Difference between Authentication and Authorization
Last Updated :
03 May, 2024
Authentication and Authorization are both utilized in data security, allowing the safeguarding of an automated data system. Both are very crucial topics often associated with the internet as key components of its service infrastructure. However, each term is distinct, representing different concepts. While they are frequently used in the same context with the same tools, they are entirely distinct from one another. In the authentication process, users’ identities are verified to grant access to the system, whereas in the authorization process, a person’s or user’s permissions are verified to access resources. Authentication precedes the authorization process, while the authorization process occurs after authentication.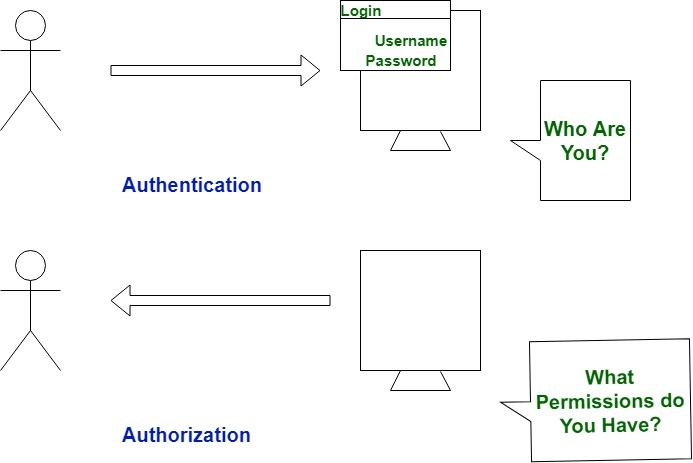
Let us see the difference between authentication and authorization:
| Authentication |
Authorization |
| In the authentication process, the identity of users are checked for providing the access to the system. |
While in authorization process, a the person’s or user’s authorities are checked for accessing the resources. |
| In the authentication process, users or persons are verified. |
While in this process, users or persons are validated. |
| It is done before the authorization process. |
While this process is done after the authentication process. |
| It needs usually the user’s login details. |
While it needs the user’s privilege or security levels. |
| Authentication determines whether the person is user or not. |
While it determines What permission does the user have? |
| Generally, transmit information through an ID Token. |
Generally, transmit information through an Access Token. |
| The OpenID Connect (OIDC) protocol is an authentication protocol that is generally in charge of user authentication process. |
The OAuth 2.0 protocol governs the overall system of user authorization process. |
|
Popular Authentication Techniques-
- Password-Based Authentication
- Passwordless Authentication
- 2FA/MFA (Two-Factor Authentication / Multi-Factor Authentication)
- Single sign-on (SSO)
- Social authentication
|
Popular Authorization Techniques-
|
| The authentication credentials can be changed in part as and when required by the user. |
The authorization permissions cannot be changed by user as these are granted by the owner of the system and only he/she has the access to change it. |
| The user authentication is visible at user end. |
The user authorization is not visible at the user end. |
| The user authentication is identified with username, password, face recognition, retina scan, fingerprints, etc. |
The user authorization is carried out through the access rights to resources by using roles that have been pre-defined. |
| Example: Employees in a company are required to authenticate through the network before accessing their company email. |
Example: After an employee successfully authenticates, the system determines what information the employees are allowed to access. |
Share your thoughts in the comments
Please Login to comment...