Docker, a leading containerization platform, employs container runtimes like runc to execute containers. However, vulnerabilities in runC can expose systems to security threats. This article meticulously explores Docker runc vulnerabilities, emphasizing their implications and offering strategies to fortify container runtimes.
Understanding Of Primary Terminologies
- Docker: A platform for containerization that makes it easier to create and run apps inside of containers.
- runc: An open-source, lightweight container runtime that manages and creates containers in accordance with OCI (Open Container Initiative) specifications.
- Container: A container is a standard software unit that includes all the code and dependencies needed to run an application reliably and quickly across a range of computing environments.
- Vulnerability: A flaw that could let a threat actor or intruder use a computer system to carry out illegal activities.
What Is Runc Vulnerability?
A Linux container running CLI tool called runc had a vulnerability (CVE-2024-21626) that made it possible for a container order-of-operations breakout centered on the WORKDIR command. Runc vulnerability is the name given to this security hole in runc. Container escape to the underlying host operating system could occur from the exploitation of this vulnerability. This could happen if you build a container image with a malicious Dockerfile or upstream image, or if you run a malicious image.
What Are The Latest Docker Vulnerabilities?
The Docker security team is always keeping an eye out for and updating the most recent Docker vulnerabilities. Four security flaws in the container ecosystem have been found and reported by Snyk Labs security researchers23. CVE-2024-21626, one of the vulnerabilities, relates to the runc container runtime, while CVE-2024-23651, CVE-2024-23652, and CVE-2024-23653)23 impact BuildKit.
Implications Of Docker Runc Vulnerabilities: Unauthorized access, privilege escalation, and host system compromise are possible outcomes of vulnerabilities in the Docker runc protocol. To secure environments that use containers, it is imperative to understand these vulnerabilities.
Recognizing Your Vulnerabilities: Four security flaws in the container ecosystem were found and disclosed by Snyk Labs security researchers12. Among the weaknesses, CVE-2024-21626, concerns the runc container runtime, and the other three affect BuildKit (CVE-2024-23651, CVE-2024-23652, and CVE-2024-23653)12.
CVE-2024-21626: This vulnerability allows for an order-of-operations container breakout centered around the WORKDIR command3. If this vulnerability is exploited, containers may escape and reach the host operating system3.
CVE-2024-23651, CVE-2024-23652, And CVE-2024-23653: BuildKit is a framework that facilitates the efficient, expressive, and repeatable conversion of source code into build artifacts. These vulnerabilities impact it.
How To Fix Vulnerabilities In Docker Runc?
To address vulnerabilities in Docker runc, users should update to the most recent version of Docker, which includes patches for known security issues. Additionally, by following advised practices for container security — like using reliable base images and routinely updating container images — potential risks can be minimized.
For example, as soon as patched versions are made available, make sure to update to the most recent versions of runc, BuildKit, Moby, or Docker Desktop if you are using any of the affected versions3. Runc >= 1.1.12, BuildKit >= 0.12.5, Moby (Docker Engine) >= 25.0.2 and >= 24.0.9, and Docker Desktop >= 4.27.13 are the versions that have been patched. To reduce risk, adhere to these best practices if you are unable to update as soon as possible to an unaffected version after it is released: Use only reliable Docker images (official images from Docker, for example). Never create Docker images using untrusted Dockerfiles or sources.
Step-by-Step Process Of Debugging Docker Runc Vulnerabilities
Identifying Vulnerabilities: Employ vulnerability scanning tools to detect potential weaknesses in the runc runtime.
Version Updates: Regularly check for runc updates and apply them promptly to patch known vulnerabilities.
Container Hardening: As examples of best practices for container security, follow the concept of least privilege and employ privileged containers as little as possible.
To monitor and test Docker runc vulnerabilities, you can use various commands and tools to assess the security of your Docker environment. Below are some commands you can use :
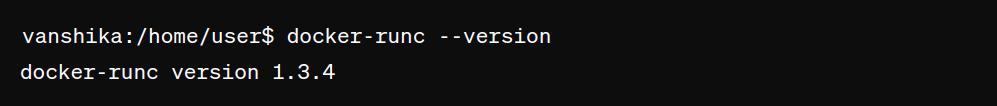
1. Check Docker runc Version
This command will display the current version of Docker runc installed on your system.
docker-runc --version
2. Check Docker Images For Security Flaws
- To check for known vulnerabilities in Docker images, utilize vulnerability scanning tools such as Trivy or Clair. You must install Trivy first:
curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/main/contrib/install.ps1 | Invoke-Expression
Then, you can scan a Docker image:
trivy image <image_name>
- Put the name of the Docker image you wish to scan in place of {<image_name>}.
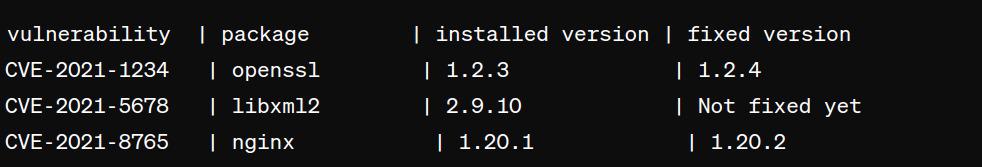
The following screenshot illustrates on checking the vulnerabilities of docker scan with trivy command.
3. Find Vulnerabilities And ExposuresCVEs)
- To find CVEs associated with Docker runc, consult the National Vulnerability Database (NVD) or other vulnerability databases.
curl -s "https://services.nvd.nist.gov/rest/json/cves/1.0?keyword=docker+runc" | jq
- This command retrieves from the NVD CVE information pertaining to Docker runc and presents it in the JSON format. Installing {jq} is required in order to parse the JSON response.

4. Run Vulnerability Tests With Metasploit
- Metasploit is a penetration testing framework that includes modules for testing Docker vulnerabilities. First, install Metasploit:
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb -o msfinstall && chmod 755 msfinstall && ./msfinstall
Then, start Metasploit:
msfconsole
- Inside Metasploit, you can search for Docker-related modules and run vulnerability tests.
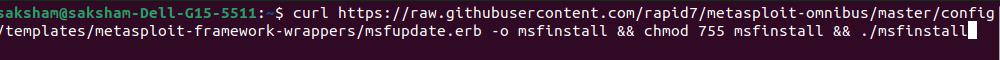
- You can start the Metasploit with running `msfconsole` as shown in the below screenshot.

5. Check Docker Desktop Logs
- Review Docker Desktop logs for any error messages or suspicious activities:
type "%USERPROFILE%\.docker\machine\machines\default\default\Logs\VBox.log"
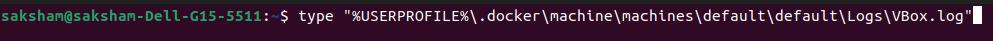
- This command displays the logs generated by Docker Desktop’s virtual machine (assuming the default installation path).
6. Analyze Docker Events
- Monitor Docker events to track container activities and detect any abnormal behavior:
docker events --format "{{.Type}}: {{.Action}} {{.Actor.Attributes.name}}"

- This command will display real-time Docker events such as container creation, start, stop, etc.
7. Run Security Scans With Docker Bench Security
- Docker Bench Security is a script that checks for dozens of common best-practices around deploying Docker containers in production. First, download and run Docker Bench:
docker run --rm -it --net host --pid host --userns host --cap-add audit_control \
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
-v /var/lib:/var/lib \
-v /var/run/docker.sock:/var/run/docker.sock \
-v /usr/lib/systemd:/usr/lib/systemd \
-v /etc:/etc --label docker_bench_security \
docker/docker-bench-security
- This script will perform security checks and provide recommendations.

- These commands and tools will help you monitor and test Docker runc vulnerabilities. Make sure to regularly update Docker and its dependencies to mitigate potential security risks.
Conclusion
The integrity of containerized applications must be preserved, which requires the security of container runtimes like runc. Users can strengthen their Docker environments against potential threats by employing strong security measures, staying informed about vulnerabilities, and updating runtime versions promptly.
Docker runc Vulnerabilities – FAQs
How Can I Check The Version Of Runc In Use?
Execute docker info | grep -i runtime to identify the runtime, including the version of runc.
Can I Run Containers Without Runc?
Docker relies on runc as its default runtime; however, alternatives like containerd can be configured.
Are There Community-driven Efforts To Address Runc Vulnerabilities?
Yes, the Docker community actively collaborates on identifying and addressing vulnerabilities, often releasing patches promptly.
Should I Be Concerned About Runc Vulnerabilities In Isolated Environments?
Yes, vulnerabilities pose risks even in isolated environments. Regular updates and security practices are crucial for mitigation.
Share your thoughts in the comments
Please Login to comment...