Securing EC2 Instances With Security Groups And Key Pairs
Last Updated :
07 Mar, 2024
Amazon provides a service for website hosting and maintenance that is EC2, Elastic Cloud instance. They are the backbone of cloud-based applications, providing scalability and flexibility in computing resources. However, there are many challenges in protecting these instances from threats and attacks. Whenever we create an EC2 instance we need to take care of its security at the top level for which we have Security groups and key pairs to discard any unauthorized access to our instance.
Understanding Of Primary Terminologies
- EC2 Instances: These are the cloud platform services given by was to host data and run applications on the cloud. It’s a virtual server in the cloud that gives its users an expandable computing capacity. These instances can easily be configured and scaled based on user requirements and specifications.
- Security Group: A Security Group is a virtual firewall for an EC2 instance. It controls inbound and outbound traffic and sets the rules for the same. Each instance has its own Security group and works for its instance on the instance level.
- Key Pairs: A key pair is a security credential used for secure access to your EC2 instance. They have both public and private keys which are generated together. These pairs are primarily used for SSH access to Linux-based instances or RPD access to Windows-based instances.
Securing Instance With Security Groups And Key Pair: A Step-By-Step Guide
Go through the following steps to create a key pair launch your instance and create a security group as specified in the step below. You can also create the security group before launching the instance or you can do so during the launch of the instance.
Step 1: Login To the AWS Console
- Navigate to AWS Console and log in with your credentials from the root user.

Step 2: Navigate To EC2 Dashboard
- From the AWS console, Navigate to your EC2 instance service.
Step 3: Configuring Instance With Details
- configure your instance with following details and launch it using following steps:
- Click on launch instance button to start with configuring your instance.
- Name the instance as per your choice and requirement.

- Select a machine image for your instance. If you want to have free tier service go with available t2 micro free tier service in Amazon Machine image.
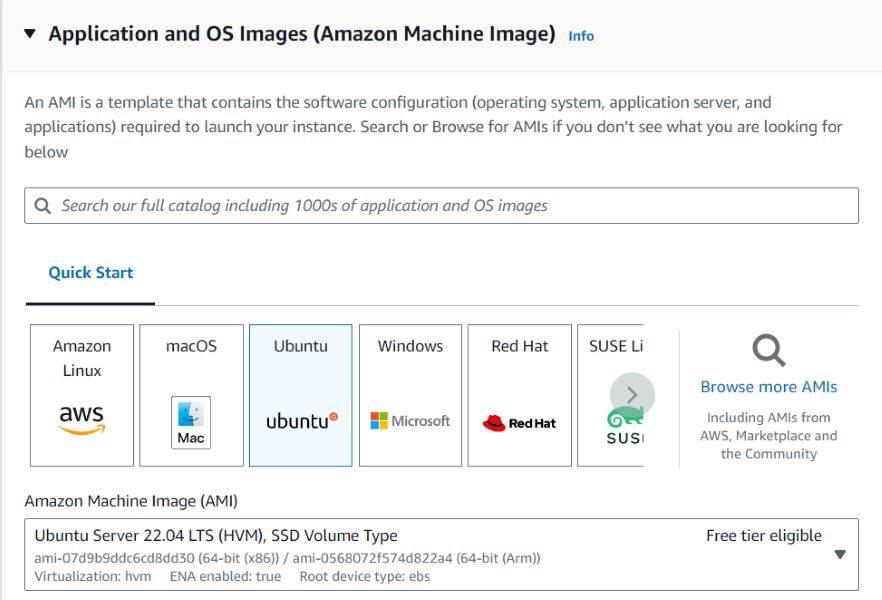
- From the launch instance window go to create key pair option and create a new key pair using following steps given in next step.
Step 4: Creating A AWS Key Pair
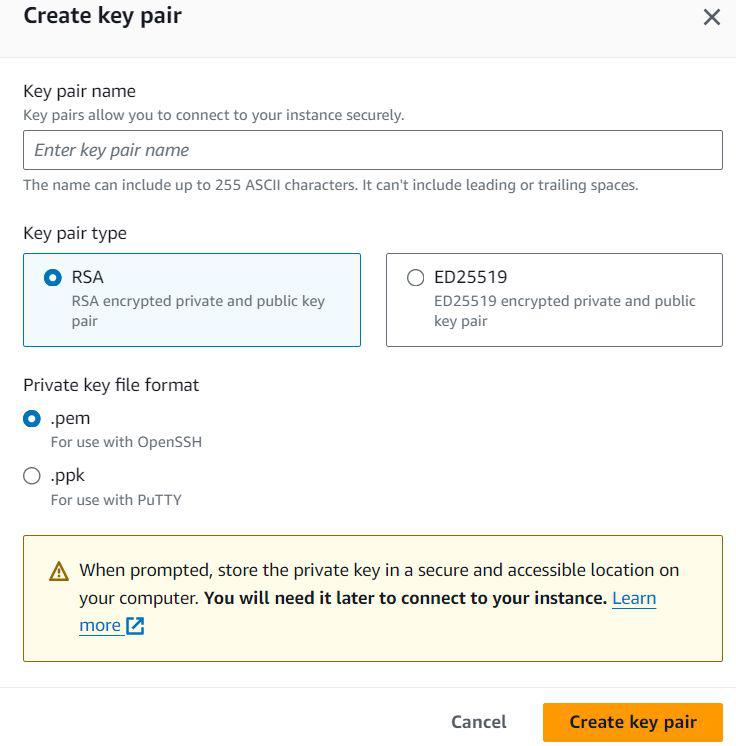
- Click on the create key pair option and yo will get a pop up window to create your Key pair.
- Select the name of your key pair as per your choice and select .pem if you will perform SSH login. After filling in the detail click on the create key pair button.
- After creating your key pair click on the launch instance and wait for some tile till your instance gets into running state.
Step 5: Configuring Network Security Groups
- After your instance gets launched go for security group creation and set inbound and outbound rule for it.
- Click on the create security group option and fill in the required details about the security group.
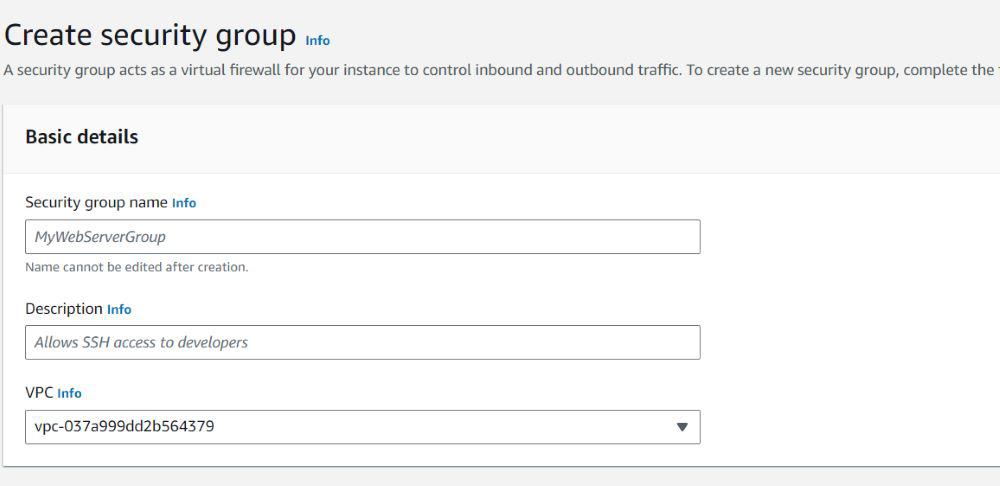
- Setup the inbound and outbound rules for your security group.

- After setting up rules for your security group click on the create Security group option.
Step 6: Connect To EC2 Instance With SSH Connection
- After creating our security group we need to associate our security group with your launched instance.
- To select your Security group select your instance, go to action button.In action button click on the security option and select change security group.
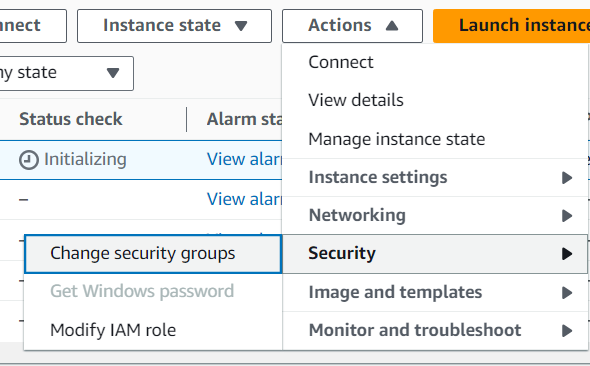
- Select the Security group that we created in previous step and associate it with your instance.
Step 7: Login Remotely From Local System
- Use SSH login method to connect to your EC2 instance. Use the private key of the key-pair that we get while we created our KEY-PAIR.
- Specify the public address in your console during SSH connnection. Use the following code formate to do so:
ssh -i path/to/private-key.pem ec2-user@public-ip
Note: Here change the key file name and ip address with your values.
Conclusion
Securing your EC2 instance using key-pair and Security Groups is the fundamental step in securing your instance from unauthorused access and maintaining its integrity and confidentiality. Secure your cloud-based infrastructure in EC2 and secure your data and webpage hosted.By following above steps you can understand the concept of Security group and key pair and create one for your instance. Remeber not to share your private or public key of key-pair and if so happens delete the key pair and security group to avoid extra billing on your account.
EC2 Instance Security Groups And Key Pairs – FAQ’s
How Do I Secure My EC2 Instance Using Security Groups?
Security groups are a virtual firewall for our EC2 instances. To get your EC2 instance secure using security group you can create and configure a security group to control inbound and outbound traffic. Define rules based on your requirements allowing only important ports to access your instance.
How Can I Enhance EC2 Instance Security Using Key Pairs?
Key pair gives us a secure way to connect to our EC2 instance. When we launch an instance we specify a key pair , and the private key given in the key pair is used to connect secure SSH to the launched instance. Be cautious, never share your private key and ensure its safety.
Can I Modify Security Group Rules After An EC2 instance Is Launched?
Yes, you can modify security group rules even after the instance I launched. You can modify the inbound and outbound rules as per the changing requirement and ports. Keep updating your security group configuration to maintain security of your instance.
What Are Some Best Practices For Configuring Security Group Rules?
Only open ports for inbound that are necessary for your application to function. Similarly, restrict the outbound traffic to essential protocols and ports.Instead of allowing traffic from all the ports, limit access to specific IP ranges or addresses to add an extra layer of security to your instance.
What Should I Do If I Accidentally Lock Myself Out Of My EC2 Instance Due To Security Group Changes?
If you restric access to your instance, you can again access it by modifying the security group rules. You can do this security edit through AWS Managment console, if you have an Elastic IP associated with your instance you can disassociate and associate it again to regain access.Always ensure you have created a backup plan and access method to recover from such situation.
Share your thoughts in the comments
Please Login to comment...