ShonyDanza – Tool For Researching, Pen Testing, And Defending With The Power Of Shodan
Last Updated :
30 Jan, 2022
Shodan is a special search engine that collects data about the device connected to the internet. It is a beneficial tool for Bug Bounty Hunters, Penetration Testers, Hackers, and many security-related actors. We can use the CLI version of Shodan through the means of an automated tool named ShonyDanza. ShonyDanza is a tool that makes the use of Shodan easier by just entering the options and getting the results quickly. We can get the IP addresses, Host Information and also find exploits according to CVE. ShonyDanza tool is developed in the Python3 Language and is available on the GitHub platform.
Note: Make Sure You have Python Installed on your System, as this is a python-based tool. Click to check the Installation process: Python Installation Steps on Linux
Installation of ShonyDanza Tool on Kali Linux OS
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/fierceoj/ShonyDanza.git
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd ShonyDanza
Step 3: You are in the directory of the ShonyDanza. Now you have to install a dependency of the ShonyDanza using the following command.
sudo pip3 install -r requirements.txt
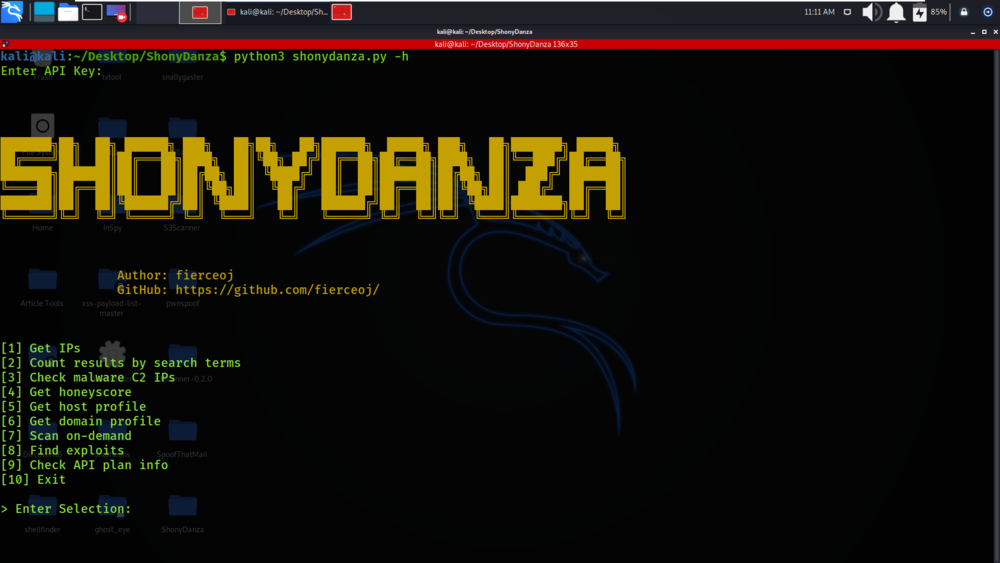
Step 4: All the dependencies have been installed in your Kali Linux operating system. Now use the following command to run the tool and check the help section.
python3 shonydanza.py -h
Working with ShonyDanza Tool on Kali Linux OS
Example 1: Search for IPs
Select Option 1
We will be retrieving the IP addresses by search terms.
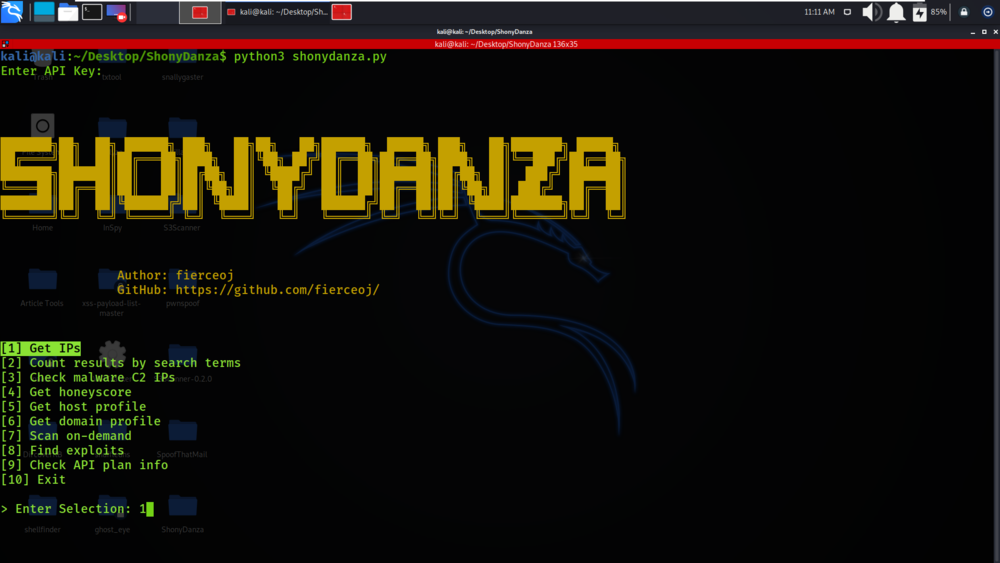
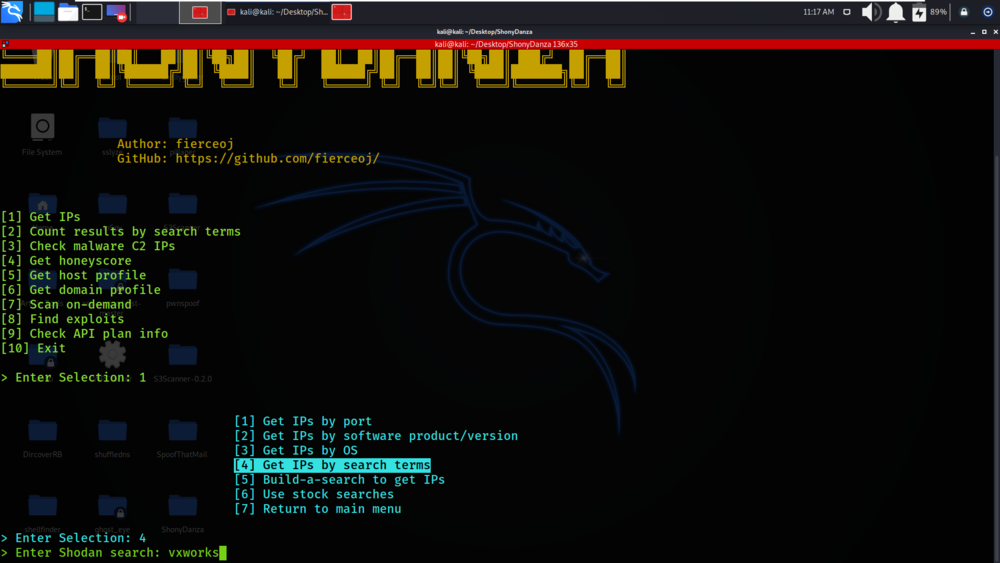
Select Option 4
We have given the search term as vxworks.
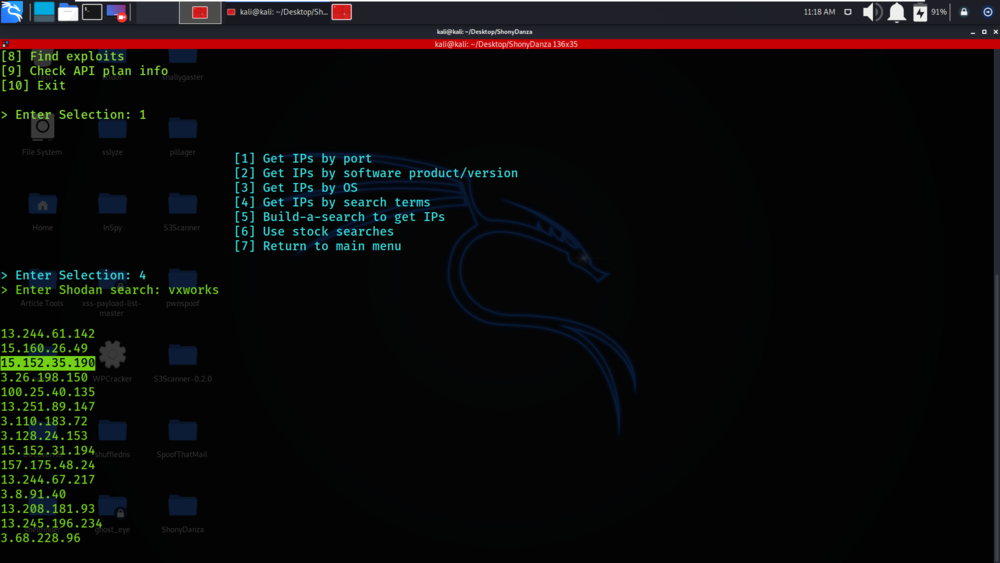
We have got the list of IP addresses that matches the search term.
Example 2: Get Host Profile
Select option 5
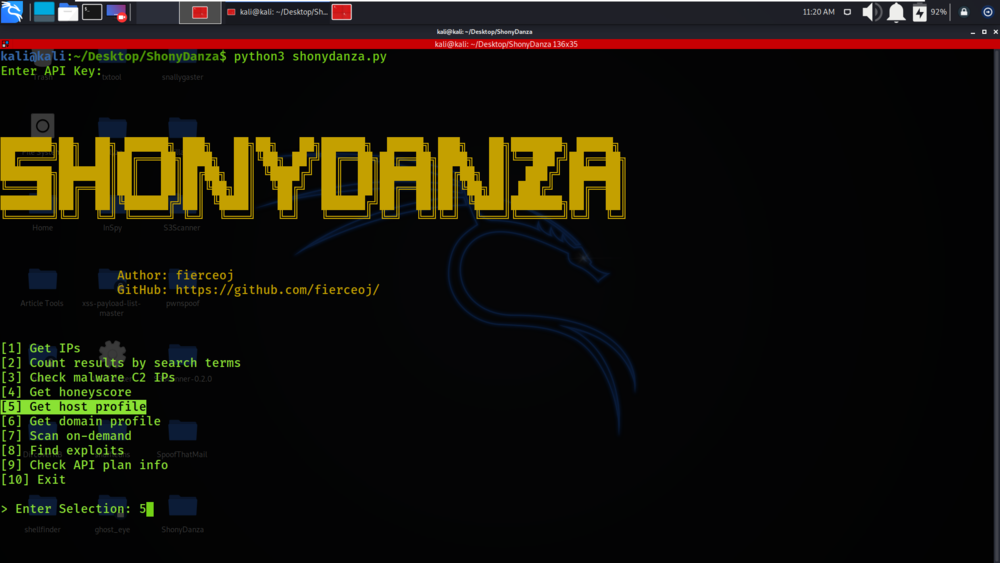
We have got the Host Information about the IP address which was inputted to the tool.
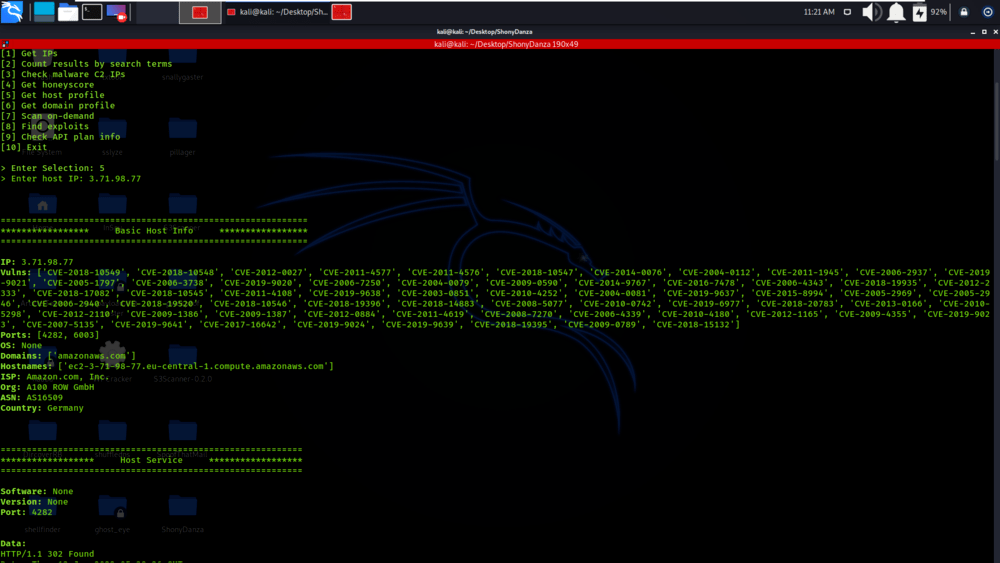
Example 3: Find Exploits
Select Option 8
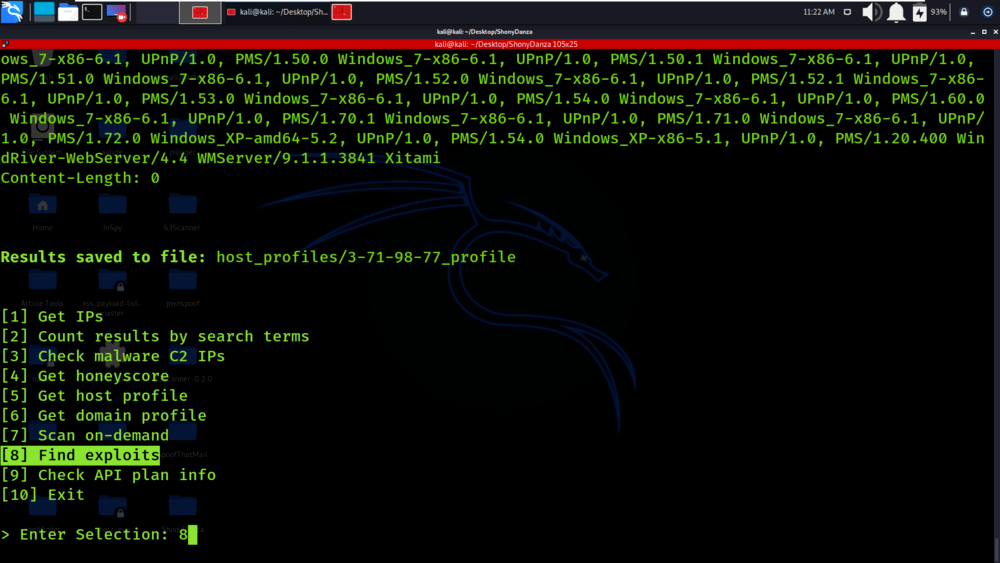
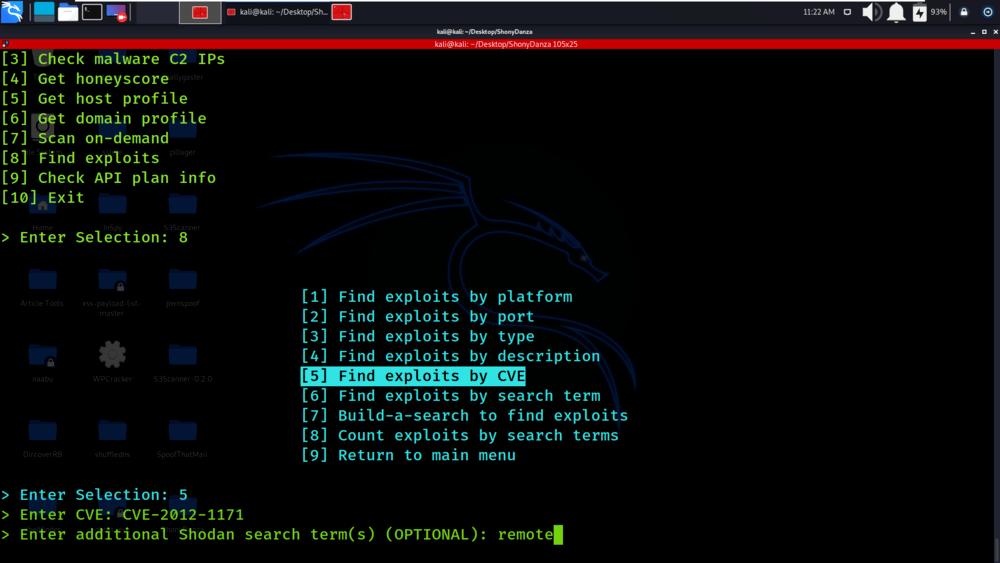
Select Option 5
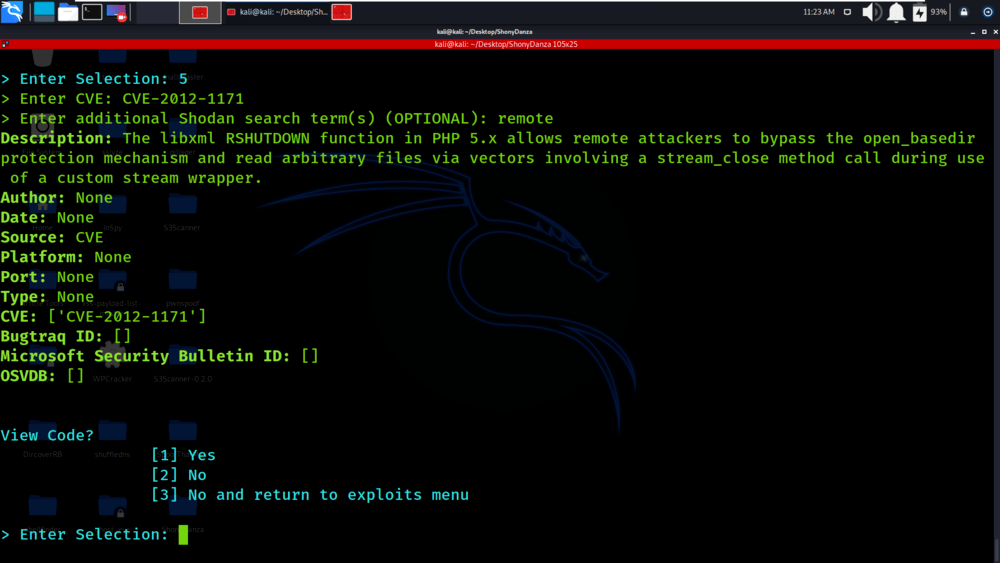
We have given the CVE name for which we need information.
We have got the details about the CVE which was passed as an input to the tool.
Share your thoughts in the comments
Please Login to comment...