Kali Linux, which is well-known as a robust and adaptable platform for cybersecurity experts and ethical hackers, is a two-edged sword. While it provides users with a toolbox for testing and safeguarding systems, it also exposes possible vulnerabilities if not adequately protected. This essay delves into the crucial measures to protect your Kali Linux distribution, ensuring that your digital fortress is impenetrable to assaults and your ethical hacking attempts are unaffected.
How to Secure Our Kali Linux to Ensure Our Protection
1. Regularly upgrading your system keeps it protected against known vulnerabilities. To keep your system up to date, use the following commands:
It is critical to upgrade your system on a regular basis to protect it from known vulnerabilities. Use the following commands to keep your system up to date:
Step 1: Launch Kali Linux’s terminal.
Step 2: To update the package list, use the following command:
sudo apt update
 Command Explanation: When you run sudo apt update, you advise your Kali Linux system to refresh its knowledge of the most recent software packages available in the official Kali Linux repository.
Command Explanation: When you run sudo apt update, you advise your Kali Linux system to refresh its knowledge of the most recent software packages available in the official Kali Linux repository.
Why It’s Important: This procedure is comparable to checking for software updates on your computer or mobile device. Kali Linux, like any other operating system, is continually updated with security patches, bug fixes, and new software packages. By running this command, you ensure that your system is informed of these updates.
Step 3: Once the update is complete, use the following command to upgrade the packages on your system:
sudo apt upgrade

Command Explanation: After updating the package information using sudo apt update, you run sudo apt upgrade. This command is in charge of updating the software packages on your system to the most recent versions.
Why It’s Important: The major goal of this command is to keep your system up to date with the most recent software versions. It includes security upgrades that address known vulnerabilities. Cybersecurity risks grow over time, and software developers actively deploy fixes to protect against these attacks. By upgrading your packages, you apply these changes to your system, increasing its security.
2. Firewall Configuration: Protecting Your Boundaries:
To properly regulate incoming and outgoing traffic, use Kali Linux’s “ufw” (Uncomplicated Firewall) administration tool:
Step 1: Launch Kali Linux’s terminal.
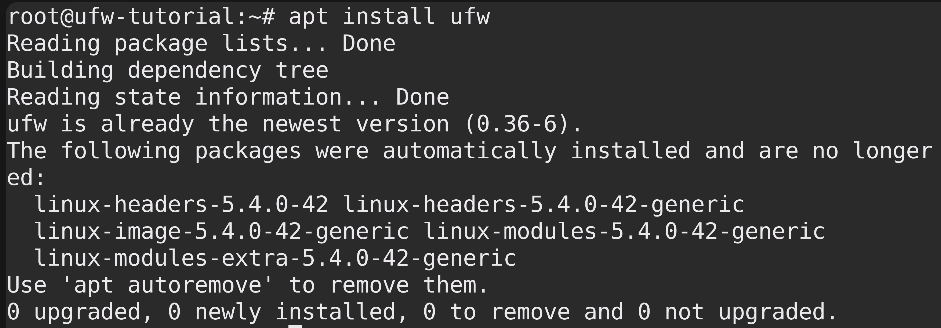
Step 2: Install “ufw” (Uncomplicated Firewall) administration tool , use the following command:
sudo apt install ufw
Step 3: Run the following command to enable the firewall:
sudo ufw enable
Command Explanation: When you type sudo ufw enable, you enable the Kali Linux Uncomplicated Firewall (ufw). This program makes firewall setting and management easier.
Why It’s Important: Enabling ufw is comparable to shutting down your digital fortress. It creates a firewall between your Kali Linux system and the outside world, allowing you to regulate network traffic. It blocks incoming connections by default unless specifically allowed, lowering the danger of unwanted access and potential threats.
Step 4: Set the default policies for incoming and outgoing traffic:
sudo ufw default deny incoming
sudo ufw default allow outgoing
Command Explanation: These instructions configure the default behavior of your Kali Linux system’s Uncomplicated Firewall (ufw) for incoming and outgoing network traffic.
Why It’s Important: sudo ufw default deny incoming: This command disables the incoming policy by default. In essence, it prevents all incoming network connections until you explicitly allow them. This is an important security feature since it inhibits illegal access attempts from outside sources, hence improving the overall security of your system.
sudo ufw default allow outgoing: By default, this command allows all outgoing network traffic. Outgoing connections, such as online browsing and emailing, are usually secure, therefore permitting them poses no substantial security risk. Outgoing traffic allows your applications and services to communicate with external servers and resources.

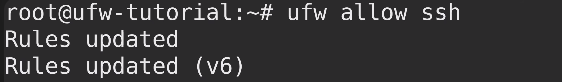
Step 4: Allow SSH traffic (or any other required services) using a command like as:
sudo ufw allow ssh
Command Explanation: This command allows incoming Secure Shell (SSH) traffic passed your Kali Linux system’s Uncomplicated Firewall (ufw).
Why It’s Important: sudo ufw allow ssh: SSH is a secure remote system management protocol. Allowing SSH traffic is required if you intend to access your Kali Linux system remotely via SSH sessions. By explicitly allowing SSH traffic, you ensure that genuine users can safely connect to your system while protecting against illegal access.
Customization: To allow certain services or apps, substitute “ssh” in the command with other service names or port numbers. If you’re operating a web server, for example, you can use sudo ufw allow 80 to allow HTTP traffic and sudo ufw allow 443 to allow HTTPS traffic. This customisation allows you to specify which services are allowed to access your system, providing an additional degree of protection.
3. Disabling Unnecessary Services: Reducing Vulnerabilitie:
Identify and deactivate any superfluous services or daemons that are running on your system. Use the “systemctl” command to manage services:
Step 1: Launch Kali Linux’s terminal.
Step 2: Determine the service you wish to disable. In the following command, replace service> with the name of the service you wish to disable:
sudo systemctl disable <service>
Command Explanation:This command disables a service on your Kali Linux system by utilizing the systemctl program.
Why It’s Important: Kali Linux, like many other Linux distributions, employs a number of background services or daemons to perform certain functions. Some of these services may not be required for your use case or may represent security issues if they are left running. By detecting and stopping superfluous services, you can lower your system’s attack surface and potential risks.
Customization: Replace the service> placeholder in the command with the actual name of the service you want to disable. To disable a service called “example_service,” for example, execute sudo systemctl disable example_service. This customisation enables you to target specific services based on the configuration and requirements of your system.

4. Examine System Logs:
Check system logs for unusual behavior on a regular basis using the “journalctl” command
Step 1: Launch Kali Linux’s terminal.
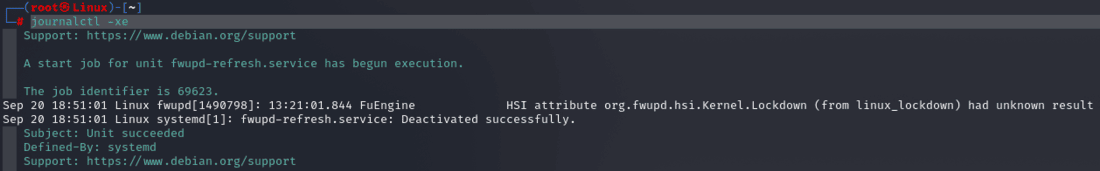
Step 2: Run the following command to inspect the system logs for any anomalies:
journalctl -xe
Command Explanation:The journalctl -xe command starts the Journalctl program, which is part of the systemd system management suite. This command gathers and displays detailed records of system events and messages, making it an indispensable tool for system administrators and cybersecurity professionals. Journalctl’s -xe settings direct it to display all available logs with detailed details, including the conclusion of each log entry.
Why It’s Important: System logs are a digital trail of your Kali Linux system’s actions. They keep track of critical information including as processes, faults, warnings, and security issues. Examining these logs provides information about any anomalies, unexpected shutdowns, failed services, or security breaches. It is critical to identify and address such issues as soon as possible in order to ensure system stability, security, and overall operational integrity. As a result, checking system logs on a regular basis using journalctl -xe is a preventative strategy that ensures the early discovery and resolution of any issues, contributing to a resilient and secure Kali Linux environment.
5. Implement Security Updates Automatically
Set up automated security upgrades to keep your machine safe against known vulnerabilities:
Step 1: Open the terminal in Kali Linux.
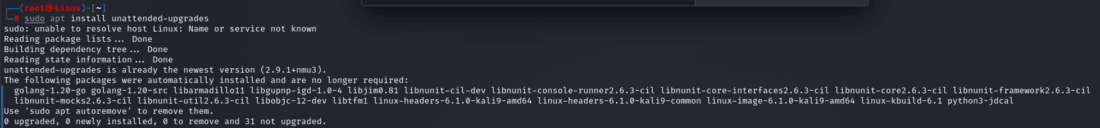
Step 2: Install the unattended-upgrades package with this command:
sudo apt install unattended-upgrades
Command Explanation: You instruct your Kali Linux system to download and install the “unattended-upgrades” package by typing sudo apt install unattended-upgrades. This package is required for fully automating the process of downloading and installing security updates without the need for manual involvement.
Why It’s Important: Installing the “unattended-upgrades” package is critical for keeping your Kali Linux system secure. Without it, you’d have to check for and install updates manually on a regular basis, which is time-consuming and prone to error. This step guarantees that your system is always up to date with the most recent security patches, lowering the likelihood of vulnerabilities being exploited.
Step 3: Set up unattended updates by running:
sudo dpkg-reconfigure -plow unattended-upgrades
Command Explanation: When you run sudo dpkg-reconfigure -plow unattended-upgrades, you are customizing the behavior of the “unattended-upgrades” package. This command launches a configuration wizard that allows you to control how and when updates are applied automatically.
Why It’s Important: Unattended updates, when configured correctly, ensure that your system gets and applies security patches and updates as efficiently as possible. By choosing the necessary options during this stage, you may adapt the update process to your preferences and guarantee that crucial security updates are installed promptly, decreasing the window of vulnerability.

6. Install and Setup an Antivirus:
While Kali Linux is mainly an offensive security tool, having an antivirus solution on hand may aid in the prevention of malware and viruses. ClamAV is a well-liked option:
Step 1: Launch Kali Linux’s terminal.
Step 2: Run the following command to install ClamAV:
sudo apt install clamav
Command Explanation – By running “sudo apt install clamav,” you direct your Kali Linux system to download and install ClamAV, an antivirus software package specifically designed to scan for and detect malware and viruses on your system.
Why It’s Important – While Kali Linux is generally used for offensive security testing, having an antivirus solution like ClamAV on hand will assist safeguard your machine from being inadvertently infected with harmful files during ethical hacking activities. Installing ClamAV provides an extra layer of defense against potential threats, keeping your digital fortress safe.
 Step 3: Run the following command to update ClamAV’s virus database:
Step 3: Run the following command to update ClamAV’s virus database:
sudo freshclam
Command Explanation – By running “sudo freshclam,” you are upgrading ClamAV’s virus database. This procedure is critical since antivirus software relies on up-to-date virus definitions to detect and quarantine the most recent threats.
Why It’s Important – Keeping your antivirus definitions up to date is critical for successful malware detection. Cyber dangers are constantly developing, and new malware strains appear on a daily basis. Running this command ensures that ClamAV can detect and neutralize the most recent malware variants, improving the overall security of your Kali Linux system.
7. Use Secure Passwords:
Make sure that all user accounts have strong, unique passwords. Use the passwd command to change your user password.
Step 1: Launch Kali Linux’s terminal.
Step 2: For all user accounts, use strong, unique passwords. To update your user password, use the passwd command:
passwd
Command Explanation – When you run the ‘passwd’ command, you start the process of changing a user’s password on your Kali Linux system. This command prompts the user to provide their current password (if applicable) before setting a new password.
Why It’s Important – Password security is critical to overall system security. Weak or easily guessable passwords can expose your system to unauthorized access. By utilizing the ‘passwd’ command to enforce strong, unique passwords for all user accounts, you enhance the first line of security against prospective intruders. This step is critical for ensuring the integrity and security of your Kali Linux distribution.

Conclusion:
In the vast world of cybersecurity, where the boundary between defender and attacker frequently blurs, reinforcing your Kali Linux installation is more than just securing your own system,it’s a critical step toward embodying ethical and responsible cybersecurity concepts. This thorough security tutorial has methodically guided you through critical ways to strengthen your Kali Linux distribution, making it an impenetrable digital fortress. By slavishly following these approaches and best practices, you ensure that your Kali Linux environment stays a formidable tool in your goal to protect systems and networks from potential threats and vulnerabilities. Remember that true cybersecurity begins within the borders of your own digital domain, and by adopting these precautions, you play a critical role in creating a safer, more secure environment.
Share your thoughts in the comments
Please Login to comment...