Amazon ECR is known as the “Amazon Elastic Container Registry”. It is an AWS-managed container image registry service that is secure, scalable, and reliable. With the help of Amazon ECR, developers can create private repositories within their AWS account and control their access using AWS Identity and Access Management (IAM) policies. It allows only authorized users or Amazon EC2 instances to push, pull, or manage your container images.
It also allows multiple features to manage our container images effectively. The lifecycle policies allow users to automatically clean up unused images, while image scanning helps identify software vulnerabilities in your container images. Its cross-region and cross-account replication enables users to replicate the images across multiple AWS regions and accounts for better availability and performance. Amazon ECR provides a secure and reliable solution for managing the user’s containerized applications, making it easier to build, ship, and run the applications using containers.
What are Image Security and Vulnerabilities in ECR?
Image Security and Vulnerabilities in the Amazon Elastic Container Registry (ECR) refer to the security risks and weaknesses that can occur with the container images stored and managed in the ECR. Developers can use the Amazon ECR private repositories to host the container images and artifacts that Amazon ECS tasks may pull from.
Following are some features of image security and vulnerabilities in ECR:
- The developer might find security holes, which means the Docker images may contain security vulnerabilities in their software, like outdated libraries, packages, or operating system dependencies. These vulnerabilities are used by hackers to access and compromise the container environment.
- ECR integrates image scanning with Amazon Inspector. It is a service that automatically scans container images for known software vulnerabilities. ECR can be configured to scan images during the upload process or on a scheduled basis and report any identified vulnerabilities or security findings.
- The Docker Content Trust is used in ECR for image signing and verification. This ensures the integrity and authenticity of images by verifying them from a trusted source.
- It provides granular access control mechanisms with the help of AWS Identity and Access Management (IAM) policies. This allows users to control who can upload, download, or manage container images in your ECR repositories, which reduces the risk of unwanted access and activities.
- This supports a private registry where container images are isolated from public registries and only accessible within the developer’s AWS account or authorized person.
- Once the images are uploaded to ECR, the container images are immutable and cannot be overwritten or modified directly. Any changes will only occur when the user creates a new image version.
- It supports server-side encryption, which protects the stored container images from unauthorized access or data breaches.
- The ECR provides Vulnerability Management Which means that the vulnerabilities are identified in container images that are configured, and then they automatically expire or remove affected images based on specified rules or schedules.
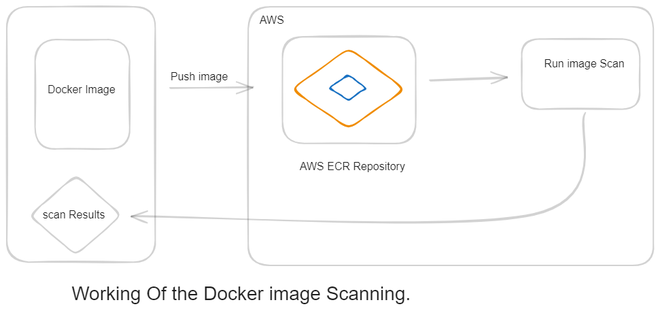
Working of the Image security & Vulnerabilities
What is the principle of least privilege and the implementation of the principle?
The principle of least privilege is a fundamental concept in computer security that suggests that users, programs, or processes should only be given the minimum level of access or permissions necessary to perform their tasks. This principle aims to reduce the potential damage that could result from accidental or malicious actions by limiting the capabilities of entities within a system.
The principle of least privilege for image security and vulnerabilities in ECR (Elastic Container Registry) can be implemented by the following:
- Access Control: Deny viewing, uploading and managing ECR container images to either limit or permit the groups as a rule. The crucial aspect is to pass the right through access to upload new images to authorized developers while others can access them on the readonly basis only. Policies of IAM (Identity and Access Management) or resource-based policies may be used to grant authorization according to roles and responsibilities.
- Container Image Scanning: Security scanning for container images will be done for vulnerability and security risk checking purposes before deploying them. But, limitations of the scanning system and presentation of only the facts by authorized people only may prevent the dissemination of unapproved information.
- Isolation: By running containers isolated in production will ensure that program lags will not occur in other containers. Employ Kubernetes or something else like that to run these containers in different namespaces or on separate nodes. The hazard therefore, is controlled by the fact that, if one container is contaminated, it has no effect on other containers.
- Immutable Infrastructure: When an image of a container has been created and distributed, don’t be make any changes to it directly. Actually imagine and create a new image, and then use it to replace the old one with it. By this means an outsider can never perform unauthorized changes and have containers run with minimal privileges in mind.
- Audit Logging: Maintain the detailed log of all access requests ECR, watch for any inconsistent or unauthorized events People are positive about AI’s impact on the workforce in the long run, but it raises ethical concerns regarding job loss and an unequal distribution of wealth. Log actions like images relies, dispatches and access attempts. This detects any security gaps and bring to the fore any permission policy that ought to be reviewed.
The developers can use the above methods by executing these activities while keeping confidential the container images of ECR restricts openings to security gaps and unapproved access with the least privilege principle.
How to enable image scanning using Amazon ECR Console?
Step 1: Sign in to the AWS Management Console and open the Amazon ECR console.
.jpg)
Step 2: Choose or create the repository for which you want to enable image scanning. Select the “Image scan settings” tab.
.jpg)
Choose or create the repository for which you want to enable image scanning
Step 3: Click on “Edit” and Check the box labeled “Enable image scanning”. Optionally, you can choose whether to send scan findings to an Amazon SNS topic. If you do, specify the ARN of the SNS topic.
.jpg)
Click on “Edit” and Check the box labeled “Enable image scanning”
Step 4: (Optional) You might have to face the Deprecation warning while enabling the image scanning setting in aws. This indicates that a particular feature or setting related to image scanning is being phased out or replaced. Image scanning in AWS refers to analyzing container images for vulnerabilities or compliance issues before deployment. To resolve this, review your AWS documentation, identify the new recommended image scanning settings or features, and migrate to the updated approach to avoid service disruptions.
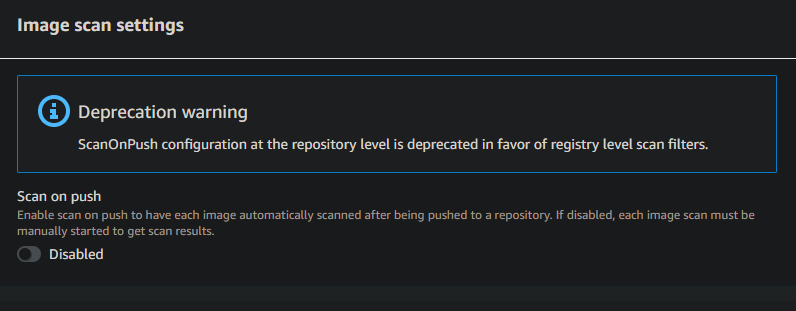
Deprecation warning while enabling the image scanning setting
Step 5: Click on “Save”.
How To Manage Image Security and Vulnerabilities in ECR?
In the following steps, We will find Image Security and Vulnerabilities in ECR using the Docker. In this, below codes can be used as the architecture of the Docker. The architecture codes needs inputs with the codes which are private credentials of the user and to know more, user must need to follow the AWS ECR instructions:
Step1: Open your AWS, sign into your account and search for the ECR.
-660.jpg)
Search for the ECR and open it.
Step2: Go to the Container and search for the images vulnerabilities section and check out the situation.
.jpg)
Go to the Container and search for the images vulnerabilities section
Step 3: Open your Docker and check out the container image carrying out the vulnerabilities and copy and paste the image into the docker.
.jpg)
check out the container image carrying out the vulnerabilities and copy and paste the image into the docker.
Step 4: Access the repository using your account id and copy the images details and paste it.
docker run –rm -v /var/run/docker.sock:/var/run/docker.sock aquasec/trivy <image_name>:<tag>
docker tag <local_image_id> <ecr_repository_uri>:<tag>
.jpg)
Access the repository using your account id
Step 5: Scan the Images Locally into the Docker with the help of following command. Remember to paste the image docker copied in the previous pages.
aws ecr get-login-password –region <region> | docker login –username AWS –password-stdin <account_id>.dkr.ecr.<region>.amazonaws.com
.jpg)
Scan the Images Locally into the Docker
Step 6: Go to the container services and copy your image tag and account id to paste it into docker into the command.
.jpg)
Step 7: Use the tag into the docker to find out the vulnerabilities into your docker.
docker push <ecr_repository_uri>:<tag>
aws ecr put-image-scanning-configuration –repository-name <repository_name> –image-scanning-configuration scanOnPush=true
aws ecr describe-image-scan-findings –repository-name <repository_name> –image-id imageTag=<tag>
.jpg)
Use the tag into the docker to find out the vulnerabilities
Step 8: Now you can visit the container image and check out the vulnerabilities.
.jpg)
Visit the container image and check out the vulnerabilities.
Advantages of Image Security and Vulnerabilities in ECR
- It provides Data Integrity which ensures that container images remain unchanged and undisturbed throughout their lifecycle. This prevents unauthorized access to the images and maintains data privacy as well as reduce the risk of deploying compromised containers.
- It offers Access Control which control the mechanisms, and allows administrators to define granular permissions for accessing and modifying container images. This prevent the risk of data breaches.
- The ECR provides encryption to both at rest and in transit, which ensures that container images are securely stored and transmitted between the registry and the Docker hosts. It adds an extra layer of security by protecting sensitive data from the unauthorized access and interception.
- It provides Vulnerability Scanning tools which automatically identify security vulnerabilities within container images. It helps to detect vulnerabilities before deploying containers into production which reduces the risk of exploitation by attackers.
- ECR promotes Immutable Infrastructure which enhances security by ensuring that containers are deployed consistently and reliably, without introducing unexpected changes or vulnerabilities.
- It provides comprehensive auditing and logging capabilities which allows the administrators to monitor user activities, track image access, and investigate security incidents.
- This offers image signing and verification capabilities which allows users to confirm the authenticity and completeness of container images before deploying them. The image signing helps to prevent tampering and ensures that only trusted, unmodified images are utilized in production environments. It adds an extra layer of security by verifying the image’s integrity and provenance, mitigating risks associated with compromised or untrusted container images.
- It also manages security patches for the container images which enables the administrators to quickly update and replace vulnerable container images with correct versions. This capability helps organizations stay alert against any upcoming security threats and maintains a secured container environment.
Disadvantages of Image Security and Vulnerabilities in ECR
- It has a very tricky setup so it’s challenging for the developer to configure all the security settings correctly. It can be a real headache, especially if user is new to the container security because one wrong move can end up all the defense system.
- Their is lack of insight which means it isn’t always giving a clear view of what’s happening with the container images. This makes it hard to spot and deal with security threats in quick time.
- It always needs the outside help to check for vulnerabilities in your container images and ECR lies on the third-party scanning tools. This makes it more complex and makes it depending on someone else’s database for being up-to-date.
- It is based on pay-as-you-go model which sounds good and favorable but the reality is that storing and managing a ton of container images can be really expensive over time. So, Users needs to stay on top of the repositories to avoid unnecessary costs while still keeping things secure.
- It is vulnerable when it comes to network-based attacks because without proper encryption and network security measures, the sensitive data inside the container images could get leaked.
Conclusion
The use of Amazon ECR provides us private repositories within their AWS account and control its access using AWS Identity and Access Management (IAM) policies. It allows only authorized users or Amazon EC2 instances can push, pull, or manage your the container images. But there are some things to think about. It is based on pay-as-you-go model which sounds good and favorable but the reality is that storing and managing a ton of container images can be really expensive over time. So, Users needs to stay on top of the repositories to avoid unnecessary costs while still keeping things secure. Also it is vulnerable when it comes to network-based attacks and their is lack of insight which means it isn’t always giving a clear view of what’s happening with the container images
However, we also can’t ignore that it provides comprehensive auditing and logging capabilities which allows the administrators to monitor user activities, track image access, and investigate security incidents which are worth these potential drawbacks. It provides Data Integrity which ensures that container images remain unchanged and undisturbed throughout their lifecycle. It gives encryption to both at rest and in transit, which ensures that container images are securely stored and transmitted between the registry and the Docker hosts. So we can conclude that it saves, both the time and effort of the user.
Image Security and Vulnerabilities in ECR – FAQ’s
What Do You Mean By Amazon ECR ?
Amazon ECR is known as “Amazon Elastic Container Registry”. It is AWS managed container image registry service which is secure, scalable, and reliable.
Why Is there a need Of the Image Security and Vulnerabilities in ECR?
The ECR provides Vulnerability Management Which means that the vulnerabilities are identified in container images which are configured and then they automatically expire or remove affected images based on specified rules or schedules.
How to Manage Image Security and Vulnerabilities in ECR?
Image Security and Vulnerabilities in ECR can be managed using the Docker. In this, codes can be used as the architecture of the Docker. The architecture codes needs inputs with the codes which are private credentials of the user and to know more, user must need to follow the AWS ECR instructions.
Explain Any Two Features Of Image Security and Vulnerabilities in ECR.
- It provides Data Integrity which ensures that container images remain unchanged and undisturbed throughout their lifecycle.
- It offers Access Control which control the mechanisms, and allows administrators to define granular permissions for accessing and modifying container images.
What Are The Limitations Of Image Security and Vulnerabilities in ECR?
It has a very tricky setup so it’s challenging for the developer to configure all the security settings correctly. It can be a real headache, especially if user is new to the container security because one wrong move can end up all the defense system.
Share your thoughts in the comments
Please Login to comment...