What is SSL Tunneling?
Last Updated :
30 Sep, 2022
SSL Tunneling involves a client that requires an SSL connection to a backend service or secure server via a proxy server. This proxy server opens the connection between the client and the backend service and copies the data to both sides without any direct interference in the SSL connection.
A diagram that demonstrates SSL Tunneling is given as follows:
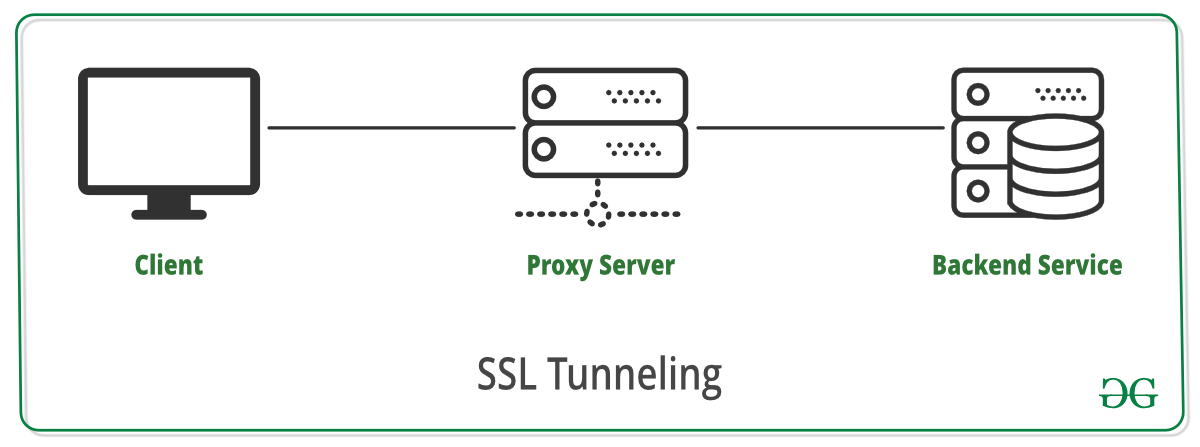
Working of SSL Tunneling
The stepwise working of SSL Tunneling from its creation to end is given as follows:
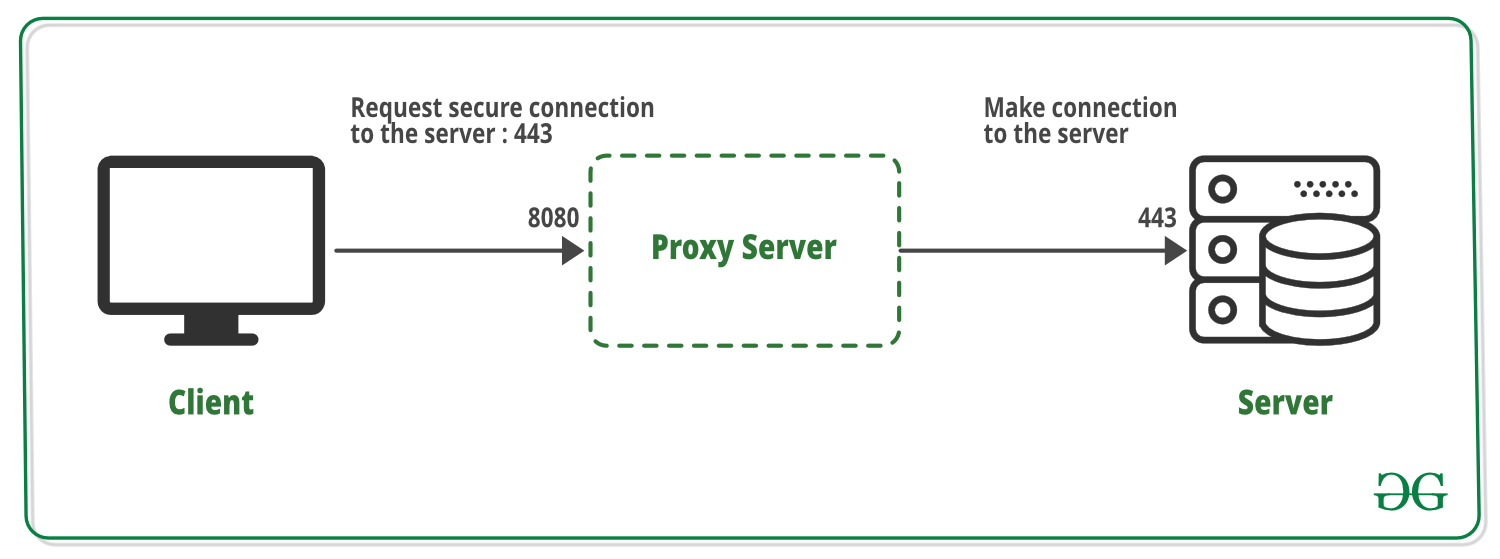
- A tunneling request CONNECT is made by the client on port 443 for HTTPS. This request is sent to the proxy server automatically for the HTTPS request. The CONNECT request is used by the RFC 2616 to establish a tunnel.
- The proxy server receives the tunneling request on the port 8080. Then it connects the secure destination server to the port that is requested by the client.
- The proxy server sends back a 200 OK response to the client to confirm that an SSL connection is created.
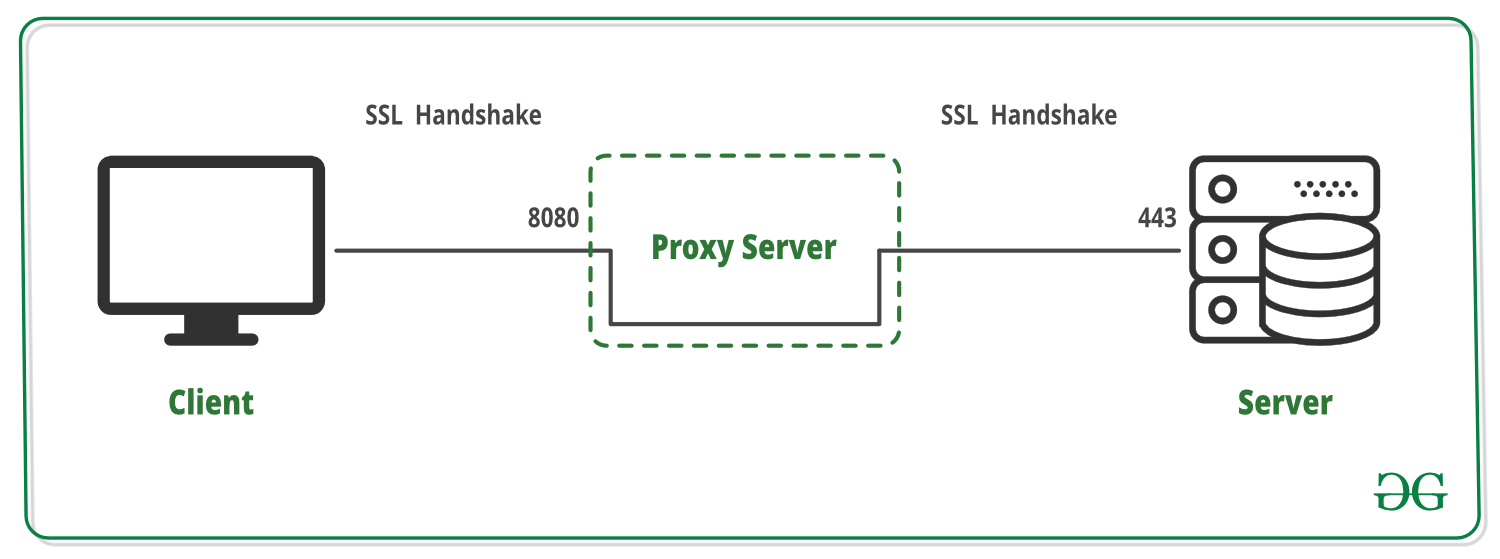
- A TLS handshake occurs effectively between the client and the server as the proxy server plays no part in it.
- After the TLS handshake, the encrypted data is passed from the client to the server via the proxy server and vice versa. This data is only decrypted at the client or the server and never the proxy server.
- When the closure of the connection is requested by the client or the server, the connections at ports 443 and 8080 are closed by the proxy server and normal operations resume.
Features of SSL Tunneling
- To perform SSL tunneling between the client and the server using HTTPS URLs, the client should support SSL and HTTPS. In case the client does not support HTTPS, the Proxy Server’s HTTPS proxying capability can be used.
- The security of SSL tunneling is on par with SSL without proxying. This means that using the proxy server does not change or reduce the security of SSL at all.
- The proxy server in SSL tunneling cannot access the transaction between the client and the server as it is encrypted. This means that no eavesdropping is possible, either from the proxy server or from third parties.
- The proxy server cannot verify if the protocol used between the client and the server is SSL as it cannot access the transaction. So it is best if known ports i.e. port 443 for HTTPS and 563 for SNEWS are used for security reasons.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...