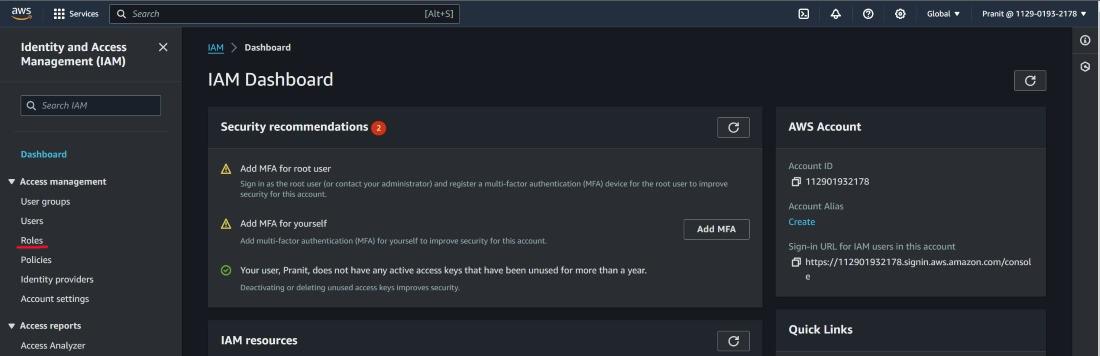
Step 2 : Then select create role at top right corner of the page .
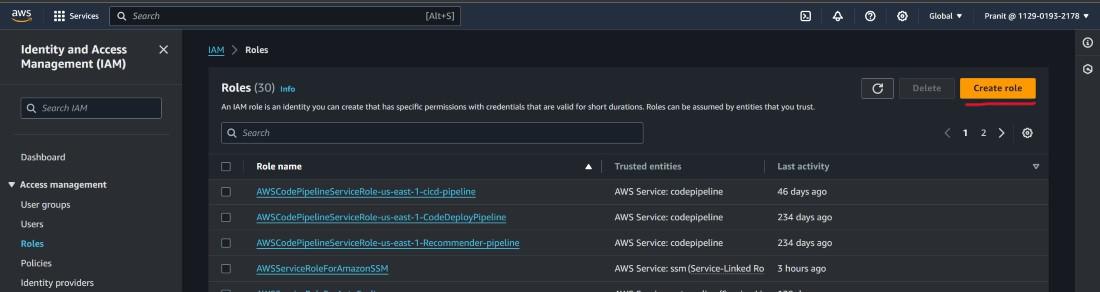
Step 3 : Select Lambda service and click next.

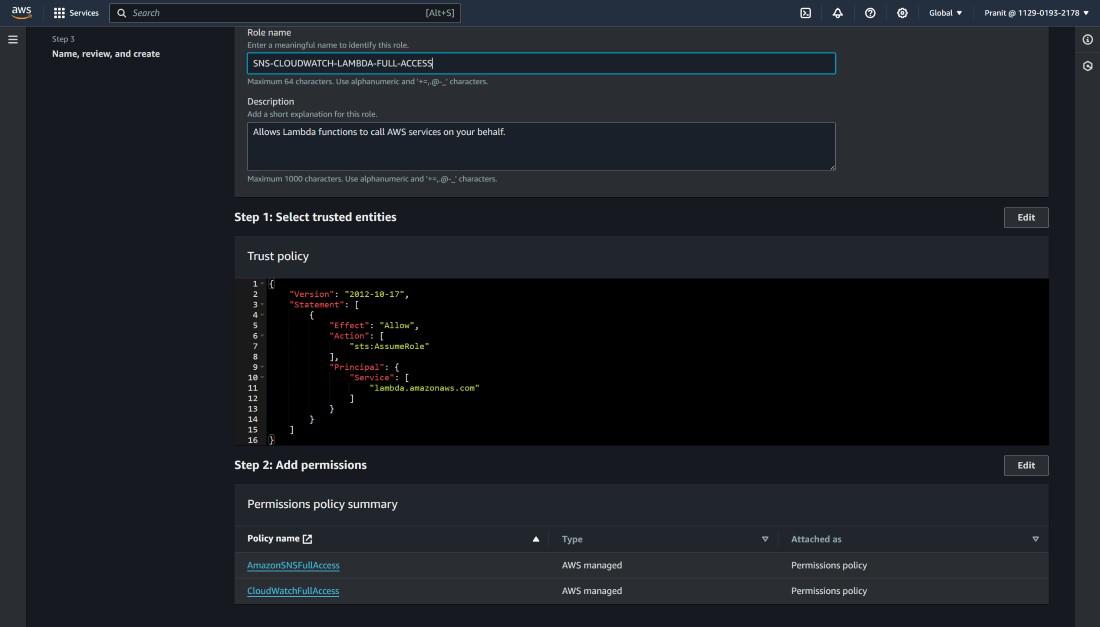
Step 4 : Now add some permission policies to the IAM role and click next . Here i have attached SNS and Cloudwatch full access permissions .
Step 5 : Now give the IAM role a name and select create role . After this step you have successfully created an IAM Role with some policies .
Step 6 : Then go to AWS Lambda dashboard and select create function .
Step 7 : Then give a name to the Lambda function and also select a runtime . Attach the IAM role created in the Step 5 to this Lambda function and select create function .

Conclusion
Here in this article you have first learned what is AWS Lambda . Then you have learned What is AWS IAM service and why to secure the Lambda function using IAM roles and policies . After this you have implemented the steps to create an IAM role and attach some policies to it, and later while creating the Lambda function you have to use this IAM role for secure access of other AWS services .
Securing AWS Lambda Functions with IAM Roles and Policies-FAQ’s
Why it is required to secure AWS Lambda functions using IAM ?
Securing AWS Lambda functions using IAM is essential to minimize the risk of unauthorize access and misuse of AWS resources .
How IAM policies are structured ?
IAM policies are the JSON documents with defined permissions .
How to monitor the AWS Lambda functions ?
By observing AWS CloudWatch logs you can monitor AWS Lambda functions .
Does AWS Lambda automatically scales up or we have to do it manually ?
AWS Lambda function automatically scales up or down on the amount of traffic it receives .
What is the key difference between AWS Lambda and AWS EC2 service ?
In AWS Lambda we can write a code and execute it without any management of servers but in EC2 we have to manage the servers to execute the code .
Share your thoughts in the comments
Please Login to comment...