A Digital Signature is a verification method made by the recipient to ensure the message was sent from the authenticated identity. When a customer signs a check, the bank must verify that he issued that specific check. In this case, a signature on a document acts as a sign of authentication and verifies that the document is authentic.
Suppose we have:
- Alice is the entity that sends a message or initiates communication.
- Bob represents the recipient or receiver of the message.
- Eve represents an eavesdropper or adversary who may attempt to intercept or tamper with the communication.
In Public Key cryptography (also known as Asymmetric cryptography), the communication process is as follows:
- Alice encrypts the message using Bob’s public key.
- The encrypted message reaches Bob.
- Bob decrypts the message sent by Alice using his private key.
Now, suppose when Alice sends a message to Bob, then Bob will check if the sender is authentic; to ensure that it was Alice who sent the message, not Eve. For this, Bob can ask Alice to sign the message electronically. So we can say that an electronic signature can prove that Alice is authentic and is the one sending the message. We called this type of signature a digital signature.
What is Digital Signature?
Digital Signature is a verification method. Digital signatures do not provide confidential communication. If you want to achieve confidentiality, both the message and the signature must be encrypted using either a secret key or a public key cryptosystem. This additional layer of security can be incorporated into a basic digital signature scheme.

Model of Digital Signature Process
Methods of Digital Signature
These two are standard Approaches to implement the Digital Signature:
- Rivest-Shamir-Adleman (RSA)
- Digital Signature Algorithm (DSA)
Rivest-Shamir-Adleman (RSA)
In the RSA approach, the message that needs to be signed is first fed into a hash function that generates a secure hash code of fixed length. The sender’s private key is then used to encrypt the hash code which makes it signature. The next step involves sending both the signature and the message to the intended receiver. For validation purposes, after receiving the message, the recipient first computes its hash-code. The sender’s public key is applied by recipient to decrypt this already encrypted signature. In case if decrypted signature corresponds to recipient-produced hashcode, that means that signature would be considered as valid. Since only the sender has access to the private key, only they could have produced a valid signature.
You can refer the below diagram for RSA, here,
- M = Message or Plaintext
- H = Hash Function
- || = bundle the plantext and hash function (hash digest)
- E = Encryption Algorithm
- D = Decryption Algorithm
- PUa = Public key of sender
- PRa = Private key of sender

RSA approach
Digital Signature Algorithm (DSA)
The DSA (Digital Signature Algorithm) approach involves using of a hash function to create a hash code, same as RSA. This hash code is combined with a randomly generated number k as an input to a signature function. The signature function depends on the sender’s private key (PRa) as well as a set of parameters that are known to a group of communicating principals. This set can be considered as a global public key (PUG). The output of the signature function is a signature with two components, s and r. When an incoming message is received, a hash code is generated for the message. This hash code is then combined with the signature and input into a verification function. The verification function depends on the global public key as well as the sender’s public key (PUa) which is paired with the sender’s private key. The output of the verification function returns a value equal to the signature’s component r, if the signature is valid. The signature function is designed in such a way that only the sender, with knowledge of the private key, can produce a valid signature.
You can refer below diagram for DSA, where,
- M = Message or Plaintext
- H = Hash Function
- || = bundle the plantext and hash function (hash digest)
- E = Encryption Algorithm
- D = Decryption Algorithm
- PUa = Public key of sender
- PRa = Public key of sender
- Sig = Signature function
- Ver = Verification function
- PUG = Global public Key

DSA Approach
Primary Termologies
- User’s Private Key (PR): This key is publicly known and can be shared with anyone. It’s used to verify digital signatures created with a corresponding private key.
- User’s Public Key (PU): A top-secret cryptographic key only possessed by the user is used in DSA algorithm’s digital signature generation. As it is, the private key must be kept secret and secure because it proves that a given user is genuine.
- Signing (Sig): Signing involves creating a digital signature with the help of a user’s private key. In case of DSA, this process requires mathematical operations to be performed on the message that should be signed using a given private key in order to generate a unique signature for that message.
- Verifying (Ver): Verifying is the process of verifying whether or not a digital signature has been forged using its corresponding public key. In DSA, this involves comparing the messages hash against the verification value through mathematical operations between two binary strings – one representing an encrypted data and another one representing plain-text original message.
Steps to Perform DSA
The Digital Signature Algorithm (DSA) is a public-key technique (i.e., assymetric cryptography) and it is used to provide only the digital signature function, and it cannot be used for encryption or key exchange.
The Steps to perform the Digital Signature Algorithm can be broadly divided into:
- Global Public-Key Components
- User’s Private Key
- User’s Public Key
- Signing
- Verifying
1. Global Public-Key Components
There are three parameters that are public and can be shared to a set of users.
- A prime number p is chosen with a length between 512 and 1024 bits such that q divides (p – 1). So, p is prime number where 2L-1 < p <2L for 512<= L<=1024 and L is a multiple of 64; i.e., bit length of between 512 and 1024 bits in increments of 64 bits.
- Next, an N-bit prime number q is selected. So, q is prime divisor of (p – 1), where 2N-1 < q < 2N i.e., bit length of N bits.
- Finally, g is selected to be of the form h(p-1)/q mod p, where h is an integer between 1 and (p – 1) with the limitation that g must be greater than 1. So, g is = h(p – 1)/q mod p, where h is any integer with 1 < h < (p – 1) such that h(p-1)/q mod p > 1.
If a user has these numbers, then it can selects a private key and generates a public key.
2. User’s Private Key
The private key x should be chosen randomly or pseudorandomly and it must be a number from 1 to (q – 1), so x is random or pseudorandom integer with 0 < x < q.
3. User’s Public Key
The public key is computed from the private key as y = gx mod p. The computation of y given x is simple. But, given the public key y, it is believed to be computationally infeasible to choose x, which is the discrete logarithm of y to the base g, mod p.
4. Signing
If a user want to develop a signature, a user needs to calculates two quantities, r and s, that are functions of the public key components (p, q, g), the hash code of the message H(M, the user’s private key (x), and an integer k that must be generated randomly or pseudorandomly and be unique for each signing. k is generated randomly or pseudorandomly integer such that 0<k < q.

Signing
5. Verification
Let M, r′, and s′ be the received versions of M, r, and s, respectively.
Verification is performed using the formulas shown in below:
- w = (s′)-1 mod q
- u1 = [H(M′)w] mod q
- u2 = (r′)w mod q
- v = [(gu1 yu2) mod p] mod q
The receiver needs to generate a quantity v that is a function of the public key components, the sender’s public key, and the hash code of the message. If this value matches the r value of the signature, then the signature is considered as valid.
TEST: v = r′
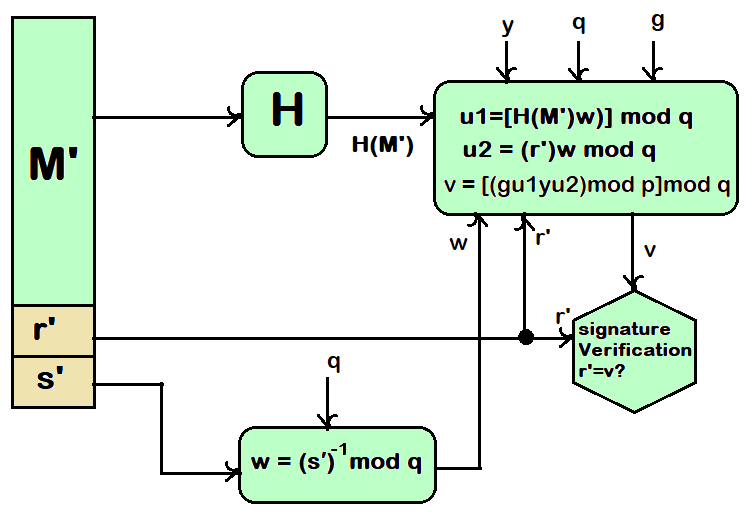
Verification
Now, at the end it will test on the value r, and it does not depend on the message or plaintext as, r is the function of k and the three global public-key components as mentioned above. The multiplicative inverse of k (mod q) when passed to the function that also has as inputs the message hash code and the user’s private key. The structure of this function is such that the receiver can recover r using the incoming message and signature, the public key of the user, and the global public key.
It is given that there is difficulty in taking discrete logarithms, it is not feasible for an attacker to recover k from r or to recover x from s. The only computationally demanding task in signature generation is the exponential calculation gk mod p. Because this value does not depend on the message to be signed, it can be computed ahead of time. Indeed, a user could precalculate a number of values of r to be used to sign documents as needed. The only other somewhat demanding task is the determination of a multiplicative inverse, k-1 .
Services
- Message Authentication: A secure digital signature scheme, like a secure conventional signature (one that cannot be easily copied) can provide message authentication (also referred to as data-origin authentication). Bob can easily confirm that the plaintext/message is sent by Alice as Alice’s public key is used for verification and the Alice’s public key woult not verify the signature signed by Eve’s private key. Hence, A digital signature provides message authentication.
- Message Integrity: When we sign a whole message, its integrity remains intact because if the message changes, we won’t get the same signature. Nowadays, digital signature methods use a special function called a hash function in both signing and verifying to ensure the message’s integrity.
- Nonrepudiation: If Alice signs a message and later claims she didn’t, can Bob provide evidence that she did? For example, if Alice instructs a bank (Bob) to transfer $10,000 to Ted’s account and then denies sending the message, Bob needs to keep the signed message and use Alice’s public key to recreate it. However, this approach may not work if Alice changes her keys or disputes the authenticity of the file. A solution is involving a trusted third party. This trusted party can authenticate messages and prevent Alice from denying them. In this setup, Alice sends her message along with her identity, Bob’s identity, and her signature to the trusted center. The center verifies the message’s authenticity and timestamps it before creating its own signature. This process ensures that if Alice denies sending the message later, the center can provide evidence to settle the dispute. Encryption can also be added for confidentiality. Thus, nonrepudiation is achievable through a trusted party.
Advantages of DSA
Authentication: At some point, digital signatures ensure strong identity authentication for the sender. The recipient can be sure that the message or document was signed by the purported signatory.
- Integrity: Digital signatures ensure the integrity of the content. If something is altered in the content after the signature is made, then it becomes invalid with respect to verifying the content.
- Non-Repudiation: A digital signature gives non-repudiation, meaning the sender cannot disclaim his creation of that document post factum. Most relevant in legal and contractual issues.
- Efficiency: Digital signatures make the process of signing electronic and automate it, giving way to fast online transactions free from the need of manual verification, paperwork, and a physical signature.
- Security: As long as the whole digital signing process is well organized, digital signatures may prove to be secure. Cryptographic public key cryptography and hashing algorithms prevent unauthorized parties from forging digital signatures.
- World Acceptance: Such a mechanism (digital signatures) to represent the conclusion of the related transaction in case of legal or contractual terms is known and widely accepted all over the world.
- Timestamping: Timestamping would also make another secure layer against replay attacks and against the freshness of the signature.
- Cost Savings: The digital signing process discontinues the need for transporting documents, thereby saving on costs to be done with printing, courier services, and manual handling.
Disadvantages of DSA
- Key Management Complexity: Cryptographic keys that are used for signing documents must be properly managed. Generating, storing, and distributing keys in a secure manner are all complicated procedures that need to be attended to, and revocation has to be handled carefully.
- Infrastructure Dependence: Digital signatures are built on a secure and reliable infrastructure of Public Key Infrastructure (PKI) and Certificate Authorities. If the infrastructure is compromised or becomes unavailable, it may compromise trust in digital signatures.
- Legal and Regulatory Challenges: Although many people are increasingly using digital signatures, there might still be legal and regulatory challenges in some places. It will be very important to observe local laws and standards.
- Initial Setup Costs: A proper setup of an extensive digital signature system may include the cost of obtaining certificates for digital certificates, putting in place safety measures, and training of the users.
- Offline Usability: In the event of not having access to the signer’s private key, digital signatures are found to be challenged. Solutions of hardware tokens and secure elements add to the complexity.
- User Education: Education of the proper application and value of digital signatures is necessary in order that the users should be educated in use. The correct measures to be taken against vulnerability, as well as being aware of any possible threat, are important in successful implementation.
- Vulnerability to Key Compromise: Private keys need to be safeguarded from unauthorized access since one compromised private key can initiate fraudulent signatures.
Frequently Asked Questions on Digital Signature Algorithm – FAQs
Do digital signatures provide confidentiality?
No, it does not provide confidentiataily, confidentiality is that only authorised user or receiver has viewed the message, it is not viewed by some scammer or attacker.
Which type of cryptography is used for digital signatures and why?
Digital signatures have been created that use public-key infrastructure, also called asymmetric cryptography, which is just a technique where the person sending the message and those receiving it generate different keys private keys and public keys.
How does DSA differ from RSA?
DSA (Digital Signature Algorithm) is a digital signature algorithm that is on the discrete logarithm problem, and widely used digital signature algorithm, especially in government and financial applications.
If we compare it with other digital signature algorithms, such as RSA and ECDSA, DSA has a few key differences:
|
Keywords
|
Description
|
|
Key size
|
DSA keys are generally smaller in size than RSA keys for same security, that can help in faster signature generation and verification, which improves complexity.
|
|
Signature size
|
Same as above, DSA signatures are generally smaller than RSA signatures for same security, which can result in less data being transmitted and stored.
|
|
Randomness requirements
|
DSA uses a random number or nonce in signature generation, while RSA does not. This makes DSA more vulnerable to certain types of attacks if the nonce is not generated properly.
|
|
Patent restrictions
|
RSA was patented until 2000, which limited its availability and use. But, DSA was developed as a part of the Digital Signature Standard (DSS) and has always been freely available for use.
|
|
Use cases
|
Government and financial applications often prefer DSA because it is standardized and has been widely examined for security purposes.
|
Overall, compared to other digital signature algorithms, DSA has several advantages and drawbacks, and the specific application requirements will determine which algorithm to choose.
Why is hashing used?
The major goal of hashing is to verify the integrity of a part of data or message. Since the hash generated is UNIQUE to the input data, it serves as a unique “fingerprint” of the input data, and it can make a hash valuable for verifying the integrity of messages sent via insecure transmission channels e.g. the internet.
Share your thoughts in the comments
Please Login to comment...