AWS CLI for SSL/TLS Certificates
Last Updated :
04 Mar, 2024
An SSL/TLS certificate is a digital object that allows systems to verify the identity & subsequently establish an encrypted network connection to another system using the Secure Sockets Layer/Transport Layer Security (SSL/TLS) protocol. Amazon recommends that you always use a secure connection, but your server is required to have a valid TLS/SSL certificate, issued by a trusted Certificate Authority, in these two instances.
Login Security Options
During buyer login, there are two options, either a popup window or redirecting the buyer to another webpage. Depending on the login type that you choose, one of the following secure connections must be used:
- Popup Login: TLS/SSL is required on the website where the button is embedded.
- Redirect Login: The return URL must redirect the buyer to a secure page.
Note: When testing in a local environment a TLS/SSL certificate is not required (http://localhost).
IPN messages – IPN (Instant Payment Notification) messages can only be sent to a secure endpoint. Without a valid certificate, Amazon can’t tell whether the server receiving the IPN messages belongs to the merchant or to somebody who is trying to intercept the data.
What Are SSL/TLS?
- Transport Security Layer (“TLS”) and Secure Sockets Layer (“SSL”) are protocols designed to ensure that data can be securely transported between a web server and a browser, using cryptographic algorithms. TLS/SSL ensures that the data transmitted comes from the source it claims to be coming from, and that it has not been modified or read by a third party during the transmission.
- SSL certificates are what enable websites to use HTTPS, which is more secure than HTTP. An SSL certificate is a data file hosted in a website’s origin server. SSL certificates make SSL/TLS encryption possible, and they contain the website’s public key and the website’s identity, along with related information.
- Devices attempting to communicate with the origin server will reference this file to obtain the public key and verify the server’s identity. The private key is kept secret and secure.
- SSL, most commonly called TLS, is a convention for encoding Web traffic and confirming server personality. Any site with a HTTPS web address utilizes SSL/TLS.

TLS/SSL uses certificates to secure and protect transmitted data. A certificate contains information about the owner of the certificate, like the organization, country, duration of validity, website address, and the certificate ID of the person who certifies (or signs) this information. It also contains the public key and a hash to ensure that the certificate hasn’t been tampered with.
Here is a sample certificate:
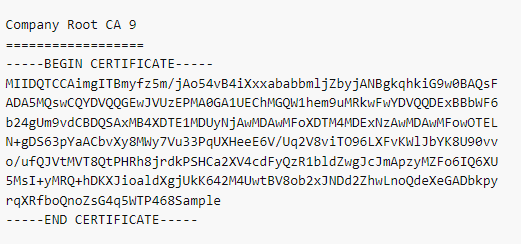
Why Do We Need An SSL Certificate?
We need SSL certificate to provide security to user data, verify ownership of the website, prevent attackers from creating a fake version of the site, and gain user trust. The following are key terminologies regarding this SSL certificate.
- Encryption: SSL/TLS encryption is possible because of the public-private key pairing that SSL certificates facilitate. Clients (such as web browsers) get the public key necessary to open a TLS connection from a server’s SSL certificate.
- Authentication: SSL certificates verify that a client is talking to the correct server that actually owns the domain. This helps prevent domain spoofing and other kinds of attacks.
- HTTPS: Most crucially for businesses, an SSL certificate is necessary for an HTTPS web address. HTTPS is the secure form of HTTP, and HTTPS websites are websites that have their traffic encrypted by SSL/TLS.
In addition to securing user data in transit, HTTPS makes sites more trustworthy from a user’s perspective. Many users won’t notice the difference between an http:// and an https:// web address, but most browsers tag HTTP sites as “not secure” in noticeable ways, attempting to provide incentive for switching to HTTPS and increasing security.

In order to achieve security we have to use SSL/TLS certificates. This will provide access control and data security to user.
Why Are SSL/TLS Certificates Important?
SSL/TLS certificates establish trust among website users. Businesses install SSL/TLS certificates on web servers to create SSL/TLS-secured websites. The characteristics of an SSL/TLS-secured webpage are as follows:
- A padlock icon and green address bar on the web browser
- An https prefix on the website address on the browser
- A valid SSL/TLS certificate. You can check if the SSL/TLS certificate is valid by clicking and expanding the padlock icon on the URL address bar
- Once the encrypted connection has been established only the client & the webserver can see the data that is sent.
- We give some benefits of SSL/TLS certificates below.
Tags Used To Create/use SSL/TLS certificates
- Protects Private Data: Browsers validate the SSL/TLS certificate of any website to start and maintain secure connections with the website server. SSL/TLS technology helps ensure the encryption of all communication between your browser and the website.
- Strengthen Customer Confidence: Internet-savvy customers understand the importance of privacy and want to trust the websites they are visiting. An SSL/TLS-protected website has the green padlock icon, which customers perceive as secure. SSL/TLS protection helps customers know that their data is being protected when they share it with your business.
- Supports Regulatory Compliance: Some businesses must comply with industry regulations for data confidentiality and protection. For example, businesses in the payment card industry must adhere to the PCI DSS. PCI DSS is an industry requirement for providing secure online transactions, including securing the web server with an SSL/TLS certificate.
- Improve SEO: Major search engines have made SSL/TLS protection a ranking factor for search engine optimization. An SSL/TLS-secured website will likely rank higher on the search engine than a similar website without an SSL/TLS certificate. This increases visitors from search engines to the SSL/TLS-protected website.
- Creating a Certificate: It Creates an SSL/TLS certificate for an Amazon Lightsail Content Delivery Network (CDN) distribution and a container service.
- Once the certificate is valid and ready to use, we have to use the Attach Certificate To Distribution action to use the certificate and its domains with the distribution.
How SSL/TLS works ?
- Request or import a SSL/TLS certificate you would like to use into your AWS account.
- Validate domain ownership for your requested certificate using Domain Name System (DNS) or email validation to complete certificate issuance.
- Use your newly issued or imported certificates in various AWS services like Elastic Load Balancing (ELB), Amazon Cloud Front etc.

Here we have requested 2 certificates which are pending status, Once certificate is validated then we can use it for our application.Use AWS Certificate Manager (ACM) to provision, manage, and deploy public and private SSL/TLS certificates for use with AWS services and your internal connected resources. ACM removes the time-consuming manual process of purchasing, uploading, and renewing SSL/TLS certificates.

Steps To Create AWS SSL/TLS Certificate
We will be performing 6 steps to request an SSL/TLS Certificate using AWS Certificate Manager.
Step 1: Provision Certificates
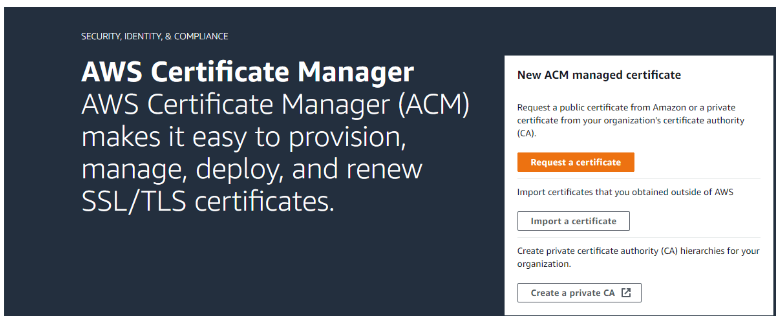
- Sign in to the AWS Management Console and navigate to the ACM console. Choose to Get started to request a certificate.
- Choose under Services → Security, Identity & Compliance → AWS Certificate Manager.
- This will list all the certificates if you already created under a particular region or will show a similar screenshot that will allow you to request a new certificate or import a certificate or create a private CA.
Step 2: Request a Certificate
- Requesting an SSL/TLS certificate
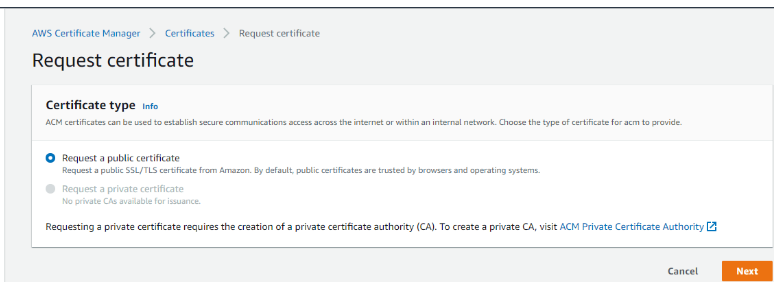
- In the first step, we are going to request a public SSL/TLS certificate for a domain to establish secure communication access across the internet. Click Request a certificate button to proceed,
- On the next screen, choose “Request a public certificate” as shown below. Here note that requesting a private certificate is grayed out because requesting a private certificate requires the creation of a private certificate authority (CA). To create a private CA, one must visit the ACM Private Certificate Authority link page shown.
- Now, choose Request a Public certificate to request a new certificate.
Step 3: Provide Domain Names
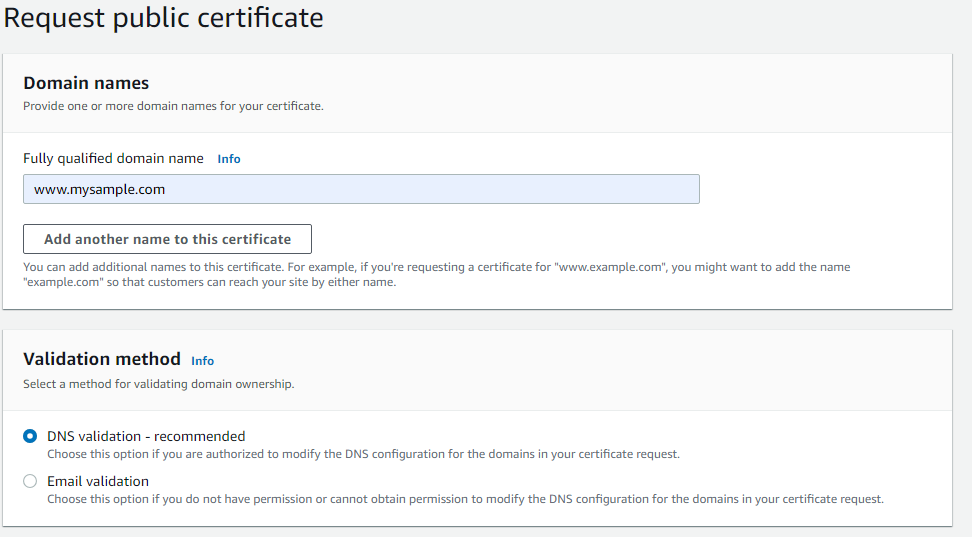
- In the following stage, clients need to give the completely qualified space name (FQDN) in the case. You may likewise add the name to the party declaration. For instance, in the event that you’re mentioning a declaration for “www.example.com”, you should add the name “example.com” so clients can arrive at your site by one or the other name.
- Provide your domain name and don’t forget to add a wildcard before your domain name.
- Choose this option if you are authorized to modify the DNS configuration for the domains in your certificate request. Another option is “Email validation” if you do not have permission or cannot obtain permission to modify the DNS configuration for the domains in your certificate request. Here we have the permission to modify the DNS configuration of the domain in the domain registrar control panel.
- In the tag section, you may provide the tag key and tag value which is an optional step. Click the “Request” button to proceed to the next step.
- Now you can see a successful request message as shown below, and you have the option to view the certificate.

- In this Certificates section, you can view the newly added domain with the status “Pending validation as shown in the below screenshot.
- Before the Amazon certificate authority (CA) can issue a certificate for the domain we have mentioned in the previous step, AWS Certificate Manager (ACM) must prove that you own or control all of the domain names that you specify in your request.
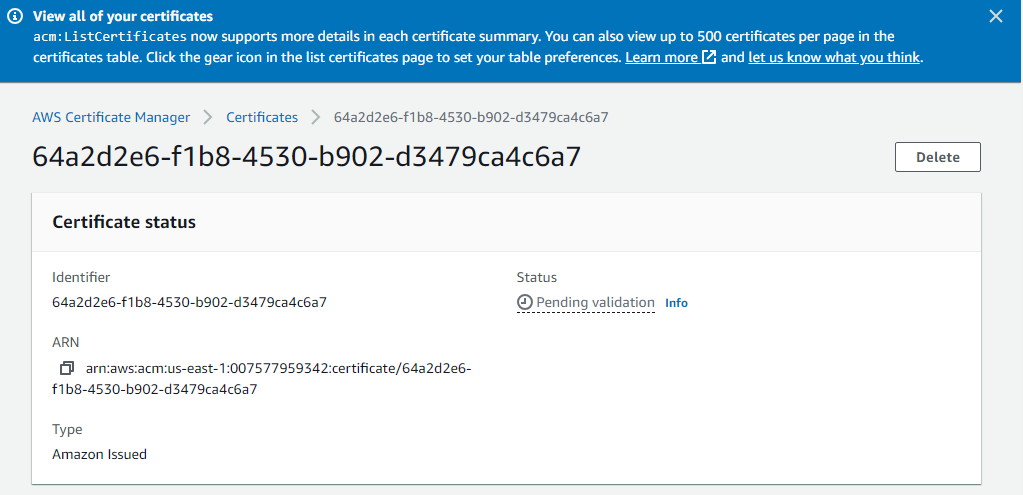
Step 4: Select The Validation Method
- On clicking the particular certificate, one can view the CNAME name and CNAME value for the domain to validate. Users can enter the CNAME name and CNAME value in the respective domain DNS section in their registrar DNS control panel, user can validate the domain manually.
- With DNS validation, you write a CNAME record to your DNS configuration to establish control of your domain name. Choose DNS validation, and then click on Next.

Create a CNAME record with the value of CNAME name ( Copy the content without the trailing domain name and paste in “Host” column in the DNS control panel ) & Copy the CNAME value and paste in the “Points to” column. Click Save and add this CNAME record.
Step 5: Create a Record in Route53
- Click on Create a record in Route53, then it automatically creates a CNAME record in Route53 hosted zone.

Step 6: Certificate Issued
- After adding the CNAME record, domain validation happens automatically after a few minutes, and you can verify this validation by the status changed from “Pending validation” to “Success” as shown in the screenshot below.
- Also, you can see the certificate status changed from “Pending validation” to “Issued” ( Shown in Redbox in the screenshot below ).
- Refresh, and once the validation is completed the status of the certificate will become issued.
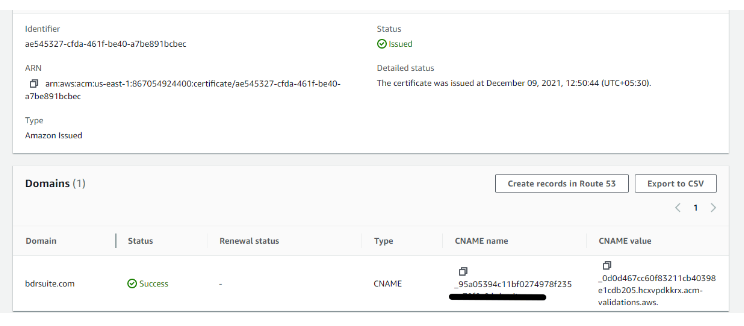
Step7: Deleting a Certificate
- You can also delete the certificate, in case of an expired certificate period or would like to discard the domain.
- In such a case, you can delete the certificate from the “List Certificate” page by selecting the certificate name and by clicking the Delete button. The below screenshot shows.

- A confirm dialog asks you to enter the text “delete” to confirm the delete process.
Importing A Certificate
Utilizing this choice, you can import testaments that you acquired beyond AWS. To import a self-marked SSL/TLS declaration into ACM, you should give both the endorsement and its confidential key. To import a declaration endorsed by a non-AWScertificate authority (CA), you should likewise incorporate the testament chain, yet all the same not a confidential key. Your authentication should fulfill the accompanying measures recorded underneath.
For all imported certificates, you must specify a cryptographic algorithm and a key size. ACM supports the following algorithms (API name in parentheses):
- 1024-bit RSA (RSA_1024)
- 2048-bit RSA (RSA_2048)
- 3072-bit RSA (RSA_3072)
- 4096-bit RSA (RSA_4096)
- Elliptic Prime Curve 256 bit (EC_prime256v1)
- Elliptic Prime Curve 384 bit (EC_secp384r1)
- Elliptic Prime Curve 521 bit (EC_secp521r1)
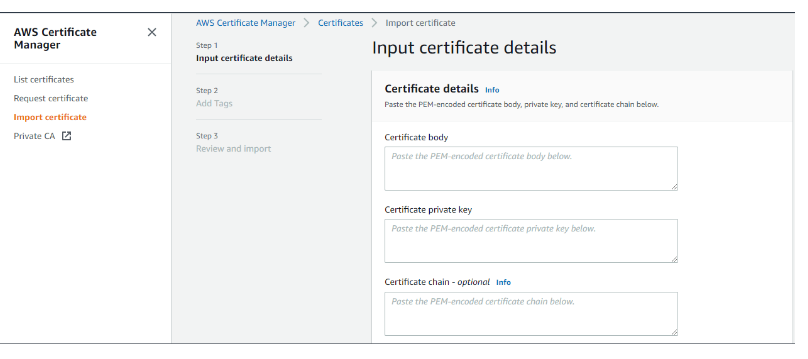
When importing a certificate, the user must need a Certificate body & Certificate Private key and optionally need a Certificate chain. The certificate, private key, and certificate chain must be PEM–encoded. The below screenshot shows these details. Here we are not importing any third-party certificates, and provide an overview of the steps involved in it.
Conclusion
The fundamental advantages of utilizing AWS Testament Director are “Free open declarations for ACM-incorporated benefits” and “Get Authentication without any problem”. With AWS Testament Director, there is no extra charge for provisioning public or confidential SSL/TLS endorsements you use with ACM-coordinated administrations, for example, Flexible Burden Adjusting and Programming interface Entryway. You pay for the AWS assets you make to run your application. AWS Authentication Director eliminates large numbers of the tedious and mistake inclined moves toward procure a SSL/TLS declaration for your site or application. There is compelling reason need to produce a vital pair or declaration marking demand (CSR), present a CSR to an Endorsement Authority, or transfer and introduce the testament once got. With a couple of snaps in the AWS The board Control center, you can demand a confided in SSL/TLS testament from AWS. When the authentication is made, AWS Declaration Administrator deals with conveying endorsements to assist you with empowering SSL/TLS for your site or application.
SSL/TLS Certificates – FAQ’s
What Is The Difference Between SSL And TLS?
Transport Layer Security (TLS) is the upgraded version of SSL that fixes existing SSL vulnerabilities. TLS authenticates more efficiently and continues to support encrypted communication channels.
Why Do We Use TLS?
Transport Layer Security, or TLS, is a widely adopted security protocol designed to facilitate privacy and data security for communications over the Internet. A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website.
Why Is SSL TLS Required?
The main use case for SSL/TLS is securing communications between a client and a server, but it can also secure email, VoIP, and other communications over unsecured networks.
Does AWS Use SSL Or TLS?
AWS Certificate Manager (ACM) is a service that lets you easily provision, manage, and deploy public and private SSL/TLS certificates for use with AWS services and your internal connected resources.
How Does SSL And TLS Work?
SSL/TLS uses both asymmetric and symmetric encryption to protect the confidentiality and integrity of data-in-transit. Asymmetric encryption is used to establish a secure session between a client and a server, and symmetric encryption is used to exchange data within the secured session.
Share your thoughts in the comments
Please Login to comment...