Juumla – Tool Designed To Identify And Scan For Version, Config Files In The CMS Joomla
Last Updated :
23 Sep, 2021
Juumla is an open-source content management system(CMS). It assists you to build powerful dynamic websites and applications. It has an automatic interface that helps you use its features and functionality to the whole. Juumla tool is an automated tool developed in the Python language which is used to identify the Joomla CMS Version running on the target domain. Juumla tool also scans the domains for vulnerabilities that can be present on the target domain server. Juumla tool also searches some config files on the domain which can have sensitive data. Juumla tool is available on the GitHub platform, it’s open-source and free-to-use. Juumla tool performs fast scanning on the target and used LOW CPU and RAM resources.
Note: Make Sure You have Python Installed on your System, as this is a python-based tool. Click to check the Installation process – Python Installation Steps on Linux
Installation of Juumla Tool on Kali Linux OS
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/knightm4re/juumla.git
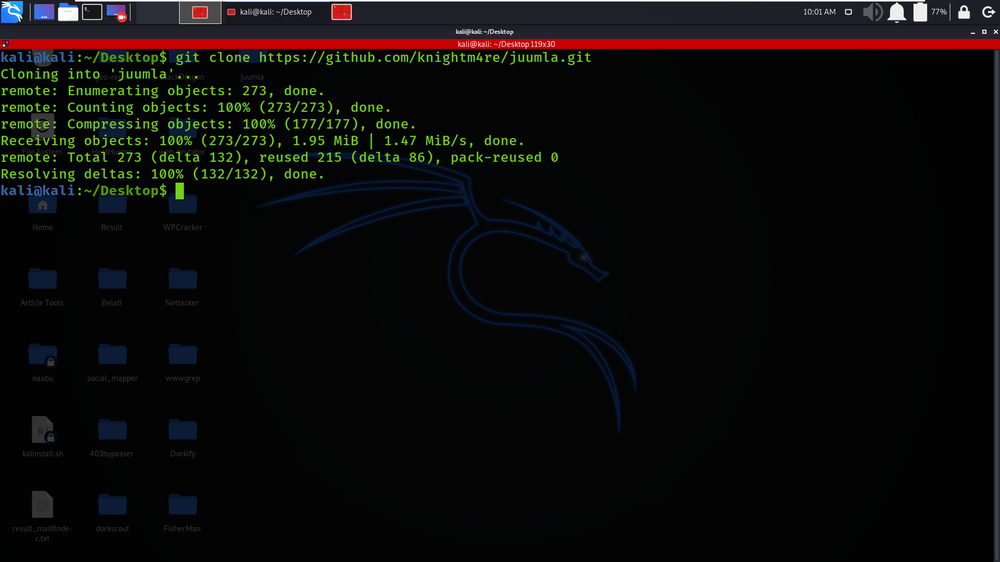
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd juumla
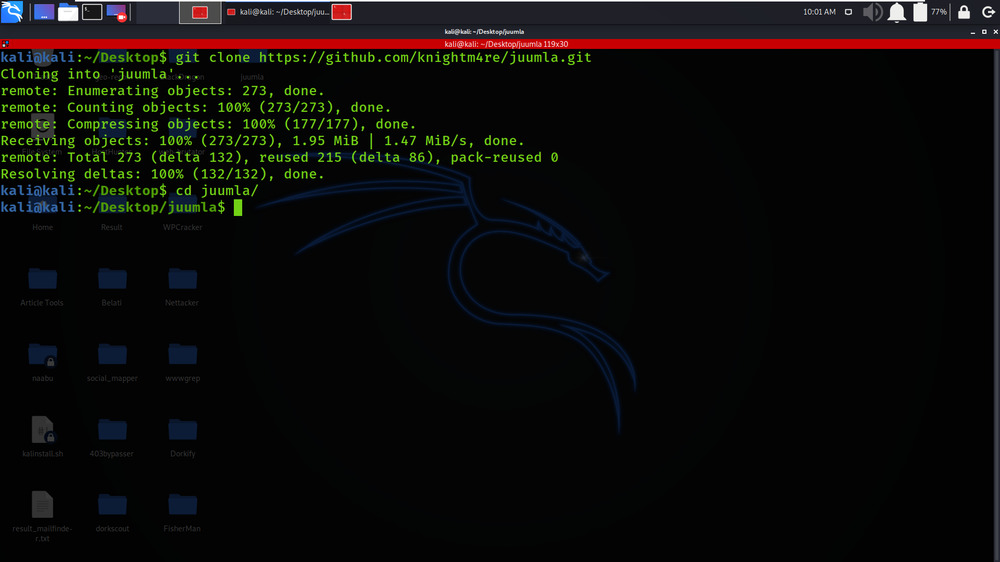
Step 3: You are in the directory of the Juumla. Now you have to install a dependency of the Juumla using the following command.
sudo pip3 install -r requirements.txt
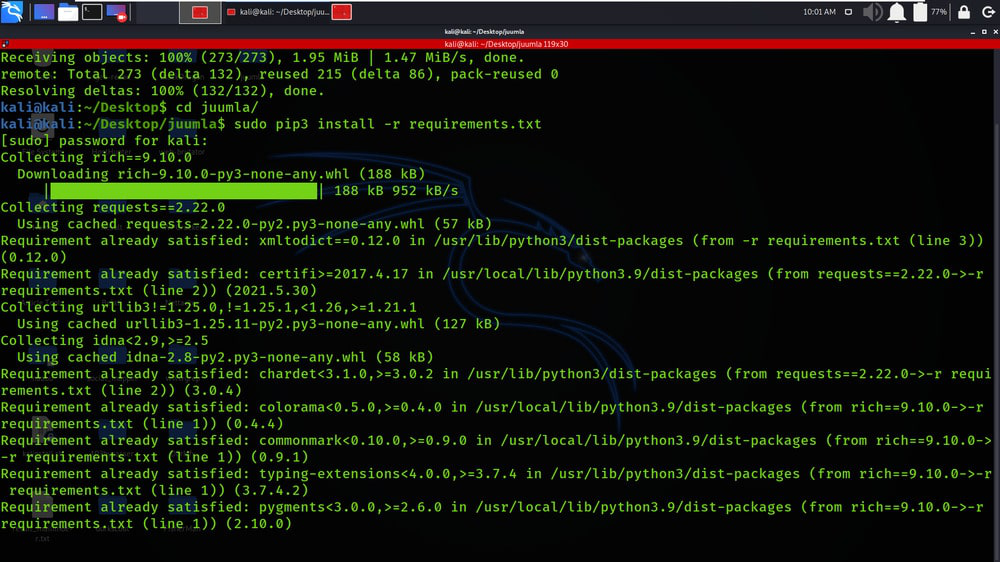
Step 4: All the dependencies have been installed in your Kali Linux operating system. Now use the following command to run the tool and check the help section.
python3 main.py -h
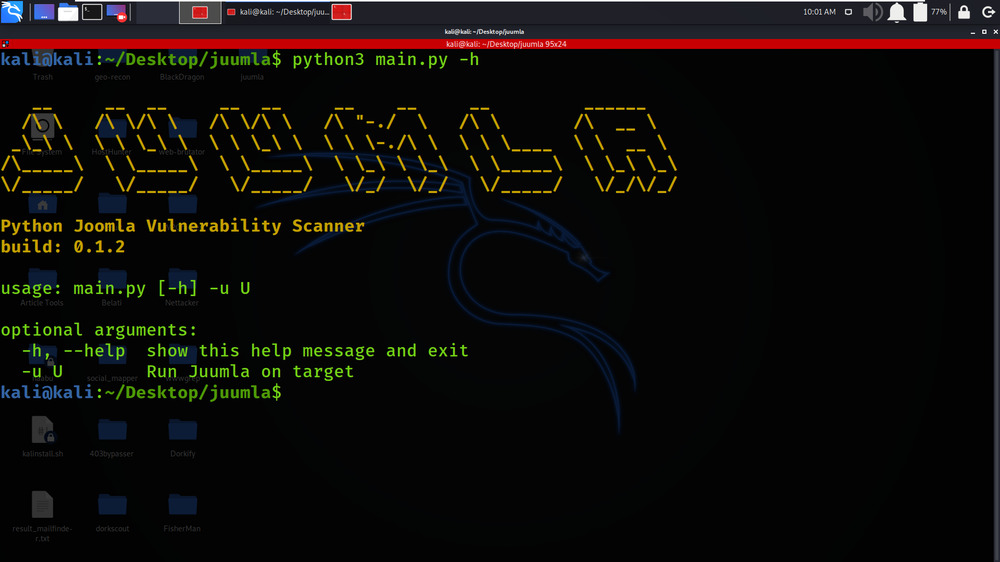
Working with Juumla Tool on Kali Linux OS
Example: Run Juumla on target
python3 main.py -u https://vdc.epson.com/
Juumla tool has detected the CMS of the target domain.
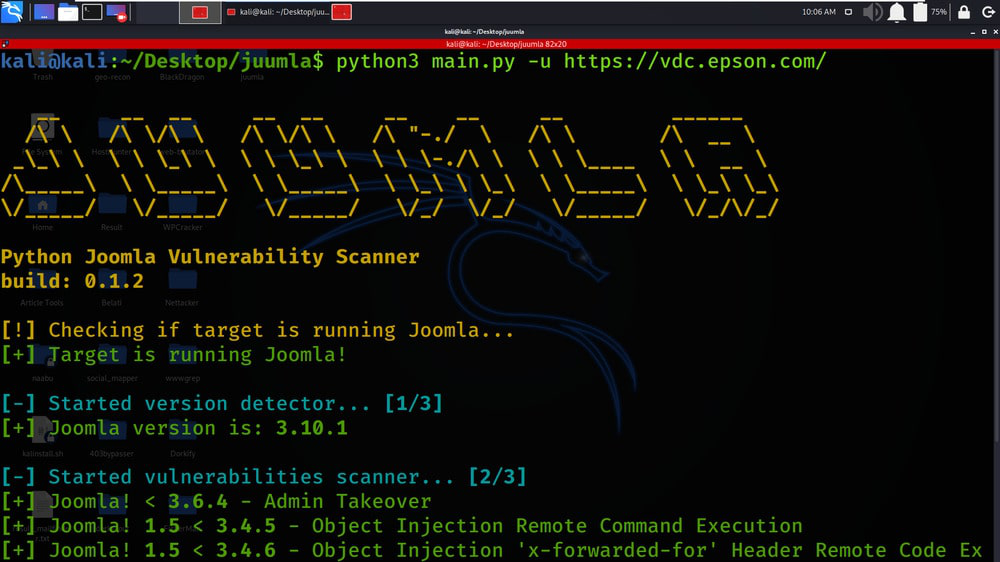
Joomla Version of the target domain is displayed in the below screenshot.
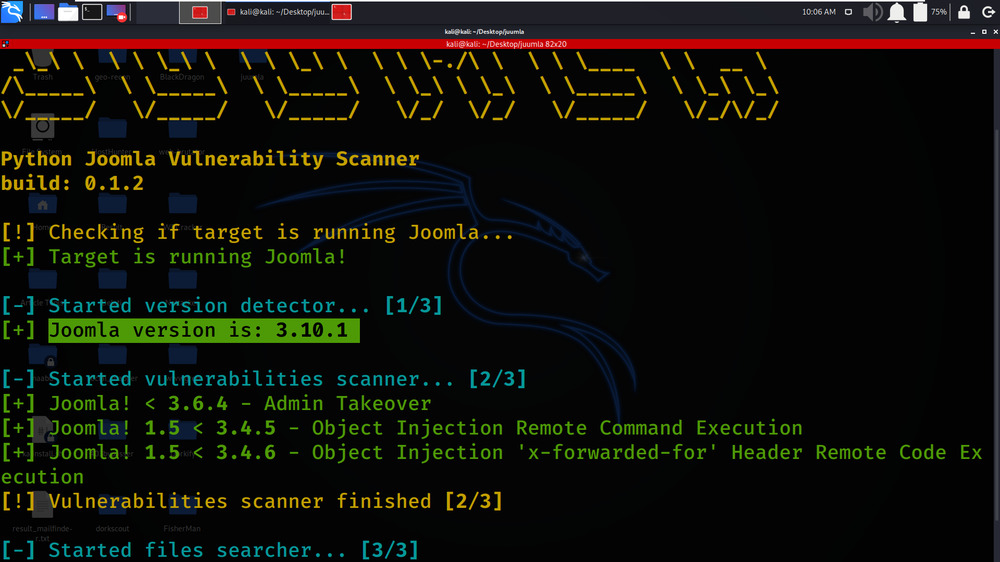
Juumla tool has identified some vulnerabilities in the target domain.
Share your thoughts in the comments
Please Login to comment...