Ever heard of ICMP? It’s like the internet’s messenger, quietly ensuring messages flow smoothly between devices. Think of it as a network detective, reporting issues when something goes wrong. In the “ping” game, ICMP checks if hosts are reachable. This article explores ICMP’s role and shows how to boost Linux security by blocking ICMP responses, using methods like firewall rules and kernel parameter tweaks. We’ll also answer common questions about making changes, potential issues, and how to undo ICMP blocks, making it a simple guide for managing ICMP in Linux.
What is ICMP in Linux?
Internet Control Message Protocol (ICMP) is like the messenger of the internet, responsible for sending messages between devices to keep everything running smoothly. Imagine it as a communication tool for devices in a network. When there’s an issue, ICMP generates error messages to let devices know what’s going wrong. For instance, if a website is unreachable or a network path is congested, ICMP steps in to report the problem. It’s also the star of the “ping” game, where it sends an “Echo Request” to a destination and expects a friendly “Echo Reply” if all is well, helping users check if a host is reachable. ICMP is like the behind-the-scenes network detective, making sure data gets to its destination and reporting back when something isn’t quite right.
In simpler terms, when you browse the internet or connect devices on a network, ICMP is the superhero working silently in the background, ensuring messages get where they need to go and alerting us when there’s a hiccup in the network. Whether it’s helping routers communicate more efficiently, letting us ping servers to check their status, or handling errors in the vast web of connections, ICMP plays a crucial role in keeping our internet experience smooth and trouble-free. So, next time you “ping” a website or troubleshoot a network issue, know that ICMP is the unsung hero making it all possible.
Understanding Ping
Ping is a commonly used tool to check the status of a device on a network. It operates using the ICMP protocol. When a Ping request is sent out in the form of an ICMP echo to the target device, the device responds with an ICMP echo reply if it is accessible.
The purpose of Ping is to send a test packet, also known as an echo packet, to a device to determine its reachability and the time it takes for the packet to reach the device. There are two main objectives:
Test the network availability to the device:
Ping helps assess whether a device on the network is reachable or not.
Network latency between two devices:
By measuring the time it takes for the echo packet to travel to the target device and receive a reply, Ping provides insights into the network latency between the two devices.
Understanding ICMP Type
In the realm of networking, the ICMP (Internet Control Message Protocol) type plays a crucial role, serving as the initial 8 bits in the header of ICMP messages. This specific type field offers a concise description of the message’s purpose, providing essential information to the network device that receives it. This information is vital for the recipient to understand why it’s receiving the message and how it should be handled.
Let’s break it down with bullet points for easy understanding:
- ICMP Type Overview:
- First 8 bits in ICMP message header.
- Briefly explains the purpose of the message.
- Guides the receiving network device on how to handle the message.
- Example: Type 8 Echo:
- Host sends an Echo message to check a potential destination system’s availability.
- ICMP type field (first 8 bits) labels it as Type 8 Echo.
- Upon receiving, the destination device can respond with an Echo Reply (Type 0), confirming its availability.
In simpler terms, the ICMP type acts like a label on a message, telling devices why they’re receiving it and how to respond. In the case of Type 8 Echo, it’s like asking, “Hey, are you there?” and getting a reply saying, “Yes, I’m here” (Echo Reply Type 0). This organized system helps devices communicate effectively on a network.
Block PING requests of ICMP via kernel parameters in Linux
Blocking ICMP (Internet Control Message Protocol) responses on a Linux system is a security measure that involves preventing certain types of ICMP packets from being processed by the system. ICMP is a network layer protocol that is used for various network-related tasks, such as error reporting, network diagnostics, and control messages.
Blocking ICMP responses can be achieved using firewall rules, with tools like iptables or firewalld. Let’s discuss the process in detail, along with examples and explanations.
1. Using iptables to Block PING Requests of ICMP in Linux
Step 1: List current iptables rules:
sudo iptables -L
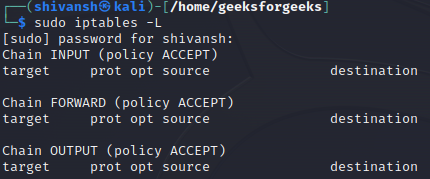
This command displays the existing iptables rules on your system, allowing you to review the current configuration before making any changes.
Step 2: Block ICMP Echo Requests (Ping):
iptables -A INPUT -p icmp --icmp-type echo-request -j DROP
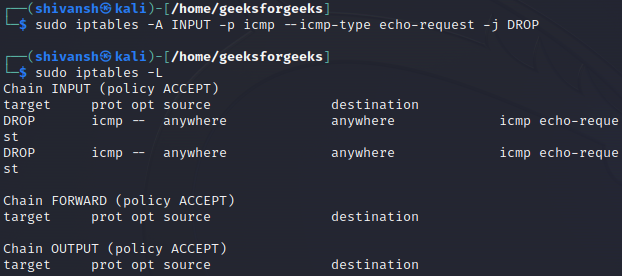
This rule appends (`-A`) a new entry to the INPUT chain, specifying that ICMP packets of type “echo-request” (ping) should be dropped (`-j DROP`). As a result, the system will not respond to ping requests.
We have also verified out updates in iptables using command mentioned below:
sudo iptables -L
Step 3: Block ICMP Destination Unreachable:
iptables -A INPUT -p icmp --icmp-type destination-unreachable -j DROP
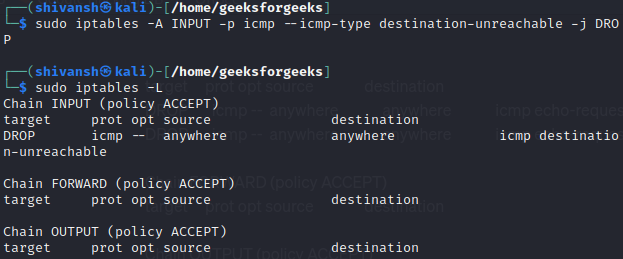
This rule blocks ICMP Destination Unreachable messages. These messages are often used by network devices to indicate that a destination is unreachable. By dropping them, you reduce the information available to potential attackers probing your network.
We have also verified out updates in iptables using command mentioned below:
sudo iptables -L
2. Permanently Blocking Ping Requests on a Linux System using sysctl.conf”
To permanently block ping requests on a Linux system, you can follow these steps and explanations:
Step 1: Edit sysctl.conf
Edit the sysctl configuration file, which is used to configure kernel parameters.
Open the file /etc/sysctl.conf:
sudo nano /etc/sysctl.conf
Add the following line at the end of the file:
net.ipv4.icmp_echo_ignore_all=1
This line sets the `icmp_echo_ignore_all` parameter to 1, meaning the system will ignore or reject all incoming ICMP (ping) requests.
Step 2: Apply Changes
To apply the changes made in `sysctl.conf`, run:
sudo sysctl -p
This command reloads the sysctl settings, applying the changes you made.
Step 3: Temporary Blocking Methods
If you want to block ping requests temporarily, you have two options:
a. Using /proc/sys/
echo "1" > /proc/sys/net/ipv4/icmp_echo_ignore_all
This command writes ‘1’ to the file `/proc/sys/net/ipv4/icmp_echo_ignore_all`, temporarily blocking ICMP requests.
b. Using sysctl command
sudo sysctl -w net.ipv4.icmp_echo_ignore_all=1
This command sets the `icmp_echo_ignore_all` parameter to 1 temporarily using the sysctl command.
Step 4: Checking Status
To check whether ping requests are blocked, you can use the following command:
cat /proc/sys/net/ipv4/icmp_echo_ignore_all
This will display ‘1’ if ICMP requests are currently being ignored.
Step 5: Verifying Blockage
To verify if ping requests are being blocked, you can use the ping command with the -c option to specify the number of packets to send. For example:
ping -c 4 example.com
This will attempt to send 4 ICMP echo requests to example.com. If ping requests are blocked, you’ll see output similar to:
PING example.com (93.184.216.34) 56(84) bytes of data.
— example.com ping statistics —
4 packets transmitted, 0 received, 100% packet loss, time 3056ms
Here, the 100% packet loss indicates that the requests were blocked.
How to Block Ping (ICMP) Responses – FAQs
What are the different methods to block ICMP responses?
This is a common starting point, as people want to understand the available options before diving into specifics. Popular methods include using iptables firewall rules, modifying the kernel parameter `net.ipv4.icmp_echo_ignore_all`, and editing the `/etc/sysctl.conf` file.
What are the permanent vs. temporary solutions?
Users often want to choose the appropriate approach based on their needs. Modifying the kernel parameter offers a temporary solution effective till the next reboot, while editing `/etc/sysctl.conf` or using firewall rules provide permanent solutions that persist across reboots.
What are the downsides of blocking ICMP responses?
Understanding the implications is crucial. While blocking ping can enhance security and reduce network traffic, it can also hinder network troubleshooting and mask underlying connectivity issues.
How to unblock ICMP responses if I accidentally blocked them?
This concern arises from potential mistakes during configuration. Providing instructions for reversing the blocking process using the chosen method (e.g., deleting firewall rules, reverting kernel parameter change) is helpful.
Do I need to restart my system after making changes?
The need for a restart depends on the chosen method. Modifying the kernel parameter takes immediate effect, while changes in `/etc/sysctl.conf` require applying them with `sysctl -p`. Clarifying these dependencies avoids confusion.
Conclusion
In this article we discussed how to Block Ping (ICMP) Responses in Linux which is crucial for maintaining a secure and efficient network environment. ICMP, acting as the internet’s silent messenger, ensures effective communication between devices and plays a key role in the widely-used “ping” tool. By exploring methods to block ICMP responses in Linux, such as firewall rules and kernel parameter adjustments, users can enhance system security. However, it’s essential to weigh the benefits against potential downsides, as blocking ICMP may hinder network troubleshooting. This comprehensive guide equips readers with the knowledge to navigate and implement ICMP management effectively, empowering them to make informed decisions based on their specific network needs.
Share your thoughts in the comments
Please Login to comment...