How to create Azure Alerts using Terraform
Last Updated :
30 Apr, 2024
Azure Monitoring helps you monitor the data in your Azure cloud environment. If you set alerts, it will help you proactively respond to any issue that arises within their Azure resources. Azure Monitoring data platform is made up of Logs and metrics. Each feature of Azure Monitoring collects various kinds of data and also helps to enable different Azure Monitoring features, respectively.
Terraform is infrastructure as code (IAC) practices which is important for monitoring Azure resources and provides various benefits. This helps to manage low-level and high-level components like storage, computing and networking resources, DNS entries, and SaaS features.
Creating Azure Alerts using Terraform | Step-by-Step
Step 1: The user has to set up Terraform and Azure by installation on a local machine, and the following are the steps:
- Terraform installation: Install and download Terraform on your local machine from the official website.
- Azure CLI installation: Install and download Azure CLI for to authenticate Terraform with your Azure account.
Step 2: You have to configure the provider in Terraform and have to create a new file.
- Create a file name with Azure alerts or name it with any other file name with ‘. tf ‘ extension and to configure the Azure provider you have to add the following configurations to provider.tf .
provider "azurerm" {
features {}
}
Step 3: You have to define the Azure Alert rule using Terraform.
- Create a new configuring terraform file for Azure, for example : “azure monitor“. After this, you have to define the alert rule accordingly as per the user requirement specify the conditions under which the alert triggers when a specified metric breaches a threshold, the resource it should monitor as specified by the user, and the action to take when the condition is met.
Below is the example where the user can take reference and configure accordingly as per the requirement:
resource "azurerm_monitor_metric_alert" "azure_monitor" {
name = "azure_monitor"
resource_group_name = "<resource_group_name>"
scopes = ["<resource_id_of_the_monitored_resource>"]
criteria {
metric_namespace = "<metric_namespace>"
metric_name = "<metric_name>"
aggregation = "<aggregation_function>"
operator = "<comparison_operator>"
threshold = <threshold_value>
}
action {
action_group_id = "<action_group_id>"
}
}
- Make sure to replace the value of <resource_group_name>, <resource_id_of_the_monitored_resource>, <metric_namespace>, <metric_name>, <aggregation_function>, <comparison_operator>, <threshold_value>, and <action_group_id> with actual values respectively.
Step 4: You have to apply Terraform Configuration.
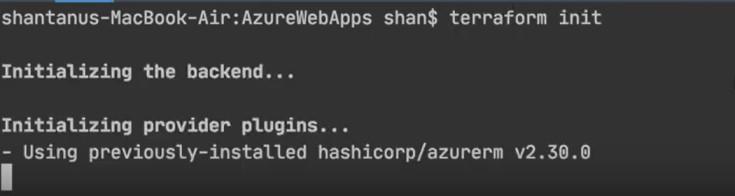
- Initialize the terraform using the following init command to initialize the backend in the working directory:
terraform init
- Run the following terraform command to ensure that the execution plan will create the resources as per the expectation:
terraform plan

- If the above command compiles successfully moving forward user can apply the Terraform configuration to create the Azure resources.
terraform apply
(1).jpg)
- Once the above command executed by the user , then the user can check the same alert create on the azure portal as shown below
.png)
Step 5: Verify and Test the alerts on azure.
- As discussed above after applying the Terraform configuration, verify that the Azure resources, including the alert rule, are created successfully by checking the Azure portal.
- By this user can verify the functionality of the alert rule by deliberately triggering the conditions outlined in the criteria. For example, if the alert is based on CPU usage, you can simulate high CPU usage on the monitored resource.
Refer the below image we have an example email received where an email is received to the user when the CPU threshold reached over 90% of the sever.
.png)
Conclusion
In this post, we’ve covered a few of the crucial commands and instructions that are used in and detailed how create an azure alert using terraform using examples. It provided easy-to-grasp syntax and examples for each and every command.
Create Azure Alerts Using Terraform – FAQs
What are Azure Alerts?
Azure Alerts allow users to monitor the resources deployed in Microsoft Azure. They enable you to receive notifications and take automated actions based on defined conditions from various Azure services.
What are the type of azure alerts offered by azure:
Six different types of Azure Alerts are available as mentioned following.
- Metric Aert
- Activity log Alert
- Log Analytics Alert
- Service Health Alert
- Security Alert
- Azure Monitor Alert
Why use Terraform for creating Azure Alerts?
Terraform provides a declarative syntax for defining infrastructure configurations, including Azure resources. Using Terraform for creating Azure Alerts ensures that the alert configurations are version-controlled, reproducible, and can be managed alongside other infrastructure components.
What are the prerequisites for creating Azure Alerts using Terraform?
Before creating Azure Alerts using Terraform, you need an Azure subscription, Terraform installed on your local machine, and appropriate Azure permissions to create resources.
How do I get started with Terraform?
To get started with Terraform, you need to download and install the Terraform CLI on your local machine. You can then define your infrastructure configurations in Terraform configuration files with the .tf extension.
Share your thoughts in the comments
Please Login to comment...