The application load balancer distributes incoming HTTP and HTTPS traffic across multiple targets such as Amazon EC2 Instances, microservices, and containers, based on request attributes. When the load balancer receives a connection request, it evaluates the Listener rules in priority order to determine which rule to apply, and if applicable, it selects the target from the target group for the rule action. AWS EC2 and Elastic Load Balancing are two different services that work well together. AWS ELB is built to support increased traffic without increasing the hourly cost. ELB scales automatically.
Types of Elastic Load balancers
The Elastic Load balancer supports in different ways, which are
- Application Load Balancers
- Network Load Balancers
- Gateway Load Balancers
- Classic Load Balancers
Components of Application Load Balancer:
The Load balancing is made up of three components:
- Origin pools: These contain one or more servers.
- Origin servers: These respond to individual requests.
- A load balancer: This decides which traffic goes to each origin pool
If the load balancer works normally, requests to your application will go to individual servers directly. With a load balancer, requests first go through the load balancer. Your load balancer then routes requests to specific pools. Within each pool, requests then go to individual servers. And that server is what responds to the request.
How Application Load balancer work
- Clients make requests to your application.
- The listeners in your load balancer receive requests matching the protocol and port that you configure.
- The receiving listener evaluates the incoming request against the rules you specify, and if applicable, routes the request to the appropriate target group. You can use an HTTPS listener to offload the work of TLS encryption and decryption to your load balancer.
- Healthy targets in one or more target groups receive traffic based on the load balancing algorithm, and the routing rules you specify in the listener.
Overview of Application Load Balancer
An Application Load Balancer functions at the application layer, the seventh layer of the Open Systems Interconnection (OSI) model. After the load balancer receives a request, it evaluates the listener rules in priority order to determine which rule to apply, and then selects a target from the target group for the rule action.
You can configure listener rules to route requests to different target groups based on the content of the application traffic. Routing is performed independently for each target group, even when a target is registered with multiple target groups.
You can configure the routing algorithm used at the target group level. The default routing algorithm is round robin; alternatively, you can specify the least outstanding requests routing algorithm.
Elastic Load Balancing scales your load balancer as traffic to your application changes over time. Elastic Load Balancing can scale to the vast majority of workloads automatically, and configure health checks, which are used to monitor the health of the registered targets so that the load balancer can send requests only to the healthy targets.

Features of Application Load Balancer
Application Load Balancer operates at the request level (layer 7), routing traffic to targets (EC2 instances, containers, IP addresses, and Lambda functions) based on the content of the request. Application Load Balancer simplifies and improves the security of your application, by ensuring that the latest SSL/TLS ciphers and protocols are used at all times.

1. Native IPv6 Support
Application Load Balancers support native Internet Protocol version 6 (IPv6) in a VPC. This will allow clients to connect to the Application Load Balancer via IPv4 or IPv6.
2. TLS Offloading
You can create an HTTPS listener, which uses encrypted connections (also known as SSL offload). This feature enables traffic encryption between your load balancer and the clients that initiate SSL or TLS sessions.
Application Load Balancer supports client TLS session termination. This enables you to offload TLS termination tasks to the load balancer, while preserving the source IP address for your back-end applications.
You can choose from predefined security policies for your TLS listeners in order to meet compliance and security standards. AWS Certificate Manager (ACM) or AWS Identity and Access Management (IAM) can be used to manage your server certificates.
3. HTTPS Support
An Application Load Balancer supports HTTPS termination between the clients and the load balancer. Application Load Balancers also offer management of SSL certificates through AWS Identity and Access Management (IAM) and AWS Certificate Manager for pre-defined security policies.
4. HTTP/2 and gRPC Support
HTTP/2 is a new version of the Hyper Text Transfer Protocol (HTTP) that uses a single, multiplexed connection to allow multiple requests to be sent on the same connection. It also compresses header data before sending it out in binary format and supports SSL connections to clients.
Application Load balancer can route and load balance gRPC traffic between microservices or between gRPC enabled clients and services. This allows introduction of gRPC traffic management in the architectures without changing any of the underlying infrastructure on the customers’ clients or services.
gRPC uses HTTP/2 for transport and is becoming the protocol of choice for inter-service communications in microservices architectures. It has features like efficient binary serialization and support for numerous languages in addition to the inherent benefits of HTTP/2 like lighter network footprint, compression, and bi-directional streaming making it better than the legacy protocols like REST.
5. Layer-7 Load Balancing
You can load balance HTTP/HTTPS traffic to targets – Amazon EC2 instances, microservices, and containers based on request attributes (such as X-Forwarded-For headers).
6. Mutual TLS Support
Mutual TLS is a protocol for two-way authentication between clients and servers that use x509 certificate based identities. With this feature, the ALB will authenticate client certs and perform revocation checks for certificates issued by both third party Certificate Authorities(CAs) or Private Certificate Authority (ACM PCA).
The load balancer will also proxy client certificate information to the targets, which can be used for authorization decisions by the application.
7. Sticky Sessions
Sticky sessions are a mechanism to route requests from the same client to the same target. Application Load Balancers support both duration-based cookies and application-based cookies.
The key to managing sticky sessions is determining how long your load balancer should consistently route the user’s request to the same target. Sticky sessions are enabled at the target group level. You can use a combination of duration-based stickiness, application-based stickiness, and no stickiness across all of your target groups.
8. Content-based Routing
An Application Load Balancer can route a request to a service based on the content of the request such as Host field, Path URL, HTTP header, HTTP method, Query string or Source IP address.
- Host-based Routing : You can route a client request based on the Host field of the HTTP header allowing you to route to multiple domains from the same load balancer.
- Path-based Routing : You can route a client request based on the URL path of the HTTP header.
- HTTP header-based routing : You can route a client request based on the value of any standard or custom HTTP header.
- HTTP method-based routing : You can route a client request based on any standard or custom HTTP method.
- Query string parameter-based routing : You can route a client request based on query string or query parameters.
- Source IP address CIDR-based routing : You can route a client request based on source IP address CIDR from where the request originates.
9. Load-Balancing Algorithm
Application Load Balancer supports a round-robin load-balancing algorithm, and it supports a slow start mode with the round-robin algorithm that allows you to add new targets without overwhelming them with a flood of requests.
With the slow start mode, targets warm up before accepting their fair share of requests based on a ramp-up period that you specify. Slow start is very useful for applications that depend on cache and need a warm-up period before being able to respond to requests with optimal performance.
10. Outposts Support
Application Load Balancer supports AWS Outposts, a fully managed service that extends AWS infrastructure, services, and tools to virtually any datacenter, co-location space, or on-premises facility for a truly consistent hybrid experience. Customers can provision ALBs on supported instance types and the ALB will auto scale up to the capacity available on the rack to meet varying levels of application load without manual intervention.
Customers can also get notifications to help them navigate their load balancing related capacity needs. Customers can use the same AWS Console, APIs, and CLI to provision and manage ALBs on Outposts as they do today with ALBs in the Region.
11. Redirects
Application Load Balancer can redirect an incoming request from one URL to another URL. This includes the capability to redirect HTTP requests to HTTPS requests, which allows you to meet your compliance goal of secure browsing, while being able to achieve better search ranking and SSL/TLS score for your site.
12. Fixed Response
Application Load Balancer can control which client requests are served by your applications. This enables you to respond to incoming requests with HTTP error response codes and custom error messages from the load balancer itself, without forwarding the request to the application.
13. WebSockets Support
WebSockets allows a server to exchange real-time messages with end-users without the end users having to request (or poll) the server for an update. The WebSockets protocol provides bi-directional communication channels between a client and a server over a long-running TCP connection.
14. Server Name Indication (SNI)
Application Load Balancers can support a smart certificate selection algorithm with SNI. It is an extension to the TLS protocol by which a client indicates the hostname to connect to at the start of the TLS handshake. The load balancer can present multiple certificates through the same secure listener, which enables it to support multiple secure websites using a single secure listener.
If the hostname indicated by a client matches multiple certificates, the load balancer determines the best certificate to use based on multiple factors including the capabilities of the client.
15. User Authentication
Application Load Balancer will securely authenticate users as they access cloud applications, and it is integrated with Amazon Cognito, which allows end users to authenticate through social identity providers such as Google, Facebook, and Amazon, and through enterprise identity providers such as Microsoft Active Directory via SAML or any OpenID Connect-compliant identity provider (IdP).
If you already have a custom IdP solution that is OpenID Connect-compatible, Application Load Balancer can also authenticate enterprise users by directly connecting with your identity provider.
How to Deploy an Application Load Balancer
Step 1: Visit the AWS Console and type “EC2” into the search bar. After selecting EC2 dashboard drop-down menu below, you will be select to the Elastic Load balancing, where you can click “Create Load balancer”. As shown in the screenshots.
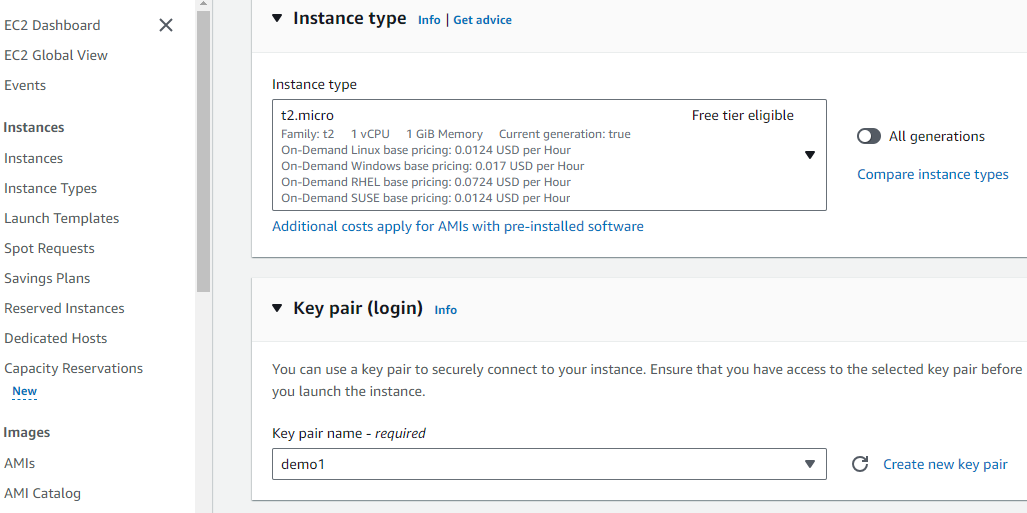
Step 2: In this step, first you can launch EC2 instance, Amazon EC2 allows you to create virtual machines, or instances, that run on the AWS Cloud. Quickly get started by following the simple steps below.
In this step EC2 instance give name and tags for identification purpose specific name given to ec2 instance(Webserver).

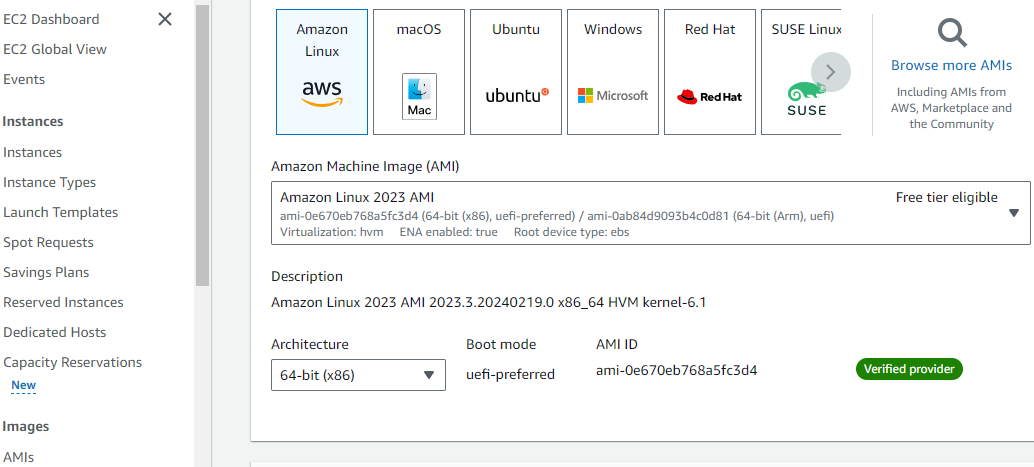
Application and OS Images, An AMI is a template that contains the software configuration (operating system, application server, and applications) required to launch your instance. Search or Browse for AMIs if you don’t see what you are looking for below
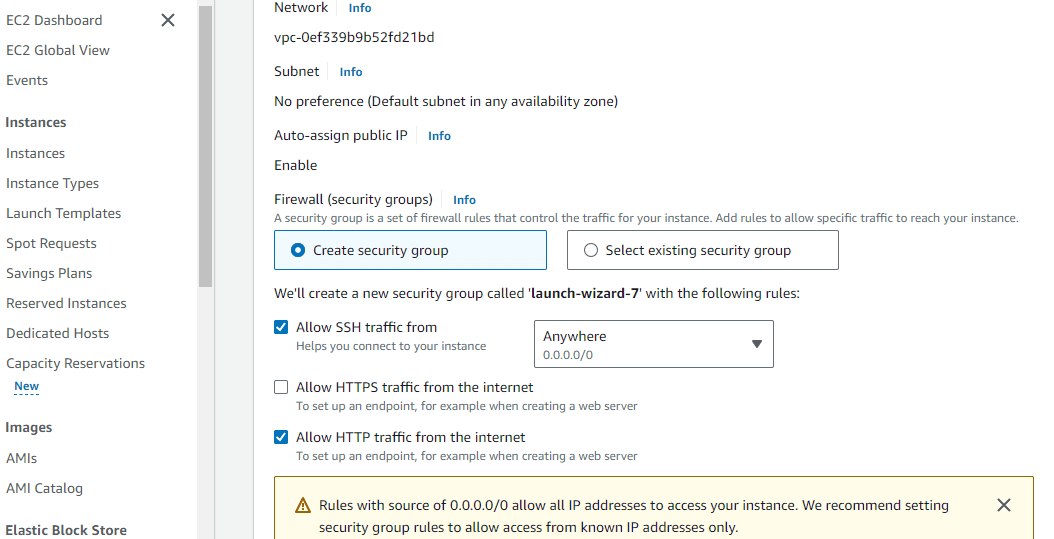

After enter the all details , the EC2 instance created succesfully as shown below,

Step 3: Choose a load balancer type
Elastic Load Balancing supports different types of load balancers. In this step, we are going to create Application Load balancer, click on create an Application load balancer, and enter the basic configuration of application load balancer.

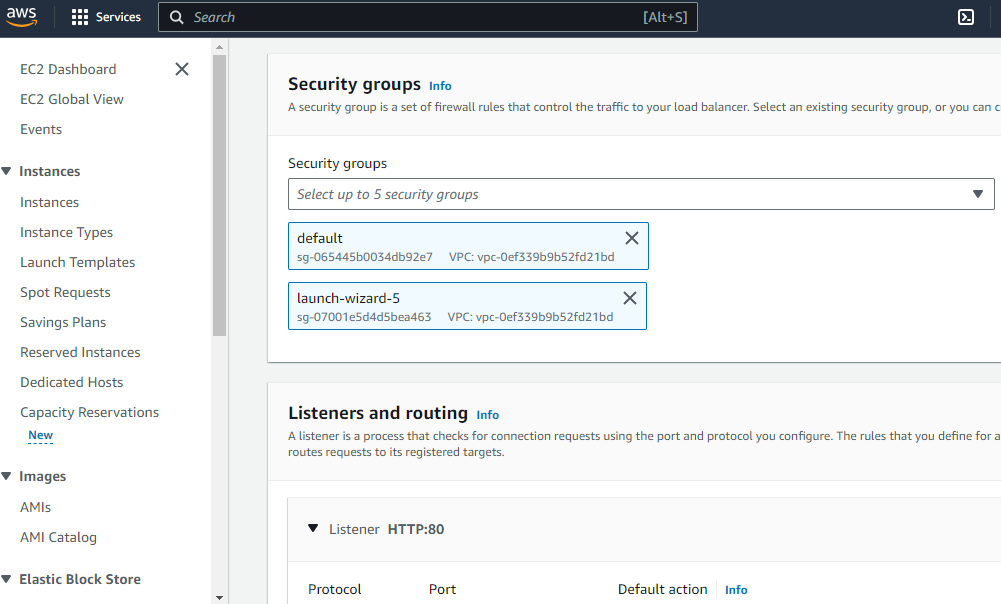
Step 4:Configure your load balancer
In this step to create an Application Load Balancer, you can provide basic configuration information for your load balancer, such as a name, scheme, and IP address type. Then, you provide information about your network, and one or more listeners. A listener is a process that checks for connection requests. It is configured with a protocol and a port for connections from clients to the load balancer.


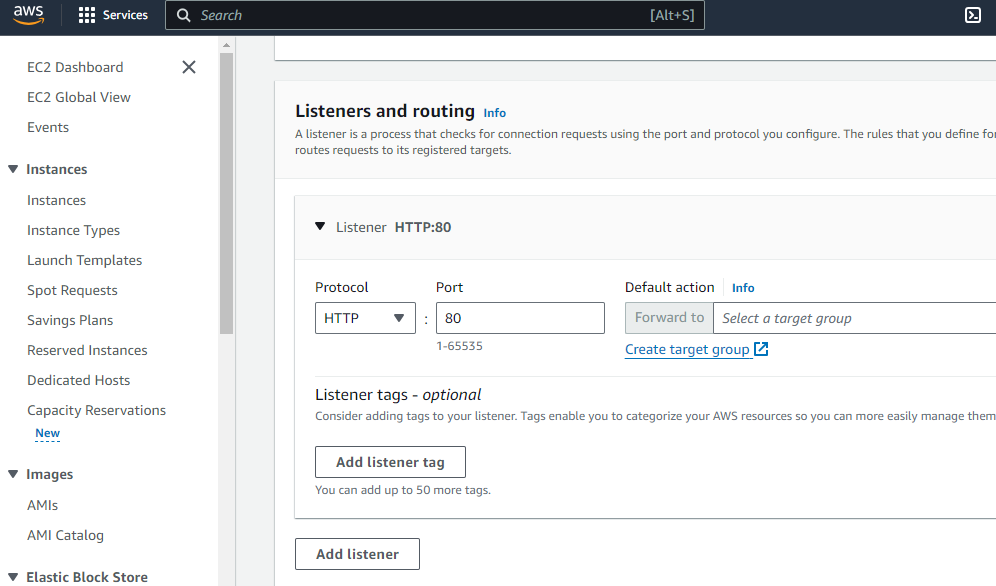
Step 5: Configure your target group
you can create a target group, which is used in request routing. The default rule for your listener routes requests to the registered targets in this target group. The load balancer checks the health of targets in this target group using the health check settings defined for the target group.
- Choose Create target group.
- Under Basic configuration, keep the Target type as instance.
- For Target group name, enter a name for the new target group.
- Keep the default protocol (HTTP) and port (80).
- Select the VPC containing your instances. Keep the protocol version as HTTP1.
- For Health checks, keep the default settings.
- Choose Next.
- On the Register targets page, complete the following steps. This is an optional step for creating the load balancer. However, you must register this target if you want to test your load balancer and ensure that it is routing traffic to this target.
For Available instances, select one or more instances.
- Choose Create target group.
- Successfully created My-target-group.
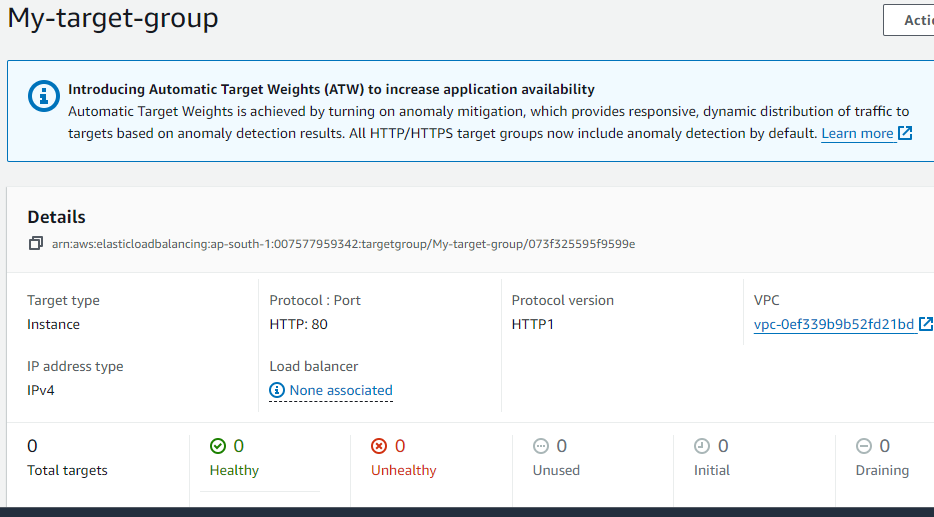
created Target Group
Step 6:Test your load balancer
After you are notified that your load balancer was created successfully shows below.
Select the newly created load balancer.
Choose Description and copy the DNS name of the load balancer (for example,Test-LB-504127462.ap-south-1.elb.amazonaws.com). Paste the DNS name into the address field of an internet-connected web browser. If everything is working, the browser displays the default page of your server.
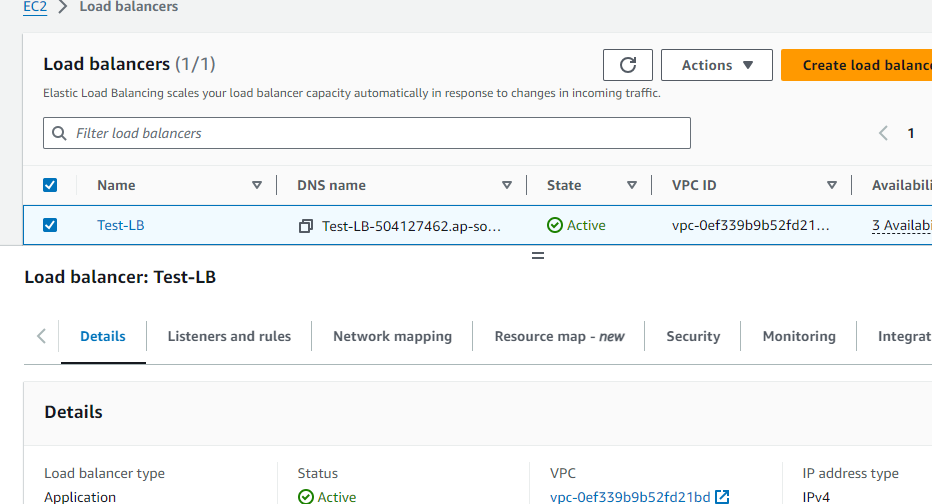
Created Application load balancer
Step 7: Delete your load balancer
you are billed for each hour or partial hour that you keep it running. When you no longer need a load balancer, you can delete it. As soon as the load balancer is deleted, you stop incurring charges for it. Note that deleting a load balancer does not affect the targets registered with the load balancer. For example, your EC2 instances continue to run after deleting the load balancer created in this guide.
To delete your load balancer
- Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
- In the navigation pane, under Load Balancing, choose Load Balancers.
- Select the checkbox for the load balancer, choose Actions, then choose Delete.
- When prompted for confirmation, choose Yes, Delete.
Conclusion
An Application Load Balancer supports HTTPS termination between the clients and the load balancer. Application Load Balancers also offer management of SSL certificates through AWS Identity and Access Management (IAM) and AWS Certificate Manager for pre-defined security policies. Cloud load balancing ensures distributing your site’s traffic to available servers effectively. It prevents downtime or machine breakdown issues while ensuring the applications are available to the client at all times.
Application Load balancer(ALB) – FAQ’s
Is the load balancer horizontally scalable?
Yes. The Application Load Balancer for VPC automatically adjusts its capacity based on the load. When horizontal scaling takes place, the number of IP addresses associated with the application load balancer’s DNS changes.
What are the default settings and allowed values for health check parameters?
Health check interval – Default is 5 seconds, and the range is 2 – 60 seconds.Health check response timeout – Default is 2 seconds, and the range is 1 – 59 seconds.Maximum retry attempts – Default is two retry attempts, and the range is 1-10 retries.
Are the ALB IP addresses fixed?
Application load balancer IP addresses are not guaranteed to be fixed. During system maintenance or horizontal scaling, you see changes in the available IPs associated with the FQDN of your load balancer.
Why does HTTPS listener creation or update tell me that my certificate is invalid?
Check for these possibilities:
- The provided certificate CRN might not be valid.
- The certificate instance in the Secrets Manager might not have an associated private key.
Why is my listener not receiving traffic?
Make sure that the security group rules that are attached to your load balancer allow incoming ingress and outgoing egress traffic on your listener’s port. Security groups attached to your load balancer can be found on your load balancer’s overview page. Locate the Attached security groups tab from the load balancer overview, then select the security groups that you want to view and modify their rules.
Share your thoughts in the comments
Please Login to comment...