Cariddi tool in Kali Linux is an open-source tool that is used for reconnaissance, vulnerability assessment, and also for security testing of Web-based applications. This tool allows hackers, security professionals, bug hunters, and penetration testers to crawl domain URLs and scan for various types of information, including endpoints, secrets, API keys, file extensions, and tokens. Cariddi is highly configurable and provides a wide range of options for tailoring your testing approach. In this article, we will see the installation steps of the Cariddi tool in Kali Linux, Key Features, and practical examples to perform testing on the target application.
Features:
- Endpoint Discovery: Cariddi can discover and enumerate endpoints, which are specific URLs or web application paths, that might be of interest during security testing. These endpoints often include login pages, admin panels, or other critical application functionality.
- Secrets Detection: The tool is capable of identifying secrets and sensitive information in the target domain, which can include hardcoded API keys, credentials, or other confidential data.
- File Extension Scanning: Cariddi can search for various file extensions on the target domain. This is useful for identifying files that may contain sensitive information, such as configuration files or backup files.
- Customization: Cariddi allows you to customize your testing by specifying custom parameters for endpoint hunting and custom regular expressions for secret detection.
- Concurrency and Delay Control: You can control the concurrency level for crawling and set delays between requests to avoid overloading the target server.
- HTTP Response Storage: The tool can store HTTP responses, enabling you to further analyze the server’s behavior.
How to Install Cariddi on Kali Linux?
In this section, we will see the detailed steps to install the Cariddi tool on the Kali Linux Operating System. So follow the below steps to get the Cariddi tool ready for usage on our system without encountering any problems.
Step 1: Firstly, on the Kali Linux system, we need to launch the terminal, as all the commands that need to be executed are done on the terminal of the Linux system. We can launch the Terminal from the Application Menu or by using the shortcut “CTRL + ALT + T“.

Terminal Opened
Step 2: Execute the below command to clone (download) a Git repository from a remote source, the URL points to the Cariddi repository on GitHub. The git clone command creates a local copy of the entire repository on your system.
git clone https://github.com/edoardottt/cariddi.git

Cloning Tool from GitHub
Step 3: After running the git clone command, we’ll have a new directory created in your current location. In this case, the directory is named “cariddi” because it corresponds to the repository’s name on GitHub.So navigate to that directory using the cd command.
cd cariddi
Navigating to the Cariddi Directory
Step 4: As this tool is a Go Programming-based tool, we need to have Golang language installed on our system, we can install it by executing the below apt command in the terminal.
sudo apt install golang
Installing Golang
Step 5: After installation, we need to download and install packages and dependencies for the tool. So below command fetches the source code, compiles it, and makes it available for use.
go get ./...

Downloading Essential Dependencies
Step 6: Now, we need to build the Cariddi tool for Linux OS. So we need to execute the below command which will compile the source code and generate an executable binary that can be run on a Linux system, allowing us to use Cariddi for security testing and reconnaissance tasks.
make linux
Building Tool for Linux
Step 7: Once the tool gets built for Linux OS, we can run the below help command to get the help page of the tool and confirm the successful installation of the tool.
cariddi -h
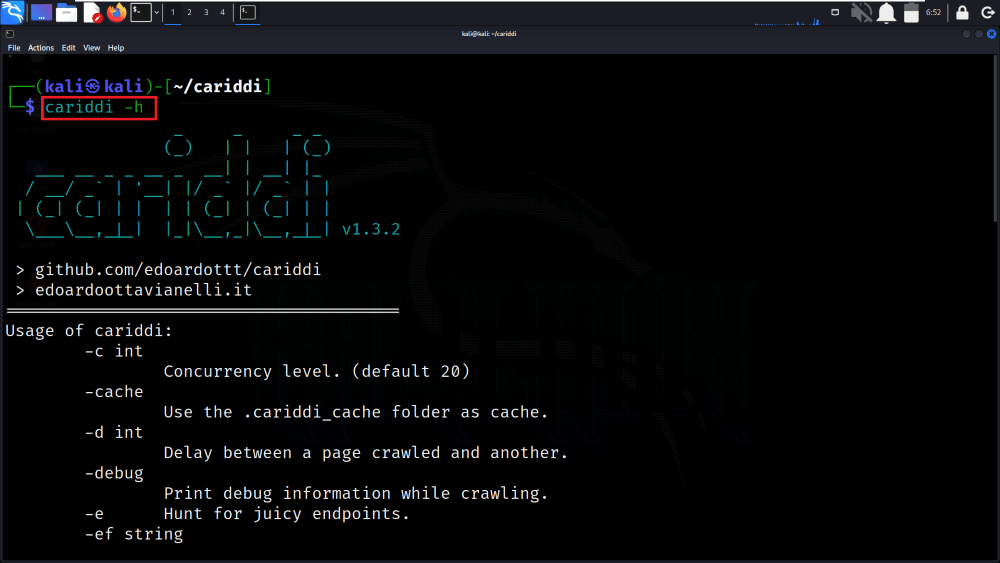
Viewing the Help Section of the Tool
How to Use the Cariddi Tool for Bug Hunting in Kali Linux?
In this section, we will see the practical usage of the Cariddi Tool to find the Hidden Endpoints of the target application.
Example 1: Simple Endpoint Scan
In this example, the command first echoes (prints) the URL “testphp.vulnweb.com” to the terminal, and then Cariddi is used to scan that URL for endpoints and secrets, providing the scan results in the terminal.
echo testphp.vulnweb.com | cariddi
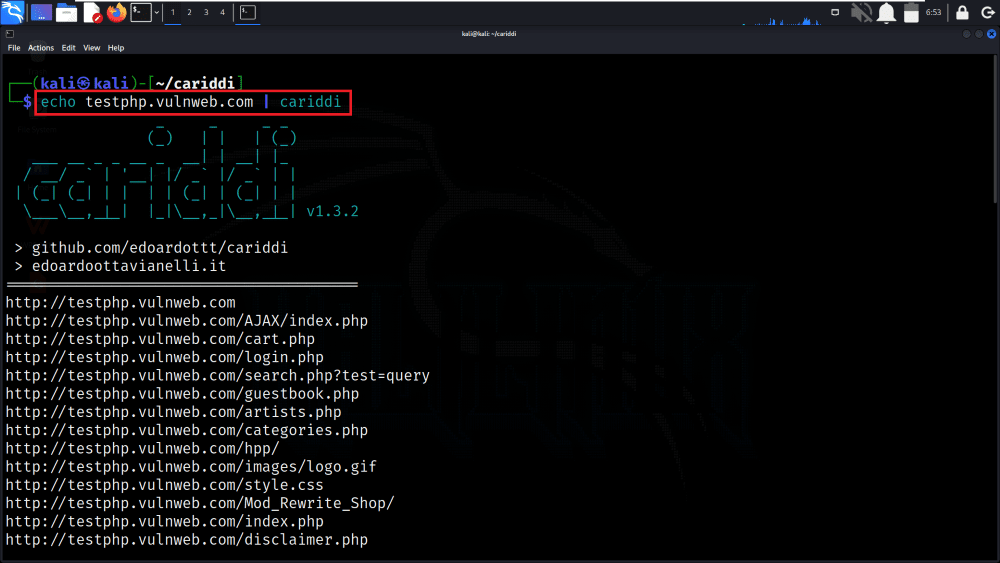
Executing Simple Endpoint Scan Command
In the below screenshot, we can see that we have got the results of a simple endpoint scan on the target domain.

Results of Simple Endpoint Scan
Example 2: Vulnerability Identify Scanner
In this example, the command scans the “testphp.vulnweb.com” URL using Cariddi with a concurrency level of 30, making it scan the target website more aggressively by sending requests from up to 30 concurrent threads. The results will be displayed in the terminal.
echo testphp.vulnweb.com | cariddi -c 30
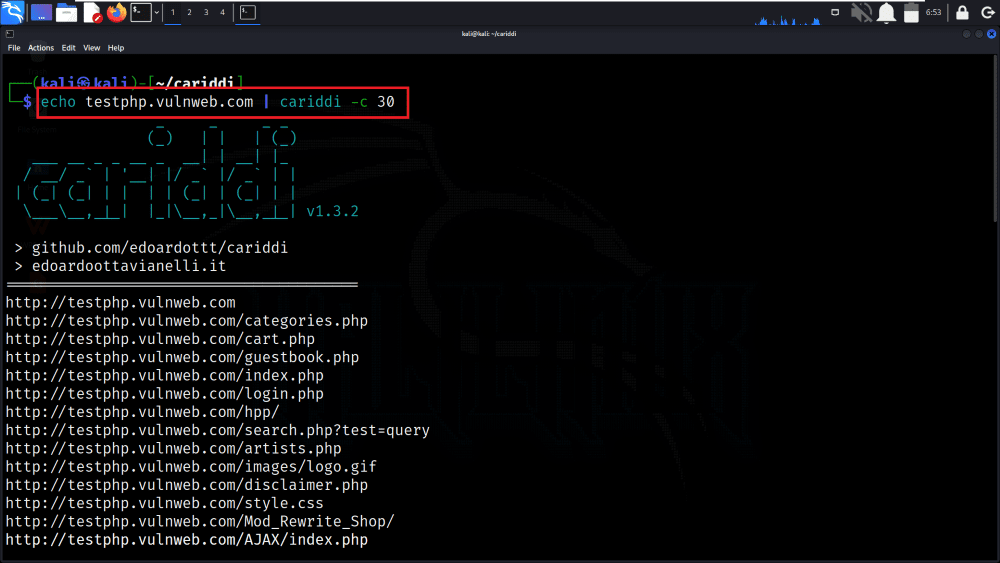
Executing Vulnerability Scanning
We have got the potential vulnerabilities present on the target web application.

Identified Vulnerabilities
Example 3: Specific Extension Endpoint
In this example, the command scans the “testphp.vulnweb.com” URL for specific endpoint extensions with “.php” using Cariddi. It focuses on hunting for endpoints with the “.php” extension, and the results will be displayed in the terminal.
echo testphp.vulnweb.com | cariddi -e php -debug

Specific Extension Type Scanning (php)
Example 4: Extract Useful Information
In this example, the command scans the “testphp.vulnweb.com” URL using Cariddi and extracts the most sensitive information from the target domain. Using this information, the target domain can be easily pentested.
echo testphp.vulnweb.com | cariddi -info

Getting Sensitive Information of Domain
In the below screenshot, we can see that, we have got sensitive information about the target domain.

Retrieved Sensitive Information
Conclusion
In Conclusion, Cariddi is a versatile open-source tool for security testing on Kali Linux, enabling users to conduct in-depth reconnaissance and vulnerability assessments on web applications and domains. With features like endpoint discovery, secrets detection, customizable scans, and various output options, Cariddi is a powerful addition to the security professional’s toolkit. It simplifies tasks such as hunting for specific endpoints, finding secrets, and customizing testing while providing actionable insights to improve web asset security. Its ability to handle multiple security testing tasks with control and flexibility makes it a valuable choice for security assessments.
Share your thoughts in the comments
Please Login to comment...