Reconspider – Most Advanced Open Source Intelligence (OSINT) Framework
Last Updated :
21 Jul, 2021
ReconSpider can be used by information security researchers, penetration testers, bug hunters, and cybercrime detectives to gather extensive information on their target. It is the most powerful open-source intelligence (OSINT) platform for scanning IP addresses, emails, websites, and organizations to extract information from various sources.

Installation
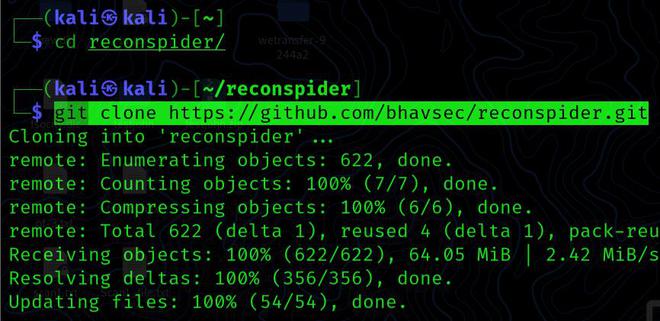
Step 1: Simply clone the Github repository to get ReconSpider. To effectively configure this tool, we first need to download it from the Github page using the commands listed below.
cd reconspider
git clone https://github.com/bhavsec/reconspider.git
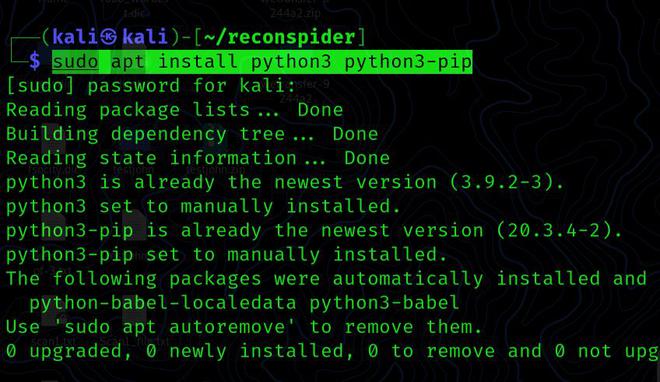
Step 2: Check that both python3 and python3-pip are installed on your system.
sudo apt install python3 python3-pip
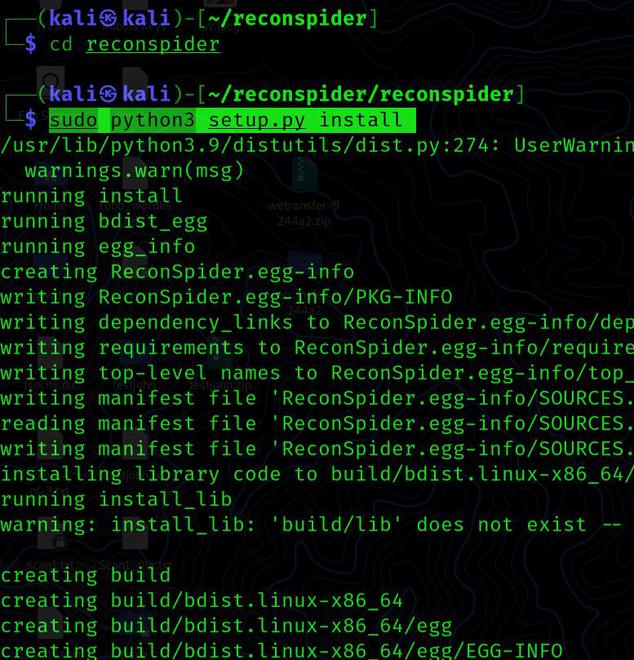
Step 3: When you clone and verify your Python installation, you will see a directory called reconspider. Now we navigate to the directory and run the command below to install this utility.
cd reconspider
sudo python3 setup.py install
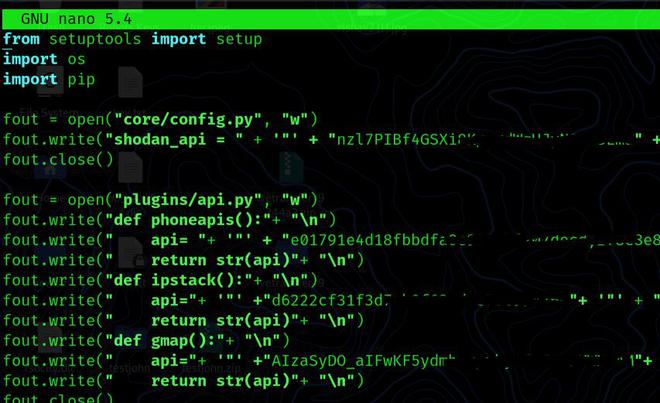
Creating API Keys and Adding Them
Before we can use this tool, we’ll need certain API keys. The APIs that we are currently using in this tool are listed below.
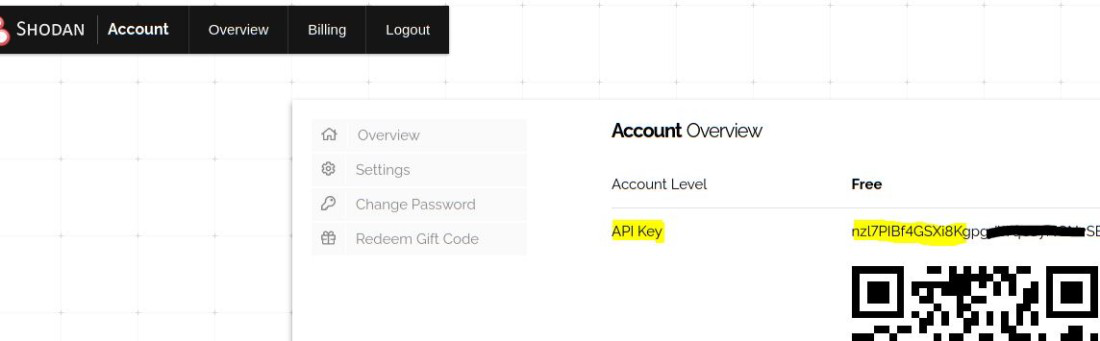
Shodan API: Create an account with Shodan and activate it. Copy the key and paste it into the config.py file in the modules directory once you’ve logged in.
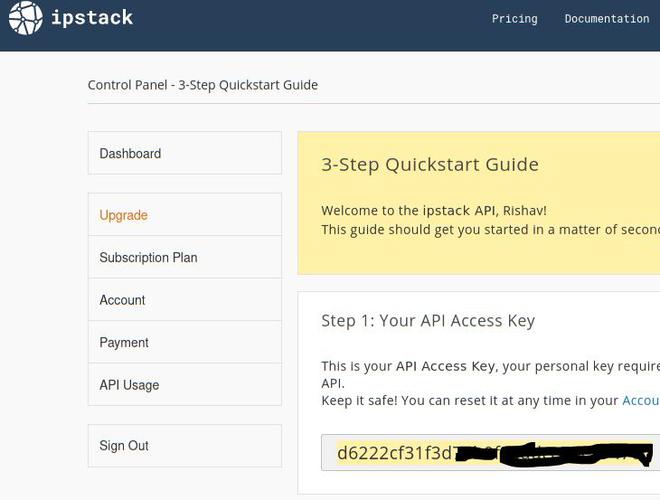
Ipstack: Create an account with Ipstack and activate it. Copy the secret API key and paste it into the config.py file in the modules directory once you’ve logged in.
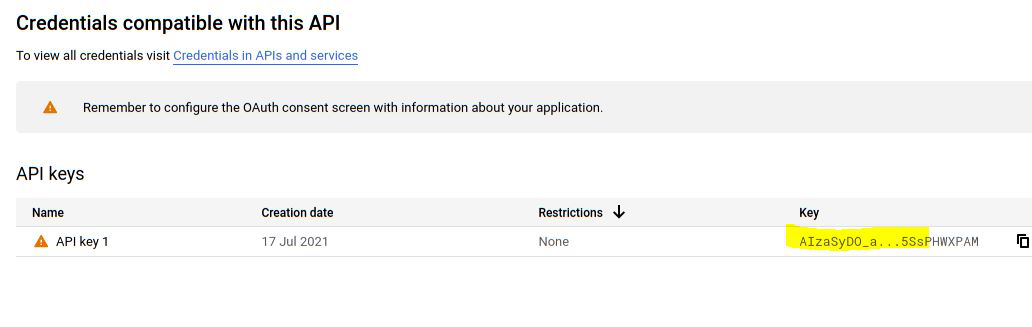
Gmap API: Gmap requires you to create an account and activate it. After logging in, click the [+ Generate New API Key] box, copy the key, and paste it into the modules directory’s config.py file.
Setup.py
Usage:
Now that we have completed all the settings and installation, we can use the Python program to launch this utility.
python3 reconspider.py
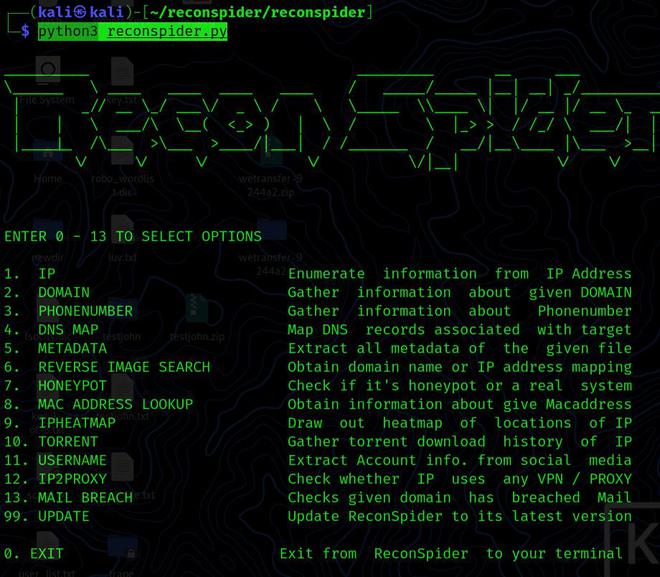
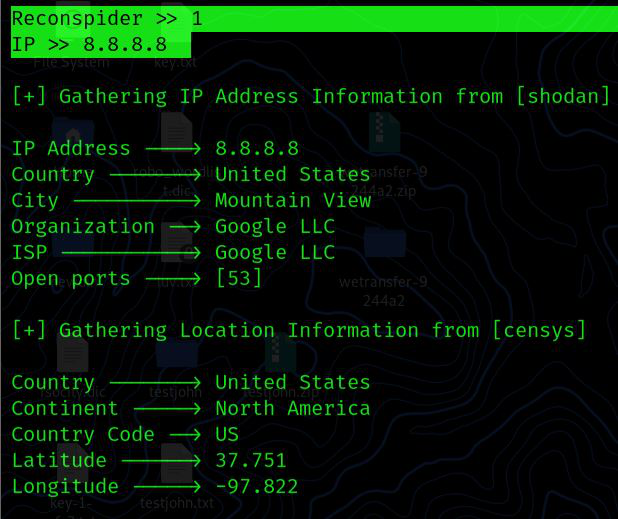
Enumerate IP Address: This option collects all information about a specific IP address from publicly available sources.
ReconSpider >> 1
IP >> 8.8.8.8
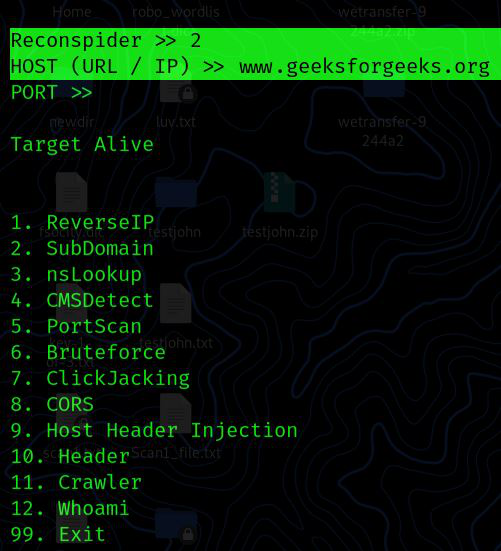
Domain Enumeration: Now we will try to get more information about the specific website. To do this, we’ll type “2” and then it will present us with all the features we can use.
Reconspider >> 2
HOST (URL / IP) >> geeksforgeeks.org
PORT >>
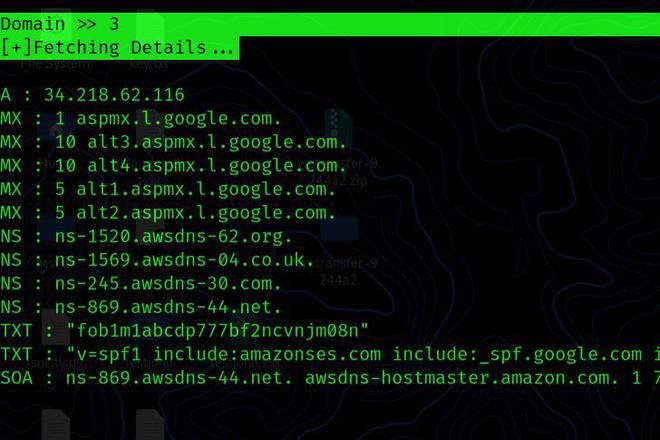
Nslookup: By providing the name of the website, an attacker can obtain a domain name or IP address mapping, or other DNS records.
Domain >> 3
[+]Fetching Details...
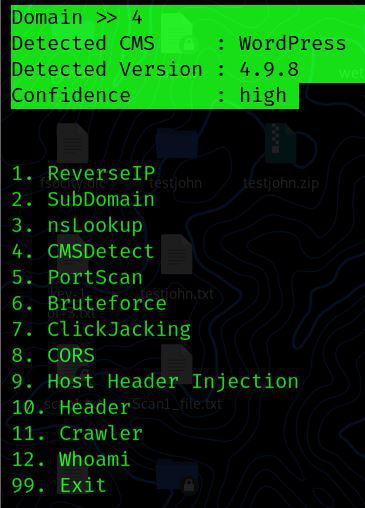
CMS Detection: We can use this approach to determine the platform the website is built on, and if a component or version is vulnerable, we can attack it.
Domain>> 4
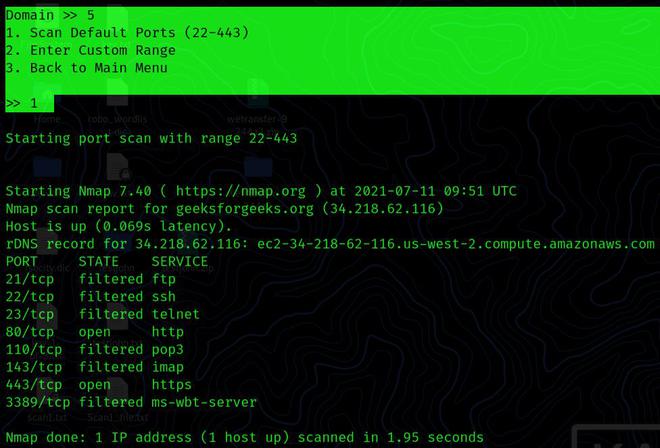
PortScan: This application provides port scanning features which can be useful for novices who want to perform port scanning against a live website.
Domain >> 5
1. Scan Default Ports (22-443)
2. Enter Custom Range
3. Back to Main Menu
>> 1
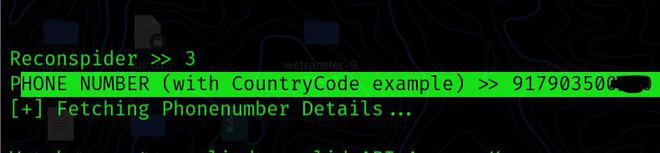
PHONE NUMBER: You may use this option to get information on a certain phone number.
Reconspider >> 3
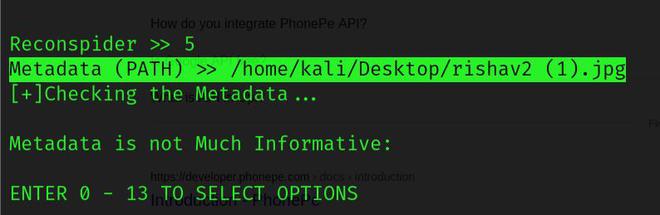
METADATA: You can use this option to remove the entire metadata of the file.
Reconspider >> 5
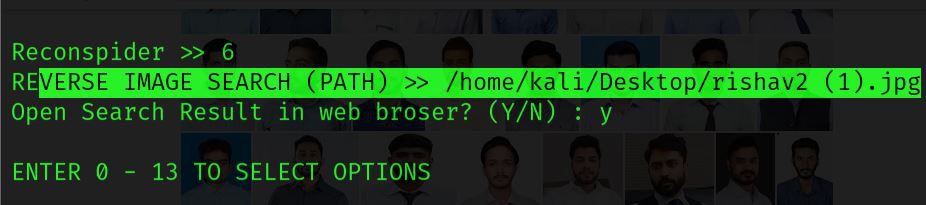
REVERSE IMAGE SEARCH: This option enables you to access information and images comparable to those found on the internet.
Reconspider >> 6
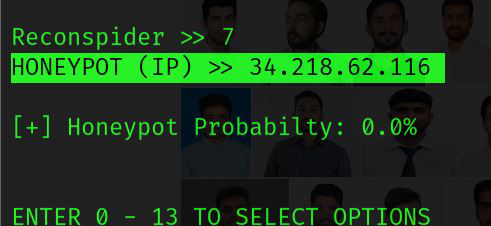
HONEYPOT: You can use this option to find honeypots! A “HoneyScore” number that can vary from 0.0 to 1.0 represents the probability that an IP address is a honeypot.
Reconspider >> 7
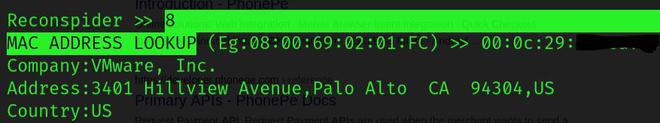
MAC ADDRESS LOOKUP: This option enables you to determine the manufacturer, address, country, and other information of a Mac address.
Reconspider >> 8
IPHEATMAP: If you link all of the supplied IP locations with the correct Coordinator, you’ll get a heatmap of the specified IP or single IP.
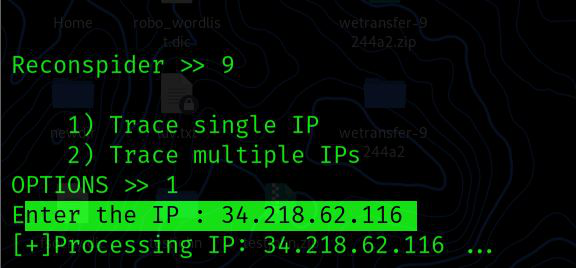
Reconspider >> 9
1) Trace single IP
2) Trace multiple IPs
OPTIONS >> 1
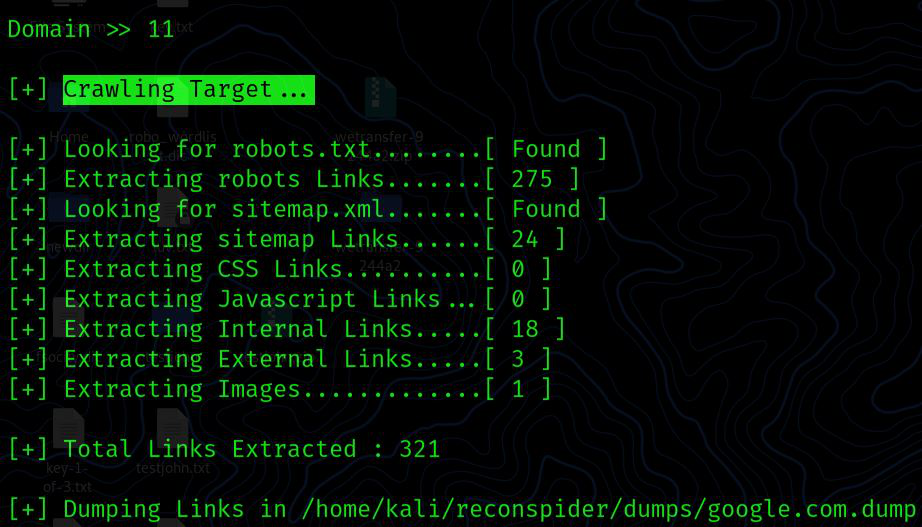
Crawling: Crawling is the process through which search engines dispatch a group of robots to look for fresh and updated material.
Domain >> 11
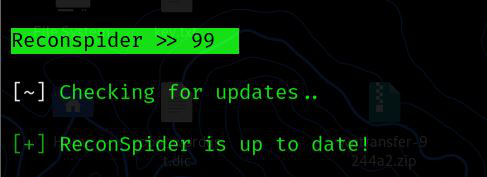
UPDATE: You can use this option to check for updates. If a new version becomes available, ReconSpider will download and integrate the changes into the current directory without overwriting any existing data.
ReconSpider >> 99
Checking for updates..
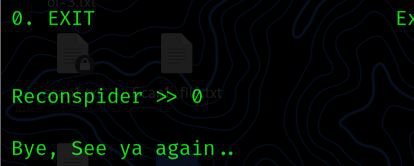
EXIT: This option allows you to exit the ReconSpider framework and return to your current operating system’s terminal.
ReconSpider >> 0
Bye, See ya again..
Share your thoughts in the comments
Please Login to comment...