How to Change or Hide the Nginx Server Signature?
Last Updated :
16 Nov, 2023
In Linux, changing or hiding the Nginx server signature consists of modifying the server tokens that are sent in the HTTP response headers. The server signature has information about the server software and its version, which can be a security perspective risk. In this article, we will see how we can change or hide the Nginx Server Signature on the Kali Linux system.
What is an Nginx Server?
Nginx Server in a Linux environment is an open-source web server and the reverse proxy server. It is a highly performance-based, table, and scalable server that is used to serve static content, act as a load balancer, and handle tasks like SSL Termination. Nginx Server is designed to handle a larger number of parallel connections and is also deployed to improve the performance and reliability of websites and web applications. Nginx can function as a reverse proxy, directing client requests to backend servers, and it’s a popular choice for hosting dynamic sites and applications.
What is Nginx Server Signature?
The Nginx server signature refers to the information about the server software and its version that is included in the HTTP response headers when a client requests an Nginx server. This signature typically reveals details like the Nginx version number, which can be useful for attackers seeking to exploit known vulnerabilities associated with specific versions. To enhance security, administrators often choose to hide or change the server signature to minimize the information exposed to potential attackers. This is done by configuring the “server_tokens” directive in the Nginx configuration file, setting it to “off” to prevent the server from disclosing its version in the response headers. This practice adds a layer of security and helps reduce the risk of targeted attacks based on known vulnerabilities.
How to change(Hide) the Nginx Server Signature?
In this section, we will see the step-wise demonstration to hide the Nginx Server signature on the Kali Linux system. Follow the below-specified steps along with the commands properly to hide the Nginx Sever Signature without encountering any issues or problems.
Step 1: Login as Root User
Firstly, we need to log in to the system with the root privileges. Using the below command we can log into the system with root privileges. After executing the sudo su command, we need to enter our user password to verify that we have the necessary permissions. Once we enter the password, we are privileged with the root permissions.
sudo su
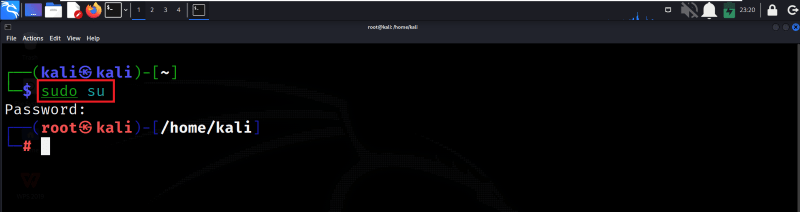
Login as Root User
Step 2: Backup Nginx Configuration
After logging in with root access, we need to create a backup copy of the Nginx Configuration file. The cp command is used to copy files, and here we’re copying the nginx.conf file to a new file named nginx.conf.backup.
cp /etc/nginx/nginx.conf /etc/nginx/nginx.conf.backup
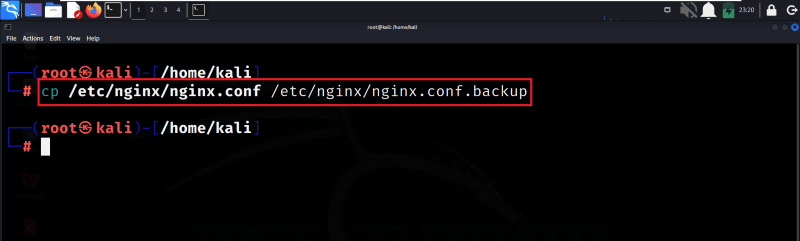
Backup Nginx Configuration
Step 3: Edit the Nginx Configuration File
Now, we need to open the Nginx configuration file in the Nano text editor. Nano is a simple and lightweight text editor. We can use any text editor as per our comfort.
nano /etc/nginx/nginx.conf
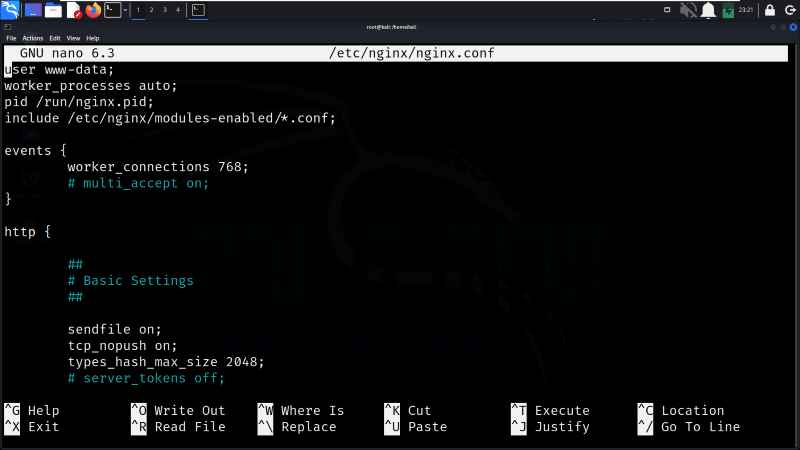
Edit the Nginx Configuration File
Step 4: Find the Server Token Directive
In the Nginx configuration file, we need to locate to the server_tokens directive. This directive controls whether Nginx includes its version in error pages and the “Server” response header. The on value or comment means it’s currently enabled.
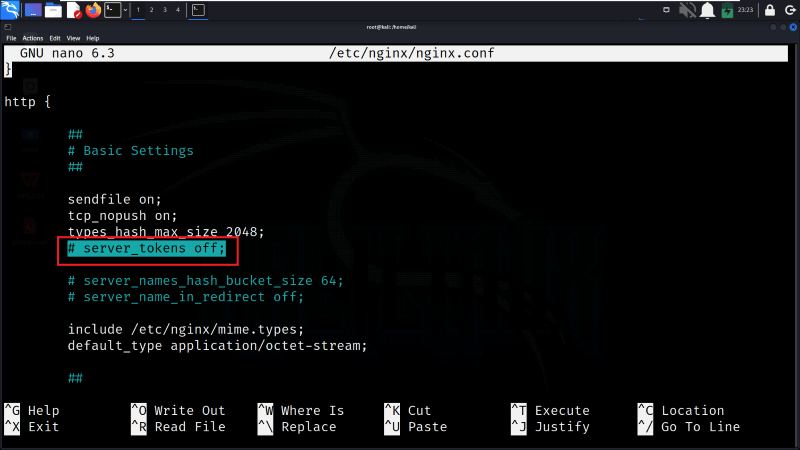
Find the Server Token Directive
Step 5: Change Server Tokens Directive
We need to change the value of the server_tokens directive to “off” and remove the # comment. This change instructs Nginx not to include its version information in the server responses.
server_tokens off;
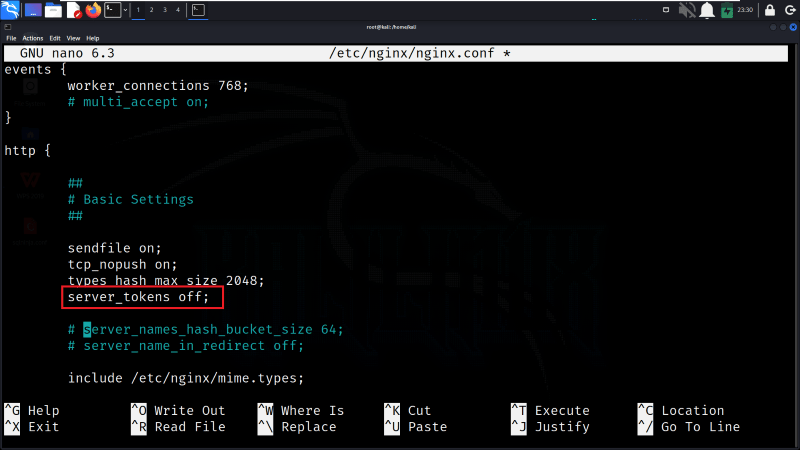
Change Server Tokens Directive
Step 6: Save and Exit
After changing, press Ctrl+O to save the file. It will prompt us to confirm the filename; just press Enter. Then press Ctrl+X to exit Nano.
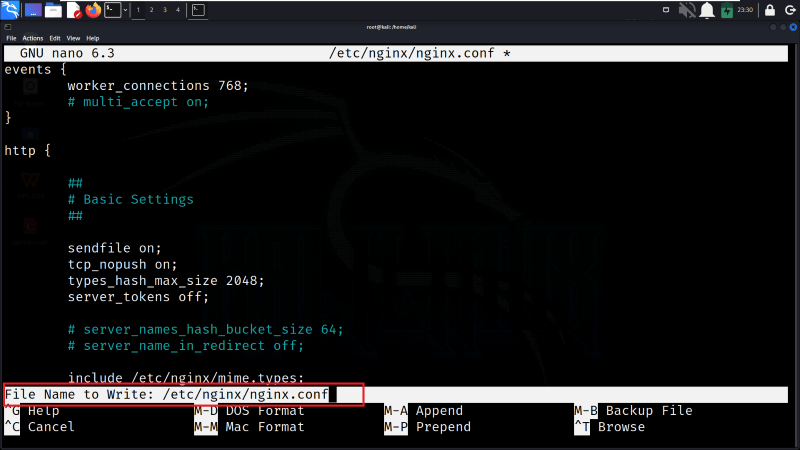
Save and Exit
Step 7: Test the Configuration
Once we are exited from the Nano editor, we will check the Nginx configuration for syntax errors. If there are no errors, it will display a message indicating that the configuration test is successful.
nginx -t
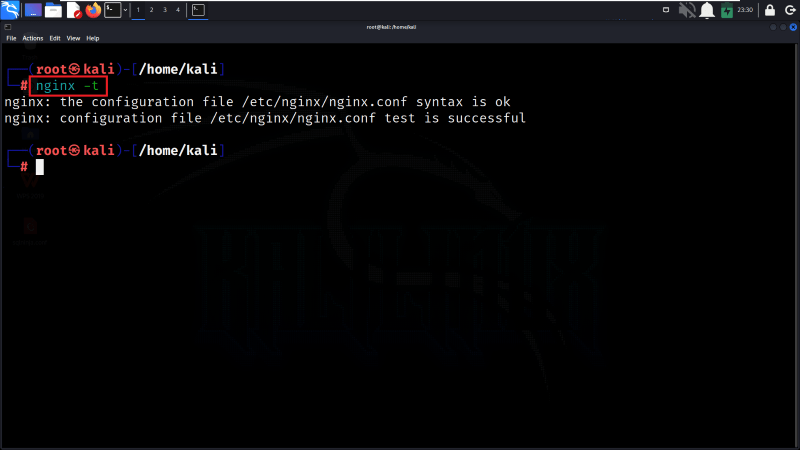
Test the Configuration
Step 8: Reload Nginx Server
Now, we will Reload Nginx to apply the changes. This command tells the Nginx service to reload its configuration without stopping the service. It ensures that the changes take effect.
systemctl reload nginx
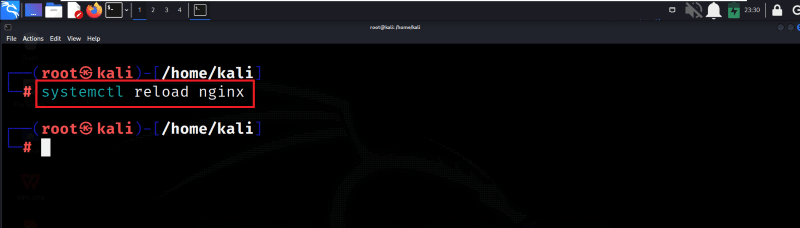
Reload Nginx Server
Step 9: Verify the Changes
To verify the changes whether the Nginx Server signature is changed (hidden) or not, we can use the curl command to make a simple HTTP request to your local server. The -I flag tells curl to show only the headers of the response. Check the “Server” header in the response to verify that it no longer includes the Nginx version information.
curl -I http://localhost
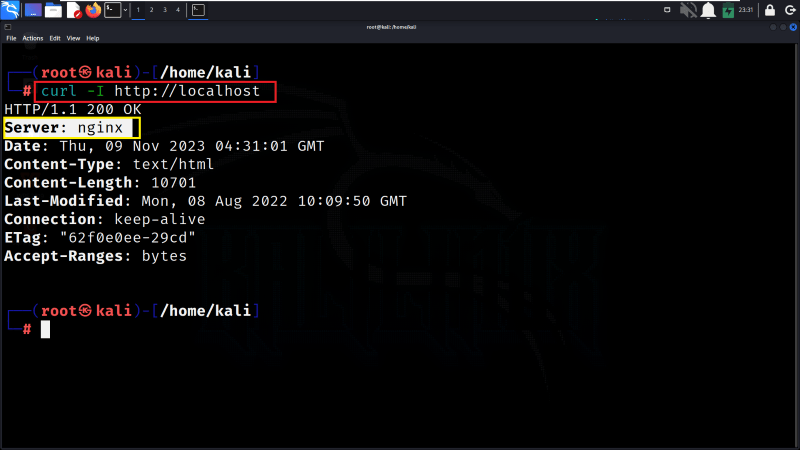
Verify the Changes
Conclusion
In conclusion, securing your Nginx server on Kali Linux involves a straightforward process of editing the configuration file to disable server token disclosure. By switching the server_tokens directive to “off” and verifying the changes through testing and reloading Nginx, you effectively conceal version information from potential attackers. This simple yet crucial step enhances security by minimizing the exposure of sensitive server details, contributing to a more robust defense against potential threats.
Share your thoughts in the comments
Please Login to comment...