SQL Injection is one of the most severe attacks on web applications that exploit the SQL Database and provide unauthorized access to the Database. This attack can be done through different techniques like Manual and Automated. The manual approach requires more effort as all the steps are to be carried out from scratch. The automated approach consists of various automation tools that can be used to gain access to the Database. This automation process can be done using the tool named Sqlninja. We can install this tool on Kali Linux OS and perform various attacks on the target web application. In this article, we will see the information about the Sqlninja tool, its features, Installation steps, and the uninstallation process.
What is Sqlninja?
Sqlninja is not a single tool, but a suite of penetration testing tools used to test the security of SQL (Structured Query Language) databases. It is designed to exploit SQL injection vulnerabilities in web applications and gain unauthorized access to the underlying database systems. SQL injection is a type of security vulnerability that occurs when an application does not properly validate user input, allowing attackers to execute arbitrary SQL queries. The Sqlninja is used to automate the process of exploiting SQL injection vulnerabilities and extracting data from databases.
Features of Sqlninja:
Below are some of the features of the Sqlninja tool:
- SQL Injection Identification: Sqlninja can automate the process of identifying SQL injection vulnerabilities within a web application. It scans the application for potential injection points.
- Automated Exploitation: Once a SQL injection vulnerability is identified, Sqlninja provides automated exploitation capabilities. It can craft and send malicious SQL queries to the vulnerable input points in the application.
- Data Extraction: Sqlninja is capable of extracting data from the database, which may include sensitive information such as usernames, passwords, and other records. It can retrieve data by manipulating the SQL queries.
- Command Execution: In some cases, Sqlninja can execute arbitrary SQL commands on the database server, potentially allowing an attacker to gain control of the server.
- Evasion Techniques: The tool is equipped with techniques to evade security mechanisms like Web Application Firewalls (WAFs) that may attempt to block or detect SQL injection attempts.
- Fingerprinting: Sqlninja can help fingerprint the underlying database management system (DBMS) to perform the exploitation attempts on the specific DBMS being used.
How to Install Sqlninja in Kali Linux?
Before installing and using the Sqlninja tool in Kali Linux, we need to ensure that we have all the below prerequisites satisfied for successful installation.
Prerequisites:
- Kali Linux: We need to have a working Kali Linux distribution installed on your system.
- Terminal Access: We should have access to a terminal or command-line interface on your Linux system. Most Linux distributions provide this by default.
Step-by-Step Installation Process:
Now, follow the below steps to install the Sqlninja tool in the Kali Linux Operating System:
Step 1: Firstly, we need to open a terminal on our Kali Linux system. We can usually find the terminal application in our system’s applications or by searching for “Terminal” or we can also use the shortcut “CTRL + ALT + T” to launch the terminal.
Opening the Terminal
Step 2: Once the terminal is been opened, we need to update our system with the latest package information. This can be done by using the apt manager on the system. So we need to execute the below update command to update all the repositories to their latest version.
sudo apt update
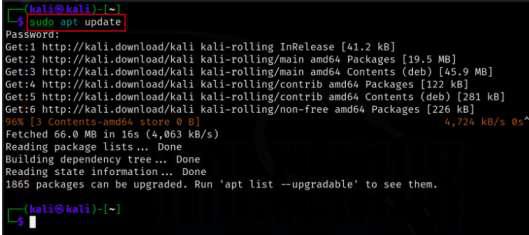
Updating the System
Step 3: Once the package list is updated, you can install Sqlninja using the following command.
sudo apt install sqlninja
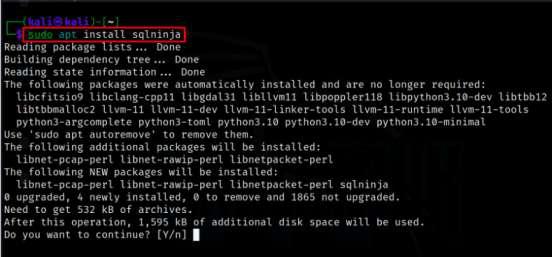
Installing the Tool
Step 4: During the installation process, you might see a list of packages that will be installed, and you may be prompted to confirm the installation and allocate disk space. To confirm the installation, type ‘Y‘ and press Enter. The package manager will then download and install Sqlninja and its dependencies.
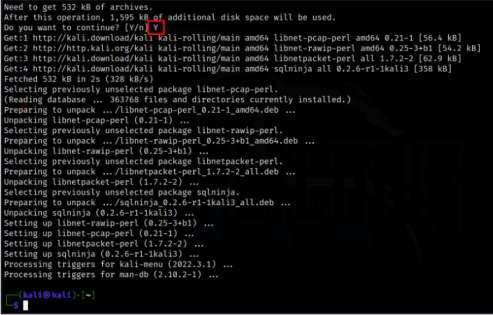
Confirming the Installation
Step 5: After the installation is complete, you can verify that Sqlninja has been successfully installed by running the following command
sqlninja --version
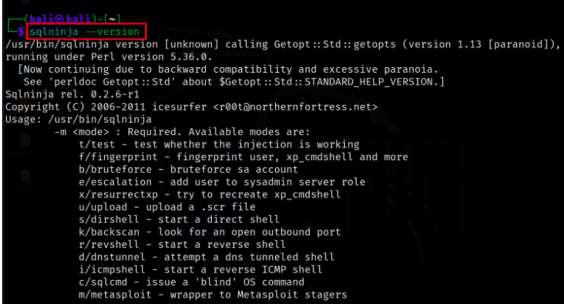
Verifying the Installation
How to Use Sqlninja in Kali Linux?
In this section, we will see the practical usage of Sqlninja in Kali Linux. Below are some of the examples demonstrating the usage of Sqlninja tool.
Firstly, we need to have the sqlninja.conf file in which the target domain is been specified. So below we have a sample conf file in which we have given the target as “http://testphp.vulnweb.com/listproducts.php?cat=1“.
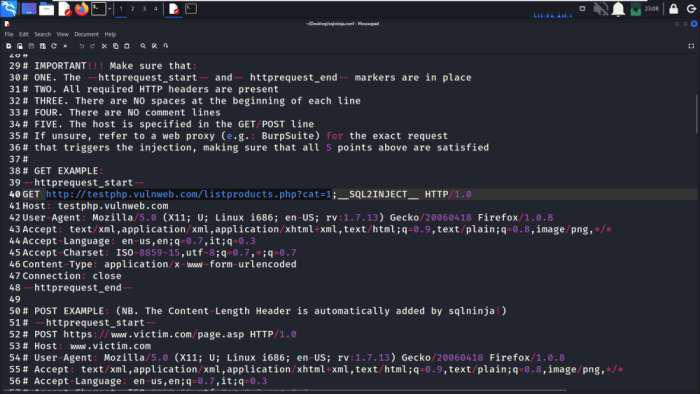
Specifying Target Domain
Example 1: Using Test Module
sqlninja -mt -f sqlninja.conf
In Example 1, the “Test” module (-mt) is employed in SQLNinja to assess the security of a target application specified in the sqlninja.conf configuration file. We can see that the application is not vulnerable for SQL Injection.
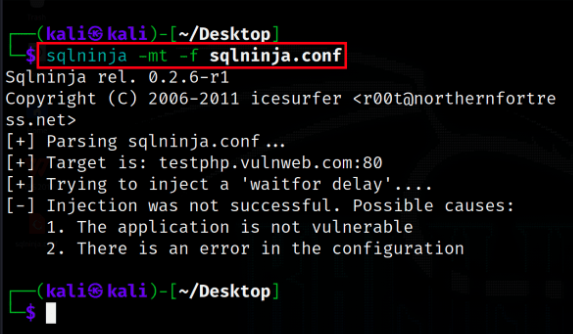
Using Test Module
Example 2: Using FingerPrint Module
sqlninja -m fingerprint -f sqlninja.conf
In this Example 2, we have run the “Fingerprint” module (-m fingerprint) by loading the configuration from the sqlninja.conf file (-f sqlninja.conf). This module is used to gather information about the underlying database management system (DBMS) and its version by sending various SQL queries. It helps in identifying the specific DBMS in use, which can be useful for planning further attacks or understanding the target system’s architecture.
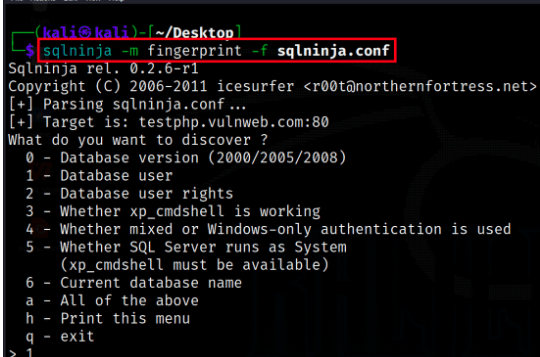
Using Fingerprint Module
Example 3: Using Upload Module
sqlninja -m upload -f sqlninja.conf
In this example, the SQLNinja tool is being used with the “Upload” module to attempt the upload of a debug script named “nc.scr” from the local “/tmp” directory to a target system, as defined in the sqlninja.conf configuration. This action helps assess the security of the target system and its vulnerability to file uploads.
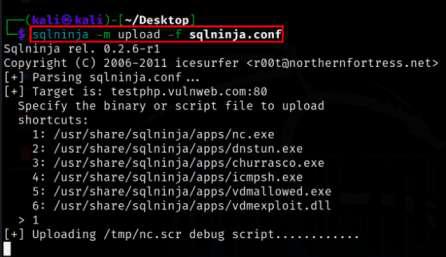
Using Upload Module
How to Uninstall Sqlninja on Kali Linux?
Once the usage of the Sqlninja tool is done, and we need to remove the tool from our system permanently, then we can follow the below Uninstallation process.
Step-by-Step Uninstallation Process:
Step 1: Firstly, we need to open a terminal on our Kali Linux system. We can usually find the terminal application in our system’s applications or by searching for “Terminal” or we can also use the shortcut “CTRL + ALT + T” to launch the terminal.

Opening Terminal
Step 2: If we want to remove Sqlninja without deleting its configuration files, then we can use the following command:
sudo apt-get remove sqlninja
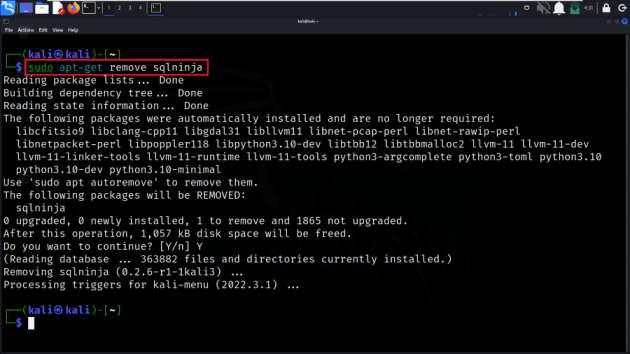
Removing sqlninja by keeping config files
This command will uninstall Sqlninja but leave the configuration files intact.
Step 3: If we want to completely remove Sqlninja, including its configuration files, use the following command:
sudo apt-get purge sqlninja
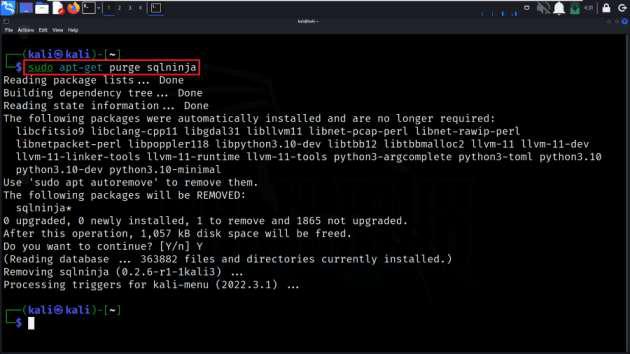
Complete Removal of the Sqlninja tool
Step 4: We can verify that Sqlninja has been uninstalled by running the following command. This will return a message indicating that the command is not found.
sqlninja --version
.jpg)
Command Not found
Conclusion
In conclusion, installing Sqlninja on Kali Linux is a straightforward process that allows security professionals and penetration testers to leverage this tool for ethical hacking and security testing. By using the package manager ‘apt,’ Kali Linux users can easily obtain and set up Sqlninja on their systems. This tool’s installation involves updating the package list, specifying the target URL and parameters for exploitation, and confirming the installation.
Share your thoughts in the comments
Please Login to comment...