Data Isolation in DBMS
Last Updated :
13 Sep, 2023
In today’s era effectively managing volumes of data is crucial, for businesses and organizations. Database Management Systems (DBMS) play a role in this aspect by providing tools to store, retrieve, and manipulate data. However when multiple users are. Their transactions interact with the data simultaneously ensuring the integrity and consistency of that data becomes a significant challenge. The concept of data isolation is crucial, in the context we’re discussing. In this article, we will delve into the depths of data isolation within a database management system (DBMS) exploring its significance, terms, levels of isolation, and real-world implications.
What is Data Isolation?
At its core data isolation refers to maintaining actions between transactions to prevent interference with each other’s operations. The objective is to avoid situations where one transaction reads or modifies data while another transaction is simultaneously accessing it. By doing data isolation ensures the accuracy, reliability, other’s and predictability of a database’s behavior, in high-demand real-world scenarios.
Key Terminologies Used in Data Isolation
1) Data Isolation
Data isolation involves keeping transaction activities separate to prevent conflicts and maintain the integrity of a database. Maintaining data isolation is crucial, in managing databases as it ensures the integrity of data and consistency in environments, with users.
2) Database Transaction
A transaction refers to a series of activities performed on a database that is considered a unit of work. To maintain the integrity of the database the system follows the ACID principles which’re Atomicity, Consistency, Isolation, and Durability.
3) Concurrency Control
This involves managing transactions that occur simultaneously. Its objective is to prevent any inconsistencies or conflicts, in data when transactions interact with each other.
4) Isolation Levels
It determines how much separation there is between transactions, in a database. They range from the READ UNCOMMITTED) to the most restrictive (Serializable) balancing performance with isolation.
5) Phenomena of Reading
Reading phenomena refer to occurrences when transactions read data that is being modified by transactions. These phenomena include reads, non repeatable reads and phantom reads.
6) Dirty Read
A dirty read happens when a transaction retrieves data, from another transaction, which can later be undone resulting in data being read.
7) Non Repeatable Read
This phenomenon occurs when a transaction reads the data times but obtains different values during each read due, to concurrent updates.
8) Phantom Read
Phantom reads occur when a transaction retrieves a set of records based on conditions but other transactions insert or delete records that meet those conditions causing readings by the first transaction to differ.
Isolation Techniques
DBMS employs methods to achieve these levels of isolation including locking, multiversion concurrency control and timestamp based approaches;
Locking: Locking is an used technique where a transaction obtains locks on data items before accessing them. These locks can be. Shared (read locks) or exclusive (write locks). While effective, in maintaining the integrity of data locking can also lead to complications like deadlocks, which occur when two or more transactions are stuck waiting for resources held by each other.
Multiversion Concurrency Control (MVCC): MVCC creates versions of data items to support transactions. Each transaction sees a snapshot of the data as it existed at the beginning of the transaction preventing inconsistencies caused by updates during the transactions duration.
Timestamp based Methods: Transactions are assigned timestamps and the DBMS ensures that transactions with timestamps are executed before those, with timestamps. This approach guarantees serializability. Helps avoid conflicts.
Importance of Data Isolation
The importance of data isolation cannot be overstated when it comes to maintaining the accuracy and reliability of a database. Without isolation conflicts between transactions can result in results, data corruption and unpredictable behavior. By enforcing isolation levels a DBMS ensures that transactions can proceed without interfering with each other thus preserving data integrity.
Isolation Levels
Modern DBMSs offer isolation levels each striking a balance between isolation and performance. Lets delve into the used isolation levels:
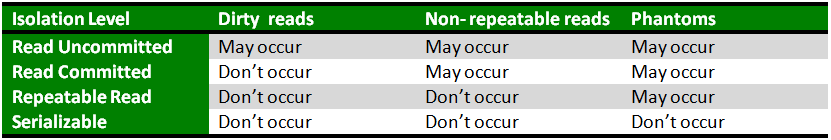
Isolation Levels
- Read Uncommited: This level provides the level of isolation allowing transactions to see uncommitted changes made by other transactions.
- Read Commited: At this level transactions cannot see uncommitted data avoiding issues like dirty reads. However non repeatable reads and phantom reads are still possible.
- Repeatable Read: This level prevents repeatable reads by locking rows during reads; however phantom reads can still occur.
- Serializable: The highest isolation level ensures that transactions execute sequentially without any read phenomena occurring. However it may impact performance due, to increased locking.
Real world implications
The impact of data isolation goes beyond discussions. In the banking industry if transaction processing is done incorrectly it can result in losses. Similarly in e commerce when multiple updates are made to stock there is a risk of overselling products. Healthcare systems need to ensure that patient records remain consistent during loads. Without isolation measures, in place these situations could cause chaos. Erode trust in the system.
FAQs on Data Isolation in DBMS
Q.1: Are there any drawbacks to using higher isolation levels?
Answer:
When using levels of isolation such as Serializable it’s important to note that this can lead to increased locking and a decrease, in system performance.
Q.2: Are there any tools to assist with managing data isolation, in database management systems (DBMS)?
Answer:
Most modern DBMSs offer built in mechanisms for handling data isolation, which include support for levels of isolation locking strategies and transaction management. Developers can utilize these tools to ensure the integrity of the data.
Q.3: How does data isolation contribute to the reliability of a system?
Answer:
Data isolation ensures that transaction results remain consistent and predictable in environments with high concurrency. This reliability helps establish trust among users and enables decision making based on the stored data.
Q.4: How does distributed data impact data isolation?
Answer:
In distributed databases ensuring data isolation becomes more intricate due to network latencies and potential discrepancies in isolation levels across nodes. Coordinating distributed transactions is crucial, in maintaining both isolation and consistency.
Share your thoughts in the comments
Please Login to comment...