AWS CLI For Identity And Access Management
Last Updated :
11 Mar, 2024
Amazon Web Services (AWS) is a comprehensive cloud computing platform offering many services, including storage, computing, databases, and more. AWS Identity and Access Management (IAM) is a core AWS service that allows you to securely control who can access your AWS resources and what actions they can perform. IAM enables you to create users, groups, and roles, and define granular permissions for each.
AWS CLI
Amazon’s command-line interface (CLI) is a powerful tool that allows users to interact with various AWS services through a command-line interface.
Install AWS CLI
Assuming you already have an AWS account, follow the steps below to install AWS CLI on your system (these steps are based on Ubuntu OS).
You can either follow the instructions from the AWS documentation or run the below commands in your terminal to install AWS CLI in your system
sudo apt-get install awscli -y
-1024.png)
Install AWS CLI
Configure AWS Credentials
- Login to AWS Console
- Click on your username at top right corner and click on Security Credentials
- Under Access keys click on Create access key –> Choose Command Line Interface (CLI) –> add some description for it -> Create
- Either copy Access key ID and Secret access key displayed on the screen or download csv file.
aws configure --profile <profile-name>
For example:
aws configure --profile dillip-tech
-1024.png)
Configure AWS CLI with custom profile
Fill the prompts for access key and secret you’ve copied in above steps, and now you’re all set to tryout AWS IAM resources.
Manage IAM resources with CLI
The AWS CLI offers a comprehensive set of commands for managing various aspects of IAM. Here’s the comprehensive list of examples demonstrating common operations:
Creating Users:
To create an IAM user, run the below command, This command creates a new IAM user named “new-user.”
aws iam create-user --user-name new-user
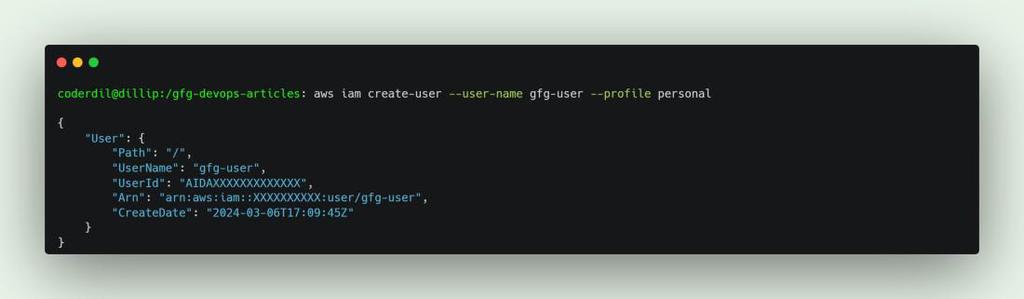
Create IAM User
Listing Users and Roles:
aws iam list-users
This will list the IAM users in the mentioned profile, with basic details, like Username, UserId, Arn, and createdDate, refer the sample below.
-1024.jpg)
List IAM Users
aws iam list-roles
These commands list all the roles currently existed in your AWS account, with all basic details, RoleName, RoleID, Arn, and AssumeRolePolicyDoc.
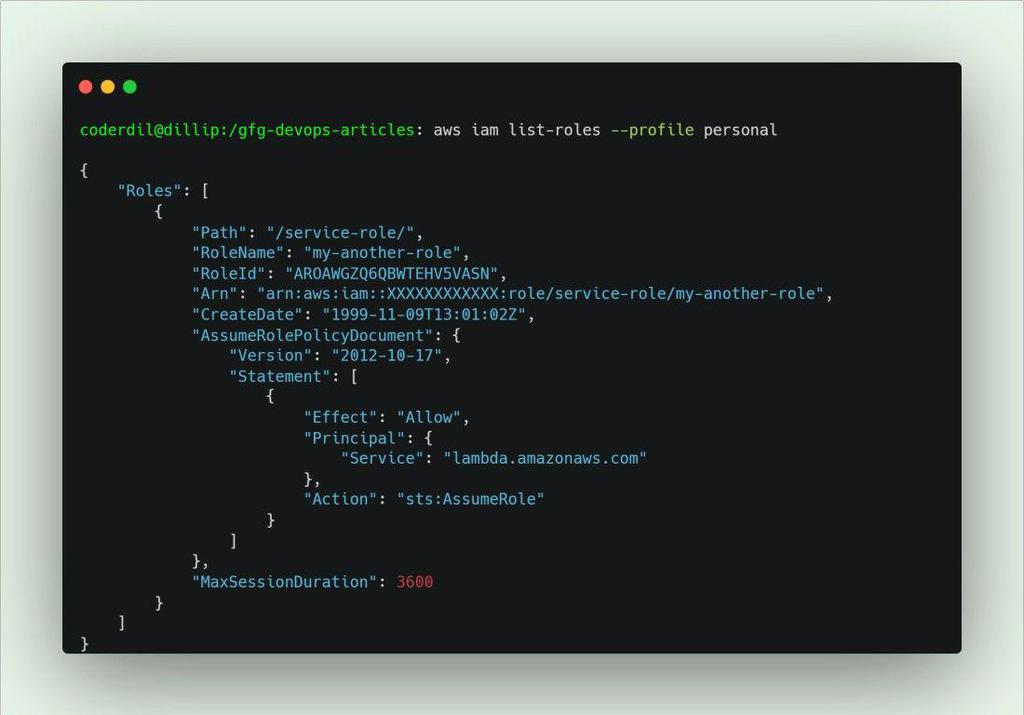
List IAM Roles
Create Access Keys for Users:
This below command generates a new access key ID and secret access key for the user new-user, we can use it for various use cases like CLI, SDK.
aws iam create-access-key --user-name new-user
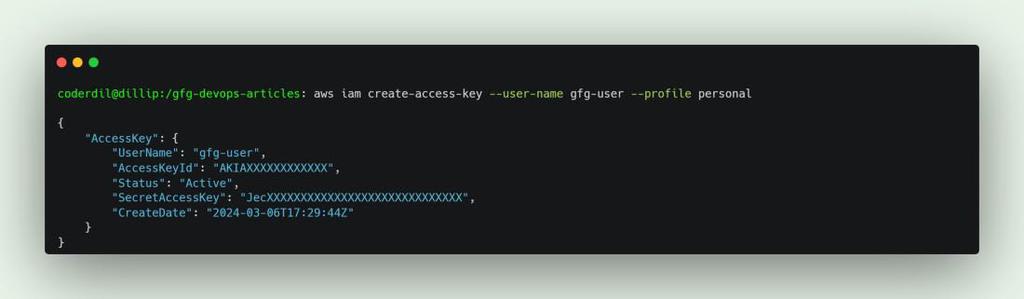
Create Access key for user
Create IAM Groups:
aws iam create-group --group-name new-user-group
This command creates a new IAM group named new-user-group.
.jpg)
Create IAM Group
Add Users to Groups:
aws iam add-user-to-group --user-name new-user --group-name new-user-group
This command adds the user new-user to the group new-user-group.
.jpg)
Add User to IAM Group
Create IAM Roles:
aws iam create-role --role-name my-new-role --assume-role-policy-document file://trust-policy.json
This command creates a new IAM role named my-new-role.
.jpg)
Create IAM Role
Attach Permissions Policies to Roles:
aws iam attach-role-policy --role-name my-new-role --policy-arn arn:aws:iam::aws:policy/AmazonEC2FullAccess
This command attaches the managed policy “AmazonEC2FullAccess” to the role my-new-role, granting access to EC2 resources.
.jpg)
Attach Role Policy
Assume IAM Roles:
aws sts assume-role --role-arn arn:aws:iam::123456789012:role/my-new-role --role-session-name my-temp-session
.jpg)
Assume IAM Role
This command allows you to temporarily assume the permissions of the role my-new-role for a specific session named my-temp-session.
These are just a few examples, and the AWS CLI offers a comprehensive range of commands for managing IAM entities and permissions.
Beyond the Basics: Advanced Features
The AWS CLI empowers you with advanced functionalities for IAM management:
- User Password Rotation: Reset or rotate user passwords to maintain security.
- MFA (Multi-Factor Authentication) Configuration: Enforce MFA for enhanced security when accessing AWS resources.
- Granular Permission Policies: Craft custom IAM policies with fine-grained control over user and role actions.
- Simulate User Actions: Test IAM policies to verify user permissions before granting access.
- By leveraging these advanced capabilities, the AWS CLI becomes a powerful tool for managing IAM within your AWS environment.
AWS CLI for Identity and Access Management – FAQ’s
How can I enhance security when using AWS CLI access keys?
Implement best practices such as rotating access keys regularly, using IAM roles instead of long-term access keys.
What considerations should I keep in mind when creating IAM roles?
Clearly define the role’s purpose and attach policies with the minimum required permissions, restrict based on aws services, users as principals, so that the purpose would not deviate.
Can i update the credentials for Profile?
Yes, you can update credentials at any time, just run the command again, i.e aws configure –profile <profilename>, it will prompt for updated credentials, enter the credentials, these will be replaced with old ones.
Share your thoughts in the comments
Please Login to comment...