Private Browsing
Last Updated :
03 Nov, 2021
Private Browsing Overview:
As day by day, the use of internet browsing has been increasing, people are getting aware of their privacy and protecting personal information. No one wants to disclose what sites they are browsing and the local data associated with it, which can be used to retrieve personal sensitive information.
For example, if on a computer system, a user is accessing a bank site, it is obvious that he would not want any other user to know his credentials which are stored by the web browser by default (allow by asking). For protecting the history of the websites the user has visited and the local data associated with it, we use private browsing.
How the cache is maintained?
Whenever a user visits a website the first time, the browser creates a temporary file called cache. It is maintained for speeding up browsing so whenever the user revisits that site again, that page will be loaded from its cache copy rather than downloaded again from the internet. But if you are using a public system then it can give some personal sensitive information to another user as it can store sensitive information such as passwords, therefore, the cache should be cleared in order to maintain privacy. Basically, Private Browsing hides the browsing history of the user from another user who is accessing the same machine.
Private Browsing:
Private Browsing is a concept of disabling the browser’s history, removing cookies, and not storing the web cache. The browser will not store browsing information (of the session) such as credentials of the user or the sites visited or the data you enter into forms if private browsing is enabled. Private Browsing doesn’t make you anonymous as your Internet Service Provider (ISP) will still be able to track you. Also, it is a common myth that it will protect users from keyloggers or spyware, but it will not.
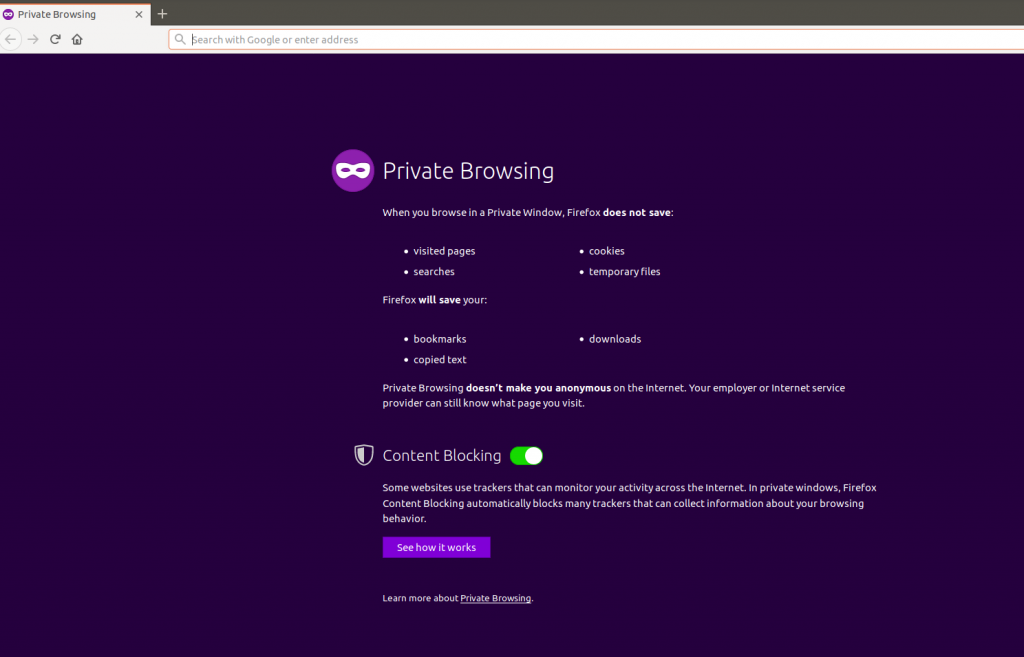
The local data associated with a visited website that can be blocked by private browsing are:
- Browsing history –
It is a list of URLs recently visited by the user.
- Cache –
A temporary file that can consist of multimedia files or full web pages. It is used to speed up internet browsing. No cache is saved when private browsing is enabled.
- Cookies –
These are used by websites to maintain user-specific settings, information such as credentials, and also for tracking. It can also be used to track users across different websites by third parties. These are held temporarily in memory and discarded at the end of the session when private browsing is enabled.
- Passwords –
The credentials associated with a particular website will not be saved by private browsing.
Note – Bookmarks saved and downloaded files will not be discarded at the end of a private browsing session (only if saved in a private browsing session). But recent researches have shown that it isn’t able to fully protect users’ data even when the private browsing mode is enabled. The researchers were able to find enough information about the web pages visited when private browsing is enabled.
How private browsing is not fully private?
There is some research that shows that there are enough left traces even after the private browsing mode is enabled. When a user wants to access a website and only knows the name of the website then a protocol is run, called Domain Name Service (DNS). The domain name is translated into a 32-bit IP address which is further used by networking devices to carry forward the domain name request and reply.
A special table called DNS cache is maintained for the purpose by the machine, in which a domain name with its corresponding translated IP address is maintained. If a technical user got access to your machine, he can exploit this information to a great extent and can find out what sites have been visited.
Another vulnerability is that the operating system of a machine could write information to your hard drive while using private mode. This can contain images or certain HTML code linked to a website. In both these scenarios, the web browser itself will not delete this information as it doesn’t have the authority to access these parts of the operating system.
Dubbed Veil:
To resolve these issues with the current system, MIT researchers developed a technology called dubbed veil. It was proposed to enhance the privacy of the users on public machines. The process involved in the proposed project is as follows:
Veil delivers a web page to the machine through a “blinding-server”. Whenever a user types a URL, the associated page will get retrieved from blinding servers. Blinding-server is a proxy that will retrieve the requested web page and encrypt it before transmitting it to the browser. Also, a special garbage code will be injected into the page by which the page will look similar to the user but the HTML code will be modified. By this, the source code and the website’s associated browsing history can be hidden.
Support of private browsing in different browsers:
- Google Chrome –
If a user doesn’t want Google Chrome to remember the activities like website searches etc, then Google chrome allows an option called incognito mode for private browsing. By enabling this mode, it will not store site cookies, browsing history, etc but files downloaded or bookmarks will be stored. The user has to manually delete these.
- Safari:
The same goes with safari. All temporary files, browsing history, form data, etc will be wiped out in safari private browsing mode.
- Opera:
Opera provides an extra level of secrecy as it provides an option of VPN (called Opera VPN, a proxy service) which will encrypt all the traffic operated by browser but notedly only for the traffic of opera. All the traffic is directed through the VPN provider SurfEasy.
- Mozilla Firefox:
In addition to erasing browsing history, cookies, etc, Firefox has an additional feature called content blocking. It prevents trackers from collecting users’ data.
- Internet Explorer and Edge:
The same implies to Microsoft’s browser Internet Explorer. It doesn’t store temporary files like cookies. In addition, it also disables third-party toolbar while in a private session.
Share your thoughts in the comments
Please Login to comment...