Amazon Web Services – Managing Invalid Keys in Key Management System
Last Updated :
28 Mar, 2023
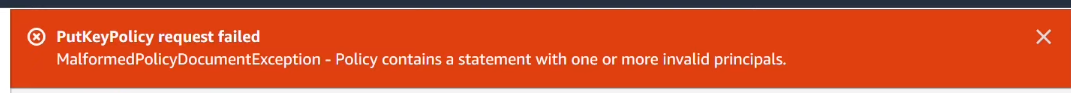
In this article, we will look into how to resolve an error indicating that a “customer master key policy statement contains one or more invalid principles”.
When we create identities within AWS Identity and Access Management (IAM). We often give them friendly names like developer, some name or administrator. IAM entities can also be identified with their ARNs. When IAM creates a user group role policy instance profile or server certificate, it assigns to each entity a unique ID that looks like below:
LJKSDFGHLK9FGHKLJ5GFH
Suppose user1 an IAM user in our company is specified in an AWS Key Management Service key policy and user1 leaves the company. Then a new person also named user1 is hired an IAM user may be created with the same name. In general, when an IAM user or an IAM rule that has access to the KMS key is deleted, KMS replaces the ARN of this entity with its unique ID in the key policy.
This makes sure that this new employee user1 does not inherit the key permissions granted to our previous user.
To resolve this issue follow the below steps:
Step 1: After logging into the AWS Management Console, navigate to the KMS console. Then select the key.
Step 2: Now choose Key policy.
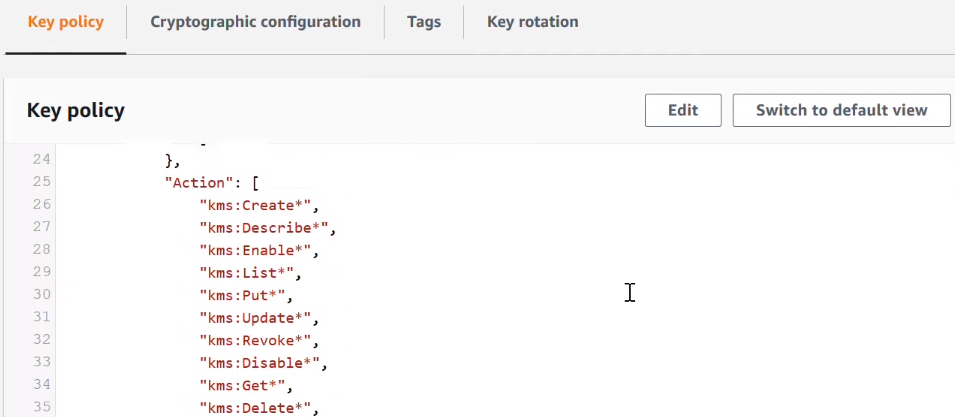
Here we can see the current permissions on the selected key.
Step 3: Navigate to the IAM console and choose the required users and then choose Delete user.

Step 4: Next choose Roles.
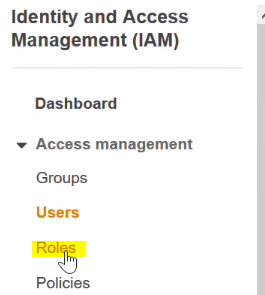
Step 5: Select the Role AdminRole.
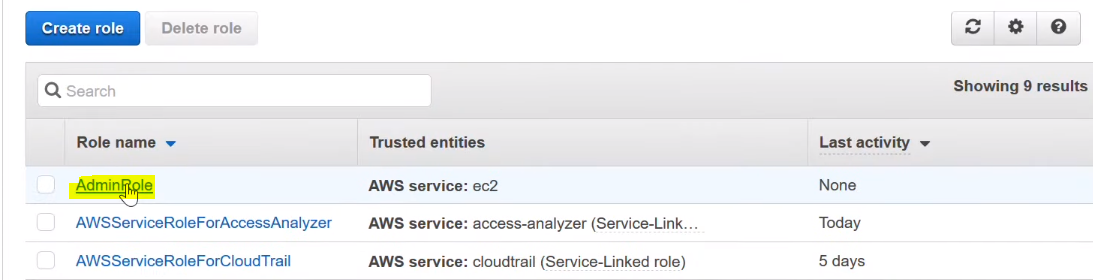
Step 6: Then choose Delete role.

Step 7: Navigate back to the KMS console. Note that the ARN of the user user1and admin rule have now been replaced by their unique ids.
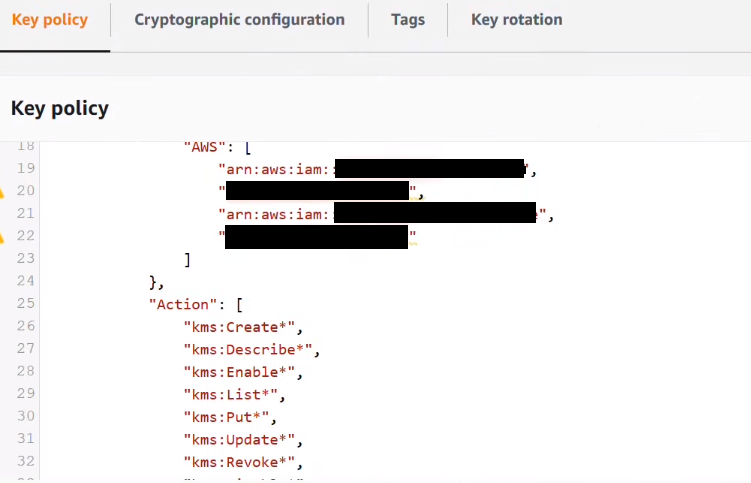
Step 8: To resolve the above-mentioned error, review the statements in the key policy and remove any unique IDs while paying attention to trailing commas. Choose Save changes.
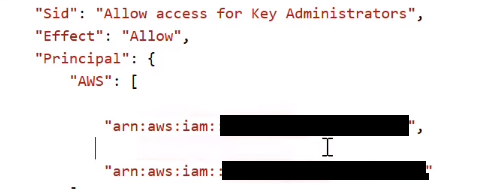
So now we’ve demonstrated to you why an invalid principle error occurs in KMS and what to do to resolve this.
Share your thoughts in the comments
Please Login to comment...