Types of Cyber Attacks
Last Updated :
14 Mar, 2023
Cyber Security is a procedure and strategy associated with ensuring the safety of sensitive information, PC frameworks, systems, and programming applications from digital assaults. Cyber assaults is general phrasing that covers an enormous number of themes, however, some of the common types of assaults are:
- Altering frameworks and information existing in it
- Abuse of assets
- Unapproved access to framework and getting to delicate data
- Jeopardizing typical working of the business and its procedures
- Utilizing ransomware assaults to scramble information and coerce cash from casualties
The assaults are currently turning out to be increasingly inventive and complex that is equipped for disturbing security and hacking of frameworks. So it’s tiring for the business and security expert to defend against these assaults.
As indicated by Accenture’s 2019 “Cost of Cybercrime” study, there has been a 67 percent expansion in security attacks in the course of most recent five years. The absolute estimation of danger emerging from these digital wrongdoings is pegged at USD 5.2 trillion throughout following five years. The intentions of hoodlums can be as straightforward as acquiring your budgetary subtleties and as deadly as breaking data sets containing basic individual recognizable data (PII) of clients, assaulting the foundation to spread malware, and so forth. It will be appropriate to examine significant classifications of cyber attacks, and why a one-size-fits-everything approach doesn’t help in countering them. Some basic Cyber attacks are:
1. Phishing: Phishing is a fraudulent action of sending spam emails by imitating a legitimate source. At its center, phishing abuses human motivations through alluring message or offer. Aggressors as a thumb of rule resort to phishing assaults by focusing on huge gatherings and subsequently increase the odds of probably few targets succumbing to assault. A commonplace case of phishing assault includes aggressor mimicking individual or foundation and sends messages to clueless targets requesting prompt assistance with connection appended to correspondence. Unaware client taps on connection, which takes them to phony site that appears to be like real site. Individual, uninformed of snare, falls into it and winds up offering individual subtleties to aggressor, who at that point ransacks client even before they understand that they have been assaulted.
Social Engineering Attacks
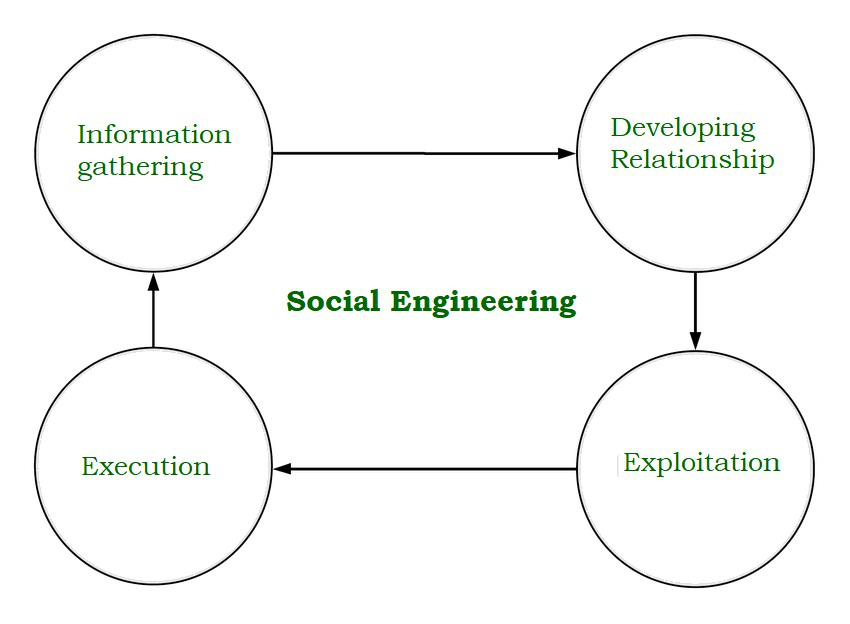
Social engineering is now common tactics used by cybercriminals to gather user’s sensitive information.
Social engineering assaults come in wide range of structures and can be performed in any place where human collaboration is included. Coming up next are five most basic types of advanced social engineering attacks. Social engineering assaults occur in at least one stage. A culprit initially researches proposed casualty to accumulate fundamental foundation data, for example, likely purposes of passage and feeble security conventions, expected to continue with assault. At that point, assailant moves to pick up casualty’s trust and give upgrades to resulting activities that break security rehearses, for example, uncovering sensitive data or allowing admittance to basic assets. Most berated type of bedeviling utilizes physical media to scatter malware. For instance, aggressors leave trap—regularly malware-tainted glimmer drives—in prominent territories where potential casualties are sure to see them (e.g., restrooms, lifts, the parking garage of a focused on organization). Snare has credible look to it, for example, name introducing it as organization’s finance list.
2. Ransomware: Ransomware is a document encryption programming program that utilizes a special encryption calculation to scramble records on objective framework. It is particular malware disseminated to blackmail cash from targets and is one of most pervasive and known instances of cyber attacks. Assailant disseminates malware as infection to get to objective PC’s hard drive. It, at that point, encodes information and makes PC/information unusable for client until they make the payoff installment requested by assailant. It is frequently difficult to decode record’s substance without anyone else. WannaCry and Maze ransomware are ongoing instances of how malware could unleash devastation, driving numerous enterprises to dish out bitcoins and cash to pay for recovering their undermined machines and information.
3. Cryptocurrency Hijacking: As digital currency and mining are becoming popular, also it is among cyber criminals. They have found their evil benefit to crypto-currency mining which involves complex computing to mine virtual currency like Bitcoin, Ethereum, Monero, Litecoin so on.
Hackers have two primary ways to get victim’s computer to secretly mine cryptocurrencies. One is to trick victims into loading crypto mining code onto their computers. This is done through phishing-like tactics: Victims receive legitimate-looking email that encourages them to click on link. Link runs code that places crypto mining script on the computer. Script then runs in background as the victim works.
The other method is to inject script on website or ad that is delivered to multiple websites. Once victims visit website or infected ad pops up in their browsers, script automatically executes. No code is stored on the victims’ computers. Whichever method is used, code runs complex mathematical problems on victims’ computers and sends results to server that hacker controls.
Hackers often will use both methods to maximize their return. “Attacks use old malware tricks to deliver more reliable and persistent software [to the victims’ computers] as fallback, ” says Alex Vaystikh, CTO and cofounder of SecBI. For example, of 100 devices mining cryptocurrencies for hacker, 10% might be generating income from code on the victims’ machines, while 90% do so through their web browsers.
Some crypto mining scripts have worming capabilities that allow them to infect other devices and servers on network. It also makes it harder to find and remove; maintaining persistence on network is in the cryptojacker’s best financial interest.
4. Botnets Attacks:
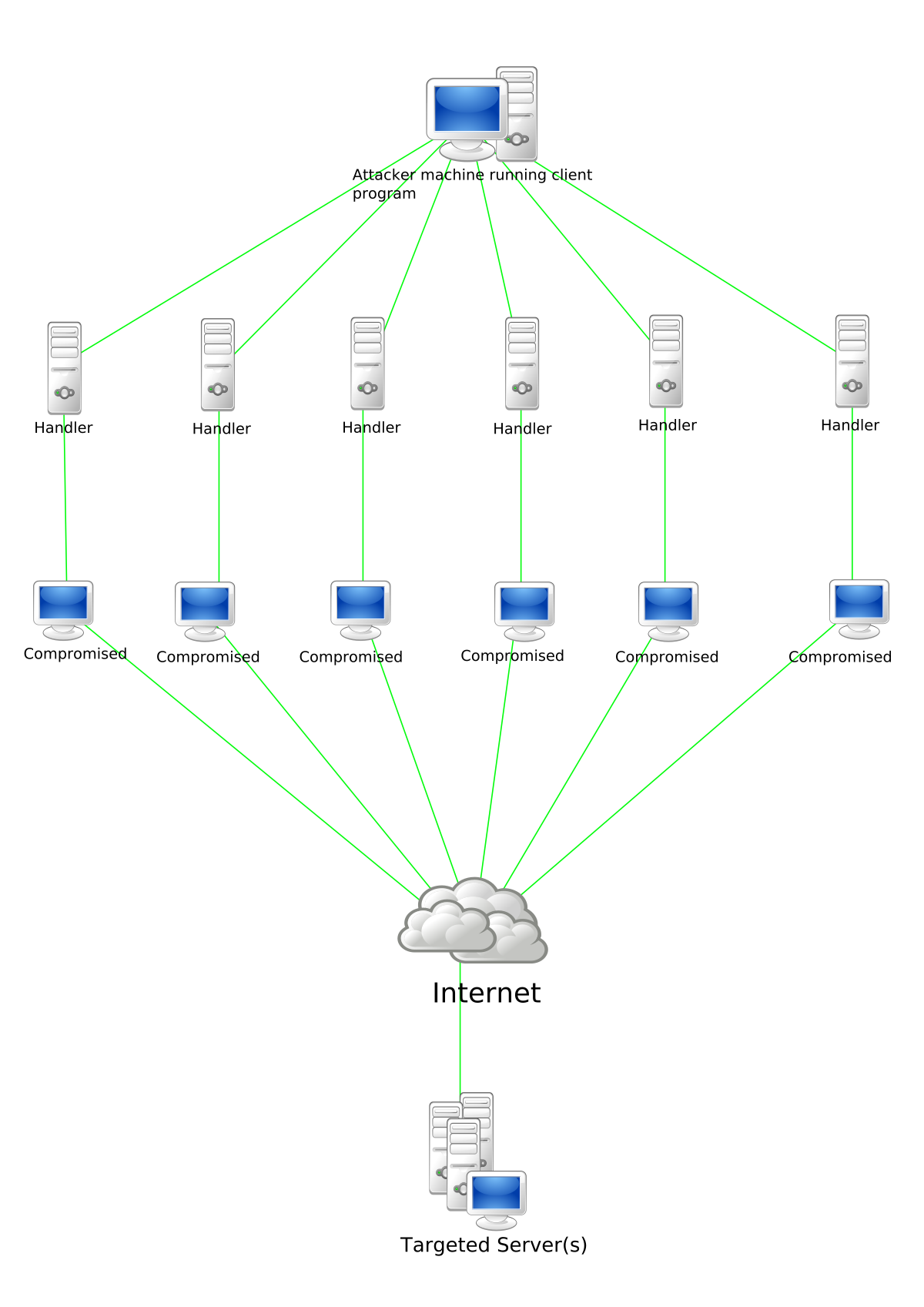
Botnets assaults are commonly targeted against huge-scope organizations and associations because of the immense information get to. Through this assault, the programmers can control countless gadgets and bargain them for their shrewd intentions.
Botnet proprietors can approach few thousand PCs all at once and can order them to do malignant exercises. Cybercriminals at first access these gadgets by utilizing unique Trojan infections to assault the PCs’ security frameworks, before executing order and control programming to empower them to do malevolent exercises for huge scope. These exercises can be mechanized to empower however many synchronous assaults as would be prudent. Various kinds of botnet assaults can include:
- DDOS assaults that cause impromptu application personal time.
- Approving arrangements of spilled qualifications (certification stuffing assaults) prompting account takeovers
- Web application assaults to take information
- Giving aggressor admittance to gadget and its association with the organization.
In different cases, cybercriminals will offer admittance to the botnet network, now and again known as “zombie” organization, so different cybercriminals can utilize the organization for their own malevolent exercises, for example, actuating spam crusade.
How Do Cyber Attacks Impact Businesses and Individuals?
Cyber attacks can have significant consequences for businesses and individuals alike. Here are some impacts of cyber attacks:
- Financial Losses: Cyber attacks can result in financial losses for businesses and individuals, such as theft of credit card information, bank account details, and cryptocurrency.
- Loss of Reputation: Cyber attacks can damage a company’s reputation and erode the trust of its customers, leading to significant financial losses.
- Loss of Data: Cyber attacks can result in the loss of critical data, such as customer information, trade secrets, and intellectual property.
- Disruption of Services: Cyber attacks can disrupt critical services, such as healthcare and emergency services, which can have life-threatening consequences.
Preventing Cyber Attacks:
There are several measures that businesses and individuals can take to prevent cyber attacks, including:
- Installing and updating antivirus software and firewalls to prevent unauthorized access to computer systems and networks.
- Educating employees on how to recognize and avoid phishing attacks and other forms of cyber attacks.
- Using strong passwords and two-factor authentication to protect sensitive data.
- Regularly backing up data to protect against data loss.
Conclusion: Cyber attacks are a serious threat to businesses and individuals alike. They can result in significant financial losses, damage to reputation, and even life-threatening consequences. Understanding the different types of cyber attacks and implementing appropriate security measures can help businesses and individuals protect their assets and prevent cyber attacks from causing harm.
Share your thoughts in the comments
Please Login to comment...