Cyber Security – Introduction to DNS Tunneling
Last Updated :
06 Sep, 2022
DNS(Domain Name System) is a host-name to IP address translation service. It is an application layer protocol for message exchange among users and servers. Each host is recognized by the IP address, as recalling numbers is exceptionally hard for individuals, and furthermore, the IP addresses are not static subsequently. So DNS is utilized to translate the domain name of the sites to their numerical IP address.
What is DNS Tunneling?
DNS Tunneling is a strategy for a digital exploit that encodes the information of different programs or protocols in DNS inquiries and responses. DNS tunneling frequently incorporates information payloads that can be added to an exploited domain name server and used to control a distant system and applications. Normally, DNS tunneling requires the undermined framework to have outside organization availability, as DNS tunneling expects admittance to an interior DNS server with network access. Hackers should likewise control a system that can go about as a definitive server to execute the server-side tunneling and information payload executable programs.
Why DNS Tunneling is a Problem?
DNS was initially made for name resolution and not for data exchange, so it’s regularly not seen as a malignant interchange of information and data exfiltration danger. Since DNS is entrenched and confided protocol, attackers realize that organizations seldom investigate DNS packets for malevolent movement. DNS has less consideration and most organizations center assets around breaking down web or email traffic where they believe, attacks regularly occur. As a general rule, constant endpoint checking is needed to discover and forestall DNS tunneling. Besides, tunneling application bundles have become an industry and are uncontrollably accessible on the Internet, so hackers don’t generally require specialized advancement to execute DNS tunneling exploits.
- DNS tunneling exploits can give aggressors a consistently accessible back channel to exfiltrate taken information. It depends on utilizing DNS as a convert correspondence channel to sidestep a firewall.
- Hackers tunnel various types of protocols like SSH or HTTP with DNS, at that point secretly pass stolen information or passage IP traffic.
- A DNS tunnel can be utilized as a full controller channel for an already exploited inside host. This lets the hackers secretly move records out of the organization, download new code to the existing malware, or have total distant admittance to the servers, etc.
- DNS tunnels can likewise be utilized to bypass captive portals, to abstain from paying for Wi-Fi services.
- DNS tunneling utilizes the DNS protocol to tunnel the malware and other information through a client-server model.
How Does DNS Tunneling Works?
- The hacker enlists a domain, for example, hello.com. This domain name server focuses on the aggressor’s system, where a tunneling malware program is introduced. The hacker exploits a PC, which frequently sits behind an organization’s firewall, with malware.
- Since DNS demands are constantly permitted to move all through the firewall, the attacked PC is permitted to send an inquiry to the DNS resolver. The DNS resolver is a server that transfers demands for IP addresses to root and high-level domain-servers.
- The DNS resolver courses the inquiry to the aggressor’s command server, where the tunneling program is introduced. Presently, a connection has been established between the attacked person and the hacker through the DNS resolver.
- This passage can be utilized to exfiltrate information or for different pernicious purposes. Since there is no direct connection made between the victim and hacker, which makes it harder to follow the hacker’s PC.
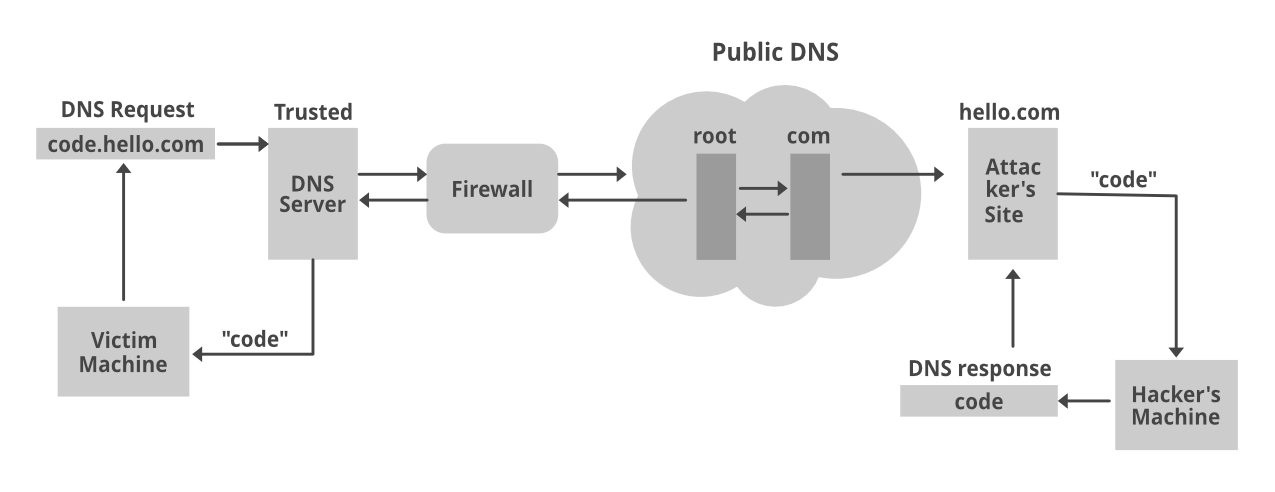
DNS is essential to all organizations. Lamentably, obstructing DNS-based dangers is a significant test, and cyber criminals are utilizing its inescapable however not entirely obvious exploitable surface for their potential benefit.
As per research, over 80% of malware utilizes DNS to distinguish a command-and-control (C2) server to take information and spread malware. On the head of that, aggressors are expanding their utilization of domain generation algorithms (DGAs) to make it considerably harder to distinguish and stop these dangers. Then, security groups are feeling the squeeze to authorize predictable insurance against a large number of new malevolent domains and remain in front of cutting edge strategies like DNS tunneling.
Common Abuse Cases
- Information Exfiltration: Attackers sneak delicate information out over DNS. It’s absolutely not the most proficient approach to get information from a casualty’s PC—with all the additional overhead and encoding—yet it can work.
- Command and Control (C2): Hackers utilize the DNS convention to send basic orders to a remote access trojan (RAT).
- IP-Over-DNS Tunneling: There are utilities that have actualized the IP stack on the DNS inquiry reaction convention. That would make it generally simple to move information utilizing standard communication programs like FTP, Netcat, ssh, etc.
Detecting DNS Tunneling
- Payload Analysis: In this, the cybersecurity specialists are taking a gander at bizarre information being sent to and fro: peculiar-looking hostnames, a DNS record type that is not utilized all that frequently, and unordinary character sets that can be spotted by factual strategies. This technique can help us in detecting certain DNS Tunneling utilities.
- Traffic Analysis: Protectors are taking a gander at the number of solicitations to a DNS and contrasting it against normal utilization. Attackers who are performing DNS tunneling will make exceptionally weighty traffic to the DNS. In principle, a lot more noteworthy than ordinary DNS communication. This strategy does a search for some specific attributes which help in the detection process such as no. of hostnames per domain, geographic location, domain’s history, etc.
- DNS Monitoring Utilities: There are also some utilities available for monitoring the DNS like dnsHunter, reassemble dns, etc.
Common DNS Tunneling Toolkits
- Iodine: Through this one can easily tunnel the IPv4 information through a DNS server. It makes an organization interface on every one of the customers and associates them together as though they had a similar organization. This element is interesting to Iodine since different DNS tunneling instruments center around tunneling explicit ports, and not the whole IPv4 traffic. This permits PCs to ping one another, control all UDP/TCP ports, and all different conventions that are embodied by an IP header. This tool is a built-in case of the Kali OS but incase of others both the client and the server can be configured by using a TUN/TAP device. Features of this tool include self-optimization, high-performance, portability, authentication. But there are some problems also which include tunneling of only IPv4 traffic, no encryption of tunneled data, requirements of drivers.
- DNSCat2: This toolkit is partitioned into two segments, a client and a server. The server is programmed in C language whereas the client is in Ruby. The server is extensive and can uphold associations from numerous customers, which makes it an essential C&C worker. It should run first, before any of the customers. Some of its features include encryption, sessions just like Metasploit, and tunnels for TCP forwarding, etc. But, the problems we can face with the toolkit include slow performance, limited sessions, tunneling limitations.
- Heyoka: This is a tool commonly used for exfiltration with the support of dismissive DNS queries in order to create a bidirectional connection. this tool isn’t under dynamic improvement any longer and as indicated by its creators, is up to 60% quicker than other toolkits available. This tool generally makes the identification by a firewall and finding the machine that is tunneling a lot harder. So, it right now works just on Windows. Some of its features include high-performance, complex attacks, independent of interpreters or compilers. But, the problems we can face with this include instability, executable only on windows OS, no encryption, etc.
- There are much more available such as OzymanDNS, etc.
Precautions For DNS Tunneling
- Always use a tool which can easily distinguish between both pre configured tool kits and different methods
- Boycott stations are known for information exfiltration
- Incorporate a DNS firewall that searches for DNS tunneling
- Do automated monitoring, which can be done by using real-time analytics
- Preferably, DNS protection should be accomplished by stand-alone solutions
- Make those tools come into play which can easily detect various malicious queries, and effectively terminate them.
Conclusion
DNS isn’t the main protocol that can use for tunneling. For instance, Command and Control (C2) malware frequently use HTTP as an approach to conceal correspondences. Similarly likewise with DNS tunneling, the attackers shroud their information however, for this situation, it’s made to seem as though browser traffic to a far off-site (constrained by the hackers). It can communicate under the radar of observing monitoring that is not sensitive to this danger of abusing HTTP for underhanded purposes.
A firewall is not, at this point enough to isolate inner networks and secure it, as DNS tunneling has proved to be one of the most innovative strategies used by hackers for spoofing the organizations and getting away. For instance, Heyoka’s covertness component demonstrates that what’s undetectable from the firewall’s viewpoint, is clearly malevolent from the endpoint’s perspective. To battle DNS tunneling, the weight has moved away from the organization to the endpoint. Security experts and sellers must analyze approaching and active traffic at the endpoint to recognize and crush these attacks.
Share your thoughts in the comments
Please Login to comment...