Network Protocols and Proxies in System Design
Last Updated :
19 Feb, 2024
In the system design, the effective functioning of networks is essential for seamless communication and data transfer. Network protocols and proxies play important roles in shaping the structure of the system, ensuring efficient data transmission, and improving security. This article explores the significance of network protocols and proxies in system design, their roles, and how they contribute to the overall functionality and security of a system.

Important Topics for the Network Protocols and Proxies in System Design
What are Network Protocols
Network protocols are a set of rules and conventions that initiate the communication and data exchange between different devices in a network. They define the standards for data encoding, transmission, and reception, ensuring that devices can understand and interpret each different’s messages. Common network protocols mainly include Transmission Control Protocol (TCP), Internet Protocol (IP), Hypertext Transfer Protocol (HTTP), etc.
Importance of Network Protocols in System Design
Network protocols act as a foundation for system design by using a standardized set of rules and conventions for communication between devices in a network. The importance of network protocols in system design consists of:
- Interoperability: Network protocols permit devices from different manufacturers and with various functionalities to communicate seamlessly, which promotes interoperability.
- Reliability: Protocols like TCP ensure reliable and ordered data transmission, which is crucial for applications that require data integrity, consisting of file transfers and email communication.
- Efficiency: Protocols optimize data transmission, minimizing latency and packet loss, contributing to the overall performance and responsiveness of networked applications.
- Scalability: Well-designed protocols allow for the scalability of the system, and give a boom in data traffic and the several connected devices without compromising in overall performance of the system.
- Security: Security protocols like SSL/TLS encrypt data during transmission, protect sensitive data from unauthorized access, and ensure the confidentiality of communications.
Commonly Used Network Protocols in System Design
1. Transmission Control Protocol (TCP)
.webp)
- Role: TCP (Transmission Control Protocol) is one of the core protocols of the Internet Protocol Suite (commonly known as TCP/IP). It provides reliable, connection-oriented communication between devices on a network. TCP operates at the transport layer of the OSI (Open Systems Interconnection) model and is responsible for ensuring that data packets are delivered reliably and in order from the sender to the receiver.
- Functionality: It establishes a connection earlier than data transfer, ensures the receipt of packets, and retransmit it if there is any loss or corrupted data.
- Use Cases: TCP is widely used in application where data integrity and sequencing are critical, along with data transfers, e-mail delivery, and web browsing.
2. Internet Protocol (IP)
.webp)
- Role: IP is responsible for addressing and routing packets throughout networks.
- Functionality: It assigns a completely unique IP address to each device and determines the best suitable path for data packets to reach their destination.
- Use Cases: IP is fundamental to all networked systems and is used together with other protocols for data transmission.
3. User Datagram Protocol (UDP)
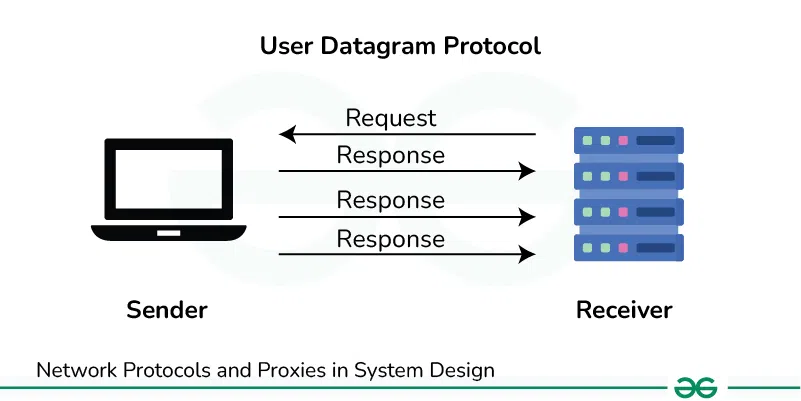
- Role: UDP is a core protocol of the Internet Protocol Suite, operating at the transport layer like TCP. Unlike TCP, which provides reliable, connection-oriented communication, UDP is a simpler, connectionless protocol that offers minimal services. UDP is often referred to as a “fire-and-forget” protocol because it does not guarantee delivery or order of packets, nor does it provide error checking or flow control mechanisms.
- Functionality: Unlike TCP, UDP does not set up a connection before the data transfer and also it does not provides any guarantee for packet delivery or sequencing.
- Use Cases: UDP is typically used in real-time applications like VoIP, online gaming, and live video streaming, where low latency is important.
Hypertext Transfer Protocol (HTTP) and HTTPS
- Role: HTTP is used for transferring hypertext files at the World Wide Web.
- Functionality: It defines how messages are formatted and transmitted between differnet web servers and clients.
- Use Cases: HTTP is used in web browsers to retrieve and display web pages. HTTPS adds a layer of security through encryption the usage of SSL/TLS.
-and-HTTPS.webp)
Secure Socket Layer/Transport Layer Security (SSL/TLS)
- Role: SSL/TLS protocols provide stable and secure connection for information exchange between different device on a computer network.
- Functionality: They encrypt information during transmission, making sure confidentiality and integrity.
- Use Cases: SSL/TLS is used for secure data transmission over the web server, which include online banking transactions, e-commerce transactions, and email communication.
4. File Transfer Protocol (FTP)
.webp)
- Role: FTP is used for transferring documents between a client and a server on a computer network.
- Functionality: It allow user to upload , download, and manipulate files on remote servers.
- Use Cases: FTP is commonly used for website maintenance, software distribution, and file sharing between different users.
5. Simple Mail Transfer Protocol (SMTP) and Post Office Protocol (POP3/IMAP)
- Role: SMTP is used for sending electronic mail messages, while POP3 and IMAP are used for receiving electronic mail messages.
- Functionality: SMTP transfers outgoing mail from a user to a server, even as POP3 and IMAP retrieve incoming mail from a server to a user.
- Use Cases: SMTP, POP3, and IMAP are crucial for e mail communication and are extensively utilized in e mail clients and mail servers.
Proxy Servers
A proxy server acts as an intermediary between client devices and servers, facilitating communication through forwarding requests and responses. It intercepts traffic between client and destination, offering several functionalities to enhance overall network performance, protection, and privacy.

Purpose of Proxy Servers
- Content Filtering: Proxies can filter out content based on differnet policies, blockading access to particular websites or content categories. This is critical for implementing applicable use policies in businesses, prevents access to malicious content material.
- Privacy and Anonymity: Forward proxies masks the IP addresses of client devices, provides a degree of anonymity all throughout web surfing. This is especially beneficial for users who want to cover their identification or location.
- Security and Access Control: Proxies make contributions to network security by examining and filtering incoming traffic. They can block malicious content, filter out dangerous websites, and enforce access to manipulate rules, preventing unauthorized access to sensitive resources.
- Load Balancing: Reverse proxies distribute incoming traffic across more than one servers to optimize resource utilization. This load balancing ensures that no single server is overloaded, enhancing performance and preventing service disruptions.
- Caching: Proxies, in particular caching proxies, keep copies of frequently accessed resources locally. This reduces the load on origin servers, faster the content delivery process, and also improves response time for clients.
- Forward proxy: Forward proxies are used to send data to user groups within the internal network. The proxy server evaluates the information given with the request to determine if it should proceed with establishing a connection.
- Reverse Proxy Server: The job of a reverse proxy server to listen to the request made by the client and redirect to the particular web server which is present on different servers.
- Web Proxy Server: When an HTTP request is forwarded via a web proxy, only the URL is sent instead of its path . A particular proxy server receives the request and respondes. HAP Proxy and Apache are two examples.
- Public proxy: Anyone can access public proxies, which function by giving their users their IP address in order to hide their identity. Even if this proxy is cheap and simple to use, still users are more vulnerable to data breaches.
Advantages of Proxy Servers
The advantages of proxy servers are as follow:
- Enhanced Security: Proxies act as a barrier between client and the internet, filtering out malicious content and imparting an extra layer of defense towards cyber threats.
- Improved Performance: Caching mechanisms in proxies boost up content delivery by means of storing regularly accessed data locally, reducing the need to fetch resources from the origin server.
- Content Control: Proxies allow administrators to manipulate and filter out the content that users can access, imposing utilization policies and retaining a secure and efficient environment.
- Load Balancing: Reverse proxies distribute incoming visitors across a couple of servers, optimizing resource usage, and ensure high availability.
Disadvantages of Proxy Servers
The disadvantages of proxy servers are as follow:
- Latency: Introducing a proxy can add latency to the communication between user and servers, impacting the reaction time, in particular for real-time application.
- Configuration Complexity: Setting up and handling proxy servers may be complicated, requiring knowledge of networking and security to make certain proper configuration and to increase overall performance.
Role of Network Protocols and Proxies in System Architecture
In system architecture, Network protocols and proxies play pivotal roles in shaping the communication, provides performance, security, and overall functionality.
- Communication Facilitation: Network protocols allow system to communicate seamlessly through defining the guidelines and conventions for data exchange, ensuring reliable and ordered transmission.
- Performance Optimization: Proxies contribute to performance optimization by caching frequently accessed data locally, reducing server load, and enhancing content delivery speed.
- Security Enhancement: Network protocols includes SSL/TLS to make sure secure data transmission, and at the same time proxies act as intermediaries, filtering out malicious traffic and adding an additional layer of protection.
- Anonymity and Privacy: Forward proxies provide anonymity via protecting user IP addresses, and contributing to more privacy during web surfing.
Integration of Network Protocols in System Design
Integration of network protocols includes incorporating them into the system design to make sure seamless communication and data exchange. Considerations for integration encompass:
- Compatibility: Ensure that selected protocols are like compatible with the system’s necessities and supports desired functionalities.
- Interoperability: Design the machine to guide interoperability through selecting protocols that facilitate communication between different components and systems.
- Scalability: Select protocols that permit for scalable solutions, giving potential growth and increase in data traffic.
- Security Measures: Integrate protocols with robust protection functions, including encryption and authentication, to protect sensitive data.
Considerations for Selecting Protocols and Proxies in System Design
- Nature of Application: Choose protocols based on the particular requirements of the application.
- Security Requirements: Evaluate the extent of security required and pick protocols and proxies that align with the system’s security rules.
- Performance Demands: Consider the performance demands of the system and pick protocols accordingly that optimize data transfer speed and reduce latency.
- Resource Efficiency: Opt for protocols and proxies that maximize resource efficiency, minimizing the effect on system resource and ensuring optimal performance.
- Ease of Implementation and Maintenance: Assess the benefit of implementation and maintenance, choosing on protocols and proxies that align with the skillset and resources available for the development to operations teams.
Proxy Server Implementation Strategy
Proxy servers play a essential function in optimizing network overall performance, improving protection, and enhancing user experience.
- Reverse Proxy vs. Forward Proxy:
- Reverse Proxy: Used to intercept requests from clients and forward them to a server. Often deployed in front of web servers to improve performance, security, and scalability.
- Forward Proxy: Used to intercept requests from clients and forward them to the internet. Typically used to control access, monitor traffic, and improve performance.
- Proxy Server Software:
- Choose a proxy server software that fits your needs. Popular options include Nginx, Apache HTTP Server, Squid, HAProxy, and Varnish.
- Consider factors such as performance, scalability, features, community support, and compatibility with your existing infrastructure.
- Deployment Architecture:
- Determine whether you need a centralized or distributed proxy server architecture.
- Centralized architecture involves a single proxy server handling all requests.
- Distributed architecture involves multiple proxy servers distributed across different locations to handle requests more efficiently and provide redundancy.
- Load Balancing:
- If you have multiple proxy servers, implement load balancing to distribute incoming traffic evenly across them.
- Load balancing can be achieved using software-based solutions like Nginx or hardware-based load balancers.
- Authentication and Authorization:
- Implement authentication mechanisms to control access to the proxy server.
- Use techniques like Basic Authentication, Digest Authentication, or integration with LDAP/Active Directory for user authentication.
- Implement authorization policies to control which users or groups can access specific resources through the proxy server.
- Logging and Monitoring:
- Implement logging mechanisms to record proxy server activities, including client requests, server responses, errors, and traffic statistics.
- Use monitoring tools to track the health, performance, and availability of the proxy server.
- Security Measures:
- Implement security measures such as SSL/TLS encryption to secure communications between clients and the proxy server.
- Configure firewall rules and access control lists (ACLs) to restrict access to the proxy server and protect against malicious attacks.
- Caching:
- Configure caching mechanisms to store frequently accessed content locally on the proxy server.
- Caching helps reduce bandwidth usage, improve performance, and decrease latency for clients accessing cached resources.
- Content Filtering:
- Implement content filtering to restrict access to certain websites, URLs, or content categories based on predefined policies.
- Content filtering can be based on URL blacklists/whitelists, domain categories, keywords, or content types.
- Scalability and High Availability:
- Design the proxy server infrastructure to be scalable and resilient to handle increasing traffic loads and provide high availability.
- Use techniques like clustering, replication, and failover to ensure continuous operation and minimal downtime.
- Compliance and Regulatory Requirements:
- Ensure that the proxy server implementation complies with relevant regulations and standards, especially concerning data privacy and security (e.g., GDPR, HIPAA).
- Testing and Tuning:
- Thoroughly test the proxy server implementation under different conditions to ensure optimal performance, security, and reliability.
- Continuously monitor and tune the configuration based on real-world usage patterns and feedback.
Security Considerations in Network Protocols and Proxies:
Security is paramount in network protocols and proxies to ensure data integrity, confidentiality, and availability. Here are numerous key considerations:
1. Encryption Protocols
- Utilize encryption protocols like SSL/TLS to encrypt data transmitted over the network, making sure confidentiality and preventing eavesdropping.
- Implement strong encryption algorithms and secure cipher suites to shield towards cryptographic attacks.
2. Authentication Protocols
- Deploy robust authentication mechanisms including OAuth, OpenID Connect, or LDAP to verifies the identities of users and devices accessing the network.
- Enforce multi-factorauthentication (MFA) for more security, requires users to give couple of test for the verification.
3. Mitigating DDoS Attacks
- Implement rate proscribing and traffic shaping mechanisms to detect and mitigate Distributed Denial of Service (DDoS) attacks.
- Utilize DDoS protection services which could identify and filter out malicious traffic, preventing service disruptions.
4. Network Vulnerabilities
- Regularly examine and patch network infrastructure for known vulnerabilities to prevent exploitation by using attackers.
- Conduct penetration testing and vulnerability checks to identify and remediate potential security weaknesses proactively.
Best Practices for Designing Scalable and Resilient Systems
You can implement these following best practices and strategies for designing and resilient system. They are described as follow:
- Modular Design: Design system with modular components that may scale independently, taking into consideration flexible resource allocation and efficient horizontal scaling.
- Load Balancing: Implement load balancers to distribute incoming traffic throughout multiple servers, preventing overloads and ensuring excessive availability.
- Redundancy and Failover: Configure redundant component and failover mechanisms to ensure non-stop operation in the event of hardware failure or network disruptions.
- Data Replication and Backup: Implement data replication across geographically distributed locations to make sure data availability and resilience towards failure. Regularly backup essential data and preserve off-site backups to mitigate the chance of data loss.
- Fault Tolerance: Design system with built-in fault tolerance mechanisms that can gracefully manage failure with out impacting overall service availability. You can use techniques like circuit breakers, retry techniques, and sleek degradation to handle transient errors and service disruptions.
Conclusion
In summary, we have discussed network protocol and proxies , type of proxies like Forward and reverse proxies. We have also explored commonly used network protocol in system design like TCP, IP, HTTP, and SSL/TLS that keep our data transmission steady and secure.
Share your thoughts in the comments
Please Login to comment...