DHCP Snooping
Last Updated :
12 Jul, 2022
Prerequisite – Dynamic Host Configuration Protocol (DHCP) Every protocol that we learn in Computer Network have some rules, these rules govern working of protocols. These rules sometimes provide way for attackers to take advantage of network. Attackers can also use working of DHCP to compromise our network. In this article we’ll learn how our network can be compromised and how we can prevent them. DHCP based Attack : Consider scenario given below. Attacker has connected his laptop to network and act as fake DHCP Server. As we know that initial DHCP’s DORA messages exchange between DHCP client and server uses broadcast address. Attacker listen to that broadcast and lease its own address, mask and default router to client. Now client will forward all its traffic to attacker. This creates Man-in-the-middle attack, violating Integrity component of security.  Figure – DHCP based attack
Figure – DHCP based attack
DHCP snooping : DHCP snooping is done on switches that connects end devices to prevent DHCP based attack. Basically DHCP snooping divides interfaces of switch into two parts
- Trusted Ports – All the ports which connects management controlled devices like switches, routers, servers etc are made trusted ports.
- Untrusted Ports – All the ports that connect end devices like PC, Laptops, Access points etc are made untrusted port.
We know that DHCP address leasing is done after exchange of DORA messages between DHCP client and server. Two messages Discover and Request comes from client side and two messages Offer and Acknowledgement comes from server side. Using these information, DHCP snooping works in following manner
- If trusted port receive Offer and Acknowledgement messages, then do nothing just let them pass.
- If untrusted ports receive Offer and Acknowledgement messages, then messages are blocked as they are message from DHCP server. Untrusted port are port that should be connected to DHCP server.
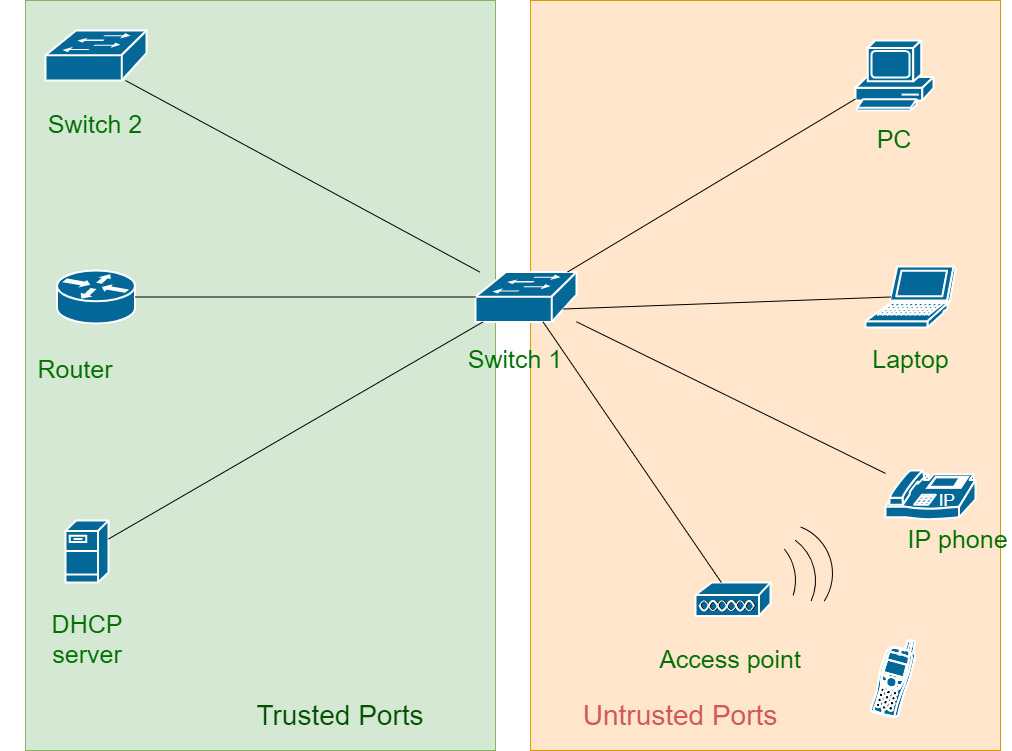 Figure – Trusted and Untrusted ports
Figure – Trusted and Untrusted ports
The logic of DHCP untrusted port can be bit more confusing. All real user population connects to untrusted port. A network administrator can’t know which are legitimate user and which are attackers. DHCP snooping function keeps record of leased address to user in DHCP Binding Table. This table contains record of interface, VLAN, MAC-address to which IP address is leased. This checks problem of identity theft in LAN. DHCP snooping can also be configured to limit number of request arriving any interface. This helps in preventing DOS attacks that can consume entire address space or overload DHCP server. 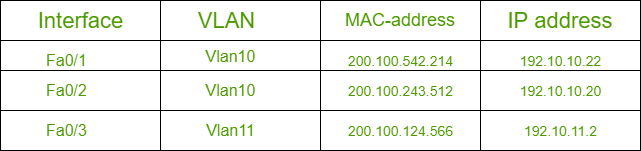 Figure – DHCP Binding Table
Figure – DHCP Binding Table
Share your thoughts in the comments
Please Login to comment...