Configuring MFA Delete On S3 Buckets
Last Updated :
11 Mar, 2024
The AWS Simple Storage Service (S3) is a cloud service provided by Amazon Web Services (AWS) to store your data securely. You can access this service through your IAM role or root user account. In this article, we’ll see how to secure your S3 data in addition to the IAM policies through the MFA assignment. Furthermore, we’ll cover how to set up MFA Delete for your AWS S3 bucket and its usage while deleting an object from the S3.
What is MFA?
Multi-factor Authentication (MFA) is an extra layer of protection on top of your username and password. MFA in AWS (Amazon Web Services) is an IAM best practice that helps you to secure services that require a second authentication in addition to the username and password credentials.
When will be MFA Delete required on the AWS S3?
- Permanently delete an object version.
- Suspend versioning on the bucket.
When do we not require an MFA Delete on the AWS S3?
- Enable versioning
- List deleted versions
Prerequisites
- Create and set up an AWS Account.
- Versioning must be enabled on the S3 bucket.
- Only the bucket owner (root owner) can enable/disable MFA Delete.
Step-by-Step Guide to Register MFA Delete on AWS S3
Step 1: Create S3 Bucket
- Login to AWS Console and navigate to AWS S3.
- Go to Buckets and click on Create a Bucket.
- Enter a unique and meaningful bucket name.
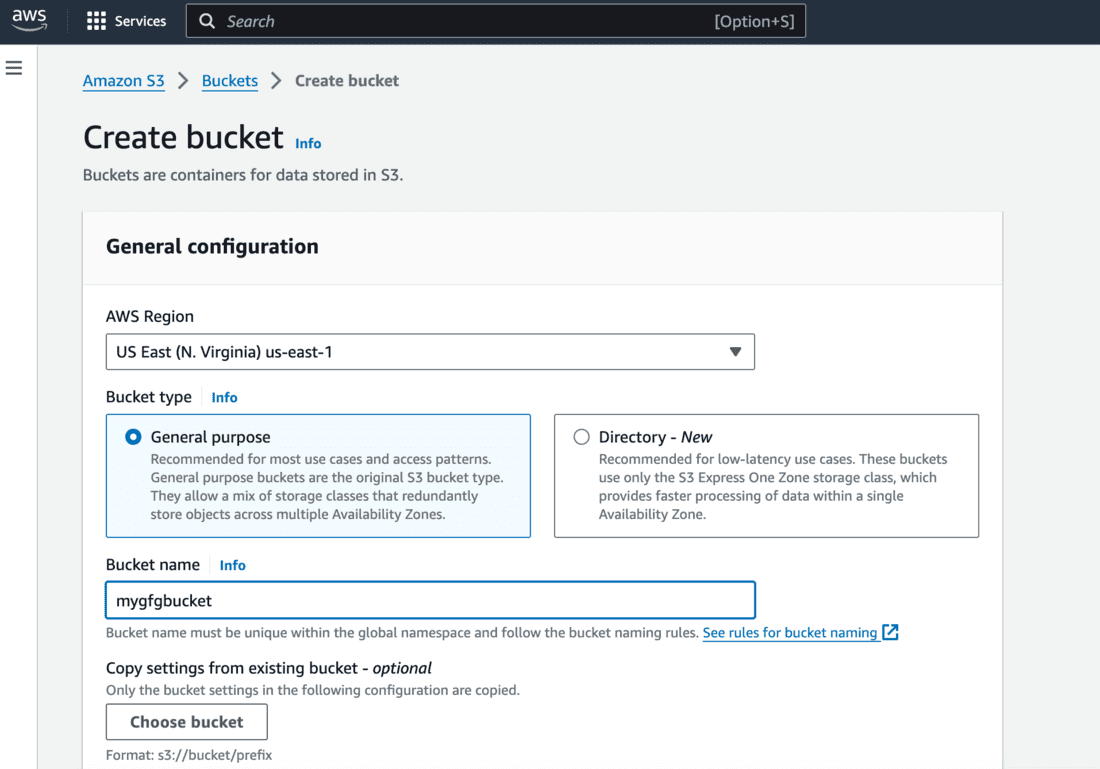
- Enable bucket versioning while creating the bucket.
- This can also be done after creating the bucket by going to the Properties tab on the bucket menu and editing bucket versioning.
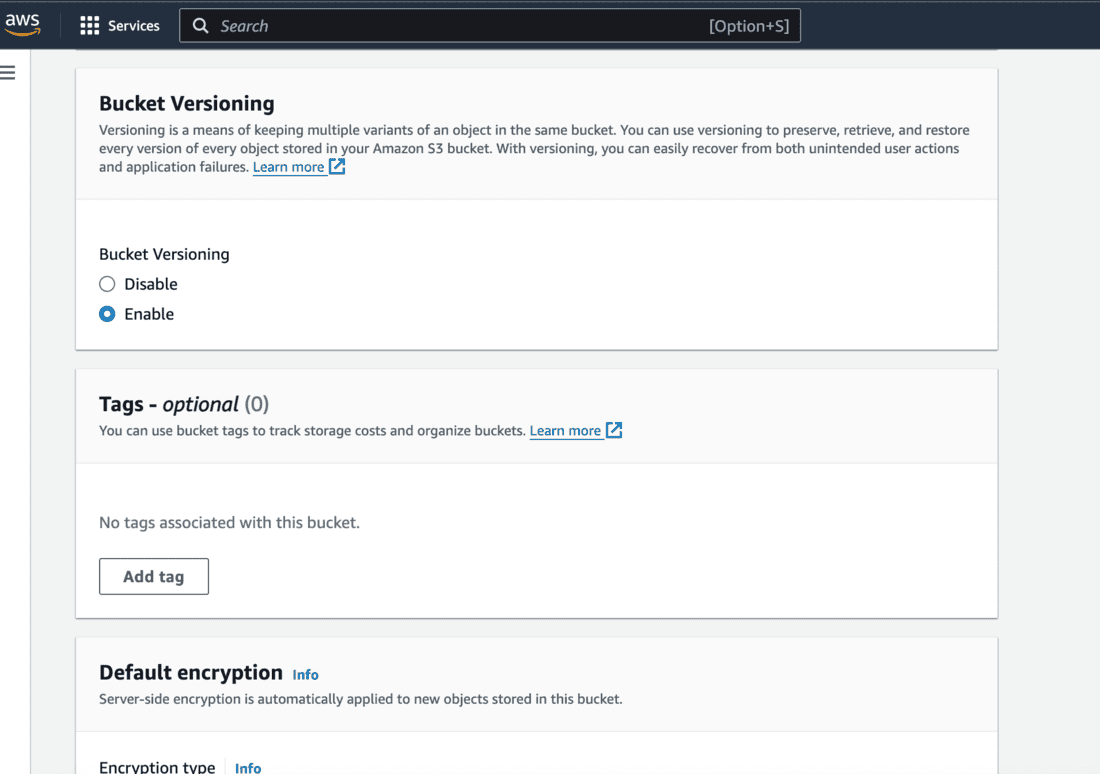
Step 2: Set up MFA on the root account
- Go to Security Credentials tab from the profile dropdown to setup the MFA for the root user.
- Make sure you’re logged into the root user account and not any IAM user.
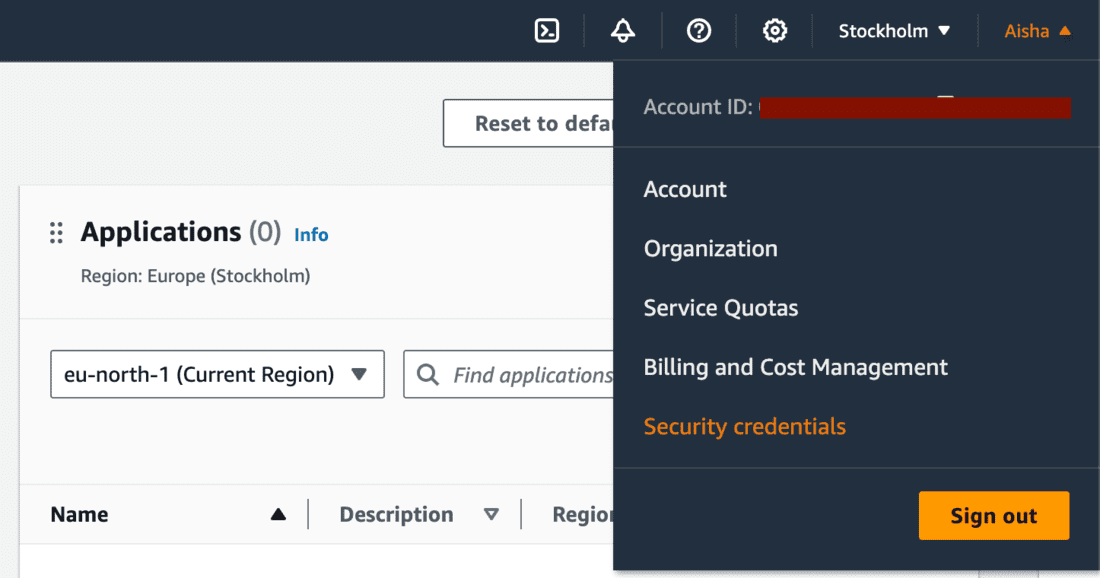
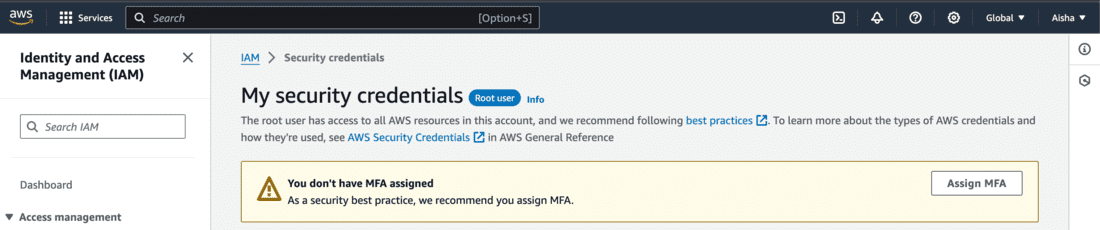
- You can see that MFA is not enabled.
- Click on Assign MFA to proceed with the setup.
- Enter a device name for the MFA for identification.
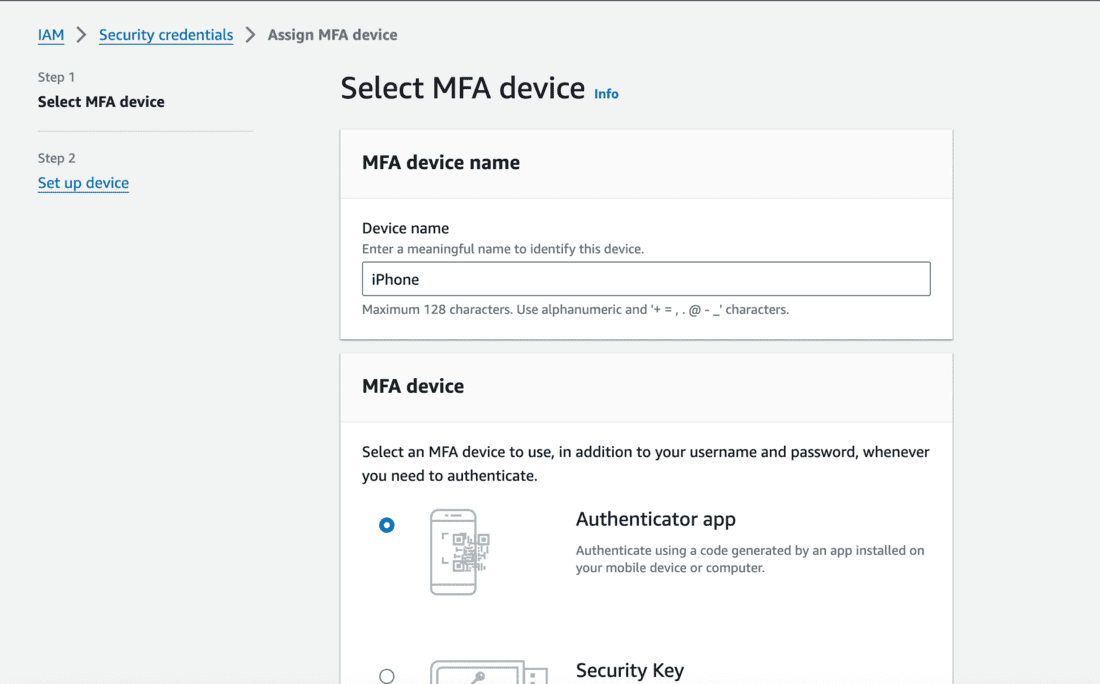
- Select your choice of MFA device.
- Let’s select Authenticator app here.
- Download an authenticator app on your mobile device like Google Authenticator, Microsoft Authenticator, Duo Mobile, etc.
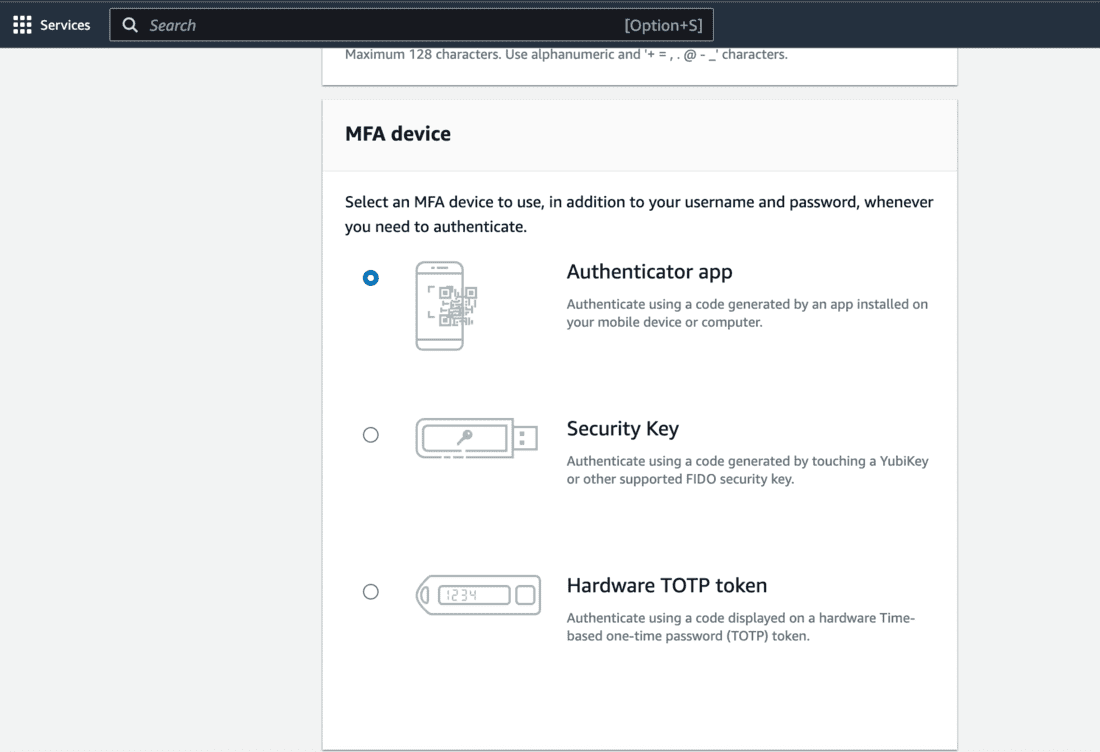
- After you’ve downloaded the app on your mobile device, configure your account.
- Scan the QR code from the authenticator app. Your AWS account will be directly visible and Time based passcode.
- Enter 2 consecutive MFA codes below to complete the setup.
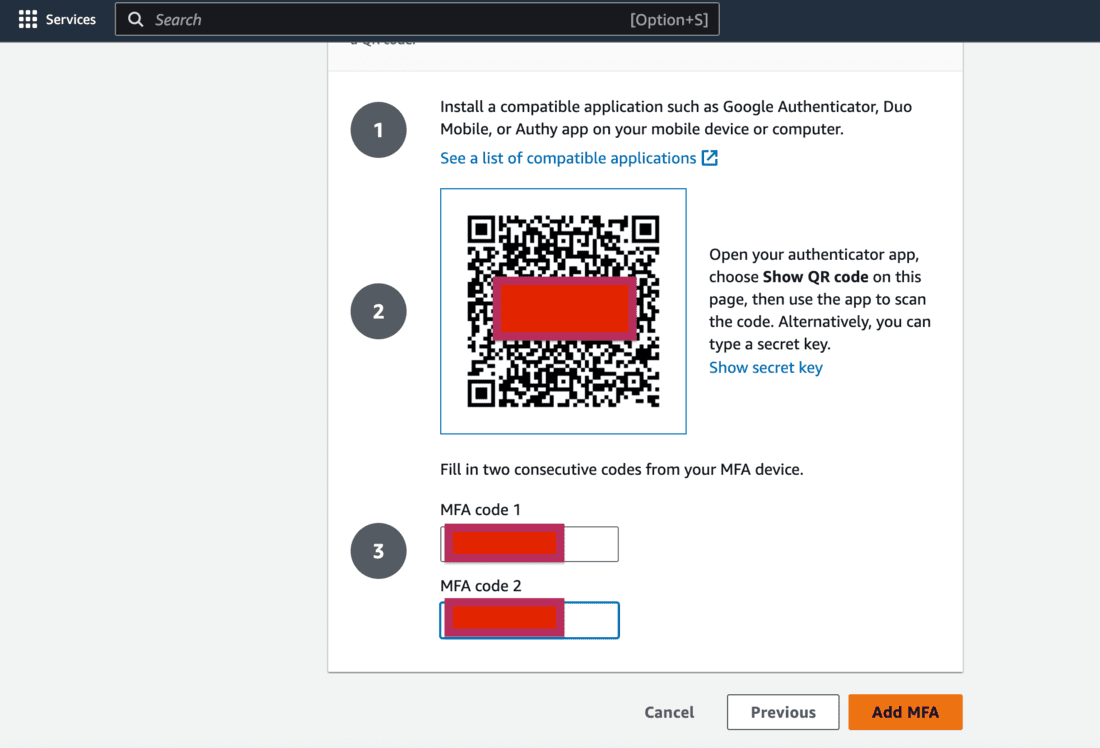
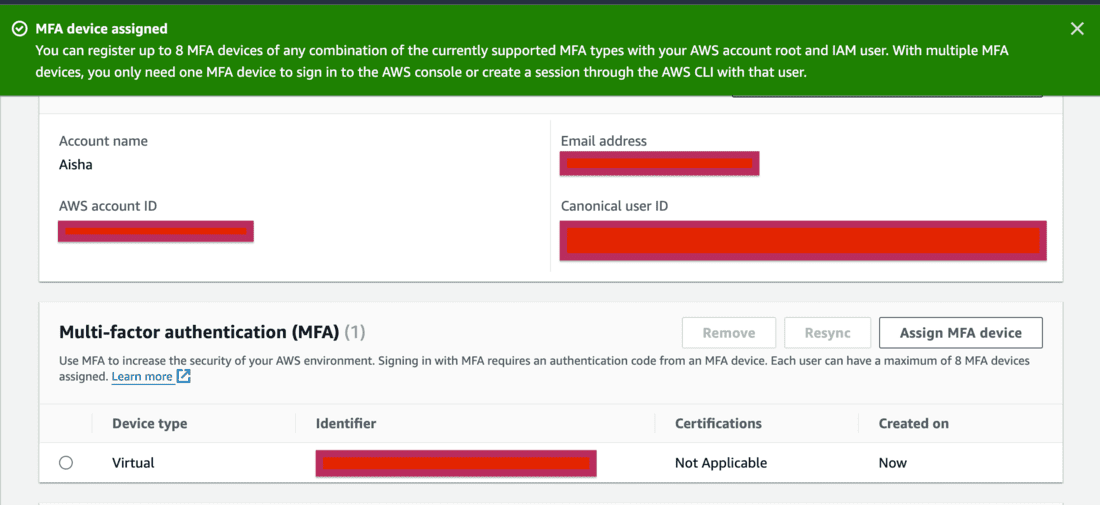
- Check if MFA device is assigned successfully.
- You’ll see the details of the MFA device under the MFA section.
Step 3: Check MFA Delete Configuration
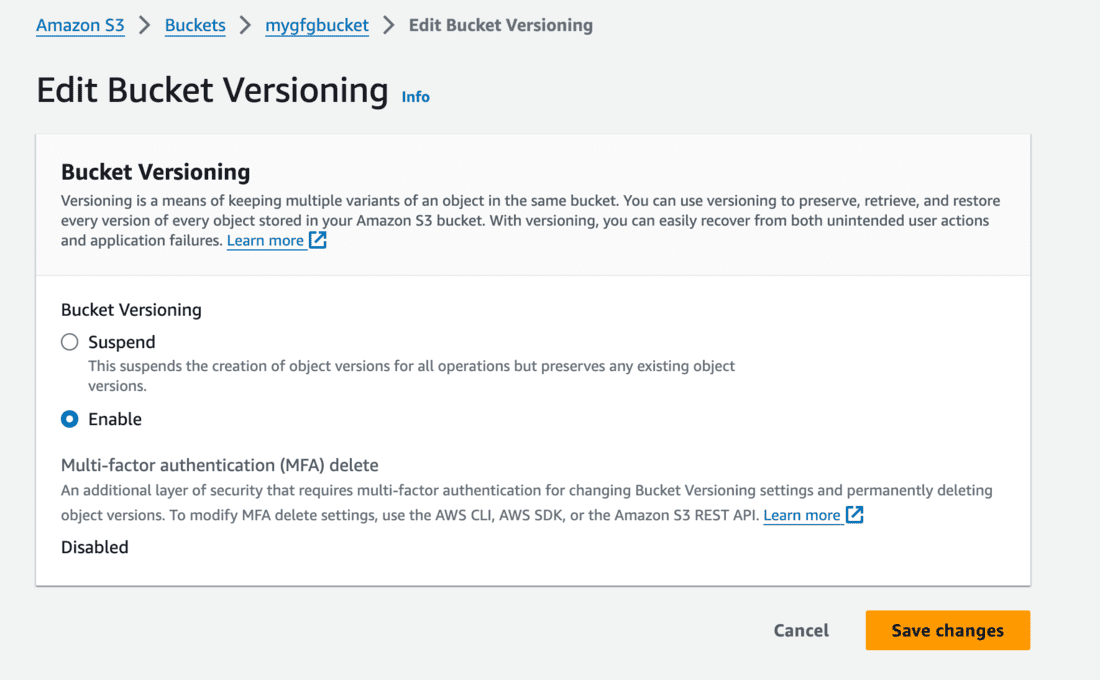
- Go to the bucket and click on the Properties tab.
- Go to Edit bucket versioning.
- You’ll see the MFA delete is disabled with a note that it cannot be changed from the AWS console.
Step 4: Configure AWS CLI for the root user
- To configure AWS CLI, you need to create access keys and secret keys on your root account.
- Go to IAM page and create access key.
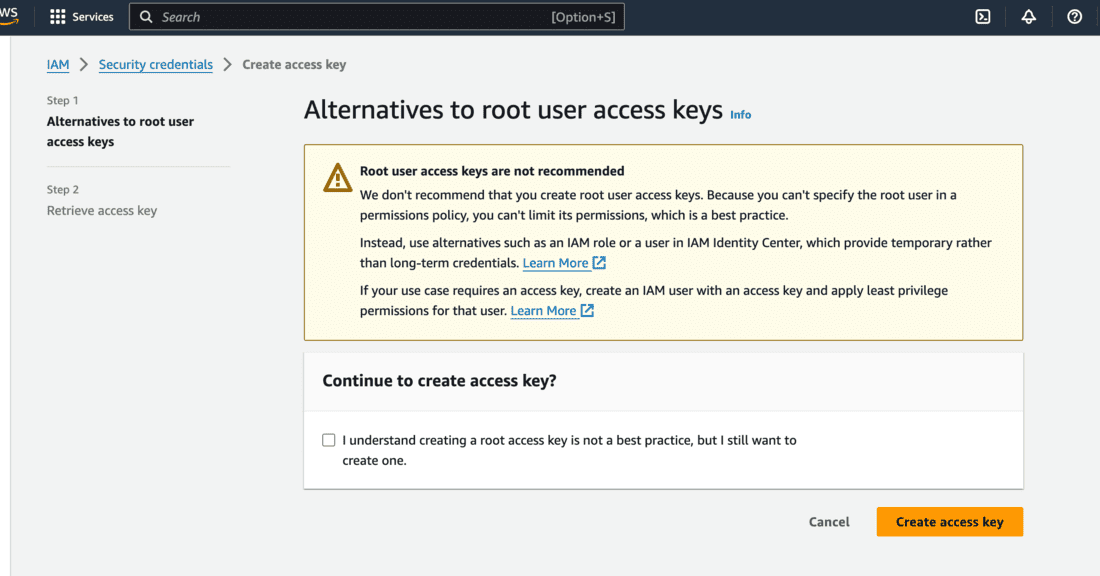
- Creating an Access Key on the root user is not recommended but in our case we need to set it up as MFADelete can be enabled only by the root user.
- Once access key is created, you’ll see it along with the Secret access key.
- Make sure you’ve stored it securely as you cannot retrieve it again!
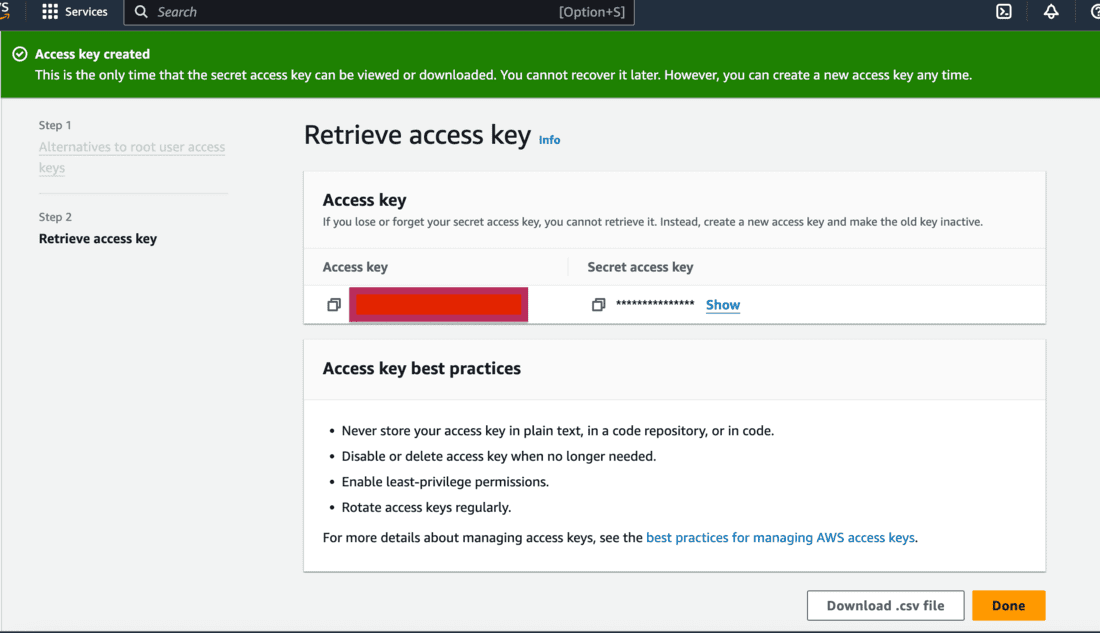
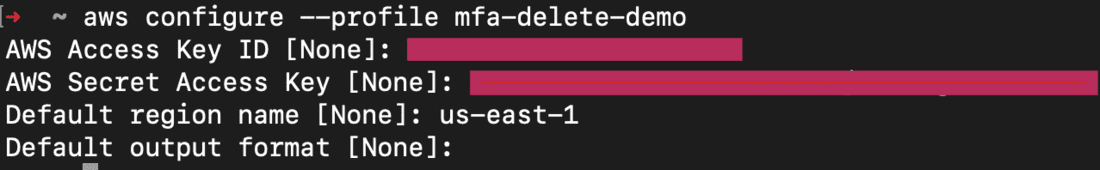
- Go to your terminal to set up a profile for enabling MFA Delete and run the below command.
- You can enter any profile name for the configuration. It doesn’t have to match with your root user’s account name.
aws configure --profile <any_profile_name>
- Enter the Access Key ID, Secret Access Key and region on prompt.
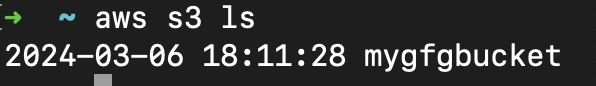
- Run below command to verify if the profile has been configured.
- You’ll see the list of buckets under that user.
aws s3 ls
Step 5: Enable MFA Delete using AWS CLI
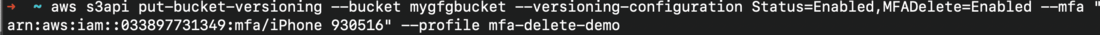
- Enable MFA Delete by executing the below command on your terminal.
- bucket_name: enter the bucket name for which you want the MFADelete to be enabled.
- arn-of-mfa-device: enter the arn for the MFA device from Step 2.
- mfa-code: enter the MFA code from your Authenticator app.
- profile_name: enter the profile name which you’ve configured previously.
aws s3api put-bucket-versioning --bucket <bucket_name> --versioning-configuration Status=Enabled,MFADelete=Enabled
--mfa <arn-of-mfa-device mfa-code> --profile <profile_name>
Step 6: Verify if MFA Delete is enabled
- Go to bucket versioning from the Properties tab and check if the MFADelete is Enabled.
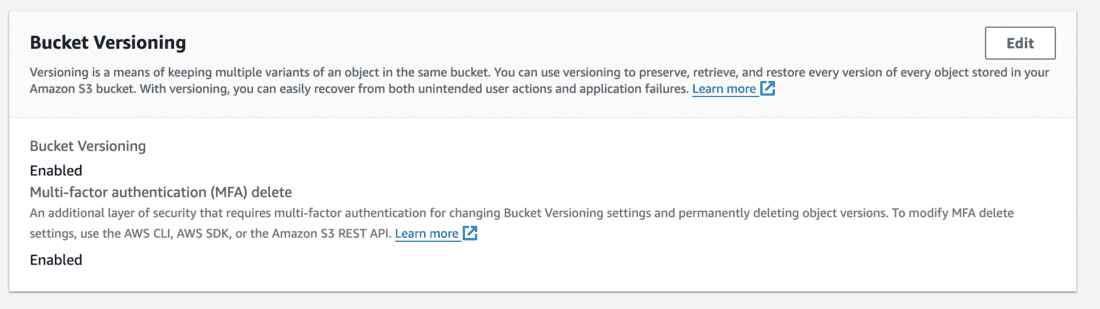
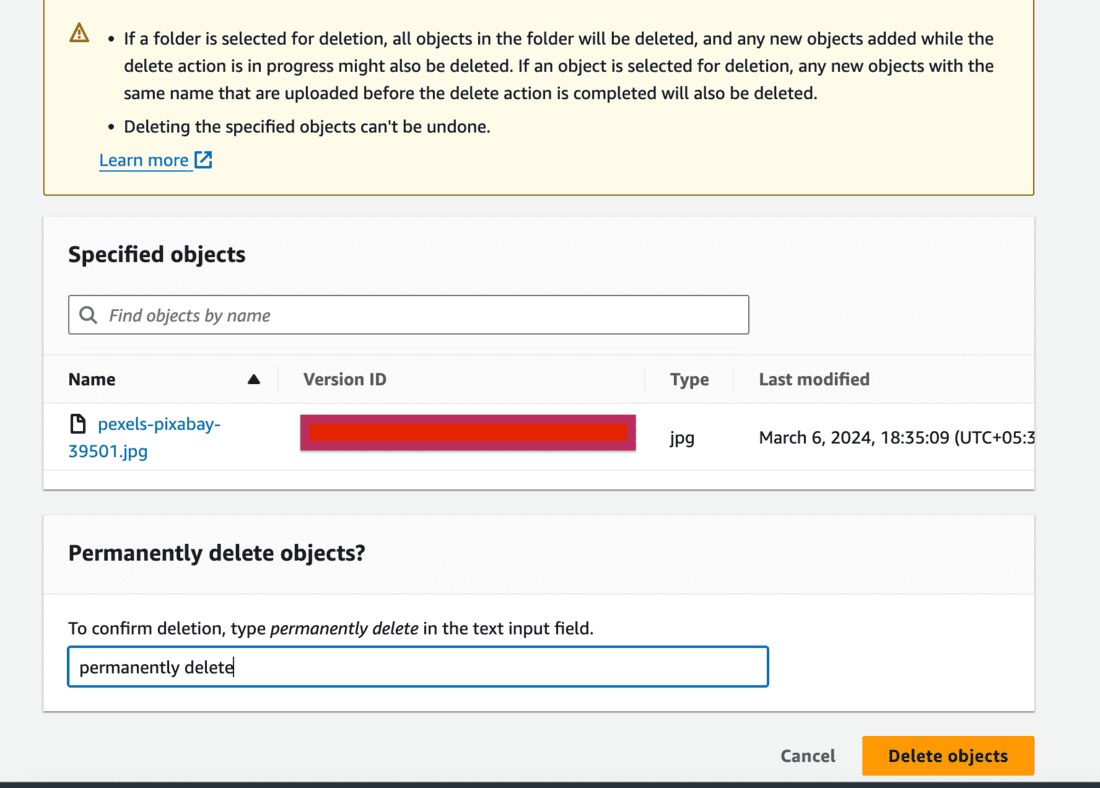
Step 7: Try deleting a file from the S3 bucket
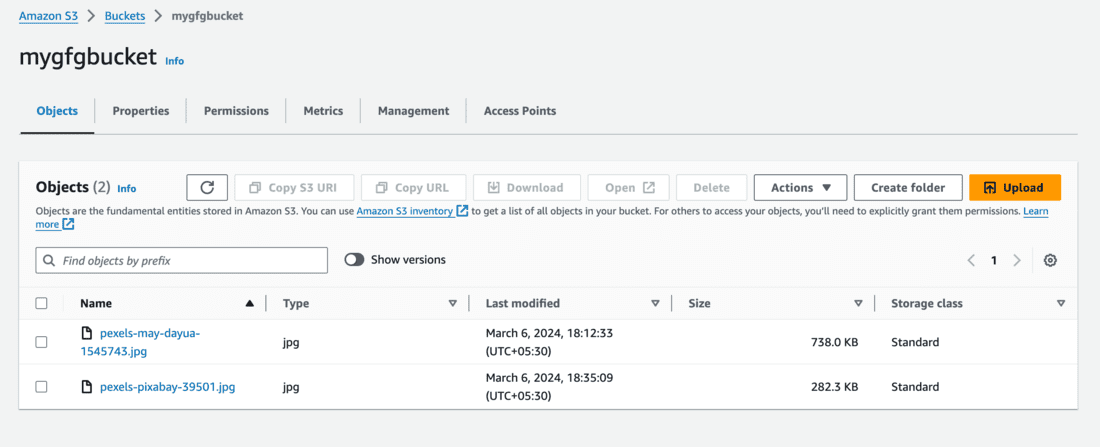
- Now let’s try to delete a file from the S3 bucket.
- You can see 2 files below. Select the second file’s (pexels-pixabay-39501.jpg) checkbox and click on Delete.
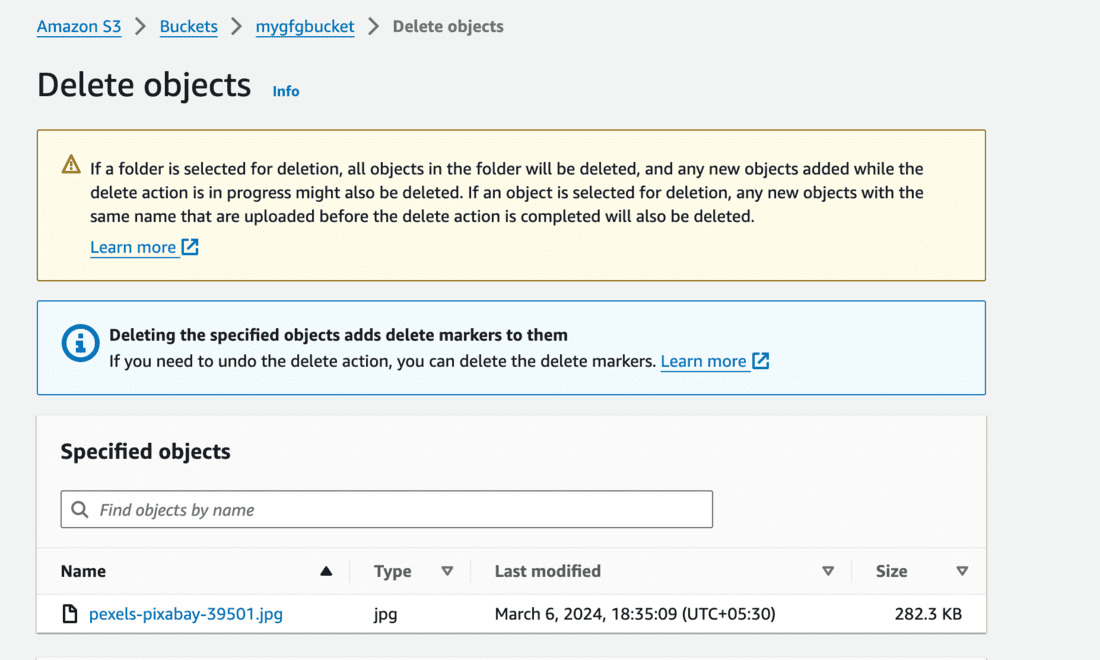
- You can see below Deleting the specified objects adds delete markers to them. This means that a different version of the file will be created since we’ve MFADelete enabled.
- After clicking on Delete, you can see 2 versions of the file in the Objects list.
- The file is still present along with the delete marker.
- Now, let’s try to delete the delete marker of the file.
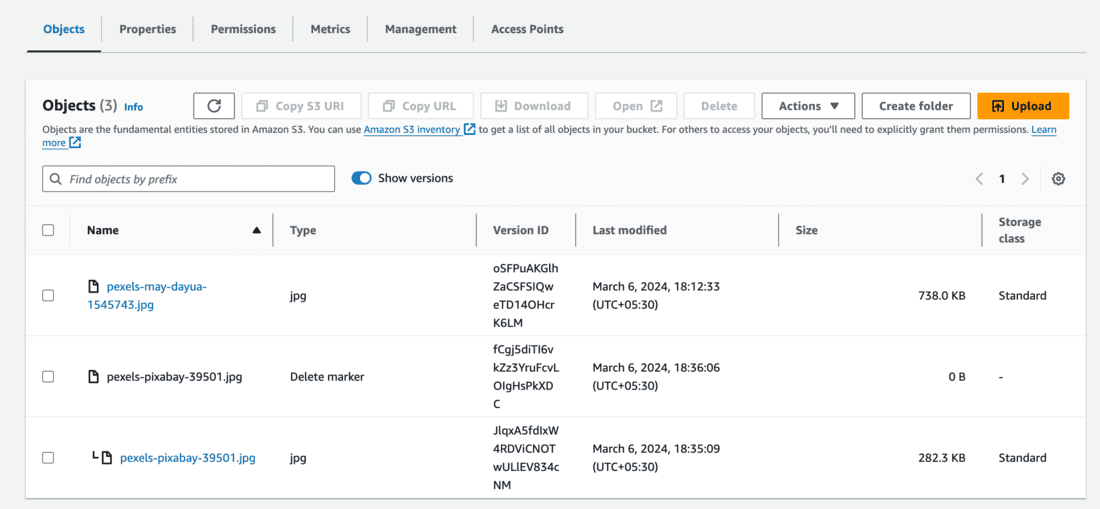
- You won’t be able to delete the object versions as MFA Delete is enabled.
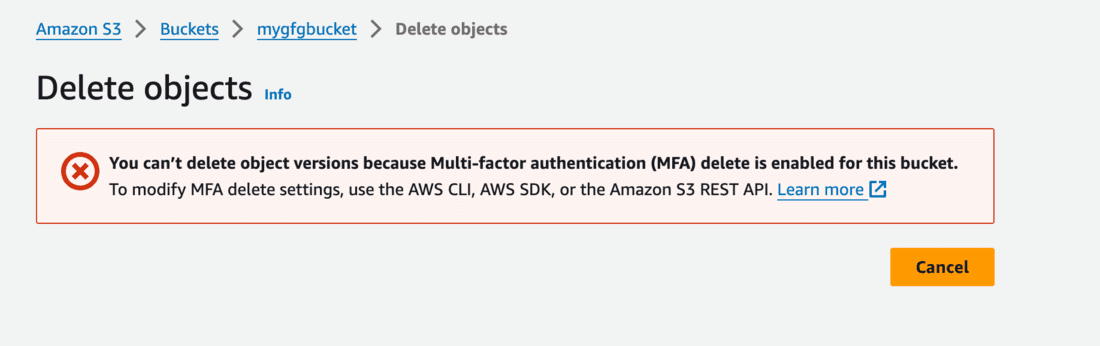
Step 8: Disable MFA Delete using AWS CLI
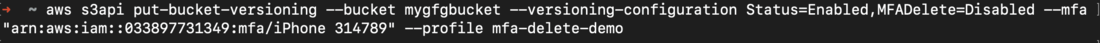
- To disable MFADelete, execute the below command.
- Here, as you can see MFADelete=Disabled.
aws s3api put-bucket-versioning --bucket <bucket_name> --versioning-configuration Status=Enabled,MFADelete=Disabled
--mfa <arn-of-mfa-device mfa-code> --profile <profile_name>
Step 9: Verify if MFA Delete is enabled
- Go to Edit Bucket Versioning and verify is MFA Delete is Disabled.

- Now try to delete the file, and you’ll be able to delete it.
- Check the object list to verify if the file is deleted.
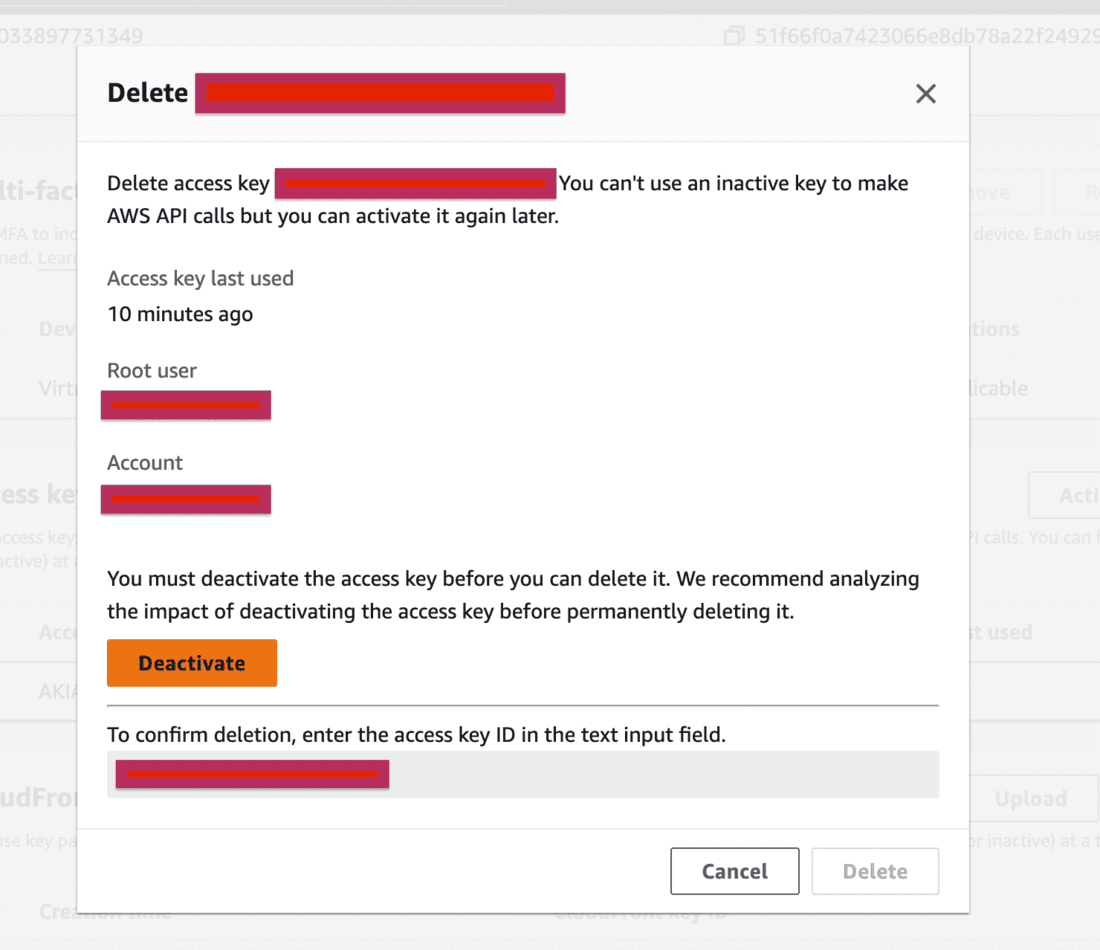
Step 10: Delete the Root User’s Access Key
- Delete your root user’s access key as soon as it’s not required.
- Select the Access key and click on Delete.
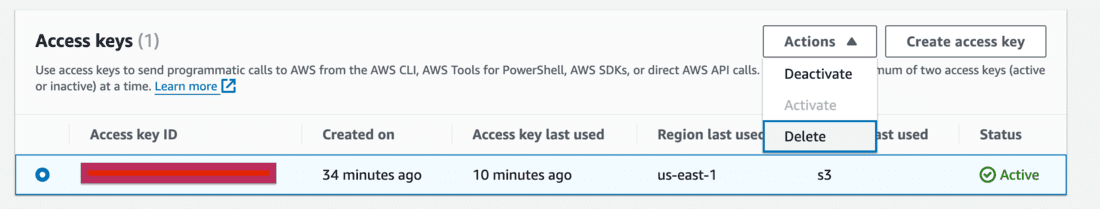
- Deactivate the access key first and then delete it permanently.
- If you want to set up the MFADelete again, you’ll have to create new access keys.
In this way you can add an additional layer of security on top of your password to restrict unauthorised member to delete objects from your AWS S3 Bucket.
Benefits of enabling MFA on the AWS
- MFA ensures only authorised personnel with both valid password and second factor authentication can access AWS S3 Bucket.
- MFA can be setup by the IAM users to provide extra security for already authorised AWS services.
- You can add more than one MFA devices. This will help you to access the account using the other MFA device, in case of the devices is lost, stolen and inaccessible.
Configuring MFA Delete on S3 Buckets – FAQ’s
What if an MFA device is lost or has stopped working?
- Select any other MFA device while signing the account.
- In case there was only one MFA device available, verify your account through email and phone number.
- Select the Troubleshoot MFA option when asked to enter the verification code.
- Verify your identity through email verification and then verify your phone number.
- Once you’ve signed in successfully, delete the lost MFA device from your MFA settings.
What devices can be set up as an MFA device?
- Virtual MFA Device: Using a mobile device as we saw in the above guide.
- FIDO security key: Hardware security keys are provided by Third Parties. Read more about FIDO in this article.
- Hardware TOTP token: A physical device which generates a six-digit numeric code based upon a time-based one-time password (TOTP) algorithm.
How many MFA devices can be set up at a time?
You can register up to 8 devices from the combination supported by AWS.
Share your thoughts in the comments
Please Login to comment...