Setup two-factor authentication (2FA/MFA) for Linux systems
Last Updated :
24 Oct, 2023
Two-factor authentication, or multi-factor authentication, is a technique or method of security that requires users to provide two different authentication factors before granting access to an account or system. These factors typically include something the user knows (like a password or PIN) and something the user possesses (like a smartphone or hardware token). 2FA adds an extra layer of security, making it more difficult for unauthorized individuals to access protected accounts or information.
So we will implement this two-factor authentication method on a Linux system.
Implementation
To implement the two-factor authentication technique, we have to follow the same procedure as listed here.
Prerequisite – VirtualBox or Vmware, Kali Linux, Ubuntu Linux.
Step 1: Install all the necessary setup and tools, and after that, open the terminal in your Kali or whatever virtual machine you have, such as Ubuntu Kali, CentOS 7, etc.
Step 2: To enable 2FA in our system, we will use the Google Authenticator Pam module. So for that, we will first install it using the below command, as shown here.
$ sudo apt-get install wget make gcc libpam0g-dev
.png)
Step 3: After that, you have to just enter the command of the Google authenticator and hit enter.
$ google-authenticator
.png)
Step 4: After that, it will ask you for some steps; you have to simply tap yes and move ahead. It will ask you to scan a QR code; for that, you have to install an application called Google Authenticator on your mobile phone and scan it.
.png)
Step 5: After scanning the code from the terminal, you will get the new code on your mobile phone. Just enter that code into the terminal for verification, which is generated by the Google Authenticator app.
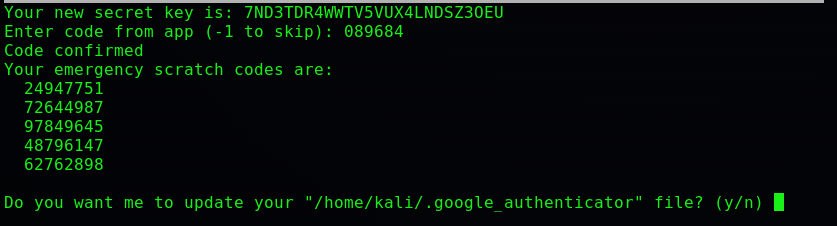
Step 6: After entering the code into the terminal, it will give you some emergency scratch codes that you can use when your mobile phone is not working to access the virtual machine. Kali uses two-factor authentication.
Once all the processes are done, they are successfully installed and configured in our system.
.png)
Step 7: To enable the 2FA in our SSH configuration, we have to just enter the below command. After that, using the nano editor, you have to just add this file and add one command in the nano editor. as a command below, then save that file.
$ sudo nano /etc/pam.d/sshd
.png)
Just go to the bottom of the nano editor file, write the command, save it, and exit.
$ auth required pam_google_authenticator.so
.png)
Step 8: Now you have to go to the SSH file configuration; for that, just put the below command. After hitting enter, you will see the interface like that, as shown below.
$ sudo nano //etc/ssh/sshd_config
.png) In this ssh nano file, you have to make some changes. Just scroll down the nano editor file, change the status from no to yes, and hit enter.
In this ssh nano file, you have to make some changes. Just scroll down the nano editor file, change the status from no to yes, and hit enter.
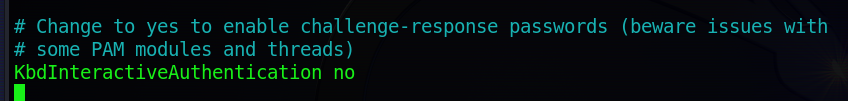
Change it to yes, press ctrl+o, save it, and exit the file.
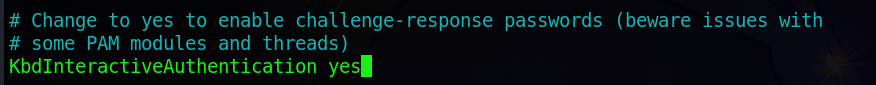
Step 9: After saving the file successfully, you have to restart the SSH server using this command.
$ sudo systemctl restart sshd.service
Once you start the ssh server, you have to just give the below command to initiate the localhost as-
$ ssh localhost@ip address
Then it will ask for your local host password, and after that, it will ask for a verification code that is known as the two-factor authentication code. You will successfully get access to SSH on Linux.
Conclusion
Overall, the implementation of two-factor authentication (2FA) or multi-factor authentication (MFA) in a Linux system is a crucial step towards enhancing security. This method adds an additional layer of protection by requiring users to provide two different authentication factors, typically something they know (like a password) and something they possess (like a smartphone or hardware token), before granting access to an account or system. It serves as a reliable deterrent against potential security threats, providing users with the confidence that their accounts and systems are well protected.
Share your thoughts in the comments
Please Login to comment...