As associations embrace cloud computing for their Infrastructure needs, the secure and effective association between on-premises organizations and cloud assets becomes pivotal. In the domain of cloud-based DevOps, a Virtual Private Network (VPN) fills in as a fundamental component for laying out secure correspondence between various organization conditions. This article investigates the arrangement of an AWS VPN utilizing Terraform, an Infrastructure as Code (IaC) tool, to smooth out the creation and the executives of the VPN infrastructure.
A Virtual Private Network permits associations to stretch out their on-premises organization to the cloud, empowering secure data transfer and correspondence between assets facilitated in an AWS Virtual Cloud (VPC) and those living in an on-premises server farm. Terraform, with its definitive and code-based approach, works with the automation of AWS VPN arrangement, giving a versatile and reliable solution for DevOps specialists.
What Is AWS VPN(Virtual Private Network)
AWS Client VPN is a completely overseen remote access VPN arrangement utilized by your remote workforce to safely get to assets inside both AWS and your on-premises organization. Completely versatile, it consequently increases, or down, in view of interest. While relocating applications to AWS, your clients access them the same way previously, during, and after the move. AWS Client VPN, including the product client, upholds the OpenVPN protocol.
AWS Site-to-Site VPN is a completely overseen administration that makes a safe association between your server farm or branch office and your AWS assets utilizing IP Security (IPSec) burrows. While utilizing Site-to-Site VPN, you can interface with both your Amazon Virtual Private Clouds (VPC) as well as AWS Transit Gateway, and two passages for every association are utilized for expanded overt repetitiveness. For worldwide appropriated applications, the Sped Up Site-to-Site VPN choice furnishes significantly more noteworthy execution by working with AWS Worldwide Gas pedal to astutely course your traffic to the closest AWS network endpoint with the best presentation.
Step-By-Step Process to Create AWS VPN
Firstly, we need to log in to AWS console by using credentials or else create an account if in case do not have an account in the AWS
Now launch an EC2 instance with Specifications AMI-amazon Linux 2, t2.micro or t3.micro, Enable port 22(SSH) and 80(HTTP)

After launching an EC2 instance now connect with git bash terminal or any command terminal
Install terraform form official site, because to execute a terraform commands we need that terraform packages. Install terraform by following commands
sudo yum install -y yum-utils
sudo yum-config-manager –add-repo https://rpm.releases.hashicorp.com/AmazonLinux/hashicorp.repo
sudo yum -y install terraform
Now create a directory for your terraform configuration files
<filename.tf>
” .tf ” is the extension of terraform without this .tf we cannot run the script
with the help of VI command we can enter into that file and in that file we can write an script
AWS Provider Configuration
This script for AWS provider with specific region, without this we cannot run our VPN
provider “aws” {
region = “eu-north-1” # Change this to your preferred AWS region
}
VPC Creation
By using this script we can creating a VPC
resource “aws_vpc” “my_vpc” {
cidr_block = “10.0.0.0/16”
enable_dns_support = true
enable_dns_hostnames = true
tags = {
Name = “my-vpc”
}
}
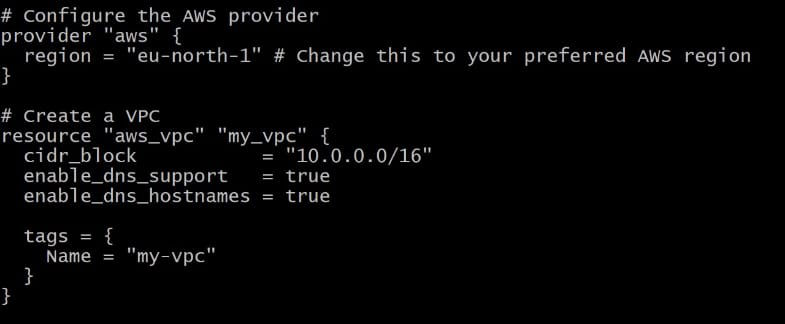
AWS Provider and VPC script
Subnets in Two Availability Zones
Here we are creating a two Subnets in our VPC, two are in different availability Zones
resource “aws_subnet” “subnet_1” {
vpc_id = aws_vpc.my_vpc.id
cidr_block = “10.0.1.0/24”
availability_zone = “eu-north-1b”
map_public_ip_on_launch = true
tags = {
Name = “subnet-1”
}
}
resource “aws_subnet” “subnet_2” {
vpc_id = aws_vpc.my_vpc.id
cidr_block = “10.0.2.0/24”
availability_zone = “eu-north-1c”
map_public_ip_on_launch = true
tags = {
Name = “subnet-2”
}
}

Internet Gateway
Here creating an internet gateway and attaches it to VPC
resource “aws_internet_gateway” “my_igw” {
vpc_id = aws_vpc.my_vpc.id
tags = {
Name = “my-igw”
}
}
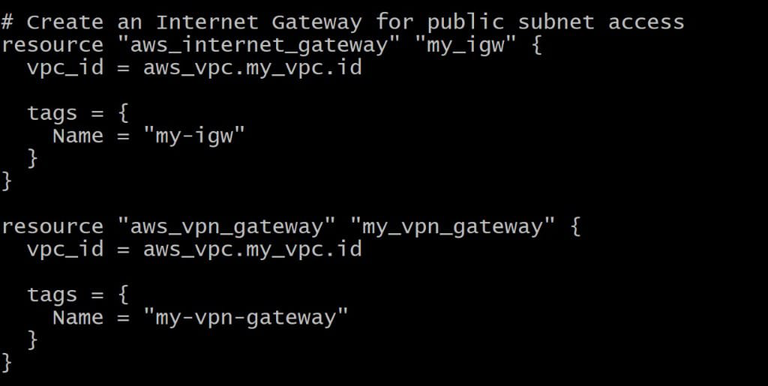
Internet Gateway
VPN Gateway and Customer Gateway
Here we creating a AWS VPN gateway associated with VPC and Customer gateway
resource “aws_vpn_gateway” “my_vpn_gateway” {
vpc_id = aws_vpc.my_vpc.id
tags = {
Name = “my-vpn-gateway”
}
}
resource “aws_customer_gateway” “my_customer_gateway” {
bgp_asn = 65000
ip_address = “16.170.236.246” # Replace with your on-premises public IP address
type = “ipsec.1”
tags = {
Name = “my-customer-gateway”
}
}
VPN Connection
Here we establishing a VPN connection between AWS VPC and on-premises network,
resource “aws_vpn_connection” “my_vpn_connection” {
customer_gateway_id = aws_customer_gateway.my_customer_gateway.id
vpn_gateway_id = aws_vpn_gateway.my_vpn_gateway.id
type = “ipsec.1”
static_routes_only = true
tunnel1_preshared_key = “ghfhv34423bxc”
}

Output For Tunnel IP Addresses
Here we difiening to output to display the IP Address of Two tunnels in the VPN connections
output “AWStunnel1IP” {
value = aws_vpn_connection.my_vpn_connection.tunnel1_address
}
output “AWStunnel2IP” {
value = aws_vpn_connection.my_vpn_connection.tunnel2_address
}

Now execute terraform commands
terraform init
terraform fmt
terraform validate
terraform plan
terraform apply –auto-approve
When we execute terraform apply –auto-approve, terraform will automatically create our infrastructure according to our terraform script

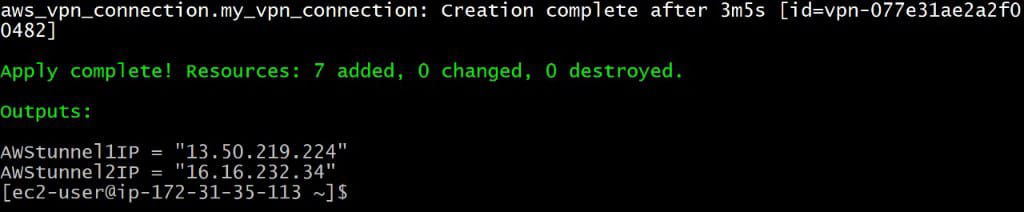
CREATED RESOURCES (OUTPUT)
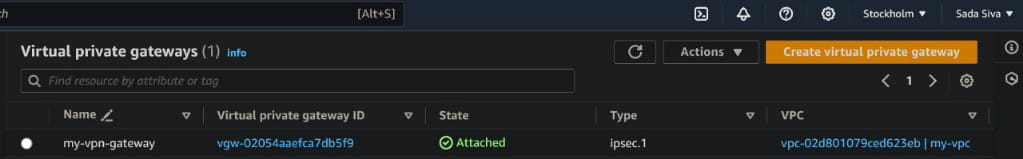
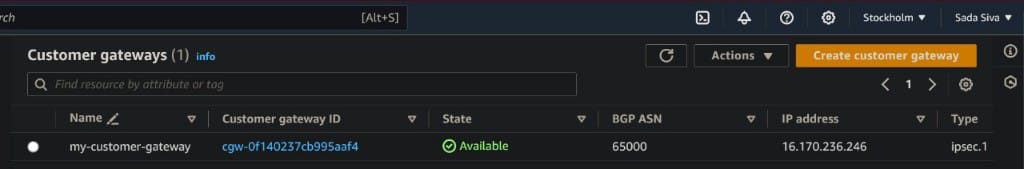

These are automatically created by using terraform script which was written in .tf file. By using this terraform we can automate easily.
Conclusion
The gave Terraform script organizes the production of a secure and versatile organization Infrastructure on AWS. It lays out a Virtual Confidential Cloud (VPC) with two subnets circulated across various accessibility zones, advancing adaptation to internal failure and high accessibility. The consideration of a Web Passage empowers web network for occasions inside the public subnets. Besides, the content coordinates the sending of an AWS VPN Gateway, Customer Gateway, and VPN Association, working with a protected association between the AWS VPC and an on-premises organization.
The outputs offer significant data about the IP addresses related with the VPN , supporting the design of the on-premises organization. It is fundamental to supplant placeholder values with real setups, ensuring a consistent incorporation with existing foundation. This content gives a strong groundwork to associations looking to lay out a versatile and secure organization engineering, mixing AWS administrations with on-premises assets. Running terraform init and terraform apply will rejuvenate this foundation, lining up with the standards of Infrastructure as Code (IaC) and improving the proficiency of cloud-based DevOps practices.
AWS VPN Using Terraform – FAQ’s
Could I update VPN after the underlying configuration utilizing Terraform?
Yes, you can adjust your Terraform configuration and apply the changes utilizing terraform apply. Terraform will brilliantly update just the necessary resources.
How does Terraform deal with state the board for AWS VPN?
Terraform keeps a state document that records the present status of the infrastructure. This record is utilized to design and apply changes, ensuring consistency and keeping away from accidental alterations.
Is it conceivable to make multiple VPN associations inside a similar VPC utilizing Terraform?
Yes, Terraform permits you to characterize various VPN connections in your configuration, giving flexibility to complex organization arrangements.
What security contemplations should to be considered while setting up an AWS VPN?
Ensure proper setup of security groups, network ACLs, and VPN verification components to improve the security of your VPN connections.
Could I use Terraform to destroy the AWS VPN infrastructure when it’s no longer required?
Yes, you can utilize terraform destroy to destroy the resources made by Terraform, really eliminating the AWS VPN infrastructure. Continuously practice wariness to stay away from accidental information misfortune.
Share your thoughts in the comments
Please Login to comment...