Terrascan is a popular software used to detect any possible vulnerabilities in IaC (Infrastructure as Code) structures. With its predefined built-in policies, Terrascan can detect any vulnerabilities in your code and let you know about the policy violations in detail, including their severity. The violations can range from minor infractions to severe structural compromises detected in the code. Before we go into detail, let’s see more about Terrascan.

What is Terrascan?
It is an open-source static code analysis tool. It is used to scan the templates in IaC and cross-check them with the in-built policies defining the structure of a good IaC. It is good for beginners trying to learn how to build IaC in the cloud, AWS, Azure, and GCP.
It provides you with a good blueprint on how to build infrastructure native to the cloud. In cloud computing, it is nearly impossible to remember almost all of the policies (there are over 500). With Terrascan, developers can check if their code matches policy standards and need not remember all the IaC policies in the cloud. It can be used to analyze and scan code in Terraform similar to other tools used for Terraform. There are various Terraform tools available. But, why do you need to use Terrascan? What are its benefits? The features of Terrascan will be discussed in detail.
What are the Key Features of Terrascan?
Numerous features of Terrascan can be used to your advantage. Key features are mentioned below:
1. Integration Support
One of Terrascan’s greatest features is its ability to integrate with any type of IaC framework and comply with its policies. These frameworks are:
- ArgoCD
- Atlantis
- GitHub
- Kubernetes

The ability to test IaC with different types enables freedom of using the framework of your choice.
2. Cross-cloud Policy Support
Terrascan provides support for different Cloud infrastructure policies enabling infrastructures spanning cross-platform. There is no need to use different software to check the policies of different cloud service providers. Terrascan provides support to the following Cloud service policies:
- AWS (Amazon Web Services)
- Microsoft Azure
- GCP (Google Cloud Provider)
- GitHub
- Docker
- Kubernetes
3. Scanning Automation
Instead of manually checking policy compliance in your IaC, you can integrate Terrascan into your preferred CI (Continuous Integration)/ CD (Continuous Deployment) pipeline. This automates the scanning of Infrastructure code in various formats without any prompts.
4. Monitoring 24/7
With Terraform being an open-source software, you can build your own instance locally which can run 24/7. This means, your infrastructure in the cloud will be monitored at all times and its logs, and vulnerabilities will be noted by Terrascan and provide you with the report.
5. Detailed Reporting
One of Terrascan’s most useful features is to explain the problem in your IaC in Layman’s terms. It will provide detailed reports about the policy violations, the severity of them, and how it will affect your code. Not only that, it also provides tips on how to mitigate this problem and provides any possible solutions.
Now that you know how useful Terrascan is, how do you use it, how do you install it? There are well-established ways for the different OS used out there.
How to Install Terrascan?
There are many ways provided by the developers to install Terrascan in your system. They are shown below.
1. For any Native Executable (MacOS or Linux)
Type the command below to download Terrascan into your system’s terminal.
$ curl -L "$(curl -s https://api.github.com/repos/tenable/terrascan/releases/latest | grep -o -E "https://.+?_Darwin_x86_64.tar.gz")" > terrascan.tar.gz
$ tar -xf terrascan.tar.gz terrascan && rm terrascan.tar.gz
$ install terrascan /usr/local/bin && rm terrascan
$ terrascan
2. For ArchLinux/Manjaro via AUR (Arch User Repository)
Type the following command in the terminal.
yay -S terrascan
3. For Homebrew Users (MacOS)
You can install Terrascan using the brew command.
$ brew install terrascan
4. Install as a Docker Image
The functionalities of Terrascan can also be used as a Docker image. You can type the following command:
$ docker run tenable/terrascan
5. For Windows systems
You can download Terrascan from this page. After installing the zip file, extract it to your desired folder.
After installation, add a path to the Terrascan executable by editing in the “Environment Variables”.

Edit the “Path” section in the Environment variables.
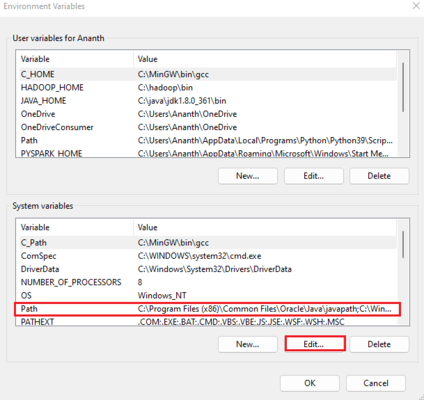
Click “New” to add a new path. Add the path to the Terrascan CMD to the paths.

6. Using Python
If you have Python, there is no need to install Terrascan in your system. The terrascan module is built in Python. You can use the pip command to install Terrascan in your system or in your Python shell.
pip install terrascan
After installing it, to check if it works, you can use the “–version” command. You can view all the available commands in the Terrascan module as shonw below using the command:
terrascan -h

How to scan your IaC using Terrascan?
You can use the following commands to scan your IaC using Terrascan.
If Python module is Installed
If you’re not using the Python module, you need to use the command in your terminal:
terrascan scan -f <filename>
If Python module is not Installed
If you’re using the Terrascan module from Python, the command line changes a bit.
terrascan -f <filename>
Updating Terrascan Software
Since it is an open-source software, there will be updates to the software from time to time. You can update it using the command:
terrascan init
What are the Use Cases of Terrascan?
Here are some common use cases of Terrascan as seen below.
1. Code Scanner
You can scan a variety of IaC using Terrascan. Consider this example where you have a file called “main.tf”.
Python3
provider "azurerm" {
features {}
}
resource "azurerm_resource_group" "example" {
name = "example-resources"
location = "UK South"
}
|
You can scan and detect vulnerabilities in this Azure infrastructure using Terrascan. By running the “terrascan -f” command, you can scan any Terraform code as shown below.

You can also use Terraform’s sandbox environment in your browser by clicking this link to scan your Terraform code.
A snippet of the JSON code to be checked in terraform environment:
Python3
provider "azurerm" {
features {}
}
resource "azurerm_storage_account" "my_storage_account" {
name = "myteststorageaccount"
resource_group_name = "myresourcegroup"
location = "westus2"
account_tier = "Standard"
account_replication_type = "LRS"
}
resource "azurerm_virtual_network" "vnet_prod" {
name = "vnet-prod"
address_space = ["10.0.0.0/16"]
location = "westus2"
resource_group_name = "myresourcegroup"
tags = {
Name = "vnet-prod"
}
}
|
Output
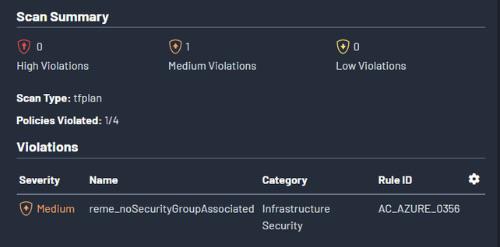
This works for all file extensions such as JSON, YAML, tf and so on.
2. Helm Chart Scanner
You can create Helm charts using the command.
helm create demo-chart
You’ll have a YAML (Yet Another Markup Language) called “values” where you can edit some values to create some vulnerabilities that Terrascan can report. You can detect vulnerabilities in Helm Charts using Terrascan.
Suppose you have the YAML code below:
Python3
Resources:
MyPod:
Type: AWS::ECS::TaskDefinition
Properties:
ContainerDefinitions:
- Name: my-container
Image: busybox
Command:
- sh
- "-c"
- "while true; do echo 'Hello, World!'; sleep 1; done"
Memory: 128
Cpu: 0.5
|
Output

3. Scanning Kubernetes Code
You can check the ability and safety of Kubernetes manifests that you’ve created in CFT (CloudFormation Template). Suppose you have a code to deploy a simple nginx deployment:
Python3
Resources:
NginxDeployment:
Type: AWS::ECS::TaskDefinition
Properties:
ContainerDefinitions:
- Name: nginx
Image: nginx:latest
Memory: 64
Cpu: 0.1
Family: nginx-deployment
|
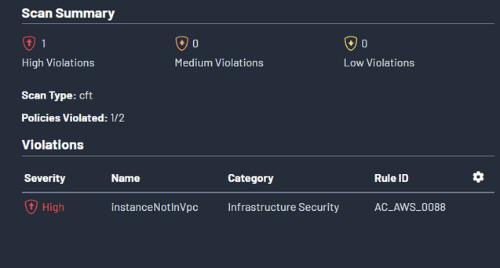
Due to its low resource requirement, this will be flagged as a major violation. To spend the right resources in Infrastructure and distribute them properly, unusually low resources will also be flagged as a violation as seen below.
Output
4. Integration with ArgoCD
You can configure Terrascan as an ArgoCD using two methods.
- Scan the remote repository after configuring Terrascan as an ArgoCD pre-sync hook.
- Deploy an already deployed Terrascan server into a Kubernetes (K8) cluster and scan remote repositories available in ArgoCD’s PreSync Hook.
Must Read
Conclusion
Terrascan plays an important role in improving the security features of IaC (Infrastructure as Code) in Cloud architecture. It also promotes cross-platform support across different cloud service providers. Due to it being an open-source software, there are many avenues where you can customize it to your preferences in your local storage.
FAQs
What is Terrascan’s role in IaC security?
Terrascan identifies vulnerabilities in IaC structures using built-in policies, ensuring code integrity.
Why is Terrascan suitable for cloud beginners?
It’s an open-source tool offering a blueprint for cloud-native infrastructure, simplifying learning on AWS, Azure, and GCP.
What are the practical uses of Terrascan?
Terrascan serves as a code and Helm chart scanner, ensuring security in Kubernetes manifests and promoting overall infrastructure security improvement.
Key features of Terrascan?
Terrascan provides ntegration support with frameworks like ArgoCD, Atlantis, GitHub, and Kubernetes, enabling flexibility in IaC testing.
Share your thoughts in the comments
Please Login to comment...