Kxss – Tool to to Identify XSS Vulnerable Parameters / Patterns
Last Updated :
25 Sep, 2023
Cross-site scripting is a common vulnerability and bug, which is the trending vulnerability identified in most web-based applications. The attacker injects some malicious popup javascript code in input parameters or sometimes through file uploads. So periodically, website designers or developers validate the input fields by encoding and validating the provided input by the user. So Kxss tool comes into focus for this identification. Kxss tool is a Golang language-based tool that finds the vulnerable parameters and patterns in the target domain URL. So if you get a positive result, you can make your XSS payload or use a strong XSS payload wordlist to hit and try XSS vulnerability on the target domain.
Installation of Kxss Tool in Kali Linux
For installing the Kxss tool in Kali Linux, we have 2 different methods. Below we have added the list of these installation methods:
- Method 1: Installing Using Go Get
- Method 2: Installing Using wget
So, let’s see both the installation methods in Kali Linux with proper step-by-step manner and command execution.
Method 1: Installing Using Go Get
In this method, we will install the Kxss tool using Go Get. For this installation, we need the Golang Language installed and configured on our system. To set up the Golang environment click here.
Step 1: If you have downloaded Golang in your system, verify the installation by checking the version of Golang, using the following command.
go version
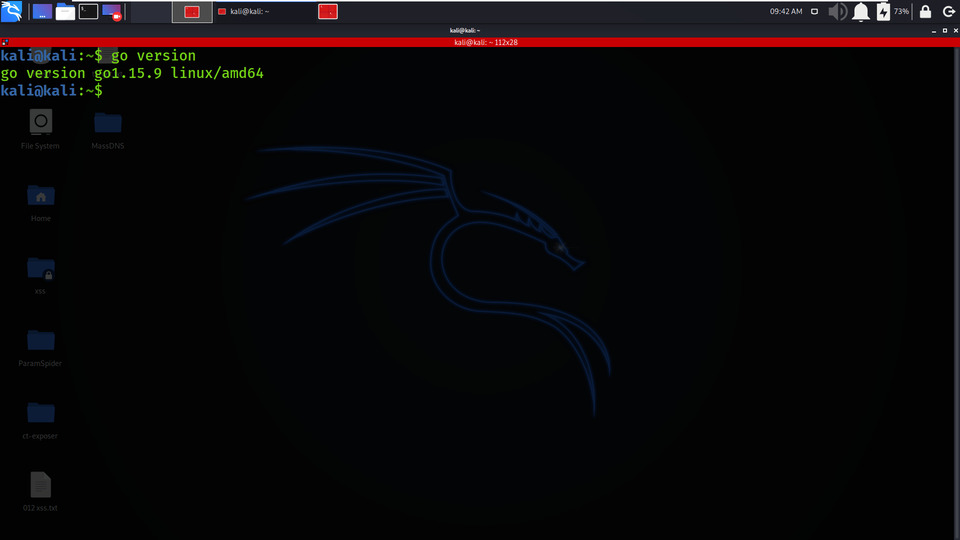
Checking Go Version
Step 2: Get the Kxss repository or clone the Kxss tool from Github, use the following command.
sudo go get github.com/Emoe/kxss

Cloning KXss tool from GitHub
Step 3: Copy the Kxss tool in the bin directory so we can easily use the tool without running the tool manually by Golang, use the following command.
sudo cp /root/go/bin/kxss /usr/local/go/bin/
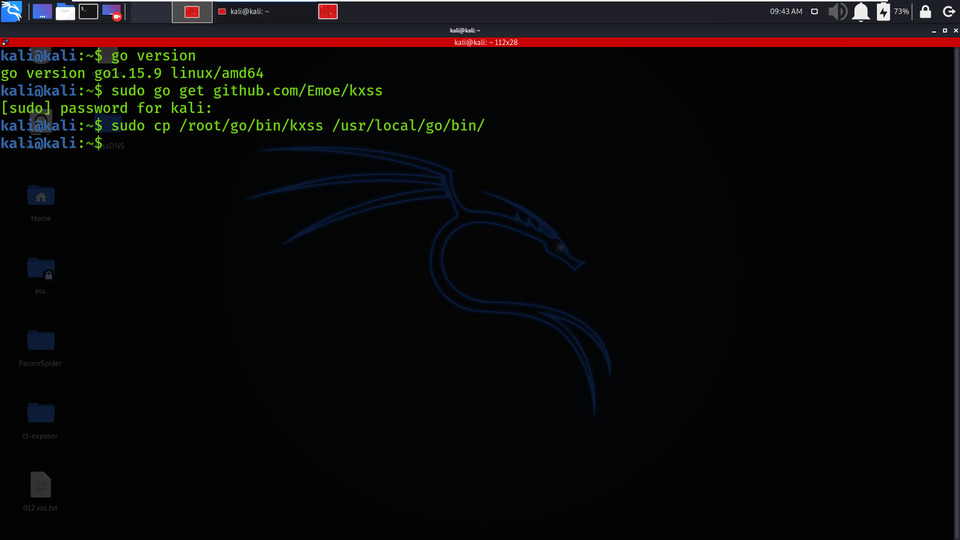
Copying tool to the bin directory
Method 2: Installing Using wget
In this method, we are using the wget command to get the package of the KXss tool in Kali Linux. Follow the below steps to install the tool in Kali Linux using the wget command.
Step 1: If you have downloaded Golang in your system, verify the installation by checking the version of Golang, using the following command.
sudo go version

Checking Go version
Step 2: Download the .zip file of the Kxss tool from Github, and use the following command.
sudo wget https://github.com/tomnomnom/hacks/archive/refs/heads/master.zip

Getting Kxss tool package
Step 3: Unzip the downloaded .zip file, use the following command
sudo unzip master.zip

Unzipping the zip file
Step 4: A New Directory will be created named “hacks-master/kxss/ ” move in that directory using the following command.
cd hacks-master/kxss/

Navigating to the tool directory
Step 5: Migrate to Go Modules using the below command:
sudo go env -w GO111MODULE=auto

Migrating Go Modules
Step 6: Now we need to Build the Tool by executing the following command.
sudo go build
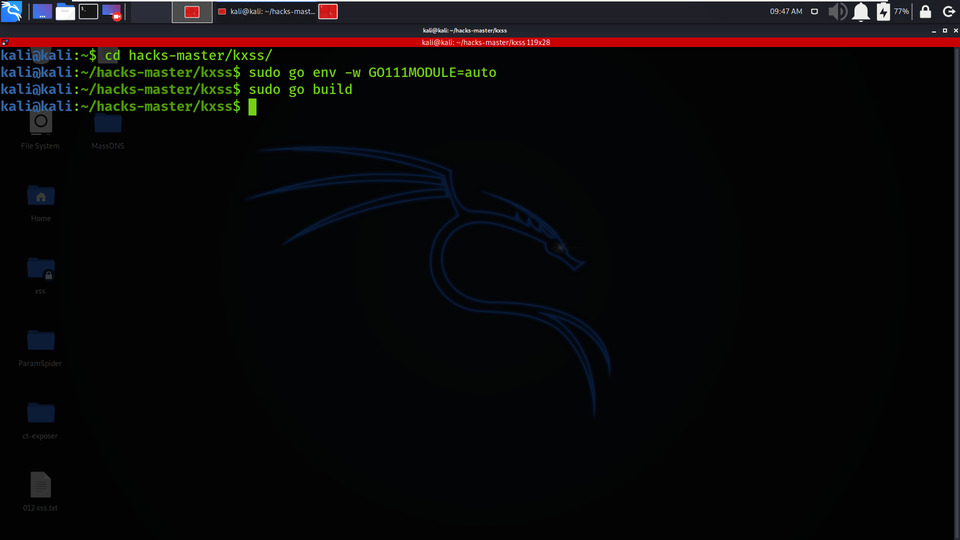
Building the Tool
Step 7: Copy the Kxss tool in the bin directory so we can easily use the tool without running the tool manually by Golang, use the following command.
sudo cp /root/go/bin/kxss /usr/local/go/bin/

Copying Tool to the bin directory
Usage of Kxss Tool in Kali Linux
In this section, we will see the practical usage of the Kxss tool on testing websites.
Example 1: Target – “http://testasp.vulnweb.com/Search.asp?tfSearch=ok”
Execute the below command in the terminal. This will find the unfiltered parameters on the target website and turn the results on the terminal itself.
echo "http://testasp.vulnweb.com/Search.asp?tfSearch=ok" | kxss
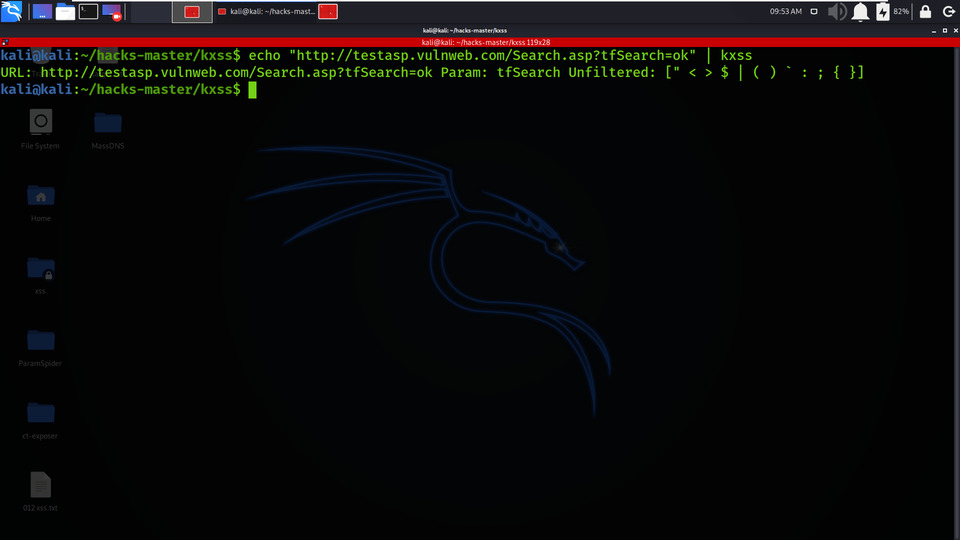
Testing target 1 application
Now we can pass the malicious payload in the parameter and paste the URL into the browser. In the below screenshot, you can see that we have executed the malicious payload by inserting the script in the parameter as it was unfiltered.
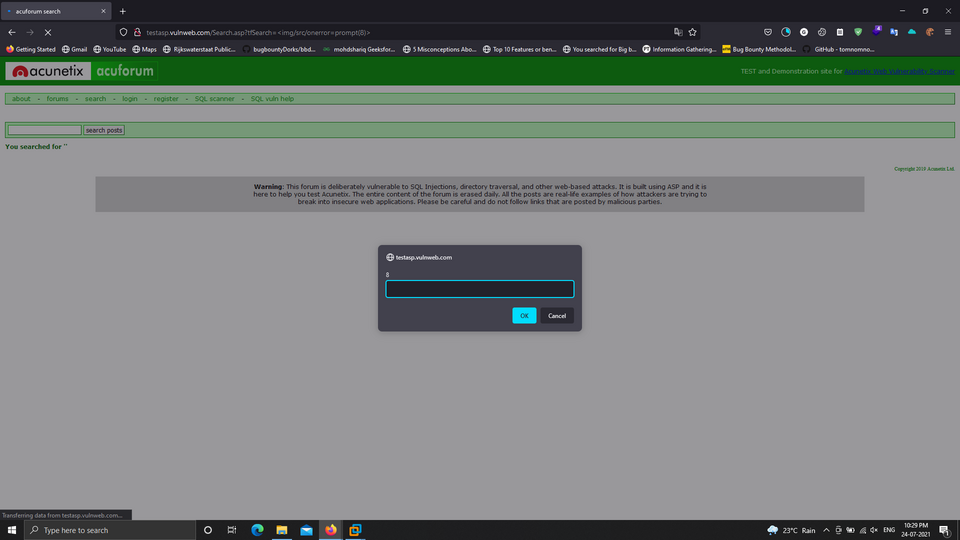
Payload Executed on Target 1
Example 2: Target – “http://www.xss-game.appspot.com/level1/frame?query=hello”
In this example, we will test one more target-testing web application. We are running the Kxss tool against the target application to find the unfiltered parameters, Through this we can inject the malicious code and get access to the web application.
echo "http://www.xss-game.appspot.com/level1/frame?query=hello" | kxss

Testing target 2 application
As we have got the unfiltered parameters list, we have created a script and pasted it in the URL. When we hit the website, the script got executed and the XSS payload got triggered.

Payload Executed on Target 2
Conclusion
In conclusion, testing the web application is an important process to prevent the software and application bugs at the early stage of the deployment. Using the automated testing tools to find the security bugs can be helpful to make the application more potentially strong against hackers. As XSS is one of the powerful attack that can impact the data of the application, to prevent this bug we can use Kxss tool and perform the XSS Testing on the web application for minimizing the rrisk of data or security theft.
Share your thoughts in the comments
Please Login to comment...