Keycloak – User Validation and Generating Access Tokens
Last Updated :
18 Aug, 2023
Keycloak is Open Source Identity and Access Management (IAM) solution developed by Red Hat. By using this, you can add authentication to applications and secure services with minimum effort. No need to deal with storing users or authenticating users. Keycloak provides user federation, strong authentication, user management, fine-grained authorization, and more. In Keycloak, user validation refers to the process of verifying the identity and credentials of a user before granting access to secured resources. When a user attempts to authenticate with Keycloak, the server performs various validation checks to ensure the user’s identity and credentials are valid. Before following this article you must refer to these two articles
Step By Step Guide
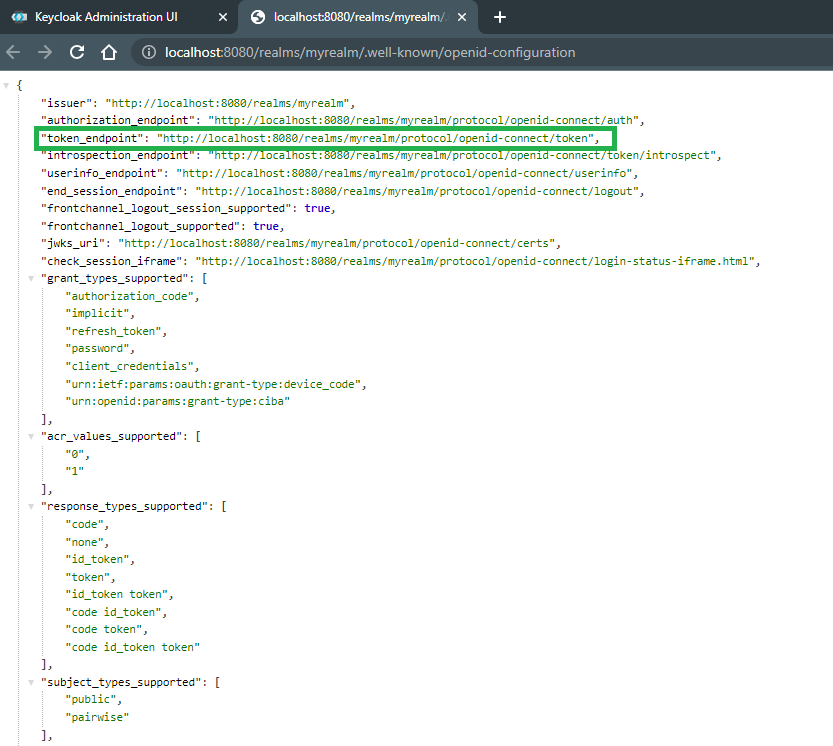
Step 1: Go to the Realm settings and click on the OpenID Endpoint Configuration to see the available endpoints. Refer to the below image.

Step 2: Now you have to send a post request to this token endpoint to get a token. You can use one of the users you have already created as credentials.
Step 3: Now go to the Postman and import the following curl.
curl --location 'http://localhost:8080/realms/myrealm/protocol/openid-connect/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=password' \
--data-urlencode 'client_id=spring-with-keycloak' \
--data-urlencode 'username=user1' \
--data-urlencode 'password=12345'
You can test it using Postman. The response would look like the one below.
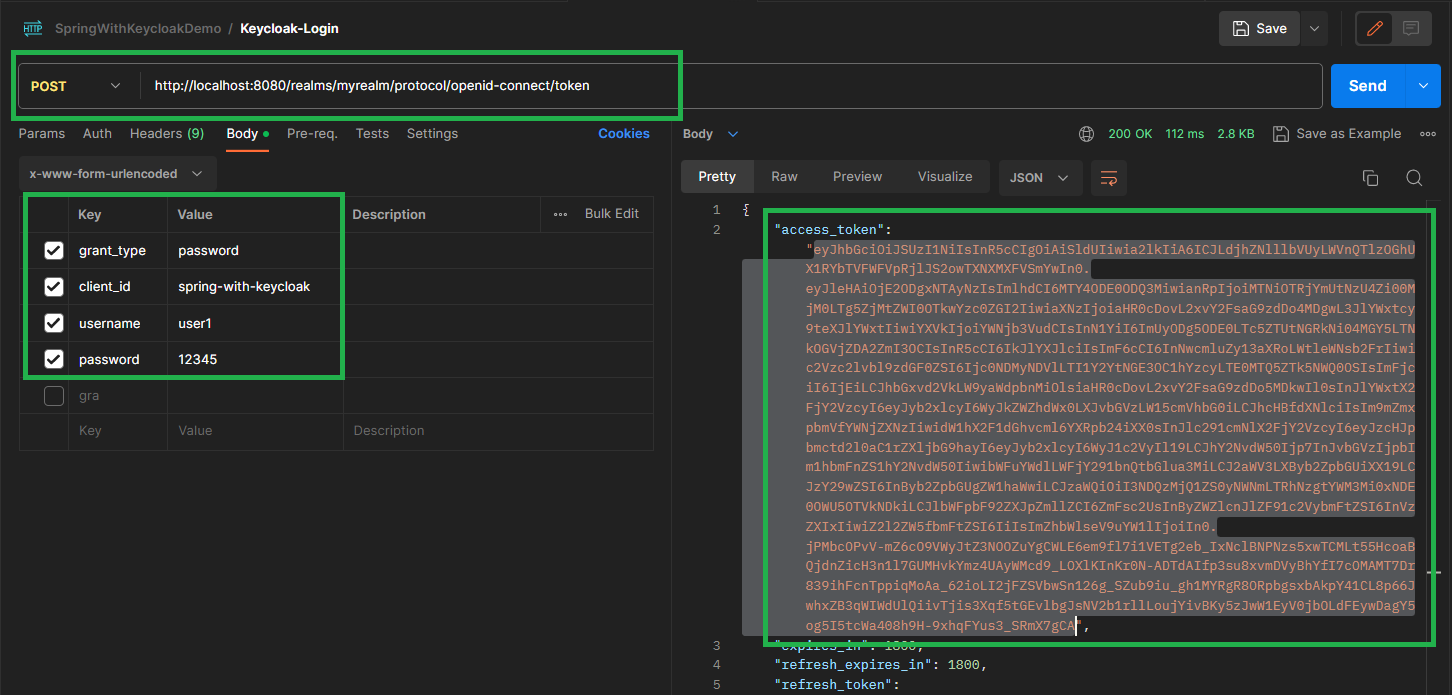
If you put bad credentials then you are going to get the 401 Unauthorized error like this.

Now you can copy that access_token and decode it using the jwt.io website to see the information inside that. Refer to the below image.

Share your thoughts in the comments
Please Login to comment...