Hidden tricks inside Tor Browser
Last Updated :
20 Dec, 2023
Hidden tricks inside Tor Browser:
Tor Browser: Anonymity and Privacy Online
Tor Browser is a free and open-source web browser designed to provide online anonymity and privacy. It achieves this through a unique method called onion routing, which encrypts your internet traffic and relays it through a global network of volunteer relays called Tor nodes. This process makes it difficult to track your online activity and identify your location.
Here are a few of the Tor Browser’s main attributes:
- Anonymity: The Tor Browser makes it more difficult for websites and internet trackers to identify you by masking your IP address and location.
- Privacy Protection: You can hide your online activity from other network observers and your internet service provider (ISP) by utilizing the Tor Browser.
- Security: The Tor Browser’s built-in security features protect you against malware, phishing scams, and other online threats.
- Onion routing: Data is encrypted at multiple levels as it passes through each Tor network node. The term “onion” refers to this process. Each node in the chain only knows the nodes before and after it, adding an extra layer of anonymity.
- Cross-Platform Compatibility: Windows, Linux, macOS, and Android are all supported by the Tor Browser.
What does Tor do?
Using the Tor Browser is just like using any other web browser. Although Tor needs to be configured in order to connect to the Tor network before it can run, configuring the browser itself is pretty much the same as setting up Chrome or Firefox.
The main distinction is that websites and services you visit while using Tor cannot see your real IP address or any other system information. It also prevents the knowledge of your activities by your Internet Service Provider.
The primary uses of Tor are as follows:
Overcoming censorship and surveillance surreptitiously accessing “.onion” websites, or hidden services on Tor, via covert internet browsing
Tor: Pros and Cons
Pros:
- If you are using Tor correctly, the websites you visit are unable to determine your actual IP address.
- You can visit websites without giving your internet service provider access to your browsing history.
- With a sizable developer and volunteer community, Tor is an open-source project that has the potential to improve tool development and security.
- The only method to reach the dark web is via the Tor Browser. A portion of the internet known as the “dark web” is only accessible with specialized software and is not indexed by search engines.
- Access to.onion websites, which are unique to the Tor network and are frequently linked to increased privacy and security, is made possible by Tor.
Cons:
- Because of the way Tor Browser routes your traffic, it may be slow at times. This is a result of the various servers that your communication is routed through, which may cause latency.
- Compared to other web browsers, Tor Browser is not as user-friendly. It may not function as intended in certain areas and has a different interface.
- It is possible for some governments and network operators to stop Tor from operating.
- Only traffic passing over the Tor network is encrypted and routed by the Tor Browser. This implies that other internet traffic you generate, including that from other apps, is not secured.
- The Tor Browser isn’t totally safe. If you are not careful, it could be discovered who you are.
Tor browser offers numerous Benefits:
Enhanced Privacy:
- IP Address Masking: Tor masks your IP address by passing via a network of servers (nodes) run by volunteers. Because of this, it becomes more difficult for websites, trackers, and hackers to identify you based on your online activities.
- Tor uses multi-layered encryption, which encrypts your web traffic several times to further safeguard your privacy and increase the difficulty of data interception.
- With its anti-fingerprint feature, the Tor browser works to stop websites from using your browser’s settings and other information to identify you specifically.
Access to Censored Content:
- You can access websites and content through Tor that might be restricted in your nation or area. This covers websites blocked by companies, governments, or academic organizations.
- Tor can also be used to get around firewalls and other internet access limitations.
Protection from Online Threats:
- Tor can assist in shielding you from online dangers like malware, phishing scams, and internet tracking. This is due to the fact that Tor makes it more difficult for hackers to find you and obtain your personal data.
- Additionally, Tor makes it harder to monitor your online activities, which might help shield you from malicious attacks.
Access to .onion Websites:
- Tor is known for its association with .onion websites, which are special domains that can only be accessed through the Tor network. These sites often host content and services that prioritize privacy and anonymity.
Decentralized Network:
- The Tor network is not governed by a single organization since it is decentralized. It is therefore more immune to control and censorship.
- The Tor network’s decentralized structure also makes it more challenging for attackers to bring the network down.
Constant Improvement:
- The Tor Project is dedicated to making the Tor browser better and better all the time. This guarantees that Tor will always be an important resource for online security and privacy protection.
Although the Tor Browser can be somewhat difficult to use, it is a very effective tool for safeguarding your online anonymity. Here are a few tips that are not well known but may come in handy:
How to Connect to Tor:
The Connect to Tor window appears when you launch the Tor Browser. This gives you the choice of setting up Tor Browser to work with your connection or making a direct connection to the Tor network. If you want to be automatically connected to the Tor network at all times, you can indicate your preference by checking this box.
CONNECT

Connect to Tor
Most of the time, selecting “Connect” will enable you to join the Tor network without requiring any additional setup.
After it is clicked, Tor’s connection progress will be displayed in a status bar. Try using ‘Connection Assist’ or refer to the Troubleshooting page if, despite having a relatively fast connection, this bar appears to become stuck at a certain place. Alternatively, you ought to select “Configure Connection” if you are aware that your connection is filtered or makes use of a proxy.

Click ‘Configure Connection’ to adjust network settings
CONNECTION ASSIST
If Tor is prohibited where you are, you might want to try a bridge. Connection Assist uses your location to select one for you.

Connection Assist automatic
You can choose your region from the dropdown menu and choose ‘Try a Bridge’ if Connection Assist is unable to locate you or if you would prefer to manually arrange your connection.

Connection Assist configuration
CONFIGURE
You may learn about the status of both your Internet and Tor network connections using the Connection Assist. ‘Quickstart’ is the first checkbox. Selecting this will cause Tor Browser to attempt to connect using your previous network settings each time you launch it.
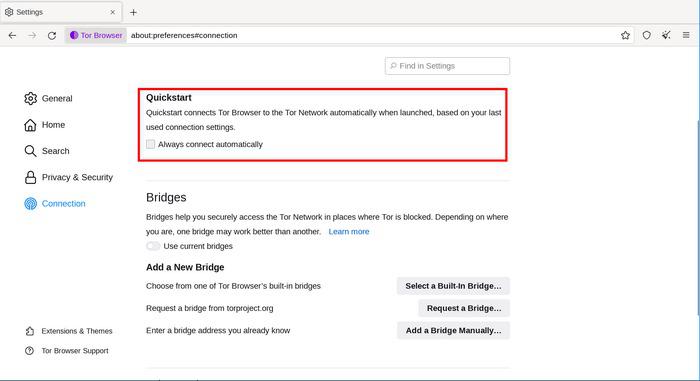
Quickstart
You may set up Tor Browser to use a pluggable transport if you are aware that your connection is censored or if you have attempted to connect to the Tor network but been unsuccessful in doing so. To set up a pluggable transport or establish a connection using Bridges, select “Bridges,” which will bring up the “Circumvention” section.
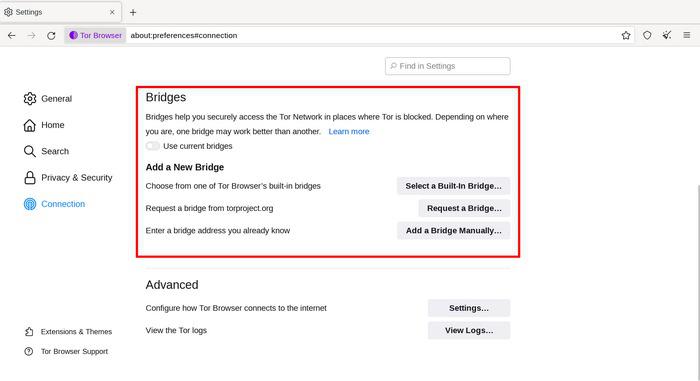
Configure Tor bridge
OTHER OPTIONS
Click ‘Settings…’ next to ‘Configure how Tor Browser connects to the Internet’ to adjust your connection if it employs a proxy. For the most part, this is not required. Since all of your browsers on your system will utilize the same settings, you should normally be able to tell if you need to click this checkbox. Seek advice from your network administrator if at all possible. Click “Connect” if your connection isn’t using a proxy.

However, it is recommended that you choose “Tor Network Settings” first if you reside in a nation with stringent censorship laws, like Egypt, China, or Turkey. You can modify your browser’s settings to get around internet limitations.
To launch the Tor browser after the configuration process is complete, click “Connect.” Once you launch the Tor browser, all traffic is encrypted, allowing you to surf various websites without risk.
Conclusion:
In conclusion, the Tor Browser provides a robust foundation for anonymous and secure browsing. By exploring and implementing its hidden tricks, users can further enhance their privacy, bypass censorship, and protect personal information. However, it’s essential to strike a balance between security and functionality, as some advanced settings may impact the usability of certain websites. Regularly updating and staying informed about the evolving landscape of online privacy tools is crucial for maintaining a secure and anonymous online presence.
Share your thoughts in the comments
Please Login to comment...