How to use AWS Credentials in Jenkins Pipeline
Last Updated :
17 Apr, 2024
Jenkins, an industry-standard automation server, assumes a pivotal role in present-day software development practices, especially in continuous integration and continuous delivery (CI/CD) work processes. As associations progressively embrace distributed computing, coordination with cloud services like Amazon Web Services (AWS) becomes fundamental for the vast majority of Jenkins projects.
AWS offers a huge array of services, from scalable registering capacity to capacity arrangements and data set service, pursuing it is a well-known decision for facilitating applications and managing infrastructure; integrating AWS credentials into Jenkins pipelines allows consistent connection with AWS resources straightforwardly from inside the pipeline scripts, working with undertakings, for example, deploying applications, provisioning resources, and managing infrastructure.
In this article, we dig into the process of safely integrating AWS credentials into Jenkins pipelines. We’ll investigate the principal ideas, step-by-step procedures, and best practices associated with actually utilizing AWS credentials inside Jenkins pipelines. Moreover, we’ll give down-to-earth models and address normal inquiries to enable designers to harness the force of AWS within their Jenkins work processes.
Primary Terminologies
- Jenkins: Jenkins is an open-source automation server that works with the automation of different programming advancement processes, including building, testing, and deploying applications.
- Pipeline: In Jenkins, a pipeline is a progression of steps or activities that define the continuous integration and continuous delivery (CI/CD) process for a product project. It tends to be defined using a Jenkins file or through the Jenkins UI.
- Credentials: Credentials in Jenkins refer to authentication data used to access outside systems or administrations. This can incorporate usernames, passwords, access keys, and other verification tokens.
- AWS Credentials: AWS credentials are the verification credentials expected to get to AWS services automatically, these normally comprise an access key ID and a secret access key, which are utilized to validate solicitations to AWS APIs.
- AWS (Amazon Web Services): AWS is a far-reaching cloud computing platform provided by Amazon. It offers an extensive variety of cloud services, including computing power, storage choices, databases, AI, machine learning, and so on.
- Plugin: A plugin is a software component that adds explicit elements or usefulness to Jenkins, In this unique circumstance, the AWS Credentials Plugin is a Jenkins module that permits clients to oversee and utilize AWS credentials inside Jenkins pipelines safely.
Step-By-Step Process to use AWS Credentials in Jenkins Pipeline
Step 1: Launch an EC2 Instance
- Login into AWS Console and login with credentials or create account
- Now go to EC2 dashboard and launch an EC2 instance
Now connect with terminal
Step 2: Install Java
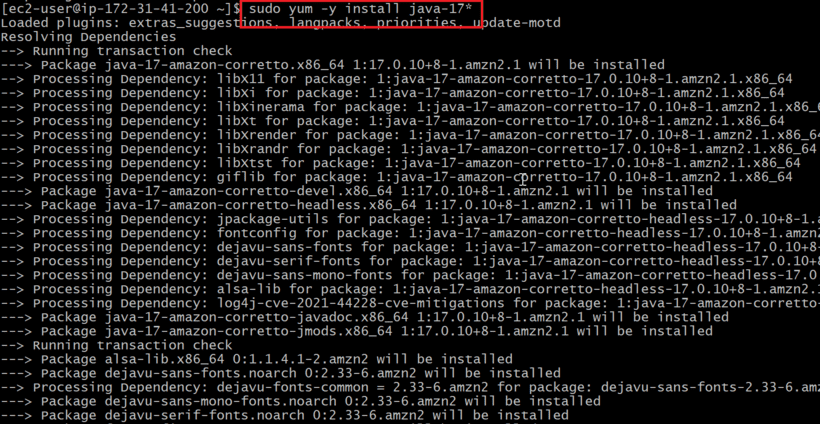
- We need to install java because jenkins run time is java. Without java jenkins cannot be run. Install java by using following command
sudo yum -y install java-17*
Step 3: Install Jenkins
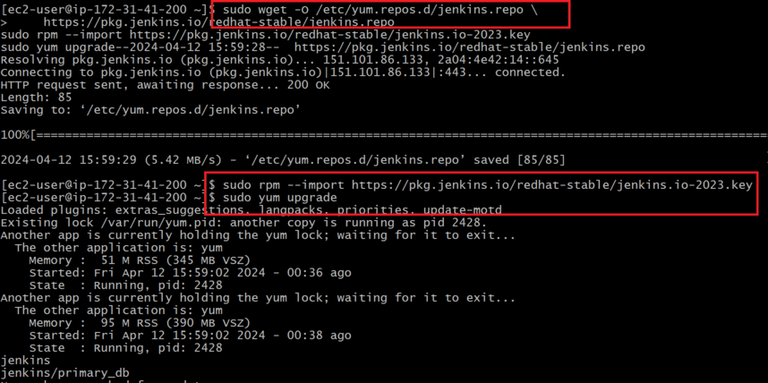
- After installation of java, now install jenkins packages from official page or follow below commands to install jenkins packages.
sudo wget -O /etc/yum.repos.d/jenkins.repo \
https://pkg.jenkins.io/redhat-stable/jenkins.repo
sudo rpm --import https://pkg.jenkins.io/redhat-stable/jenkins.io-2023.key
sudo yum upgrade
- After completion of package installation, Now install jenkins by using following command
sudo yum -y install jenkins
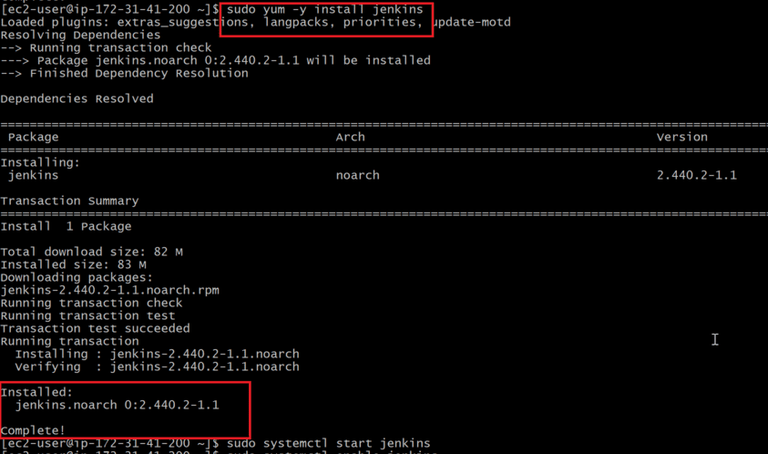
- Now start and enable jenkins by using following and also check status of the jenkins either it was running or not
sudo systemctl start jenkins
sudo systemctl enable jenkins
sudo systemctl status jenkins
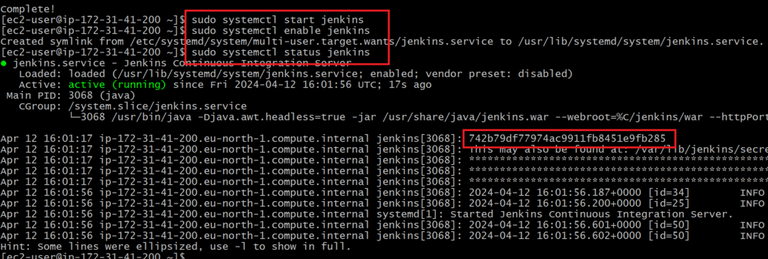
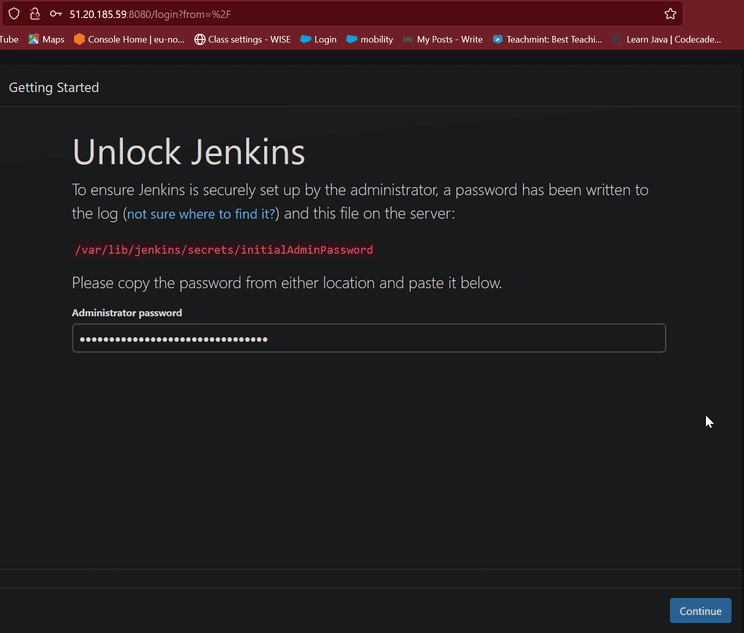
- While we executed status jenkins it’s shows administration password. Copy that password it is useful to unlock jenkins or check password in below provided path.
/var/lib/jenkins/secrets/initialAdminPassword
- Now unlock jenkins by providing administration password.
Here we see, official page of jenkins
Step 4: Install Plugin
- Here we need to install Amazon EC2 plugin because without this plugin we cannot add AWS Credentials in jenkins pipeline.
- Now follow this to install plugin
- Click on Manage jenkins then click on Plugins
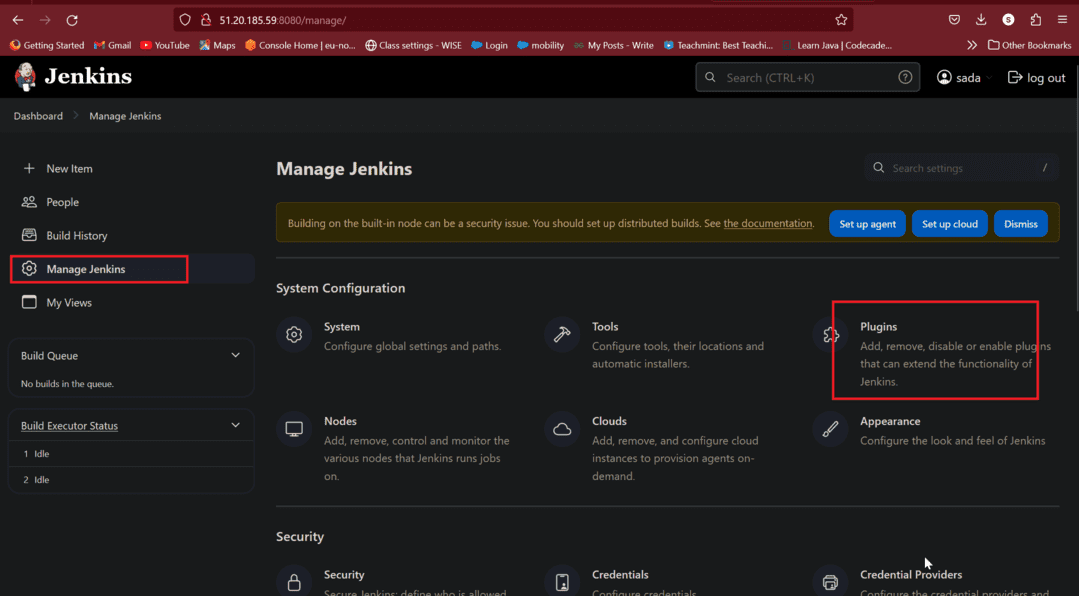
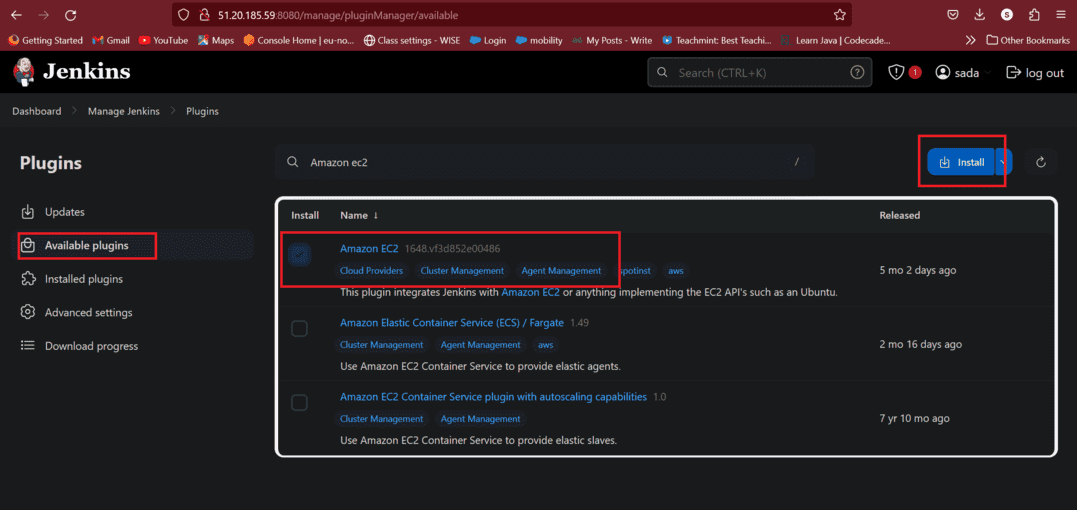
- Click on Available Plugins
- Click on Amazon EC2
- Then click on Install
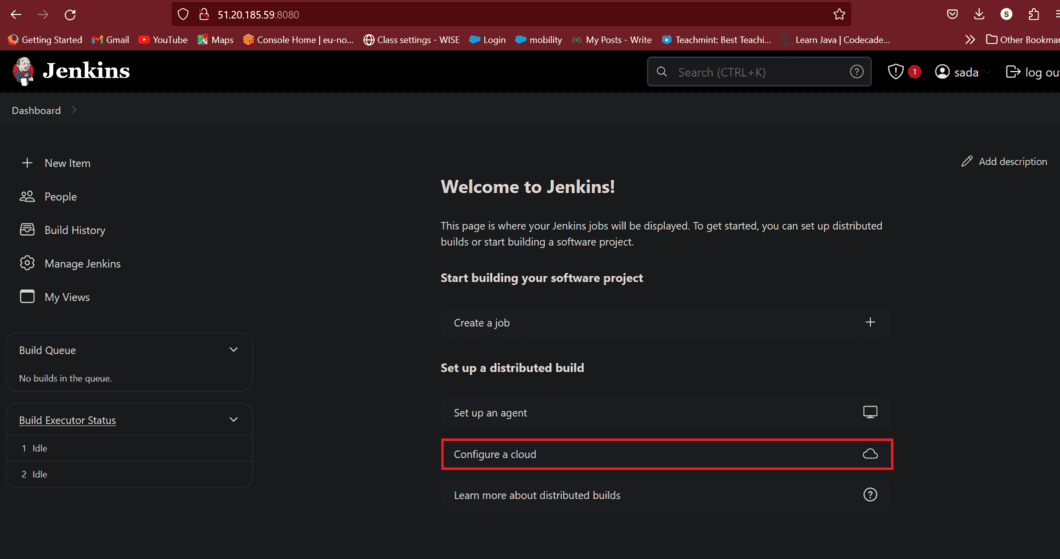
Step 5: Configure a Cloud
- Now go to jenkins dashboard choose configure a cloud
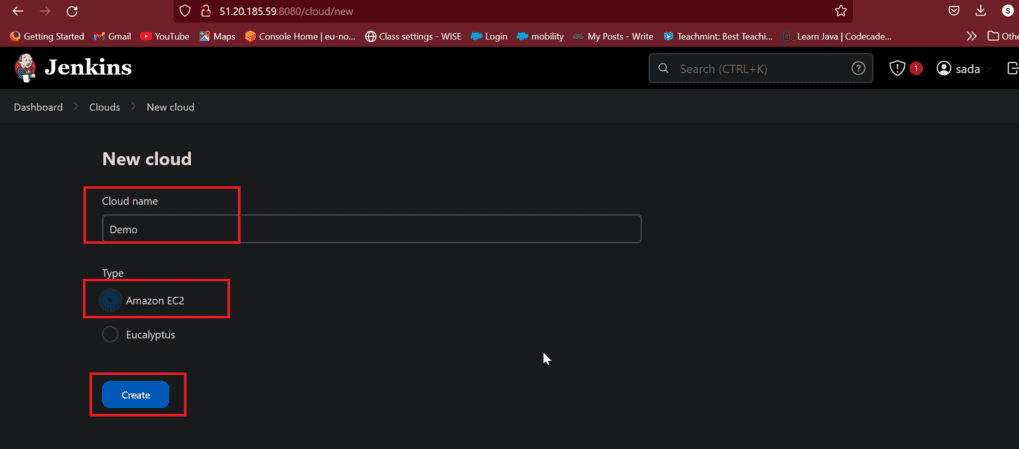
- Give cloud name and cloud type choose Amazon EC2 and click on create. Because previously we installed a plugin Amazon EC2.
- Here we are providing Amazon EC2 Credentials, Without this credentials we cannot access our AWS console. This Credentials are acts as a permissions.
- Now click on add
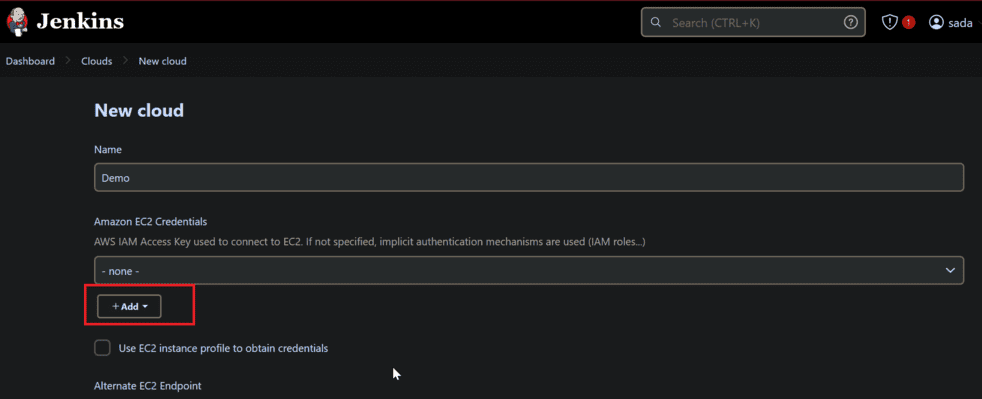
- There is a option is Kind, In this dropdown options select AWS Credentials
- Now ID name and description
- Provide your AWS Access key and Secret key in Access key section and Secret key section and click on add.
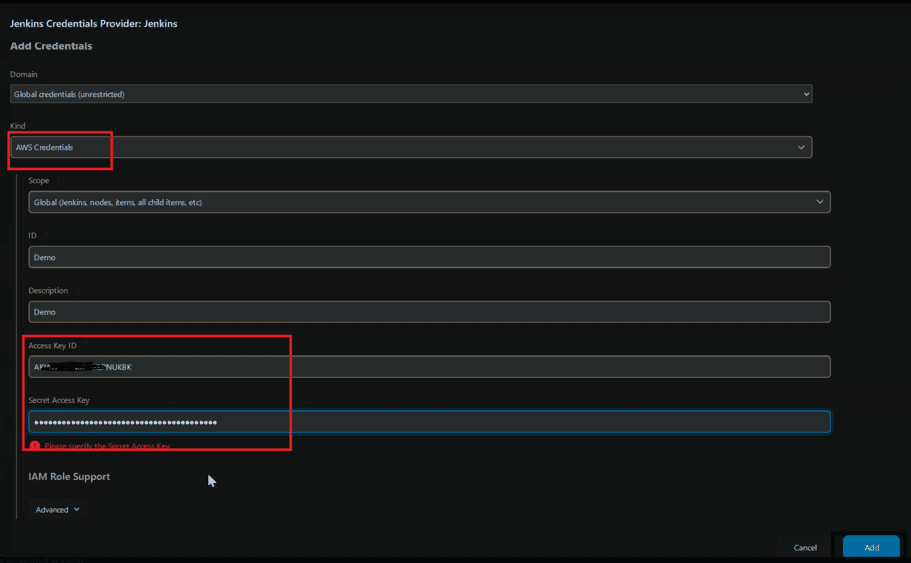
- Now add alternate EC2 endpoint, That ,means used to populate more available regions easy to find
- Now add our instance availability zone in dropdown box and add EC2 key pairs private Key, click on add
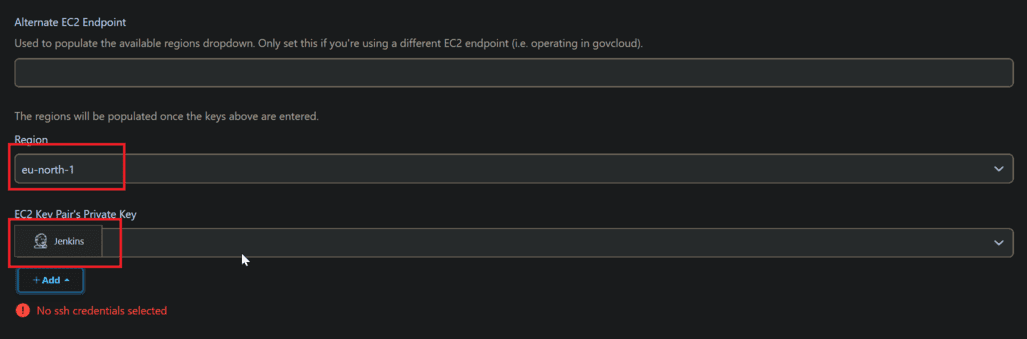
- There is an section name is KIND in that select SSH username with private key, that means we are providing our private key.
- Give ID and description
- In username give as EC2-user because we are using Amazon linux. If in case your using Ubuntu then give as ubuntu
- In private key provide keypair credentials. It can be downloaded when we launching EC2 Instance.
- Now test connection whether we are provided correct details or not. There is an option test connection click on it.
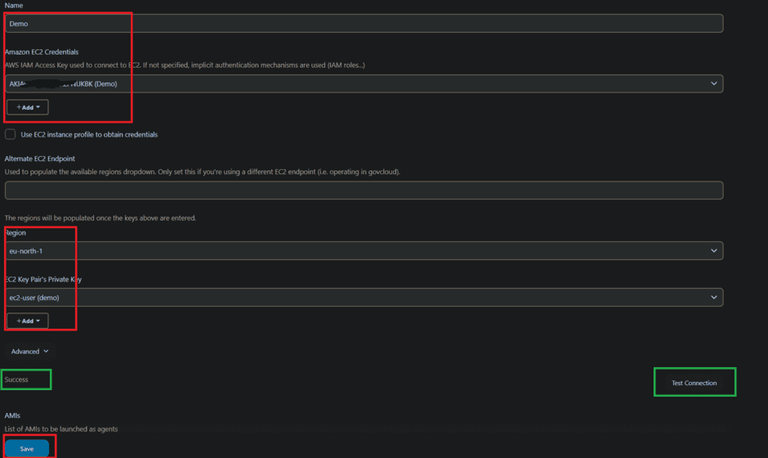
Here we see successfully our cloud network added
Step 6: Create Pipeline
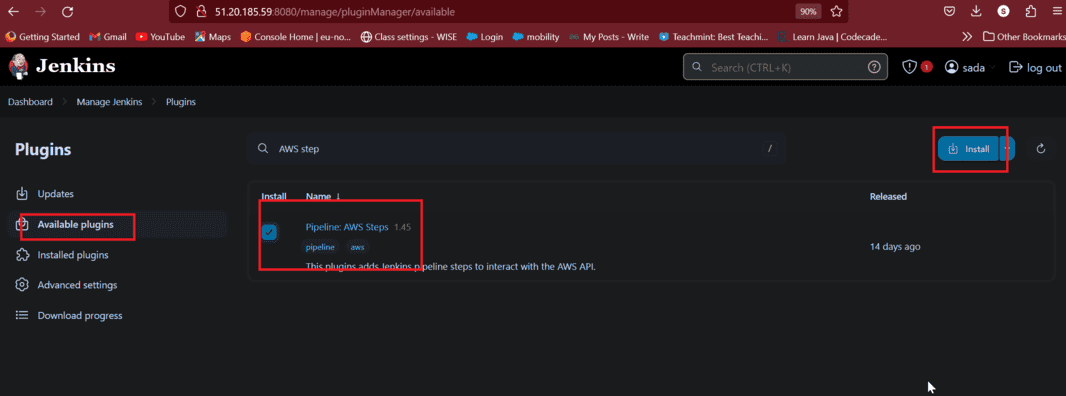
- Before going to create a pipeline we need to install one plugins that called Pipeline AWS Steps
- Click on Manage jenkins then click on Plugins, Then click on AWS Steps, Click on Install as shown image below
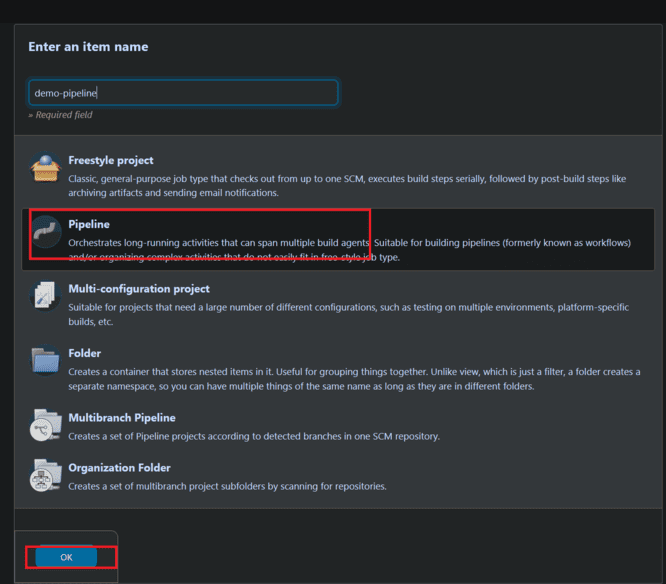
- Now go to dashboard and select create new job
- Give name to pipeline and select pipeline
- Now give description to pipeline it is optional there is no problem either given or not.
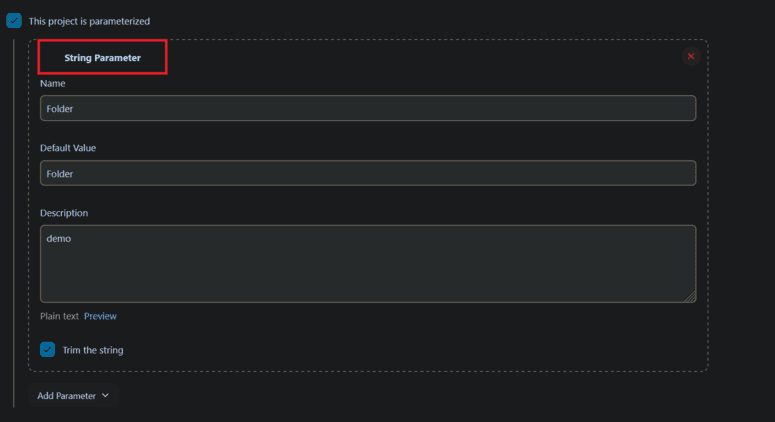
- Choose this project is parameterized
- In String Parameter give name and description
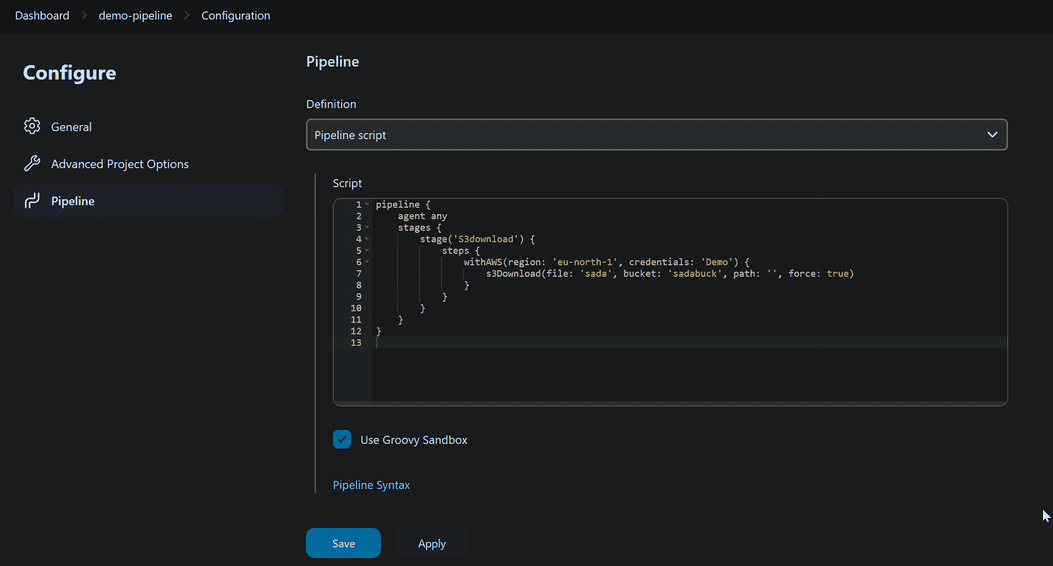
- In pipeline provide script to run pipeline
- Here we are written a script to download S3 bucket data from AWS Console by using automation.
pipeline {
agent any
stages {
stage('S3download') {
steps {
withAWS(region: 'us-east-1', credentials: 'your-credentials-id') {
s3Download(file: 'filename', bucket: 's3bucket', path: '', force: true)
}
}
}
}
}
Now build the pipeline,
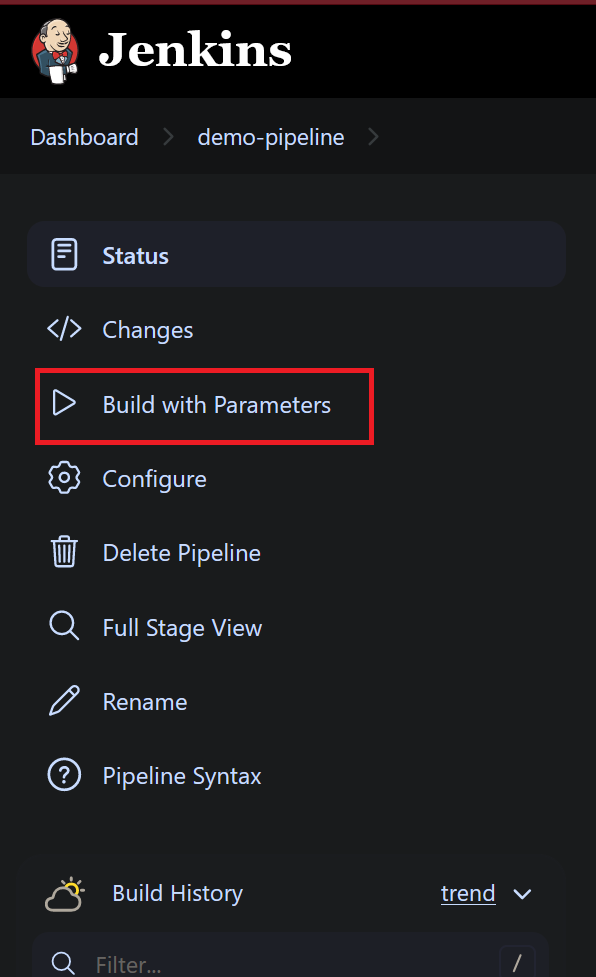
- Here we see that our pipeline build successfully
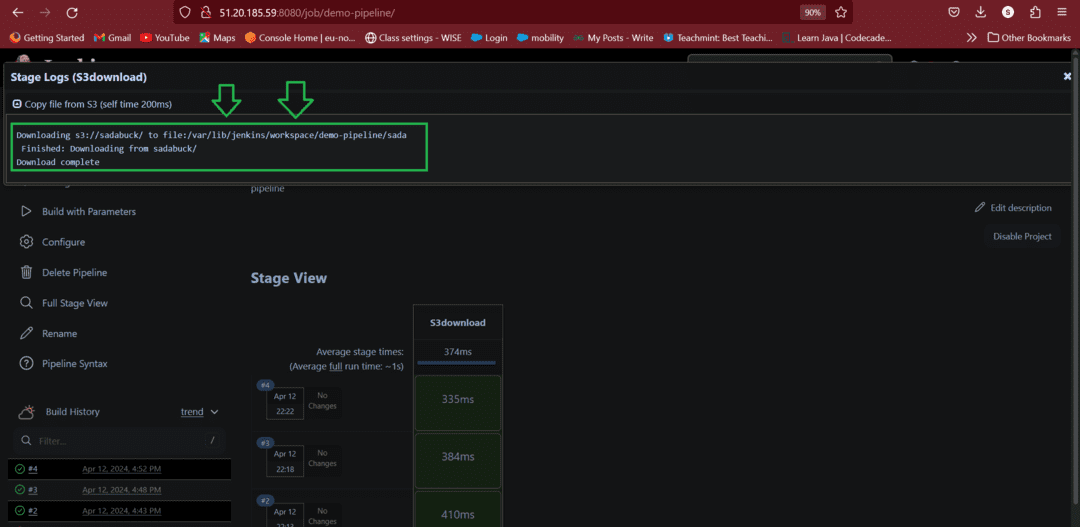
- After successfully completions of pipeline build. See they Stage Logs it downloaded data from S3 bucket which is present in my AWS S3 Bucket.
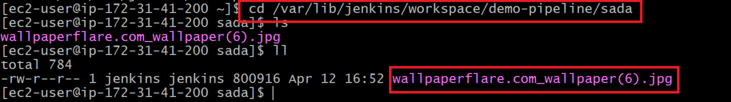
- We can check this in terminal by using provided path
Step 7: Verify
- Now connect with terminal and follow provided path
Conclusion
Integrating AWS credentials into Jenkins pipelines is significant for safely getting to AWS administrations inside CI/CD work processes, by following the means illustrated in this guide, clients can successfully oversee and use AWS credentials in Jenkins pipelines while sticking to security best practices. Firstly, adding AWS credentials to Jenkins includes safely putting away access keys in Jenkins credentials, ensuring that delicate data stays secured, these credentials can then be gotten to inside pipeline scripts utilizing the with Credentials block, taking into account consistent mix with AWS services.
When AWS credentials are configured, users can use different AWS services inside Jenkins pipelines, for example, deploying applications to EC2 instances, associating with S3 buckets, invoking Lambda capabilities, and that’s just the beginning, this empowers automated and smoothed out CI/CD processes, upgrading advancement proficiency and efficiency. Moreover, it’s fundamental for carry out appropriate safety efforts while managing AWS credentials in Jenkins pipelines, this incorporates confining authorizations to the base expected for each undertaking, routinely pivoting credentials, and observing access for any unapproved action, by following these security practices, associations can moderate the risk of credential abuse and unapproved admittance to AWS resources.
In general, coordinating AWS credentials into Jenkins pipelines enables improvement groups to construct, test, and convey applications consistently while keeping an elevated degree of safety and consistence, by utilizing the force of AWS services inside Jenkins pipelines, associations can speed up their product conveyance processes and drive advancement with certainty.
AWS Credentials in Jenkins Pipeline – FAQs
What are AWS credentials, and for hat reason would they say they are required in Jenkins pipelines?
AWS credentials comprise of access keys (access key ID and secret access key) used to confirm and approve admittance to AWS services. They are essential in Jenkins pipelines to associate with AWS services automatically, empowering automate deployment and management of AWS resources.
How would I safely store AWS credentials in Jenkins?
AWS credentials should to be put away safely in Jenkins credentials, which give a protected and unified area for delicate information. Keep away from hardcoding credentials straightforwardly into pipeline scripts to prevent accidental exposure.
Might I at any point involve IAM roles rather than access keys in Jenkins pipelines?
Yes, Jenkins pipelines can accept IAM jobs utilizing AWS Security Token Service (STS) to progressively acquire transitory qualifications, this approach wipes out the need to oversee long haul access keys and upgrades security by utilizing IAM jobs with granular consents.
How might I troubleshoot issues connected with AWS credentials in Jenkins pipelines?
If experiencing errors or issues with AWS credentials in Jenkins pipelines, check that the credentials are accurately designed in Jenkins credentials and that the proper consents are allowed. Check for any misconfigurations or grammatical mistakes in the pipeline script, and counsel AWS documentation or local area gatherings for additional help.
What safety measures would it be advisable for me to take while involving AWS credentials in Jenkins pipelines?
Continuously follow the standard of least honor by relegating just the fundamental permissions to AWS credentials. Consistently pivot access keys and monitor admittance to identify any unapproved action. Moreover, ensure that credentials are sent safely and never uncovered in plaintext.
Share your thoughts in the comments
Please Login to comment...