Difference between Byte stuffing and Bit stuffing
Last Updated :
15 May, 2023
Data link layer is responsible for something called Framing, which is the division of a stream of bits from the network layer into manageable units (called frames). Each frame consists of the sender’s address and a destination address. The destination address defines where the packet is to go and the sender’s address helps the recipient acknowledge the receipt. Frames could be fixed size or variable size. In fixed-size framing, there is no need for defining the boundaries of the frames as the size itself can be used to define the end of the frame and the beginning of the next frame. But, in variable-size framing, we need a way to define the end of the frame and the beginning of the next frame. To separate one frame from the next, an 8-bit (or 1-byte) flag is added at the beginning and the end of a frame. But the problem with that is, any pattern used for the flag could also be part of the information. So, there are two ways to overcome this problem:
- Using Byte stuffing (or character stuffing)
- Using Bit stuffing
| Feature |
Byte stuffing |
Bit stuffing |
| Definition |
A technique used to prevent the occurrence of a specific byte in a data stream by adding an extra byte. |
A technique used to prevent the occurrence of a specific bit sequence in a data stream by inserting an additional bit. |
| Concept |
Adds an extra byte to the data when a special byte is found. |
Adds an extra bit to the data when a special bit pattern is found. |
| Special byte/bit |
Flag byte (01111110) |
Flag bit pattern (01111110) |
| Insertion |
Extra byte is inserted after each occurrence of the flag byte. |
Extra bit is inserted after each occurrence of the flag bit pattern. |
| Removal |
The extra byte is removed at the receiver end. |
The extra bit is removed at the receiver end. |
| Efficiency |
Less efficient due to the addition of an extra byte. |
More efficient as only an extra bit is added. |
| Applications |
Used in protocols like PPP and HDLC. |
Used in protocols like Ethernet and Token Ring. |
| Objective |
To ensure data integrity and prevent data loss due to errors caused by the presence of a specific byte in the data stream. |
To ensure data integrity and prevent data loss due to errors caused by the presence of a specific bit sequence in the data stream.
|
| How it works |
The specific byte is replaced with a unique escape byte, followed by a second byte that indicates the original byte’s value. |
The specific bit sequence is replaced with a unique bit sequence that indicates the original bit sequence’s value.
|
| Overhead |
Adds overhead to the data stream by adding an extra byte for every occurrence of the specific byte. |
Adds overhead to the data stream by adding an extra bit for every occurrence of the specific bit sequence.
|
| Efficiency |
Less efficient than bit stuffing, as it requires the addition of an entire byte to the data stream. |
More efficient than byte stuffing, as it requires the addition of only one bit to the data stream.
|
| Usage |
Typically used in protocols that use fixed-length frames or packets, such as PPP and HDLC. |
Typically used in asynchronous transmission, such as in serial communication, and protocols that use variable-length frames or packets, such as Ethernet.
|
Byte stuffing is a byte (usually escape character(ESC)), which has a predefined bit pattern is added to the data section of the frame when there is a character with the same pattern as the flag. Whenever the receiver encounters the ESC character, it removes it from the data section and treats the next character as data, not a flag. But the problem arises when the text contains one or more escape characters followed by a flag. To solve this problem, the escape characters that are part of the text are marked by another escape character i.e., if the escape character is part of the text, an extra one is added to show that the second one is part of the text.
Example:
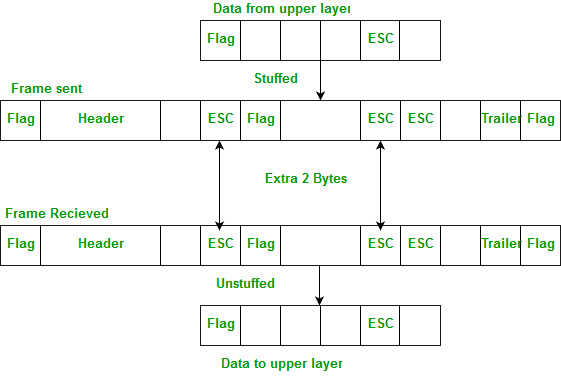
Note – Point-to-Point Protocol (PPP) is a byte-oriented protocol.
Bit stuffing – Mostly flag is a special 8-bit pattern “01111110” used to define the beginning and the end of the frame. Problem with the flag is the same as that was in the case of byte stuffing. So, in this protocol what we do is, if we encounter 0 and five consecutive 1 bits, an extra 0 is added after these bits. This extra stuffed bit is removed from the data by the receiver. The extra bit is added after one 0 followed by five 1 bits regardless of the value of the next bit. Also, as the sender side always knows which sequence is data and which is flag it will only add this extra bit in the data sequence, not in the flag sequence.
Example:
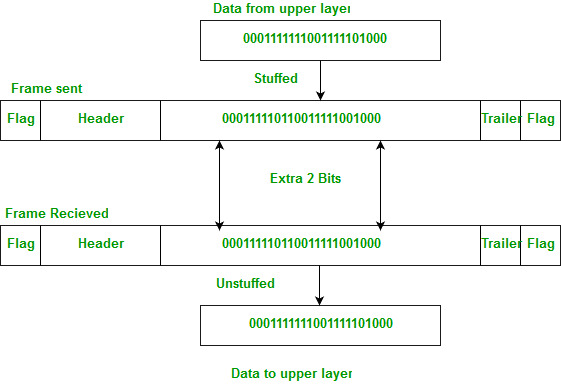
Note: High-Level Data Link Control(HDLC) is a bit-oriented protocol.
Byte stuffing: It is used to convert a message format of a sequence of bytes that may contain reserved values into another byte sequence that does not contain reserved values. It is also known as character-oriented framing. Here, a special byte is stuffed before flag and esc also that special byte is escape(ESC).
Bit stuffing: It is used for inserting one or more non-information bits into a message to be transmitted, to break message sequence for synchronization. It is also known as bit-oriented framing. Here,0 bit stuffed after five consecutive 1 bits.i.e extra bit is added after five consecutive ones.
Share your thoughts in the comments
Please Login to comment...