How To Use Docker Security Tools To Secure Docker Container Images
Last Updated :
15 Mar, 2024
Docker is a tool that is used to package the application and its dependencies into compact units called Docker containers. In this guide, I will first discuss what a docker is. Then I will discuss a security tool called Trivy, which is used to scan and detect Docker image vulnerabilities. After this, I will walk you through the different steps to detect vulnerabilities in a Docker image and also explain the steps to fix these vulnerabilities.
What is Docker?
Docker is a containerization tool used to encapsulate applications and their dependencies into compact units called Docker containers. These Docker containers have all the code, runtime, dependencies, and other libraries that are essential to running the application. Here, the developers first write a Docker file for an application. Basically, in the Docker file base image, the working directory, commands to install dependencies, and commands to run the application are mentioned. After the Docker file is built, use the Docker build command to generate a Docker image. This Docker image can later be used to run the application. Docker images are very lightweight and portable. Developers can now run their applications on any machine using the Docker image; the only condition is to install Docker on that system. Docker containers use very few resources for a system. So we can run multiple Docker containers on a single machine. Running multiple Docker containers on a single host results in maximum resource utilization of the machine, and it also helps reduce the overall infrastructure cost for running an application. In summary, we can say Docker has become a very essential tool for developers and organizations to build and run their applications on any machine without facing any hardware requirements issues.
What is Trivy?
Trivy is an open-source scanning tool that is used to scan and detect vulnerabilities in a Docker container and artifacts. It delivers the result very quickly. It can detect vulnerabilities in operating systems like Alpine, CentOS, and many more. It shows the vulnerability report in a very structured way. It classifies the issues into low-level, medium-level, high-level, and critical levels. Trivy can integrate into the CI/CD pipelines, which helps in automatic vulnerability detection. With each new update, Trivy is becoming more reliable in detecting security and vulnerability-related issues. In summary, we can say Trivy has become a powerful tool to detect the vulnerabilities of containerized applications, images, and artifacts to maintain the security of the entire infrastructure.
Pre-requisites
Before moving on to the next section, make sure that you have installed Docker on your system. If Docker is not installed, then follow these detailed geeks for geeks articles to download Docker on your system.
Steps To Use Docker Security Tools To Secure Docker Container Images
Step 1: Here first create a dockerfile . Here i have used a old version of alpine linux as the base image.
FROM alpine:3.7
RUN apk add --no-cache curl

Step 2: Now build the docker image by using docker build command.
docker build -t gfg-demo .

Step 3: Tag the docker image and push it to the dockerhub account.
docker tag gfg-demo <your-username>/gfg-demo
docker push <your-username>/gfg-demo

Step 4: Now run the trivy scanner to scan the docker image.
docker run --rm -v <any-local-path>:/root/.cache/ aquasec/trivy:0.18.3 image <your-username>/gfg-demo
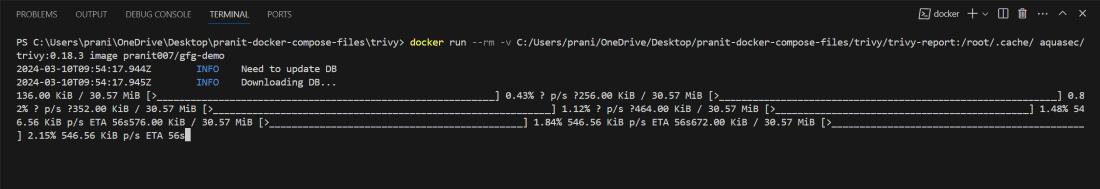
Step 5: Now you can observe all the issues . Here you will see two critical issues .

Step 6: To fix these critical issues , now update the version of alpine in dockerfile .
FROM alpine:3.19
RUN apk add --no-cache curl
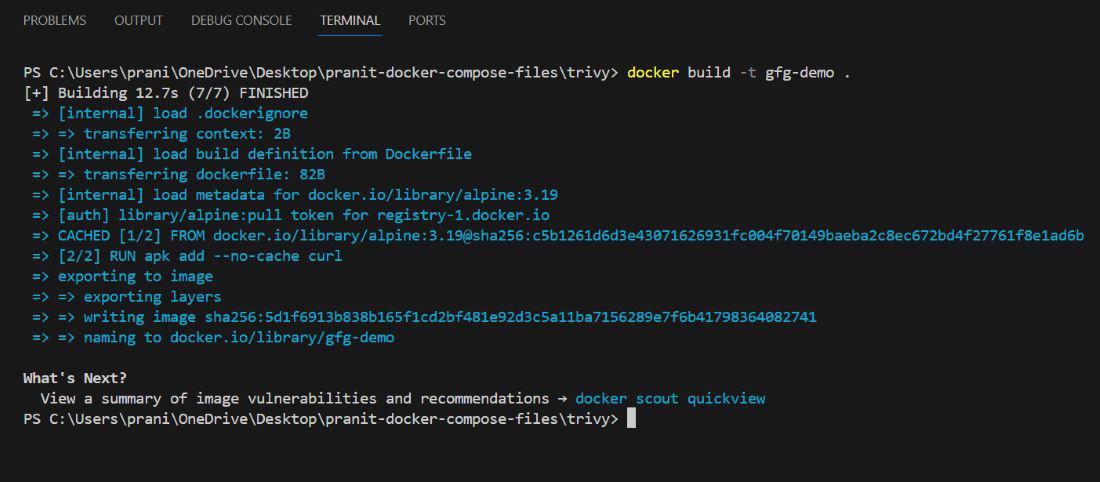
Step 7: Again build the image from the updated dockerfile.
docker build -t gfg-demo .
Step 8: Again tag the docker image and push it to dockerhub account .
docker tag gfg-demo <your-username>/gfg-demo
docker push <your-username>/gfg-demo

Step 9: Now run the trivy scan for updated docker image .
docker run --rm -v <any-local-path>:/root/.cache/ aquasec/trivy:0.18.3 image <your-username>/gfg-demo
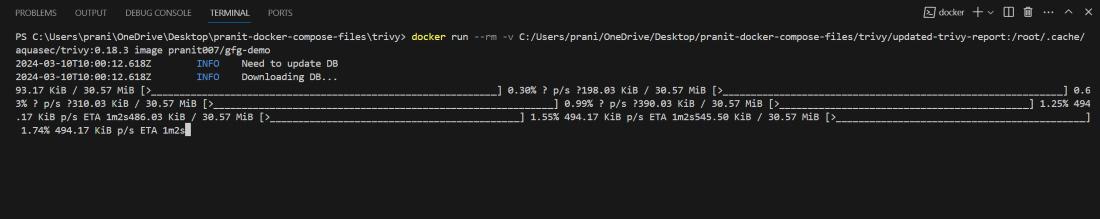
Step 10: Now observe , there are no critical issues . With just by updating the docker base image version we have fixed all the critical issues.

Conclusion
Here in this guide you have first learned what is docker. Then you have learned about a security tool called Trivy. After this you have created a dockerfile using an old version of alpine linux. Then you have build a docker image and pushed it to your dockerhub account. After this you have performed the scanning of the image by using Trivy and observed the critical issues. Finally you have updated the alpine image version to solve all the critical issues.
Docker Security Tools to Secure Docker Container Images – FAQ’s
What are key components of docker ?
Dockerfile , Docker Image , Docker Engine , Docker container , Docker compose and Docker registry are the key components of docker.
What is a docker image ?
A docker image is a lightweight and portable software package which includes the code , runtime and all the dependencies to run an application.
What are docker security tools ?
Docker security tools are those tools which is used to detect vulnerabilities in the docker image . For example Trivy , clair , Snyk , etc.
Why to secure docker containers ?
Docker containers needed to be secure to prevent any unauthorized access and security vulnerabilities.
How to protect the docker containers from the vulnerabilities ?
You have to update the old docker images and the dependencies to protect the docker container from vulnerabilities.
Share your thoughts in the comments
Please Login to comment...