How Does Certificate-Based Authentication Work?
Last Updated :
11 Apr, 2024
Certificate-Based Authentication is a cryptographic technique that enables secure identification of one computer by another across a network connection. It uses a public-key certificate. This authentication system confirms a user’s or device’s identity using digital certificates issued by a trusted authority such as a government agency or web server to verify its authenticity.
The validity of the certificate is verified against a list of trusted certificates. Access to secure resources is granted only if the certificate is on the list. Internet security protocols use certificates for authentication. For example, SSL/TLS is widely used by web browsers for secure online transactions.
Let’s see some examples of how common Certificate-Based Authentication (CBA) is. For example, the smart card is used for accessing offices or other buildings. Another example is the SSL/TLS protocol used in web browsers. CBA is also a key component of any Public Key Infrastructure (PKI) implementation.
What is Certificate-Based Authentication?
Certificate-based authentication (CBA) is a more secure alternative if we compare it to the traditional username and password combination. It can also be used alongside traditional methods for strong user authentication to form a phishing-resistant Multi-Factor Authentication (MFA). The digital certificate is present on an individual’s device or computer along with the private key, which facilitates the user’s browser or client to log into various systems automatically without more effort. When the request is made, the digital certificate can be presented for authentication.
Primary Terminologies
- E-Certificate: An online document to prove who or what you are, using secret codes and a system called PKI. It makes sure only the right things and people can enter a network. It also confirms if a site is real or fake to a web browser using SSL. It has key info like a person’s name, and a device’s code or number.
- PKI: This is a set of rules and tools to make, share, use, save, and end e-certificates and public key codes. PKI’s main job is to keep info safe when we use the web, like internet cash, online shops, and private emails.
- SSL/TLS: An e-item to check who is who and set up a safe web link using SSL/TLS code. These are part of a system called PKI. It lets one side know if the other side is real.
- 2FA: A safe way to use a site or app that needs two or more checks to get in. It keeps private stuff safe from those who know just one code. It makes things more safe and cuts the risk of info hacks.
Features
- Increased Security: Certificate-based authentication offers upgraded security compared to traditional username and password combinations. We can find that passwords are often vulnerable to easy guessing or insecure storage practices, like writing them down. If we eliminate passwords, certificate-based authentication mitigates the risk of phishing or brute-force attacks.
- Streamlined Authentication: By using Certificates, it removes the need for users to remember multiple username and password combinations and this decrease in password management tasks saves users significant time that is spent on guessing or resetting passwords. Therefore, certificate-based authentication not only decreases friction for users but also promotes overall user productivity.
- Ease of Deployment: Unlike alternative authentication methods such as one-time passcode (OTP) tokens or biometrics, certificates are stored locally on devices and require no additional hardware for implementation. Certificate-based authentication facilitates access control, as most solutions offer cloud-based management platforms. These platforms enable administrators to easily issue, renew, and revoke certificates as necessary, facilitating efficient certificate management processes.
Working
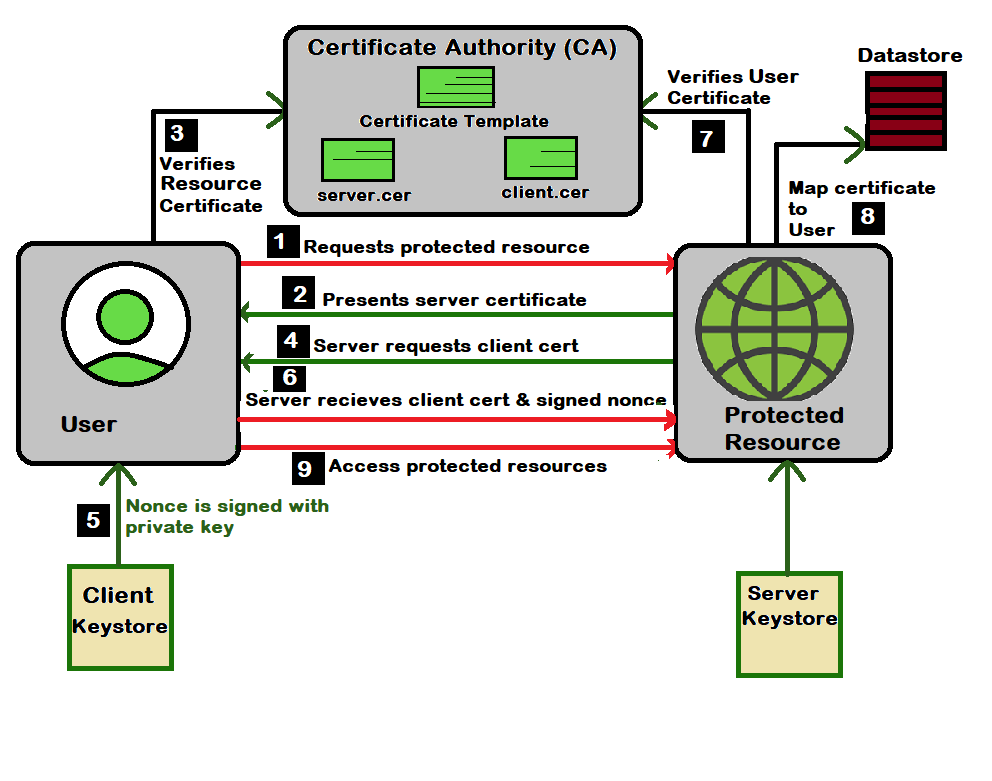
In the process of certificate-based authentication, when a user requests access to a protected resource, the server responds by presenting its certificate to the user’s browser. The browser then verifies the authenticity of the server’s public certificate. Subsequently, an authentication request is sent from the server, prompting the user to authenticate themselves. Concurrently, while the user undergoes authentication, their browser provides the server with the user’s certificate for validation. Upon successful validation of the user’s identity by the server, access to the network or protected resource is granted.
To authenticate users, machines, or devices, certificate-based authentication servers use the certificates and single sign-on (SSO) mechanisms. This authentication process hinges on the interaction of public keys, private keys, and certificate authorities (CAs). By leveraging these cryptographic elements, certificate-based authentication ensures secure and reliable verification of identities, enhancing the overall security of network access and resource utilization.
As, we know that each public key has a corresponding private key, and it is kept secret. When any data is encrypted using the public key, it can only be decrypted with the private key. This configuration enhances the security during authentication since each private key is unique to the individual or device.
Now, to ensure security, certificates should be signed digitally by trusted third-party certificate authorities (CA) who verify the identity. This process takes place between your browser and the server you are communicating with.
User authentication is essential for access management and developing a zero-trust architecture in enterprises. Digital certificates prevents unauthorized individuals from penetrating servers, networks, or applicationsonly such that only legitimate users can access protected resources.
Public Key Infrastructure (PKI) and certificate-based authentication play a key role in this by minimizing dependence on traditional password-based login methods. Once users log into their devices, they’re not typically asked to enter their password again. Instead, their identity is linked to their digital attributes or their device’s identity and verified by the designated server.
Hence, digital certificates play an essential role in Public Key Infrastructure (PKI), acting as digital “ID cards” for users and devices in the digital domain. Similar to traditional identification documents, each digital certificate possesses unique attributes.
These certificates, like the X.509 certificate, contain crucial information such as:
- Public key
- User or device’s name
- Issuing Certificate Authority (CA)
- Validity start and end dates
- Certificate version number
- Serial number
Digital certificates are considered reliable because users and devices must verify their identity before receiving them from a reputable Certificate Authority (CA). This CA serves as a trusted third party, similar to government institutions such as the Department of Motor Vehicles (DMV) or town halls that issue marriage licenses.
The CA thoroughly reviews Certificate Signing Requests (CSR), which are the documents submitted for new digital certificates. It verifies the information against official sources to ensure legitimacy. Only once the CA confirms the claimed identity and validates all details does it issue a client authentication certificate.
There are local and private CAs, and some organizations choose to issue their client authentication certificates instead of relying on widely recognized CAs like IdenTrust or DigiCert. However, private certificates lack the verification process performed by public CAs and are not trusted for securing access to external resources. Instead, they are suitable for internal purposes only.
Certificate-based authentication
The process works like this:
- The client starts the connection with the server.
- The server sends its public certificate to the client.
- The client checks the server’s certificate to ensure it’s valid.
- The server requests the client’s certificate.
- The client signs a random number with its private key and sends it, along with its public certificate, back to the server.
- The server verifies that the signed random number was indeed signed by the client using the client’s public certificate.
- Now a server checks the validity of a certificate, it is confirming that the client’s certificate has not expired or been revoked.
- If all necessary checks are successful, the server can use the attributes from the certificate to authenticate the user in its system.
- Sometimes, additional verification steps may required, such as need of verifying the Certificate Authority’s signature and tracing it back to the root CA for added security. Hence, this process guarantees that transmission between the client and server is secure and the identities of both parties are verified before any transactions or data exchanges take place.
Advantages
- Efficiency in cloud is enabled: The use of certificate based authentication with cloud computing ensures that there is no need for extra hardware such as smart card readers or terminals.
- Cost effective management: With virtual digital certificates management solutions, this case digital certificates can be issued at a lower cost thus reducing time and expenses associated with the process of issuing new certificates, replacement and revocation.
- Single Sign On (SSO) enabled Authentication: Certificate-based authentication that incorporates Single Sign-On (SSO) simplifies the authentication process by eliminating many initial steps.
- Phishing Resistant: It provides more secure digital certificate based authentications compared to traditional passwords and diminishes susceptibility to phishing attacks.
- Mutual Authentication: By use of certificate-based authentication, all parties communicating are authenticated while helping administrators identify suspicious activities.
- Scalability: External users like suppliers and partners can get access provisioned without affecting existing customers because CBA offers scalability.
Disadvantages
- Initial Investment: The cost of establishing Certificate-based Authentication on a network infrastructure may be a one-time investment however it can be high and this is why it may not be suitable for start-ups and small companies.
- Ongoing Maintenance: Certificate-based authentication requires ongoing maintenance such as issuing, renewing and revocation thereby entails operational and licensing costs associated with Certificate Management Systems (CMS) and other related resources.
Conclusion
It is important to note that CBA is a reliable and efficient way of authenticating users and devices. Therefore there will be an upsurge in its adoption as more organizations take their systems to the cloud. Certificate-based authentication facilitates access control, certificate-based authentication not only decreases friction for users but also promotes overall user productivity.
Frequently Asked Questions on Certificate Based Auhtentication – FAQs
Is Authentication same as authorization?
No, they’re different. Authentication is about confirming that users are really who they claim to be. It’s the first step in security. Authorization, on the other hand, is about giving users permission to access something. In security, it’s like giving someone a key to enter a specific room or use a particular tool.
Are username and password authentication system and Two-factor authentication same as Certificate-Based Authentication (CBA)?
No, they are not. Digital certificate is used for verifying user or device identity in CBA while username and password confirm if the user’s credentials correspond to those in the database. CBA is also different from two-factor authentication which requires both things that can prove an individual’s identity to be presented by the user since only a digital certificate is needed for CBA. These approaches are often combined with each other but it cannot mean that they are identical. More often than not, organizations prefer using several ways of preventing unauthorized access.
What is the Future of CBA?
To answer that question we need to look at some considerations. However managing digital certificates for these organizations can become heavy. Consequently, they should ensure that the certificate authority they choose can be trusted, always keep their certificates current so as not to lose them in case of any theft or loss. Nevertheless, despite these challenges, CBA continues to play a vital role in security technologies by providing an authenticated identity approach that is secure and user-friendly. Even if we are unlikely to completely discontinue using CBA, we expect platforms making it more accessible especially through Identity as a Service (IaaS) solutions
Share your thoughts in the comments
Please Login to comment...