Working of SSL
Last Updated :
06 Oct, 2023
With the ever-increasing reliance on the internet for conversation and online transactions, making sure the safety of our data has become more important than ever. One technology that plays a crucial role in safeguarding our information is SSL, which stands for Secure Sockets Layer. This article will delve into the workings of SSL and explore the way it presents a stable channel between web browsers and servers. Knowing how SSL operates, you’ll gain valuable insight into the measures taken to guard your sensitive facts online.
What is SSL?
SSL stands for Secure Sockets Layer, and it works as a digital handshake between your browser and the website you are visiting. It ensures that any data transmitted between the two parties remains private and encrypted.
Secure Sockets Layer (SSL) is an encryption security protocol. It provides security to the data that is transferred between web browser and server. SSL encrypts the link between a web server and a browser which ensures that all data passed between them remain private and free from attack.
SSL is an Internet security protocol that utilizes encryption. Originally created by Netscape in 1995, its main objective is to guarantee privacy, authentication, and data integrity in online communications. SSL paved the way for the current TLS encryption that we rely on today. To identify a website that employs SSL/TLS, simply look for HTTPS in its URL instead of the traditional HTTP.
How Does SSL/TLS Work?
When you visit a website with SSL enabled, your browser requests a secure connection from the web server. The server responds by sending its public key certificate to authenticate itself. Your browser then generates a random session key to encrypt data before sending it over the network. This encrypted data can only be decrypted by the web server using its private key, an exclusive secret code known only to itself. With this complex dance of keys and encryption algorithms, SSL creates an impenetrable armor around your online interactions.
One vital aspect of SSL is trust. In order for it to function properly, web browsers need to trust the identity of websites they communicate with through authentication certificates issued by trusted third-party organizations called Certificate Authorities (CAs). This trust ensures that when you see that little padlock symbol or https:// in your browser’s address bar, it means the website has been authenticated by a trusted CA and all communications are secured using SSL/TLS protocols.
- In order to guarantee a superior level of privacy, SSL employs encryption techniques for data transmitted online. As a result, any individual attempting to intercept this data will only perceive an unintelligible amalgamation of characters that is nearly impossible to unravel.
- The SSL protocol establishes a trustworthy connection between two devices by initiating an authentication process called a handshake, guaranteeing that both devices are genuinely representing their claimed identities.
- In order to ensure the integrity of data, SSL also employs digital signatures to verify that the data remains unaltered until it reaches its intended recipient.
Difference Between TLS and SSL
SSL has undergone multiple iterations, with each subsequent version being more secure than its predecessor. In 1999, SSL was enhanced and transformed into TLS.
The original security protocol for HTTP was SSL, which has since been replaced by TLS. Although the SSL name is still commonly used, SSL handshakes are now referred to as TLS handshakes.
TLS Handshake
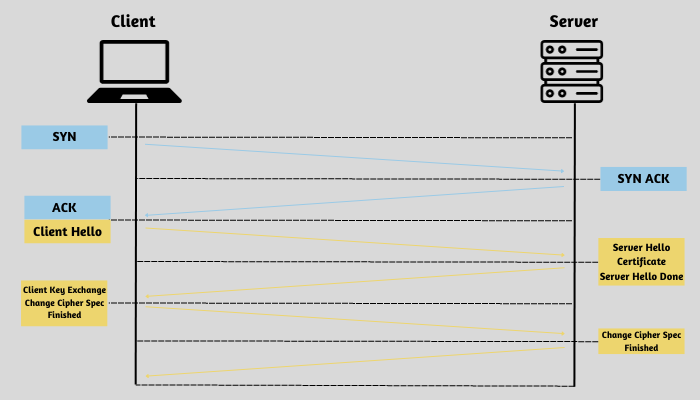
TLS Handshake
TLS is a robust encryption and authentication protocol specifically developed to enhance the security of Internet communications. The initiation of a communication session that employs TLS is marked by a TLS handshake. This crucial process involves an exchange of messages between the two parties involved, serving to acknowledge and verify each other’s identities, determine the cryptographic algorithms to be utilized, and establish session keys. The significance of TLS handshakes cannot be overstated as they form the bedrock of HTTPS functionality.
When is a TLS handshake initiated?
Whenever a user accesses a website using HTTPS, a TLS handshake occurs as the browser initiates communication with the website’s origin server. Additionally, any other HTTPS communications such as API calls and DNS over HTTPS queries also trigger a TLS handshake. These handshakes take place after establishing a TCP connection through a TCP handshake.
Steps In TLS Handshake
During a TLS handshake, a client and server exchange datagrams or messages to establish a secure connection. This process involves multiple steps as the necessary information is exchanged between the two parties, enabling further communication.
The specific sequence of actions in a TLS handshake may differ based on the type of key exchange algorithm employed and the cipher suites supported by both parties. The RSA key exchange algorithm, although regarded as insecure at present, was utilized in earlier versions of TLS prior to 1.3. Here’s basically how it goes:
- The ‘client hello’ message: The client commences the handshake process by transmitting a “hello” message to the server. This message will contain information regarding the TLS version supported by the client, the cipher suites it can utilize, as well as a string of randomly generated bytes referred to as the client random.
- The ‘server hello’ message: The server responds to the client’s hello message by sending a message that includes the server’s SSL certificate, the cipher suite selected by the server, and the server random – an additional random string of bytes generated by the server.
- Authentication: The client conducts a verification process of the server’s SSL certificate through the certificate authority responsible for its issuance. This serves to validate the server’s identity and ensure that the client is engaging with the legitimate owner of the domain.
- The Premaster Secret: The client transmits an additional string of bytes, known as the premaster secret. This premaster secret is encrypted using the server’s public key and can only be decrypted using the corresponding private key held by the server. (The client obtains the public key from the SSL certificate issued by the server.)
- Private Key Used: The premaster secret is decrypted by the server.
- Session Keys Created: Both the client and server utilize the client random, server random, and premaster secret to independently generate session keys. It is expected that they will obtain identical outcomes.
- Client is ready: The client securely transmits a message labeled as “finished” by encrypting it with a session key.
- Server is ready: The server securely dispatches a message with the label “finished”, employing a session key for encryption.
- Secure Symmetric Encryption Achieved: The handshake has been successfully executed, and further communication will be conducted using the session keys.
Every TLS handshake utilizes asymmetric cryptography, which involves the use of both public and private keys. However, it is not necessary for every handshake to involve the private key in the generation of session keys.
Handshake in TLS 1.3
TLS 1.3 excludes support for RSA, as well as other cipher suites and parameters that possess vulnerabilities to potential attacks. Additionally, it enhances the efficiency and security of the TLS handshake process, resulting in a faster and more secure TLS handshake.
The fundamental stages of a TLS 1.3 handshake are as follows:
- Client hello: The client transmits a client hello message containing the protocol version, client random, and a roster of cipher suites. As TLS 1.3 no longer supports insecure cipher suites, the available options for cipher suites are significantly limited. Additionally, the client hello includes the parameters necessary for computing the premaster secret. Essentially, the client assumes it is aware of the server’s preferred key exchange method (which is highly likely given the simplified list of cipher suites). This reduction in handshake length is a significant distinction between TLS 1.3 handshake and those of TLS 1.0, 1.1, and 2.0 handshakes.
- Server Generates Master Secret: The server has successfully received the client random, client’s parameters, and cipher suites. It already possesses the server random as it can generate it independently. Consequently, the server is now able to generate the master secret.
- Server hello and “Finished”: The server’s hello message contains the server’s certificate, digital signature, server random, and chosen cipher suite. In addition to this, it also sends a Finished message as it already possesses the master secret.
- Final steps and client “Finished”: The client conducts an authentication procedure by verifying the signature and certificate, generates a master secret, and then transmits a message labeled as Finished.
- Secure Symmetric Encryption Achieved
0-RTT( Zero Round-Trip Time)
TLS 1.3 introduces a faster version of the TLS handshake that eliminates the need for any back-and-forth communication between client and server. In cases where the client and server have previously connected, they can generate an additional shared secret called the resumption main secret from their initial session. Additionally, during this initial session, the server provides the client with a session ticket. In subsequent sessions, the client can utilize this shared secret to securely transmit encrypted data to the server in its first message, along with presenting the session ticket. As a result, TLS seamlessly resumes between the client and server.
FAQs On SSL
Q.1: What is SSL?
Answer:
SSL stands for Secure Sockets Layer. It’s a security protocol used to establish an encrypted connection between a web server and a web browser, ensuring that data exchanged between them remains private and secure.
Q.2: What is SSL certificate?
Answer:
An SSL certificate is a digital certificate that verifies the authenticity of a website’s identity. It contains the website owner’s public key and is used to initiate secure connections with browsers.
Q.3: How do I obtain an SSL certificate?
Answer:
You can get an SSL certificate from a trusted Certificate Authority (CA) or through your web hosting provider. The process typically involves generating a Certificate Signing Request (CSR) and following the CA’s validation process.
Q.4: How often do SSL certificates expire?
Answer:
SSL certificates typically have a validity period of one to two years. After that, they must be renewed to maintain a secure connection.
Q.5: What happens when an SSL certificate expires?
Answer:
When an SSL certificate expires, the secure connection will no longer work, and visitors may see security warnings when accessing your site. It’s essential to renew it promptly.
Q.6: Is SSL the same as TLS (Transport Layer Security)?
Answer:
SSL and TLS are closely related protocols, with TLS being the newer and more secure version. However, the term “SSL” is still commonly used to refer to both protocols.
Share your thoughts in the comments
Please Login to comment...